
How To: iOS 16.4 Has 53 New Features and Changes for iPhone You Won't Want to Miss
Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.


Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

Android Messages, formally named simply "Messages" now, has built-in spam protection. This doesn't get every spam SMS message, however — in fact, you can still get unwanted texts multiple times daily even with the feature enabled. Thankfully, you can manually block numbers, too.

Smartphones have put an end to camcorders. If you want to capture memorable moments in high quality, look no further than that technological marvel in your pocket. Recent Galaxy phones are shining examples of how far we've come — but the more capable a camera gets, the more complicated things can be.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

I know, "Steamdown" conjures images of a hoedown, but "Steampunk prop breakdown" is a bit of a mouthful, I thought.

Google Photos is not only an exceptional cross-platform app for photo storage but also a handy tool for generating and creating collages, movies, and animations from your photos and videos. When it comes to collages, you can now customize them and dress them up with vibrant templates.
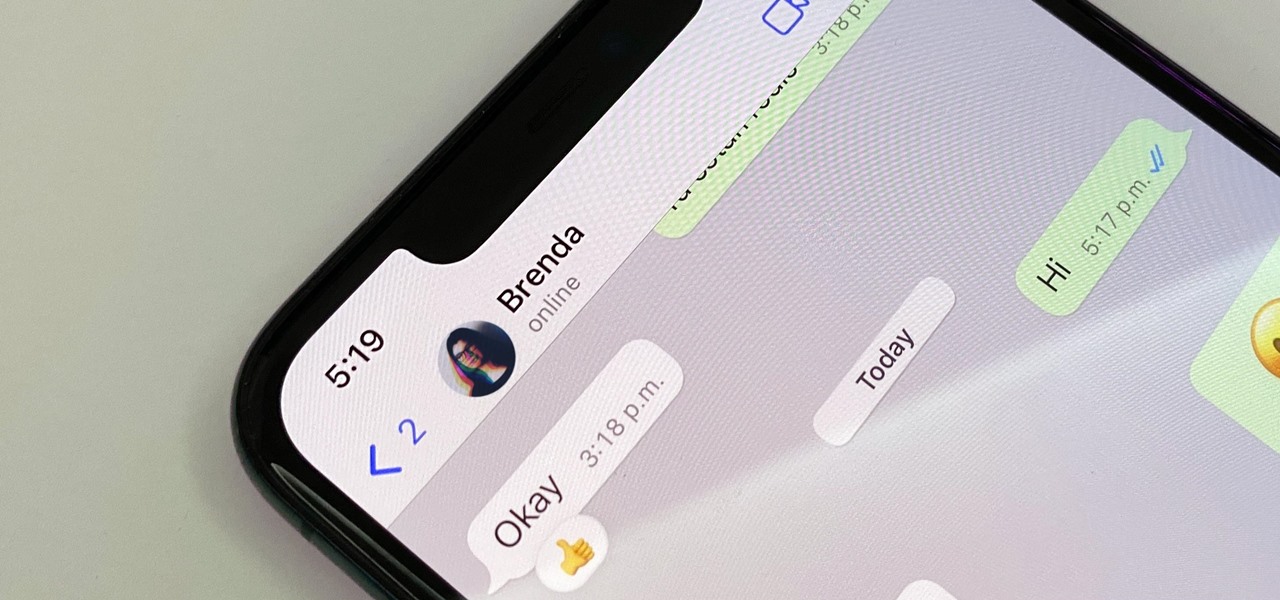
By default, everyone on WhatsApp can see when you're using the app. If someone recently messaged you and sees you're currently online, they may think you're avoiding them if you don't respond right away — especially if you don't share read receipts. However, you can block them from seeing your online or last seen status and apply it to everyone or just specific contacts.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

The camera situation on the all new HTC One is a little daunting. The M8 has not one, not two, but three camera lenses built in. First, there's the 5 megapixel selfie machine up front, then around back, there's the new Duo Camera with a refined UltraPixel sensor. HTC has done things differently here, and the UltraPixels and dual lenses means that the M8 doesn't necessarily take pictures like you'd expect—and that's not a bad thing. With a little guidance and some easy tricks, you can use all ...
You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.
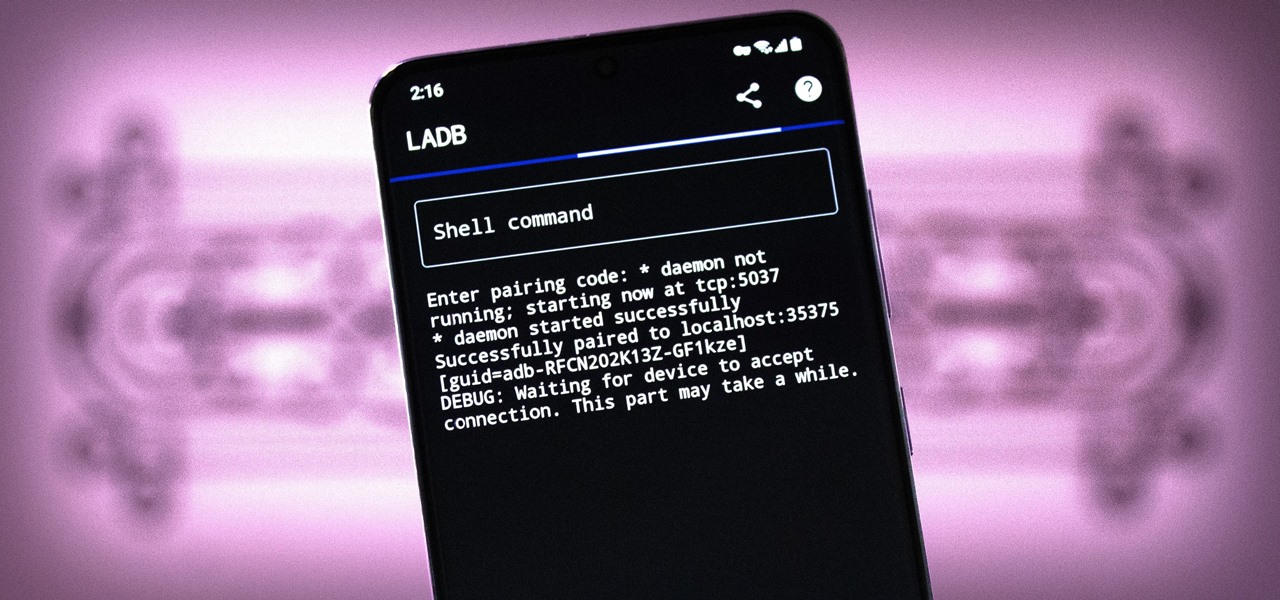
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.
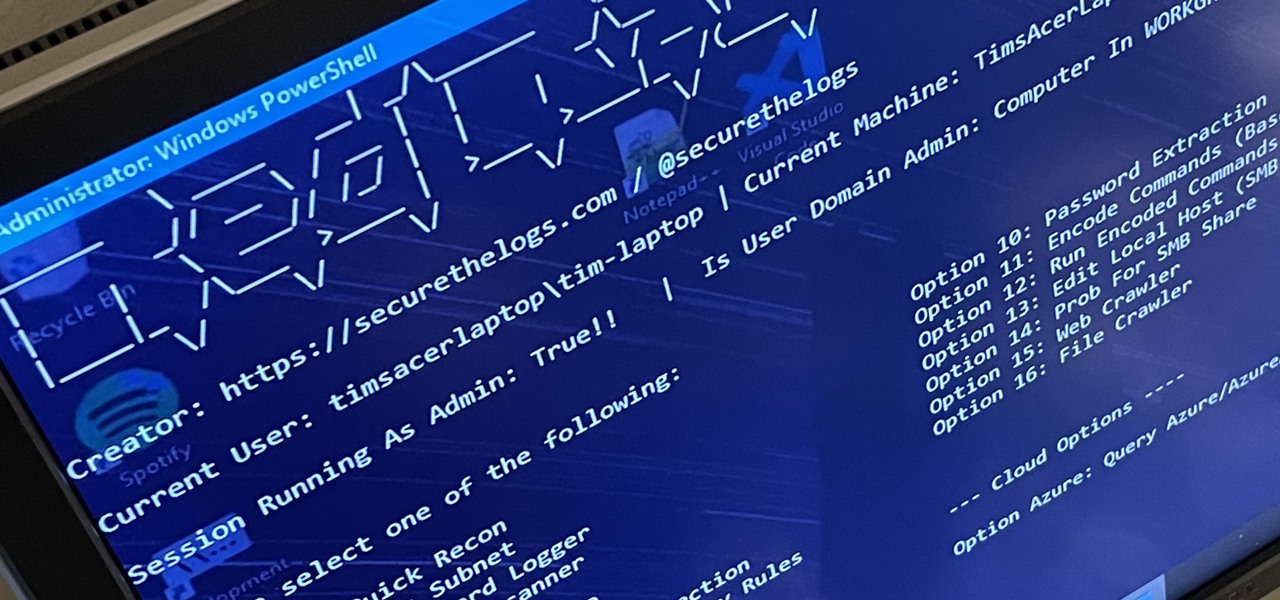
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.
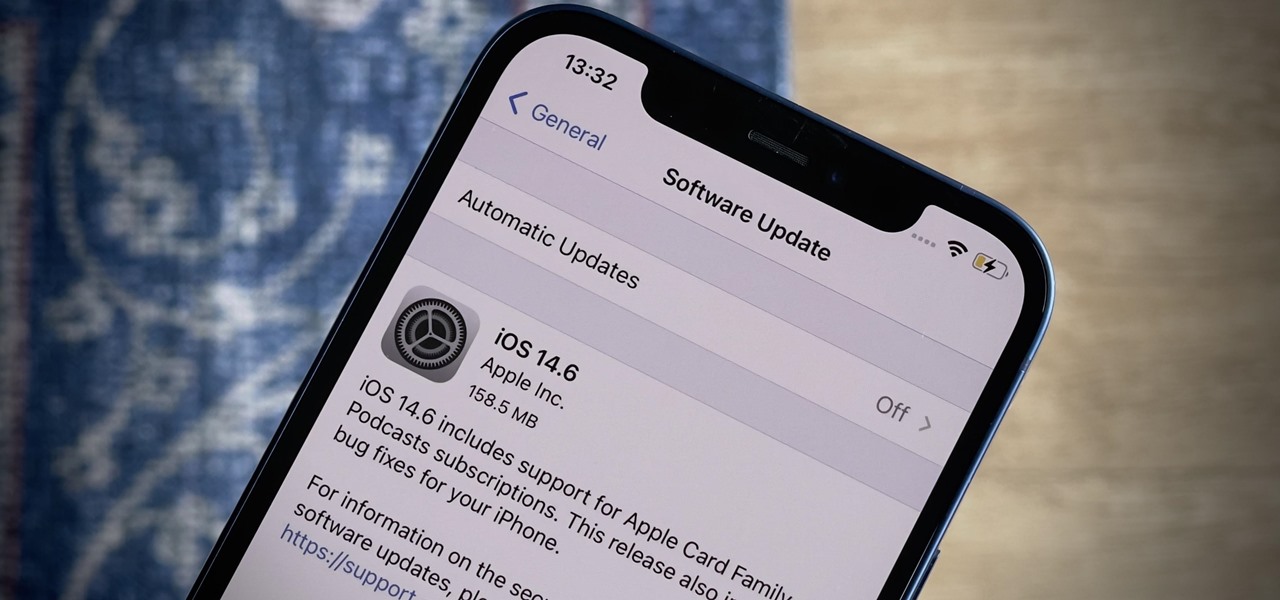
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription support for shows in Podcasts.
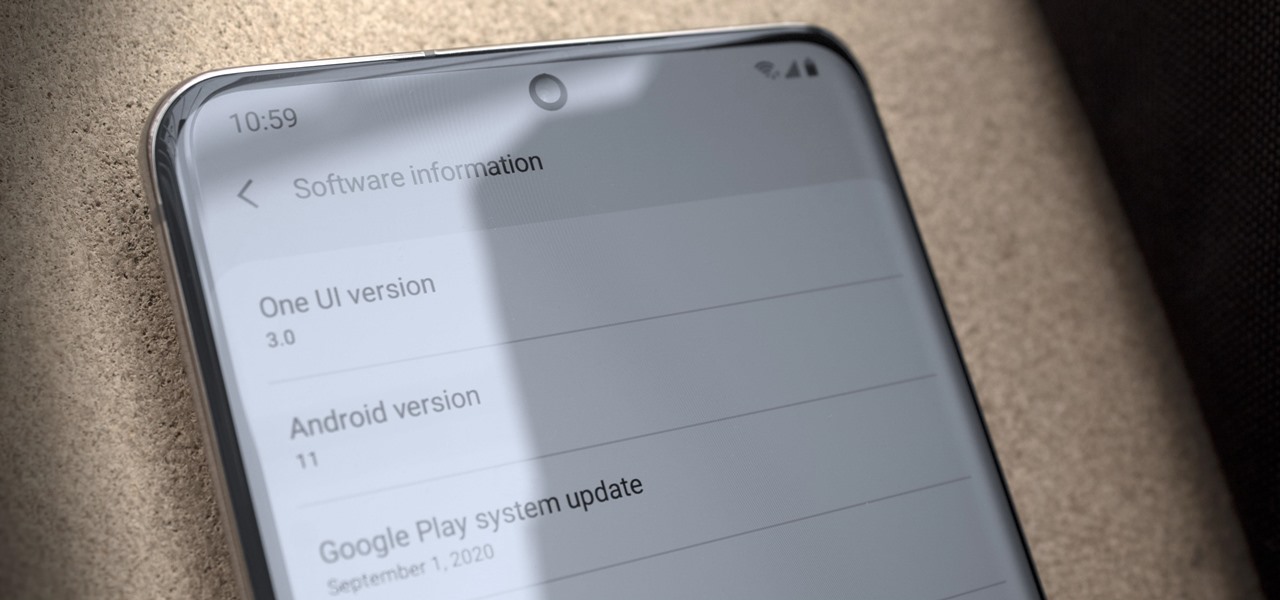
Just days after Google released the official Android 11 update, Samsung already had a pre-beta build of One UI 3.0 available for developers to test their apps on. So this year's main OS upgrade is likely hitting Galaxy phones even earlier than we thought.

Clogs are a nuisance, but happen over time. Don't let sinks, drains, or toilets overflow; clear it out! This video home improvement tutorial shows how to choose the right equipment to clear a clogged drain easily.

Watch this video from This Old House to learn how to fix a bathtub drain stopper. Steps:

My Briggs and Stratton power generator wasn't used for 3 years. Trying to start it again, lead to some problems. The video will show you the true story and the solution. The first problem was, that it lost some fuel - the fuel pipe was broken. In good hope I tried again to start it, but it stopped within seconds. A check of the spark plug to find a very dirty one. After cleaning the spark plug, the engine ran, but only for a few seconds. It lost a lot of fuel and stopped again. The fuel was c...

Watch this video from This Old House to learn how to clear a clogged drain. Steps:

Watch this video from This Old House to learn how to install an automatic shut off valve for a water heater.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

On the Android version of the Telegram app, the attachment icon disappears when you input your first letter or emoji. This "feature" forces you to either delete what you wrote to attach a picture first, or just send the file afterward. Since both of those options suck, we were happy to find a hidden third way.

So many of you like to save up your gold coins to buy things like castles, treasure cards and clothing. But sometimes when you buy something, an error message pops up. One of them is this extremely annoying one: "Transaction was not successful."This error happens mostly when buying clothes. Let's say you want to buy a robe, but it is too expensive. You change the color of the robe to brown, yellow or white and try to buy it. When you click Buy, the error pops up. You switch realms. No differe...

Lisa Nichols, contributing author of The Secret and one of the great inspirational speakers of our time, believes the best way to stay motivated when continuing your education is to “begin with the end in mind.” Pushing forward through challenges is what makes accomplishment so gratifying. Every accomplishment leads to personal growth. Nichols believes that making the completion of your degree “non-negotiable” means that you will not settle for anything less.
From ladotbikeblog:

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.
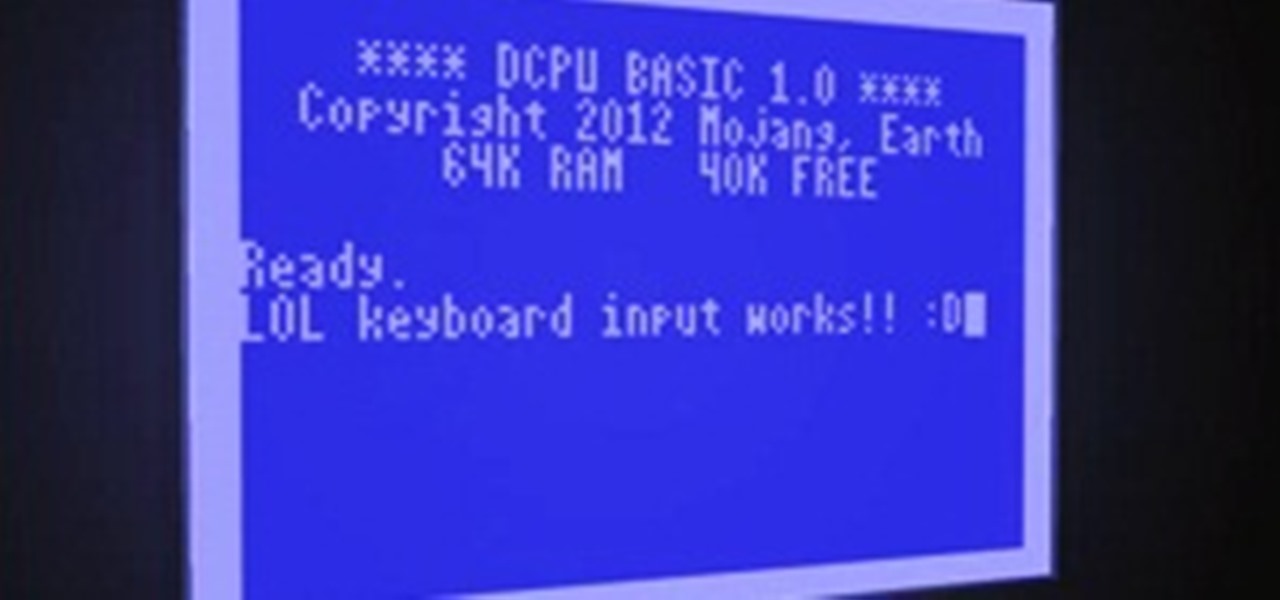
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.