In this ClearTechInfo tutorial the instructor shows with examples on how to hear and view any audio or video file on your Windows PC. This is a basic tutorial where the instructor shows how to open and play them. Video files in many formats are not recognized directly by the Windows media player like the avi format and mkv format files. Even if we try to open these files it shows an error message that the file is not supported by the player. So in order to play these kind of files we need to ...
This how-to video explains how to copy and paste text in the browser in a Motorola Droid phone.

To obtain a work permit, you must first have a job offer from a Canadian employer. To get a job offer, you can apply directly and send your resume to a perspective employer, use an employment agency, or post your resume on employment websites. Next, you must have a labor market opinion. To get an LMO, you have to fill out some forms and submit some supporting documents. This process can take from a few weeks to 6 months to complete. After the LMO is approved, you must then apply for a work pe...

This is an electronic travel authorization system used to gain travel authorization to the United States. There are certain countries that fall under a visa waiver program, meaning that you do not need a visa to enter the US to visit. In that case you use the ESTA system. The countries that qualify in the VISA waiver program include Andora, Australia, Austria, Belgium, Brunei, The Czech Republic, Denmark, Estonia, Finland, France, Germany, Hungary, Iceland, Ireland, Italy, Japan, Latvia, Lich...

So, you've downloaded Boxee... Experience TV in a brand new way! This video will help you get started.

Are you one of those vegetarians that misses meat? Have no fear. You don't have to miss out on the flavor of meat while being a vegetarian. Learn how to prepare tofu to trick your carnivorous side.

Are your fish starving? If they are, you need to do something about it, and quick. Well, there's no quicker solution to feeding your fish than hacking Happy Aquarium with Cheat Engine.

This is Cheat Engine hacking for Club Penguin. If you want more coins, you have to hack your way to them. And to hack your way to more coins, you're going to need Cheat Engine.

We've all had it happen before. You fall asleep drooling in class, resting your head on your hands. Or you use your hand to lean on as you browse websites on the computer. Once you move out of your position, all you feel is an unsettling, nervous numbness and tingling. Rather than freak out, check out this video to learn what you can do to relieve this numbness.

Those old cell phone and laptop batteries staring you in the eye? Don’t worry, recycling them is easy.

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

It’s never too late to clean up your credit record – and save yourself thousands of dollars in exorbitant interest rates in the process. Learn how to repair your credit with this guide from Howcast.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Food, water, and shelter—that’s all butterflies and birds need to consider your backyard a home. And the great thing is that what attracts them will beautify your yard as well!

Reverbnation.com is a revolutionary new website that has been taking the internet promotion idea to the next level with free emailing, widgets and stats. Learn tips on how to use this great site in this free video clip series.

In this tutorial, we learn how to use torrent software like uTorrent. First, go to the website, Burn OSX, and download their software, then install it. After this, go to isohunt. When you get to this website, type in the name of the item you are searching for. When you find it, click on it and it will start to download through uTorrent. When finished, you will be able to open up what you downloaded and then use it how you wish. It will then start seeding, which means that it is being shared w...

In order to bypass Megavideo and Veoh's viewing time limits you will first need Mozilla Firefox. To download Mozilla Firefox then go to Firefox and download the Mozilla Firefox browser. After downloading the browser you will need to install the add-ons. Go to the website Illumitux add-on in order to download the add on Illimitux, after downloading the add on then Mozilla will prompt you to close the browser window. Go ahead and close the window then re-open it. When you re-open it Mozilla wil...

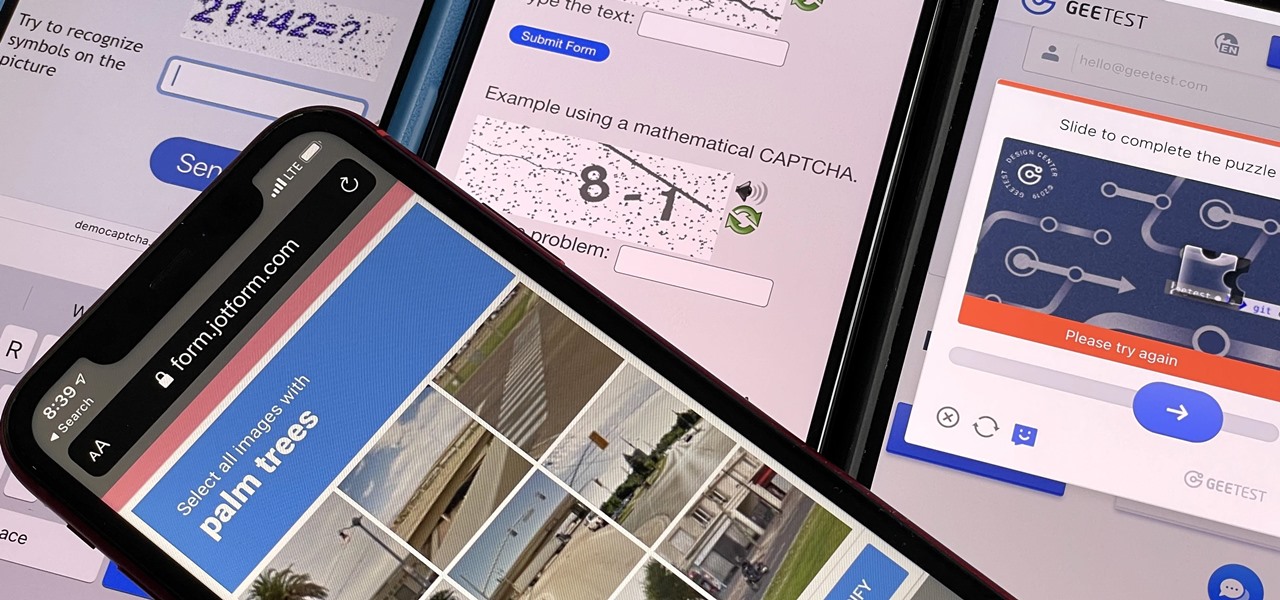
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

Let's face it: standing out in the digital world is challenging. Graphics platforms are either cumbersome to learn or produce generic stock art. A better solution is needed.

There's a lot of résumé writing happening right now. While it's a confusing and frustrating time, you don't have to wait to search for new opportunities. Maintaining a clear head and being proactive in your next career steps are two qualities that are necessary at this moment.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.

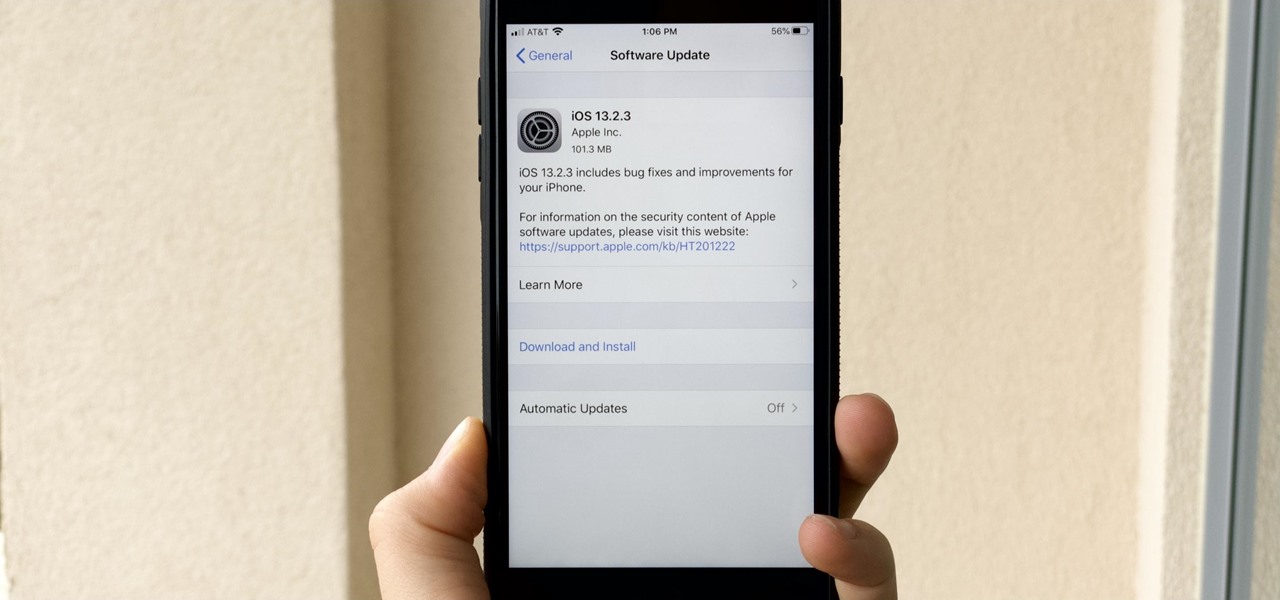
While we all refer to Apple's latest iPhone operating system as iOS 13, in truth, we're well beyond that number. The company has issued numerous updates to its big 2019 release since September, including major steps like iOS 13.1 and iOS 13.2. We've also seen minor updates, like iOS 13.2.2 eleven days ago. Today, Nov. 18, Apple releases another "minor" update, this time dubbed iOS 13.2.3.

QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

If you're noticing issues with Portrait Mode on your iPhone 8 Plus, you aren't alone. Apple confirmed the problem by introducing a new software update Monday, June 10, 17 days after the release iOS 12.3.1, and exactly four weeks after iOS 12.3. The update, iOS 12.3.2, is available only for the iPhone 8 Plus and not other iPhone models, so every other device will still be on iOS 12.3.1 for now.

The new film Brightburn, a horror take on the superhero genre produced by Guardians of the Galaxy director James Gunn, debuted in theaters on Friday, and it has some promotional backing from Snapchat to drive ticket sales.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

The long-awaited augmented reality game based on the Harry Potter franchise from Pokémon GO masterminds Niantic is closer to release, as the developer has begun public beta testing of the app.

London-based developer Andrew Hart has been working on AR navigation since Apple's original ARKit tool was still in beta preview. Now, he's ready to unleash his technology on the world.

Hollywood loves sequels so much that studios and their marketing teams are not too proud to release a sequel of an augmented reality promotion.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

The recent pitfalls and media fallout hitting Facebook hasn't stopped the social media giant from looking to the future.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.