Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.
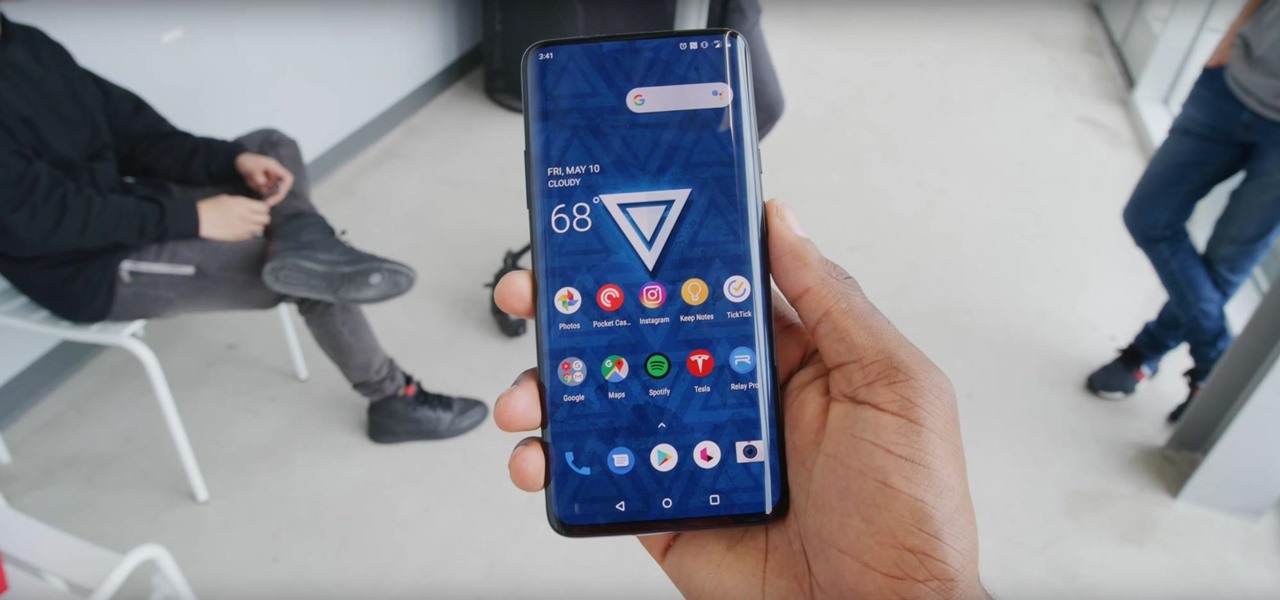
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

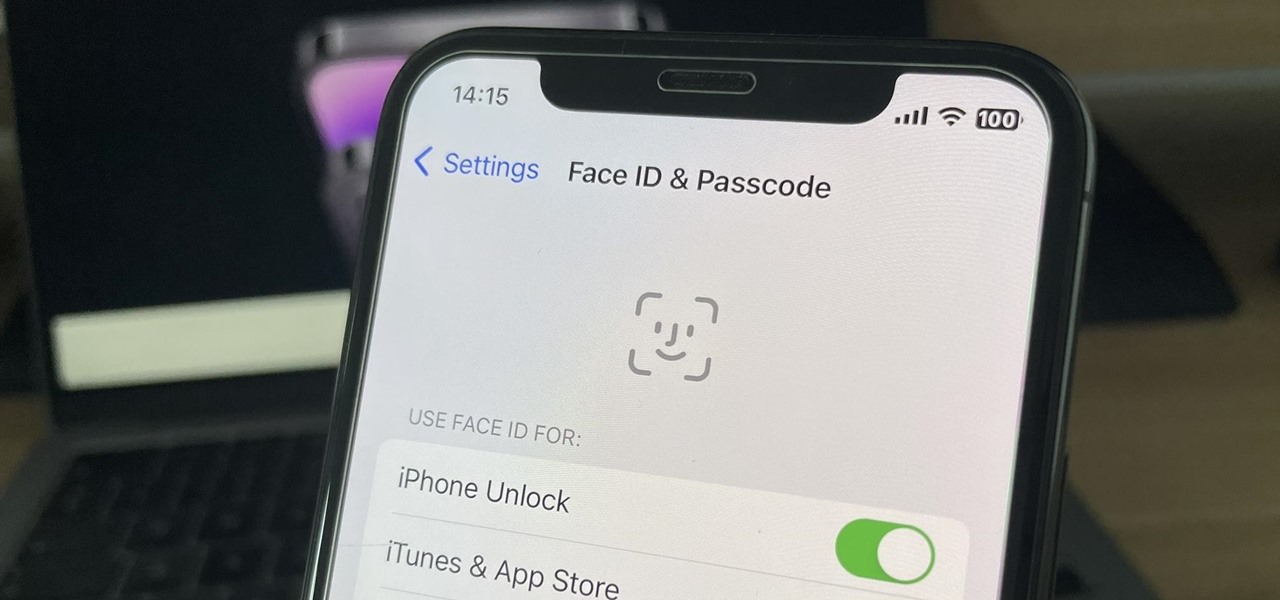
The iPhone 13 and iPhone 14 series models have a new feature on iOS 16 that lets you use Face ID when your iPhone is in landscape orientation. This is most helpful when trying to make purchases in apps and games where you use your iPhone rotated on its side. If you're having issues using Face ID in landscape mode, there may be some easy solutions to getting it working.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and easier. But it's easy to overlook some of these features, so here are some tips and tricks you need to be using if you aren't already.

URL tracking codes: you'll see them on almost every link you copy online to share with friends and followers. It could be tens or hundreds of extra characters appended to the end of a URL, which websites and marketers use to tell how you got to the link in the first place. These excess tracking tokens not only make the links you share look sloppy and spammy — they could even invade your privacy.

The Snapdragon version of the Galaxy Note 20 and 20 Ultra — the one sold in the US — can't be rooted. Without root, the level of customization is limited. Such a large group of Android users shouldn't miss out on mods, and they don't have to.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Apple's Notes app has an important feature many users overlook, yet it's arguably the most crucial thing you should use for all your notes synced across iOS, iPadOS, macOS, and iCloud.com. And Apple makes the feature much easier to use than years before, so there's no reason you shouldn't be using it.

If you're a musician in need of some lessons, there's no better way to learn than with Music Radar's so-called "Tuition" instructions. Although the title tuition is misleading, this video class is anything but costly, because it's free, right here. Whether you're looking for help with your voice, bass, electric guitar, drums, guitar effects, piano, Logic Pro or production techniques, Music Radar is here to show you the way.

You Want White Teeth Without Expensive Over-The-Counter Products? Here's An Inexpensive, Effective Solution.

In this how-to video, professional makeup artist Gary Cockerill shows how to take care of your makeup and keep a clean makeup bag. While most women know the importance of using the right makeup and the right tools, many will overlook basic hygiene which can be self-defeating for the cosmetic purpose. Check out this video makeup tutorial and learn how to clean a makeup bag and improve skills and techniques. Clean a makeup bag.

3D Dot Heroes Preview Release Date: May 11th, 2010 for the PS3

This article is all about creating content. This is a very important concept to grasp because the content that you create for a website is going to be the basis for how you will advertise and promote that website. Content, meaning articles, videos, and even podcasts is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

Since the Geminid Meteor shower is intensifying more every year, grab your binoculars and lay down in a field to enjoy the show! If you are going to observe one day, do it on the peak: December 14th.
There's gonna be a rumble.... For this week's GJ article, I thought I would jump right into talking about a mortal-lock favourite of mine: West Side Story. If you haven't seen it (and a lot of folks havent - dudes especially) and you want a lesson in filmmaking craft from a bonafide master then you kind of owe it to yourself to rent this undisputed gem.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.