
How To: Install Linux on a USB With Unetbootin
There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive.


There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive.

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

Christian Cantrell, Adobe's Air Product Manager and Evangelist, has released a video to demo websites that take advantage of the motion sensors in a mobile phone, tablet, or laptop via JavaScript. Now, let's take a look through the code and break down the core pieces that you'll need in order to build your own sites that can determine the 2-axis tilt, 3-axis gyroscope, and compass direction of the mobile device it's being displayed on.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

Warning Don't torrent things that you do not have the rights to torrent. Everything I torrent, I have a physical copy of, and just want a copy on my computer without causing wear-and-tear on my DVD drive's laser. Piracy is naughty.

It's an ambitious How-To project to say the least, or more specifically, an over-the-top political art installation by San Francisco artist Brian Goggin. You may have previously heard of Goggin for his "Defenestration" project—an installation of "frozen" furniture, being tossed mid-air from a San Francisco apartment building. But Goggin's latest project sounds significantly more challenging to execute, considering the elaborate game plan involved:

Age doesn't matter in the world of programming, only skills, and recent high school grad Jack Eisenmann definitely has them. He recently built a homebrew 8-bit computer from scratch, calling it the DUO Adept. A worn television makes up the monitor and speaker system, an old keyboard acts as the input controller and the actual computer itself is housed inside a clear Rubbermaid container, consisting of 100 TTL chips and a ton of wire.

German photographer Peter Langenhahn's process is incredibly laborious; similar to photographer Lori Nix, he can spend up to three months on a single photograph. But while Nix spends the time constructing elaborate sets, Langenhahn is anchored to the computer, editing.

Inspired by the beauty of traditional signage printed on doors and buildings, Rero is a French graffiti artist who makes a simple, yet heavy mark. Using the universally common Verdena typeface, Rero brands abandoned public spaces in extreme disarray with his own codified messages based on theories of public use of imagery and private property.

Food is the meeting place of left and right brainers: Culinary arts call for creativity, but is also deeply rooted in the What, Why and How of basic science—baking powder vs. baking soda, the rising of dough, the falling of a cake, etc. Below, two plays on left brain principles—the Möbius strip and the law of gravity—both executed with right brain flair.

If you've yet to witness B.A.S.E. jumping, it's an activity for adrenaline junkies first publicized by filmmaker Carl Boenish in '78. The freefall sport employs ram-air parachutes, and is most commonly executed in locations such as the highly elevated El Capitan rock formation of Yosemite National Park (El Capitan is also technically the birthplace of the sport).

As a non-cat owner, catnip is a mystery to me. So, people essentially... drug... their cats? Weird. Google catnip, and you will find a whole slew of incredible images related to the topic...

One of the greatest innovations in the DSLR revolution is not only being able to execute shots you never dreamed possible, but you'll find it's affordable, too. I can't think of a better example than this remote controlled DSLR helicopter rig, designed specifically for the Canon 7D and 5D. Advertised as "high definition, low altitude photography and videography," HeliVideo's founder, Eric Austin combines his experience and love of remote controlled helicopters with his knowledge as a videogra...

The V-up is one of the more challenging ab exercises. While it may appear simple, there are several factors that make this exercise difficult to execute properly. Some of these factors include timing of the movement, counterbalancing, hip positioning, flexibility, and abdominal strength.

As you all know, the first Null Byte Technical Excellence Tutorial Contest ends this coming Monday, Feb. 15, 2016. If you are working on another great article or your first article, try to complete it and submit it before midnight Pacific Standard Time (PST) to be considered in this contest. The winner of this contest will not only receive a certificate verifying the technical excellence of their tutorial, but they will also receive a free copy of the Professional version of the Exploit Pack ...
In this tutorial we will be go over how we can make use of conditionals. In Perl the main conditional is the if statement. The if statement in
Hello, Hackers/Viewers, Today's topic is going to be based on how to disable autorun for Removable Disks and Drives. Doing that is very easy, i you read the below!

Attention cheapskates and locksmith apprentices, this key copying solution is stunningly simple. We've really mulled over this one. As you can read in the comments below, people struggle with executing this successfully. But it can and will work. You just have to modify your key to fit your needs.

Monserrat Morilles sure shook up Chile. She brought a whole new brand of street performance to the city's commuter trains. Her act: strip to a bikini and poledance in the middle of rush hour. Morilles, 26, was protesting the 'prudishness' of Chilean society.
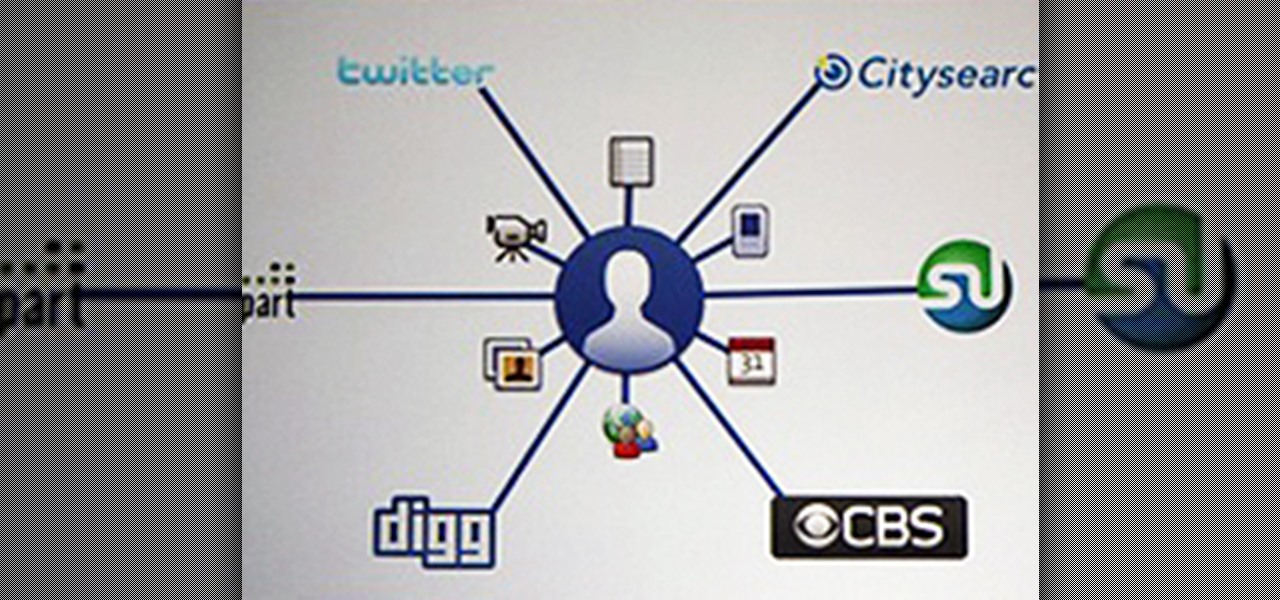
"Connect via Facebook" — these words are coated on over a million websites nowadays, but Facebook Connect poses a risk of leaking personally identifiable information to those third parties. If you're not convinced Facebook Connect is safe, then turn off the flow of personal data to those websites!

Are you ready to learn a magic trick that is sure to amaze your friends and family? Ryan Oakes is going to show you how to pass ropes right through your body. You will need two pieces of rope, about four feet long each, a pair of scissors, and white thread.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

Big news from the world of game development engines. For several years, Unity3D has been the free 3D game development engine of choice for aspiring and indie game designers around the world. While it isn't as powerful as Unreal Engine 3 or CryEngine, it's free and much easier to use. Now, according to an announcement made by Unity yesterday, Unity 3D is about to unleash a huge weapon that neither of those other engines can claim: Flash compatibility.

There's never a bad time to pull a prank on someone, right? Well, how about you consider setting up this prank during lunchtime? Next time you see a co-worker leave his/her takeout food unattended, that's when you'll strike. Follow the simple steps below and you'll be known as the master prankster at work. Tools and Materials Needed

Watch this first 'tutorial'.FauxTo! Hoax! Con! May 28, 2008, this video was uploaded to YouTube illustrating the popcorn popping power of a circle of ringing mobile phones. Radiation. Amazing. Viral. Millions viewed.

Introduction In this article you will find instructions to replace a broken LCD screen of a LG KF600 phone. To execute these steps a new replacement LCD should be bought beforehand. Stores that sell replacement KF600 LCD screen can be found on the Internet. These instructions can also be used for other type LG phones that are part of the same family or have the same internal structure.

When dancing the merengue, it's important to use your hips and execute proper footwork. Learn the basic footwork of the merengue from a professional dance instructor in this free video. Perform basic Merengue dance steps - Part 1 of 6.

In this Illustrator CS2 video tutorial you will learn to execute Pathfinder Connect. The command lets you connect multiple shapes into one shape. You have to click Expand button to see the result. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Connect multiple shapes into one shape in Illustrator.
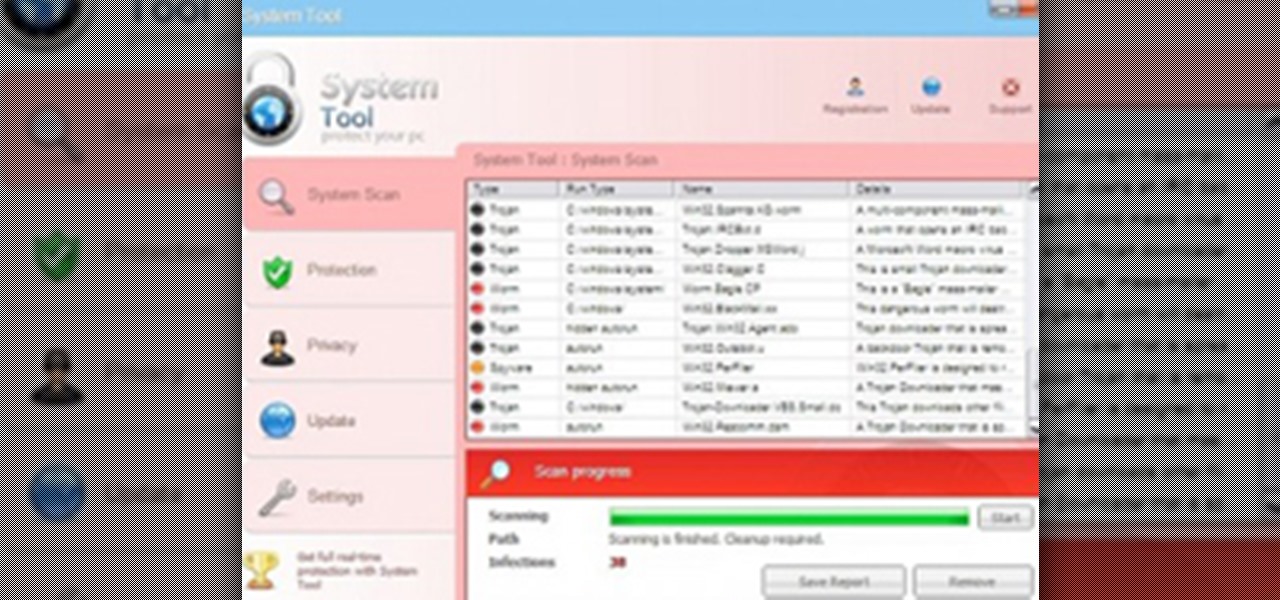
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

Bash (Shell) Scripting for Beginners Intro
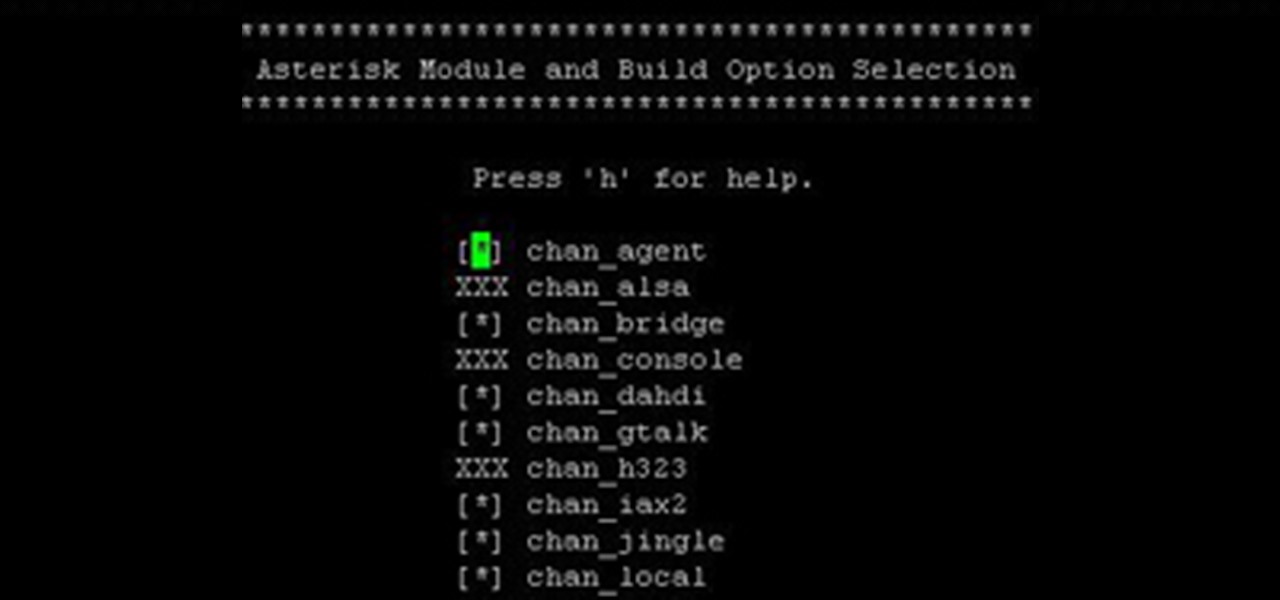
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.