
How To: Exploit Development-Everything You Need to Know
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic


Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
Does executing a perfectly timed, no-scoped headshot, followed by a well-choreographed teabagging ever get old? No, no it doesn't, and neither do custom emblems for Call of Duty: Black Ops 2. How else are we going to kill time until Black Ops 3 arrives?
Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

Apple has a few exciting surprises for you in its latest iOS 16 and iPadOS 16 software updates. Released on Thursday, May 18, version 16.5 includes new features, bug fixes, and security patches, and there are even hints of some big things coming in future software updates for iPhone and iPad.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

If you're doing the same tasks on your Android phone repeatedly each day — like playing a specific playlist at the gym, viewing work documents, or watching your favorite music video — you can save some time by automating your routine, turning each task into a one-tap gesture on your home screen.
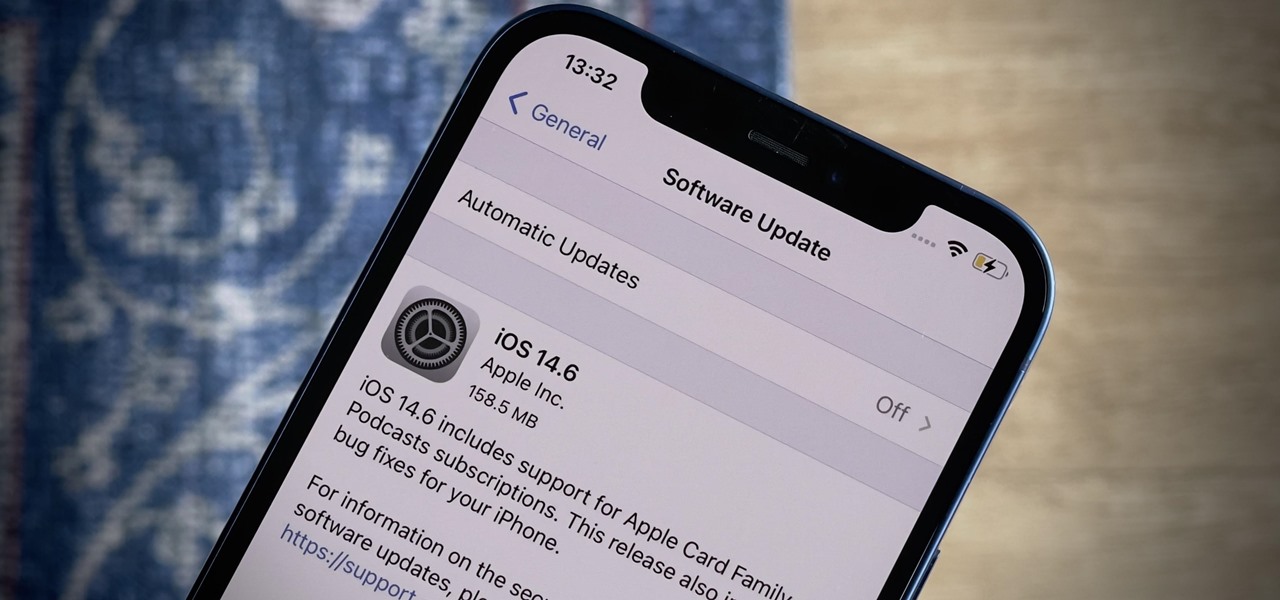
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription support for shows in Podcasts.
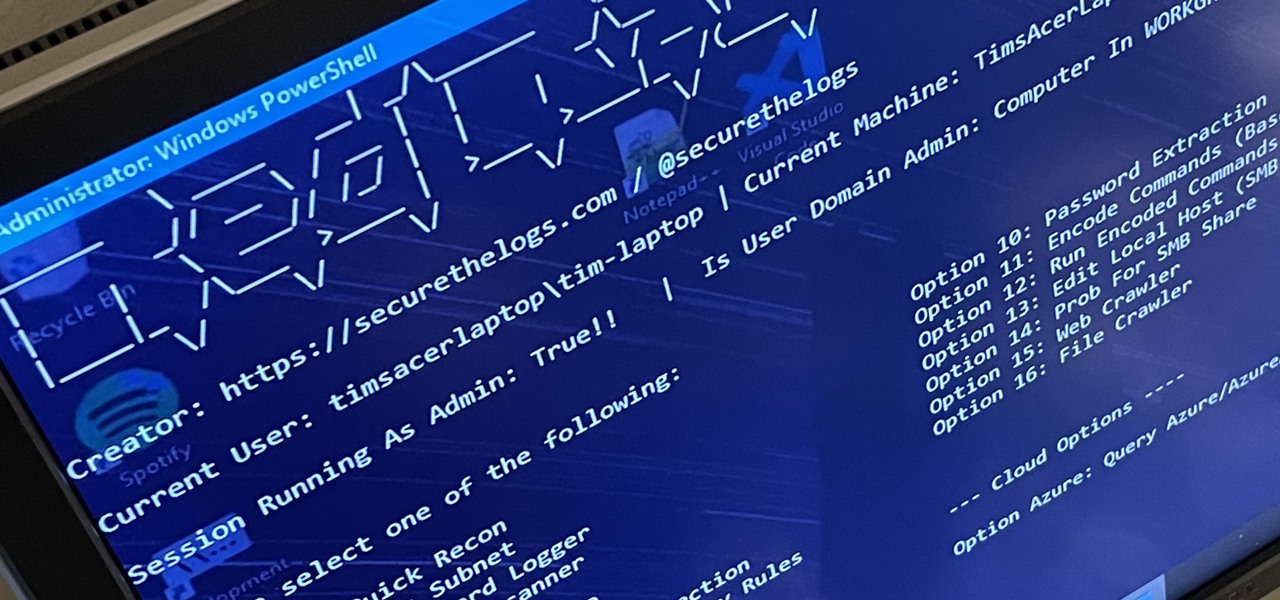
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."
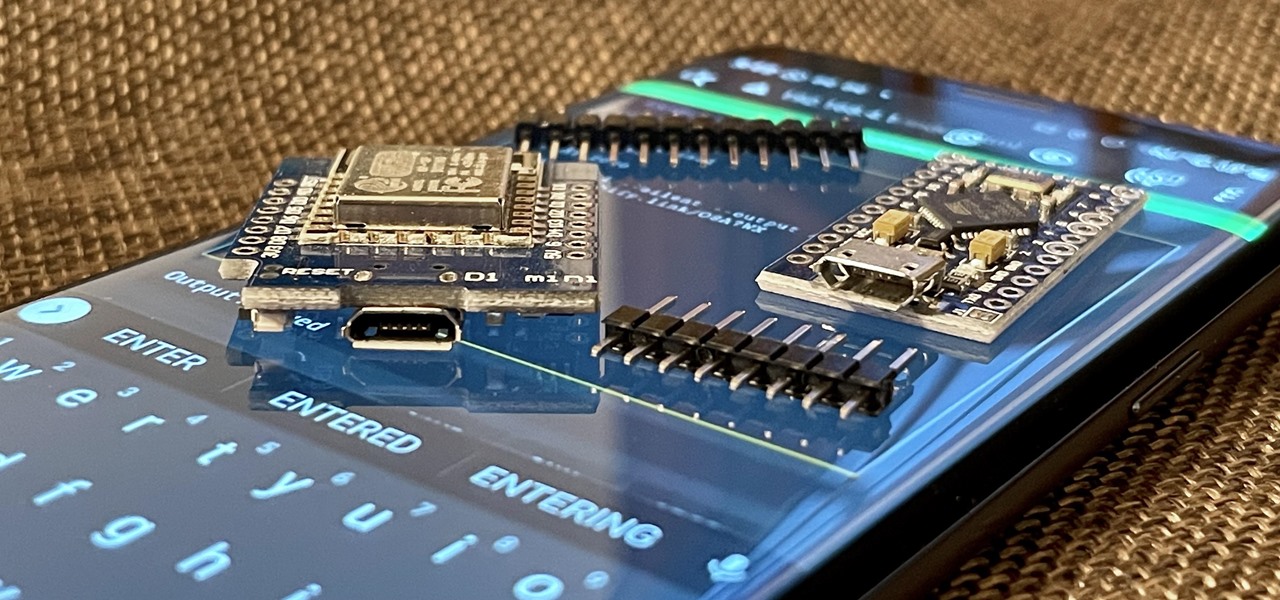
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

Social media apps like Instagram, Snapchat, and TikTok have plenty of editing tools that go beyond the basics, but there are still a lot of things they can't do. So if you want to apply interesting, unique effects to your photos and videos for social media, you'll need to add some other apps to your iPhone's arsenal of tools.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.
It hasn't been long since Apple released iOS 16.0 with over 350 new features, but iOS 16.1 just came out with even more cool updates for your iPhone. While some of the recent upgrades were expected, others are somewhat surprising — and there's even one that you may not even think was possible.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

A radical art group of Russian political pranksters, who go by the name of Voina, have delivered a giant "Up Yours!" to the Russian government... in the form of a 213-foot-tall penis.

Use the lead hand to block in praying mantis fighting techniques. Learn how to do praying mantis kung fu palm block counter punches in this free martial arts video from a black belt instructor. Execute Praying Mantis Kung Fu counter punches - Part 1 of 23.

This Blender tutorialc overs the creation of a game-friendly model (i.e. low-polygon), texturing, rigging, animating, and bringing it into the game engine with basic forward and back controls, as well as turning left and right, and running. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the ...

You won't have to jump into a time machine to get the psychedelic bag shown in this how-to video! Watch as Laura and her friends create a cool and colorful hobo bag from scratch! They're great to use for school, sleep overs or just hanging out with friends! You will need 2 pieces of fleece 20" x 20", 1 strip of fleece 36" x 3", a black marker, pins, scissors, a measuring tape, and the step-by-step instructions in this video activity tutorial. Make a tie dye hobo bag.

The catching arm break kung fu technique is always the same: block the punch and catch the forearm of the attacker. Learn an arm break technique in this free self-defense video on Northern Praying Mantis kung fu techniques. Execute the catching arm break Kung Fu technique - Part 1 of 8.

The tough bunker shot: When the pin is tucked tight to the edge of the bunker you need to learn to add loft to your sand wedge to get added height and stop on your shots. Jason Froggatt shows how to do it... Execute the high bunker shot.

Learn how to get your body into the best bio-mechanical position to execute the shot. This tip from professional archer and hunter Larry Wise teaches you how to bow hunt with the best bio-mechanical stance. He shows you the stance -- the full draw position -- to execute the shot with back tension when you bowhunt.

This video demonstrates good technique for planning and executing a pool shot, beginning with the 90 degree rule or the 30 degree rule. First visualize the aiming and impact lines, then the tangent line where the cue ball will go. Decide how fast to shoot depending on how far the ball is from the pocket. Select your hand position then execute the stroke, keeping your head down. Plan a shot in pool.

This video shows how to do cross-overs with a theraband. Add this exercise to your next chest routine. Don't let your back move while doing this exercise, keep it straight and your abdominals tight. Do cross-overs with a theraband.
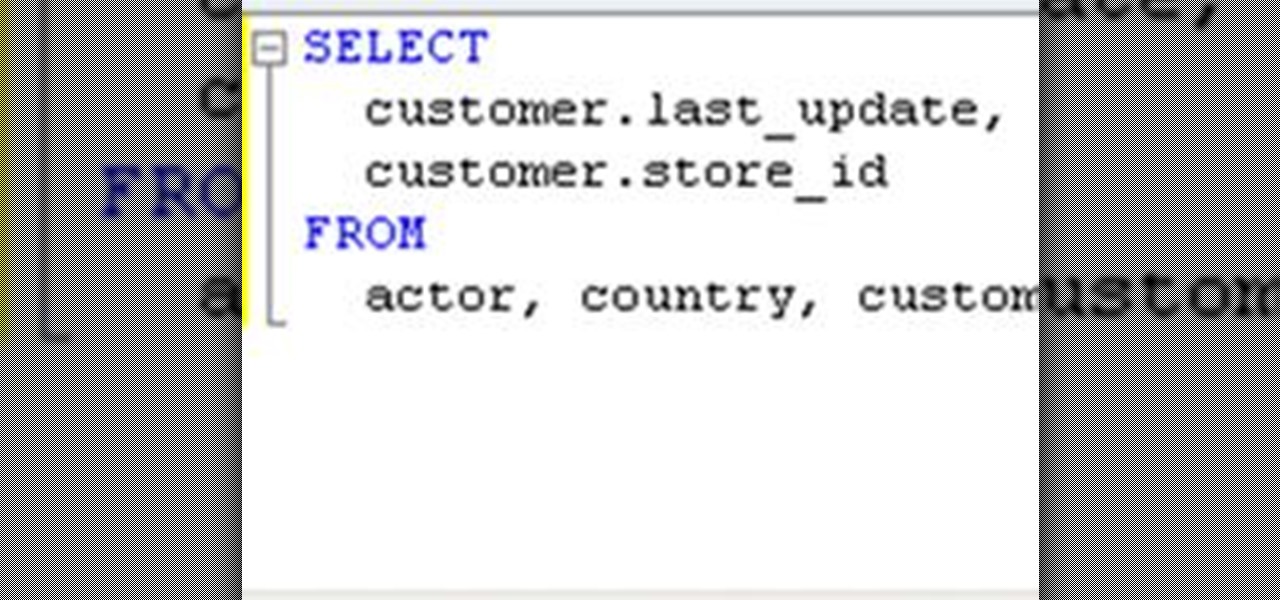
If you need to build a SQL query, you can choose one of two alternatives. The first and a rather old way is using a console. But if you build your queries in MySQL console, you have to remember all the commands and keys. This is not a convenient way, because query execution is a time-consuming process. Another way is to use some graphical interfaces for MySQL. It can fulfill many developers' requirements, including query execution.

Gameday! Bring on the best and most evil pranks. Humiliate those closest to you. This devastatingly simple office prank requires nothing out of the ordinary to perform. In fact, you could probably execute this right now, without getting up from your chair.

This simple video crocheting tutorial shows how to execute a triple or treble crochet stitch. Learn how to crochet this stitch very useful for Japanese amigurumi projects or any other shaped crochet project. Crochet a triple or treble crochet stitch.

The "wood-chopper" isn't just for lumberjacks. You can get the full woodsman workout yourself, without the axe! Men's Health shows you how to do the wood-chopper exercise, and when you power through this move, your upper and lower body, along with your core muscles, are working to the max.

Doing this workout from Men's Health will increase flexbility and strength in your rotator cuffs. Make sure to execute technical precision to avoid injury.
Summary =======

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...