Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

The knee-jerk reactions to Magic Leap's long-awaited augmented reality device, the Magic Leap One: Creator Edition, range from pent-up joy to side-eyed skepticism. That's what happens when you launch the hype train several years before even delivering even a tiny peek at the product.

Continuing its unrelenting (and mostly successful) campaign against Snapchat, on Tuesday, Facebook announced the addition of "World Effects" to its Messenger app.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Disasters can happen at any moment, and when they do, it's often hard to find the right information to help you get to safety as quickly as possible.

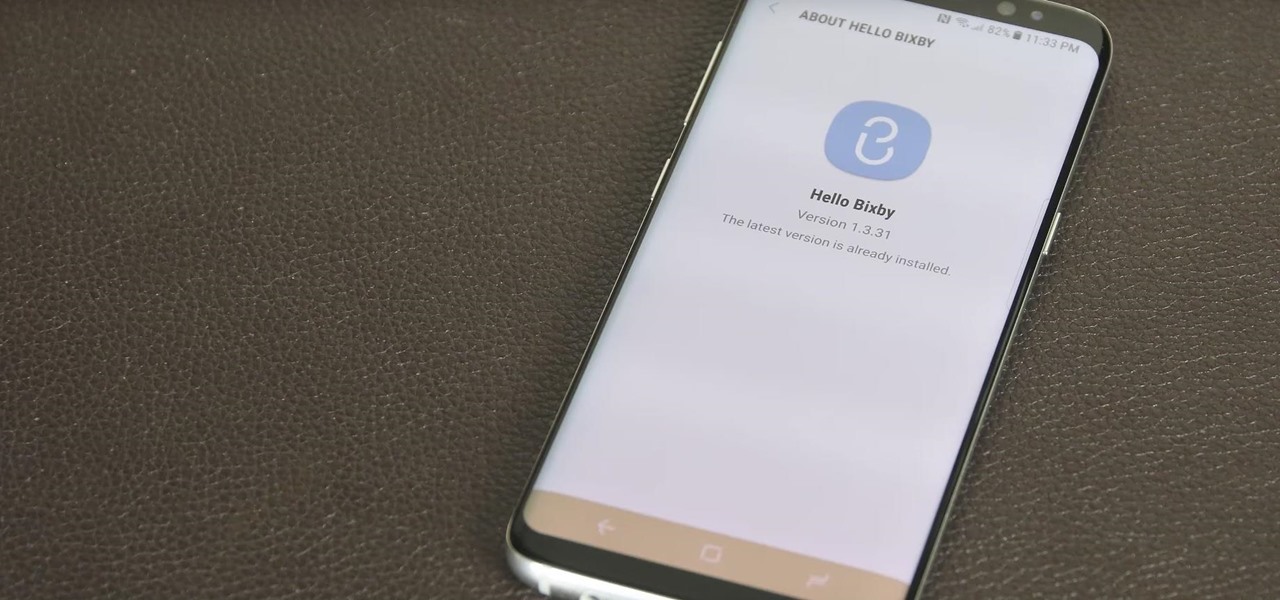
If you're not familiar with Bixby, I don't blame you. The Samsung assistant was released two months ago with the Galaxy S8 and S8 Plus. While users were excited about this Google Assistant-like feature, they were ultimately disappointed by the limited rollout of only some of Bixby's features. Now, Samsung is hopeful to perfect Bixby using you.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This weekly Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column starts with a stock price that's performing well for one company — one that HoloLens developers should know quite well.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

In an early morning blog post, Microsoft announced the expansion of the Microsoft HoloLens Agency Readiness Partner Program. This announcement comes on the tail of an expanded HoloLens release over the last few months to many countries outside the initial US and Canada.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

You might notice that there's been a few changes around here. All of us here at WonderHowTo have been working hard to create fun new spaces and topic areas to dig our heels into. We've created a few brand new websites, spiffied up our design, and today we're launching the WonderHowTo network.

From a quick, passing glance at a photograph, you may not notice that Jon Almeda's impressive displays of ceramics mastery are actually the size of coins. It's well-documented how much tiny art is loved by WonderHowTo, but this petite pottery may take the cake as the most impressive display of craftsmanship.

People have been transforming mud into art, aka pottery, for thousands of years. This is not a new phenomenon, but often the finished product has a certain utilitarian aesthetic, such as a bowl or vase.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

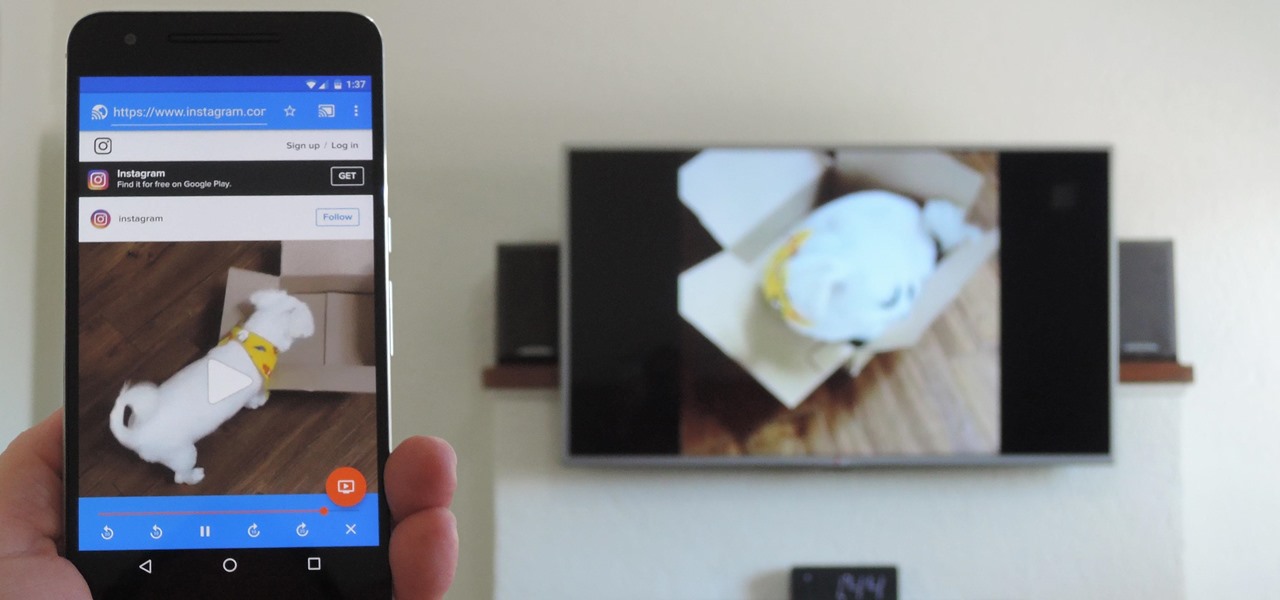
The Google Chrome browser for Android allows you to cast quite a few different videos from the web to your TV, but some sites actively disable this functionality, and others have outdated video players that won't allow for it. For example, Instagram's mobile website won't let you cast any videos, and the official app doesn't support Google Cast.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

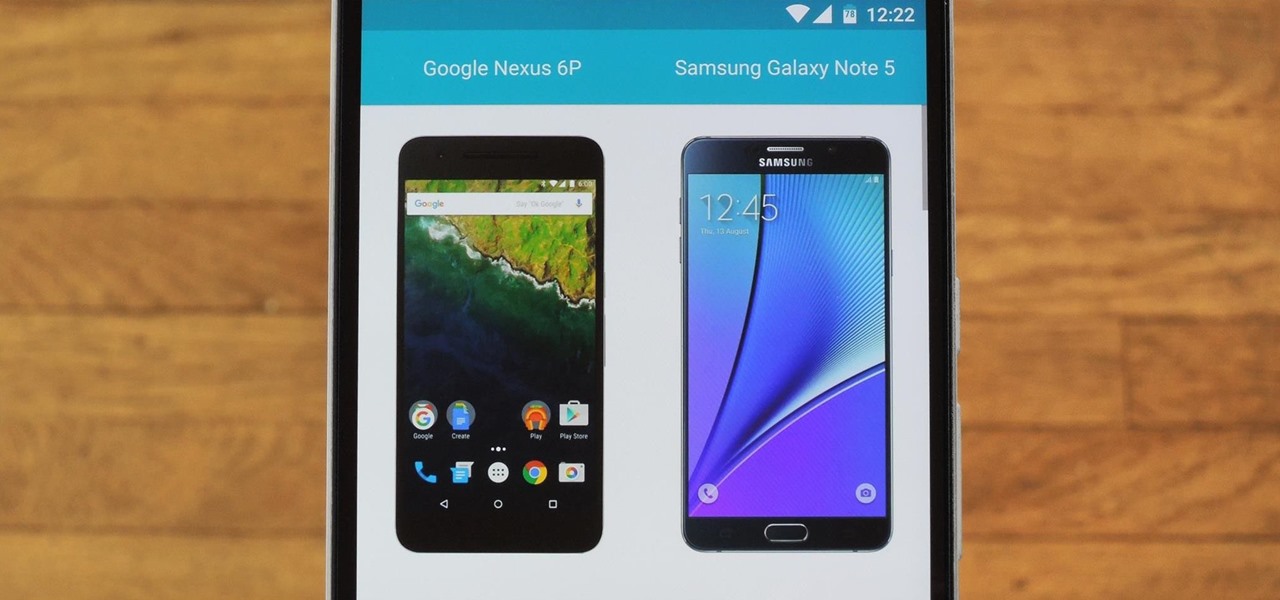
Shopping for a new phone is an entire ordeal. Even when you've narrowed it down to a few choices, comparing the finalists can be difficult, because specs and prices are scattered around on various different manufacturer websites, and if you're trying to do this on your current phone, most of these websites aren't optimized for mobile viewing.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

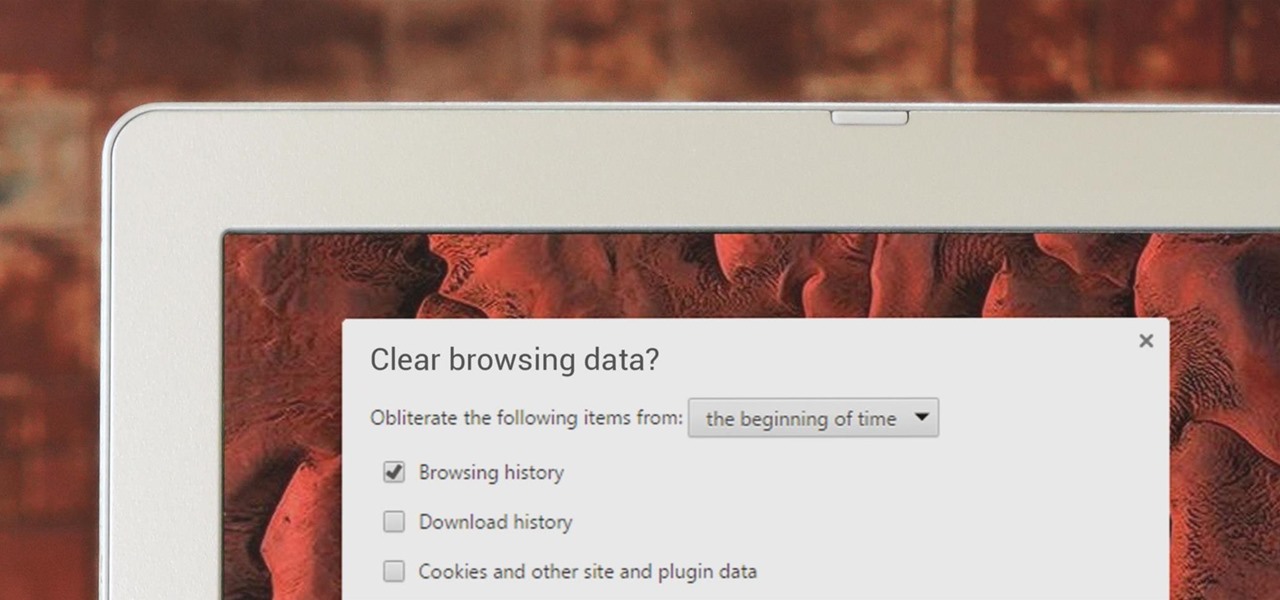
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

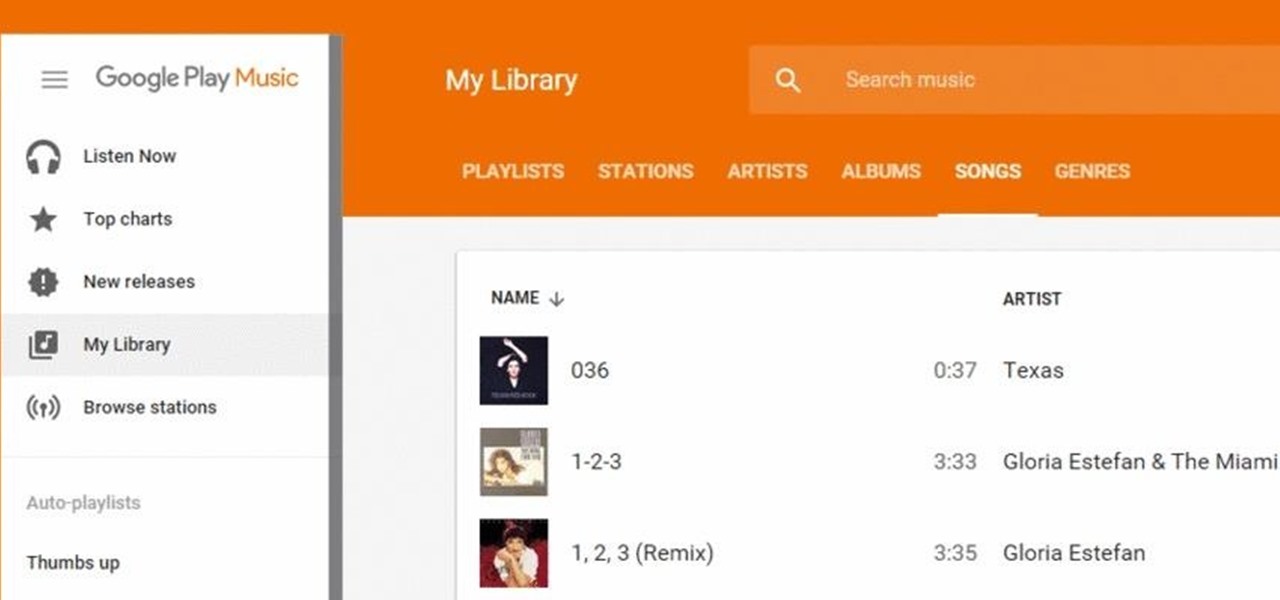
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

With iOS 8.4 and iTunes 12.2, we got our first look at Apple Music, Apple's new streaming subscription service. While it's a little late to the party, there is definitely an incentive for iOS and Mac OS X users to switch over from competitors due to its heavy integration with the Apple ecosystem.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

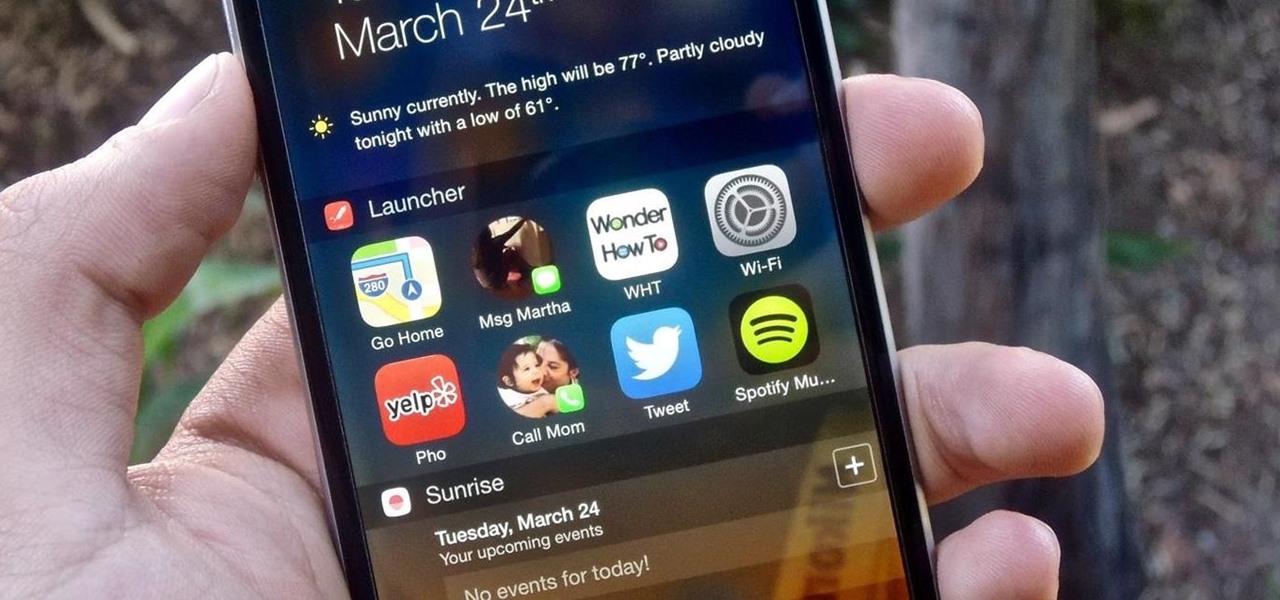
An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

With all due respect to the fine folks at DrinkTanks, it's a little surprising that no one came up with their idea sooner. After all, last I checked, beer was pretty darned popular.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"