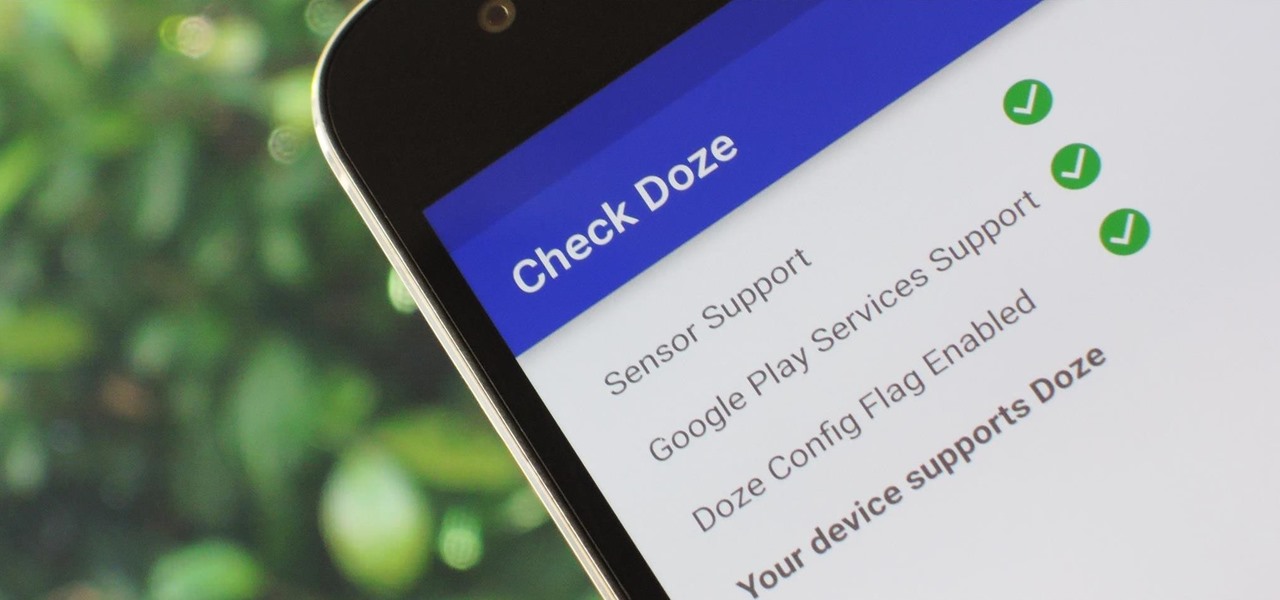
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

Soda bottle jello went viral when the popular YouTube channel AwesomeDisneyToys posted video directions for this revolutionary gelatin confection. I just had to try it out to see what the hype is all about.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

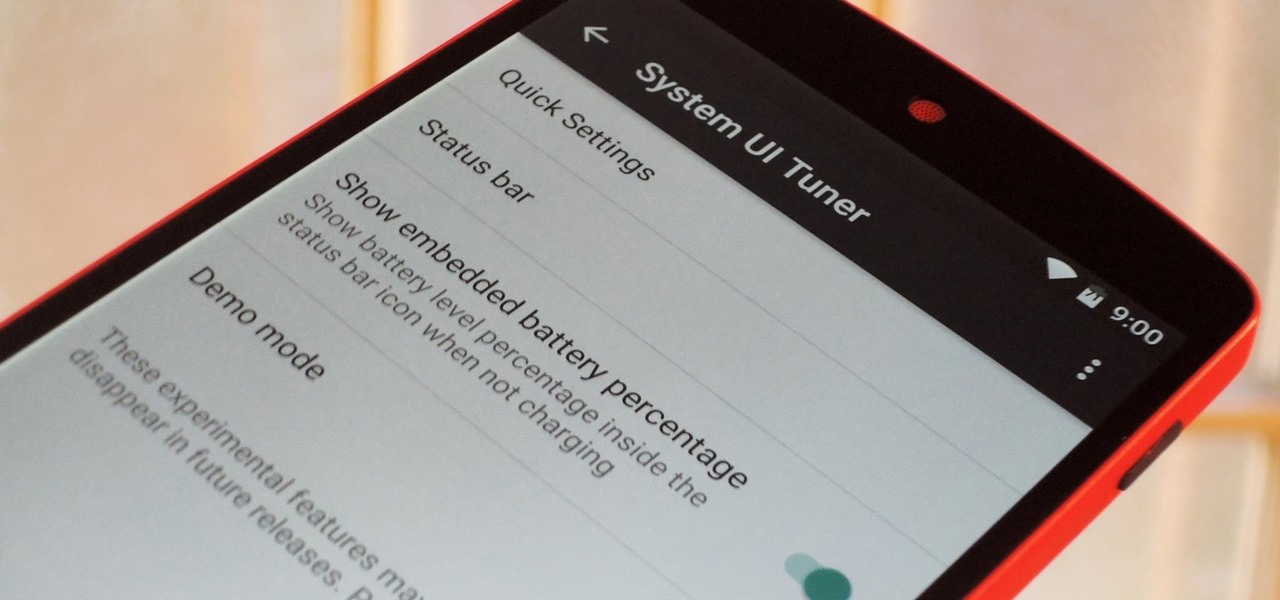
Android 6.0 Marshmallow is bringing in lots of changes to our favorite smartphone operating system, ranging from battery-saving tweaks like Doze to a Now on Tap feature that essentially bakes Google right into every app on your phone. But for folks that like to tweak the interface of their device, a new hidden menu might be the most exciting addition of them all.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

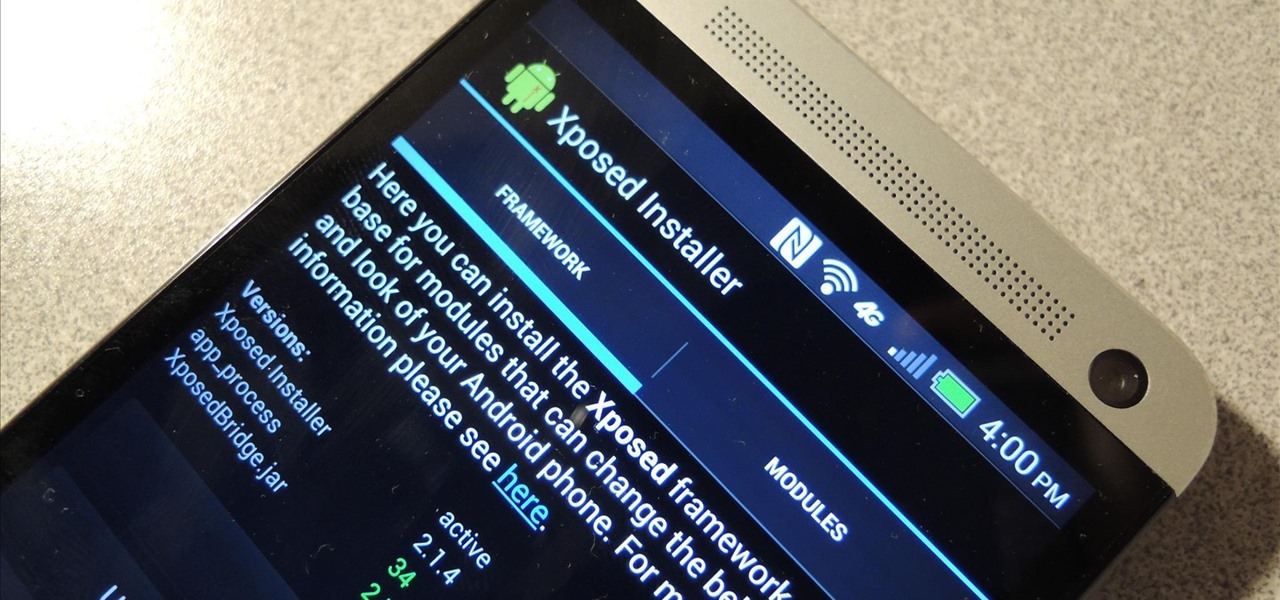
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

If you're a dedicated Instagrammer, you're probably well aware of the humblebrag hashtag #NoFilter, which expresses to other users that your photo is just so damn awesome that it looks like you added filters to it, even though you really didn't.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

When your clutch pedal is dropping down and not coming up again, the cause is most probable one of the cylinders in the hydraulic clutch system. The video will give you a step-by-step tutorial on how to replace both, the master and the slave cylinder. In addition, it is a good idea to also replace the pressure hose in-between the cylinders.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

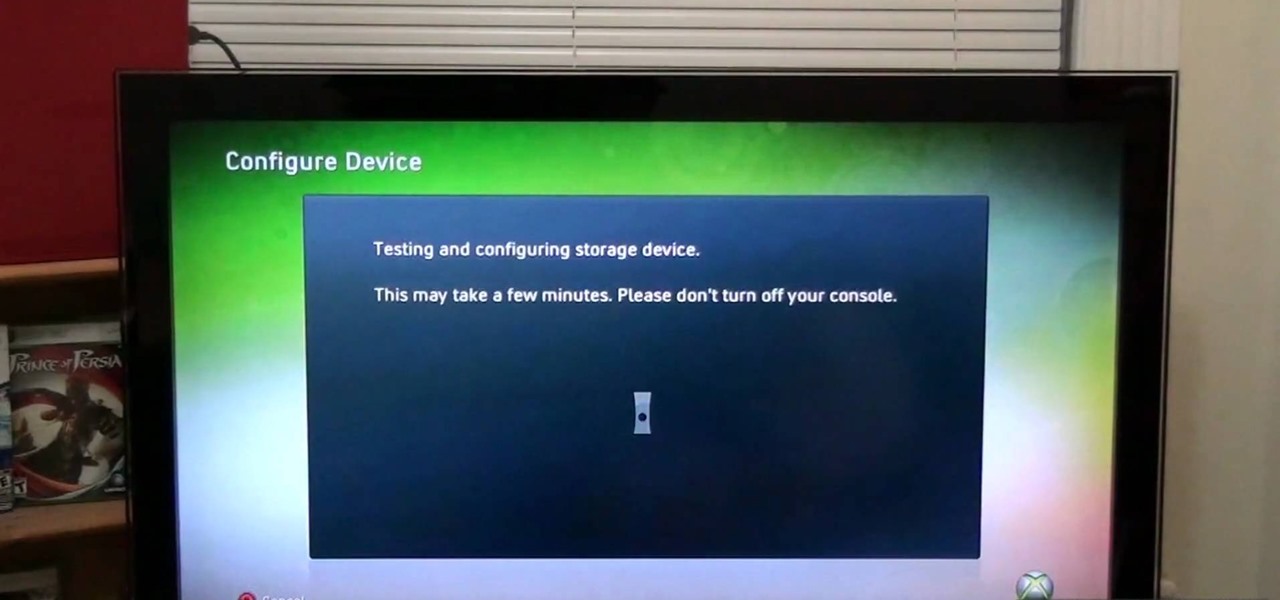
Microsoft recently made it possible to use a USB memory stick to expand your storage capacity. You'll want to watch this video to check out how it's done. Basically, you're going to need an Xbox 360 game system, and a USB flash drive with at LEAST 1G storage capacity. Under that and it won't work. The system will format the memory stick first, so make sure it doesn't have anything important on it. Go for it gamer! Oh yeah, this is also a cheap way to expand your storage too.

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients

If your iPad, iPhone 4 or iPod Touch is already on a tethered jailbreak, this is the tutorial on the new Redsn0w release for all you experienced users. An untethered jailbreak is a type of jailbreak where the device does not require rebooting with a connection to an external jailbreak tool to power up the iDevice. Jailbreaking allows users to get root access to the command line of the operating system, to download otherwise unaccessible extensions and themes, or install non-Apple operating sy...

If you need a dolly for your movie masterpiece, you don't need to go with a professional dolly system. You can save that money for your expensive actors and actresses by building your own DIY camera dolly on the cheap. You'll need some nuts and bolts, PVC pipes, scrap wood, drill bits and a drill, inline wheels and a hammer. This homemade camera dolly will cost you around 65 bucks.

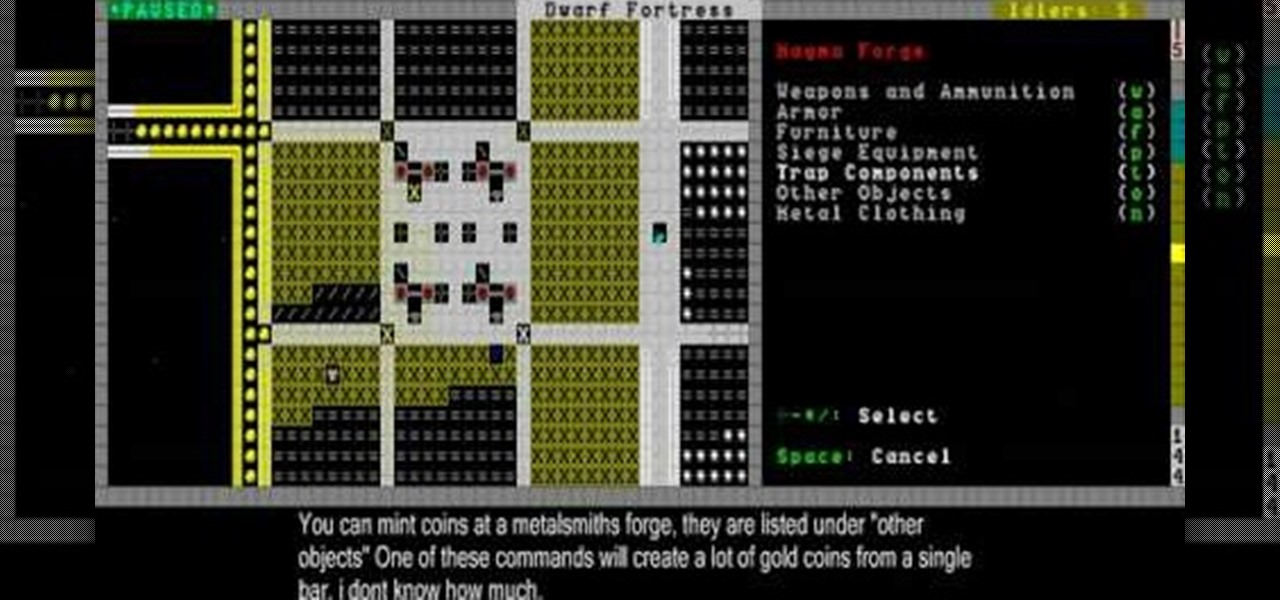
In this video you will see the results of the creator's preivous attempts to use a cave-in to trap demons in their peculiar chamber, then learn how the Justice and Economy systems work in Dwarf Fortress.

The XBox 360 console, especially the older models of it, is not very well-made. There are all sorts of different design errors that can effectively shut your system. This video will teach you how to deal with just one, the unplayable disc error that plagues the disc drives included in the system. You will learn how to fix this error on the Hitachi DVD drive included in many consoles, saving you money and helping you get back to playing games as quickly as possible.

The temperature control onto hot and the fan is turned off. A bleeder is loosened with a 12mm screwing object. A funnel attachment is placed onto the cooling system and the actual funnel placed ontop. A pre-mixed liquid is poured into the funnel. The bleeder valve is then tightened. Another set of liquid is poured into the funnel and some is poured into a reservoir at about 3/4. The vehicle is started and druiven a few steps back and left on, to run at about 2500 rpm until the cooling fan com...

Stir fry is easy to make and always a lively dish to bring to the table. Join Betty as she makes her favorite sirloin steak stir fry recipe with asparagus and rice. It's delicious!

Have you ever gotten a new computer and it works great the first few weeks that you use it? And then after only a few weeks of use it suddenly starts to respond very slow and sluggish. A very common complaint among users of Microsoft's Windows XP operating system for the PC is that it can be a slow operating system. In this video the author shows us numerous tips, tricks, and tweaks on how to substantially speed up a Windows XP computer.

The Wood Whisperer is Marc J. Spagnuolo, a professional and passionate furniture maker, who also contributes to Fine Woodworking and Popular Woodworking. In this video, Spagnuolo shows us how to build a French cleat storage system. It's a very versatile unit, and gives you plenty of storage space without cluttering up a room.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to fix low volume in video with Avidemux on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

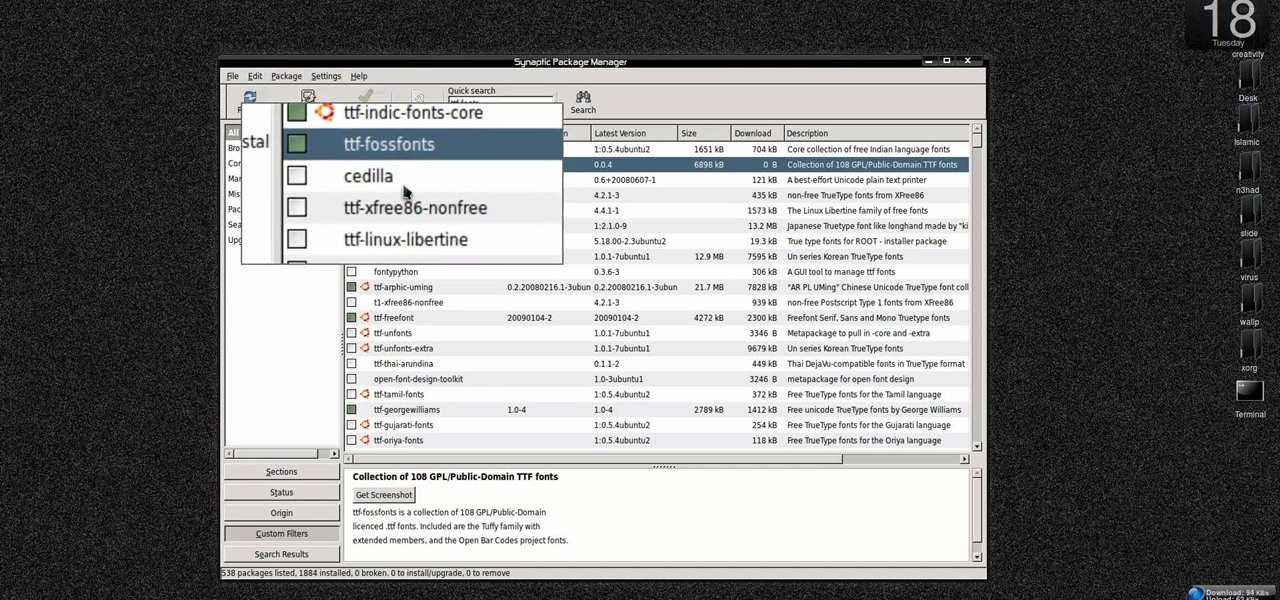
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install 200+ screensavers on Ubuntu Linux.

Build a mineral oil computer aquarium. It cools the system while giving you something to look at.

Matthew demonstrates how to improve the performance of your computer without using new software. To improve your system performance by 15% to 20%, first open up your start menu. Right click on the computer option. Choose the properties option from the right click menu. In the properties menu, click on advanced systems settings on the left hand side of the window. In the system window, choose the advanced tab. Next, under performance click on the settings button. Next, toggle the adjust for be...

How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

This video teaches you how to solve a linear system by mathematically graphing it out. The video starts off with a problem, asking to solve the system, with two given equations. To solve the system, one would insert 0 for x and solve for y in the first equation to obtain a point. Then one would insert 0 for y and solve for x at the second point. Afterwards, insert 1 for x and solve for y to obtain the third point. For the second equation, do the same thing, inserting 0 for x, 0 for y and 1 fo...

Looking to up the ante in the home secuirty department? If you are concerned about the safety of your family and home, consider purchasing a burglar alarm system by following these helpful tips.

Learn how to mount/install a twinplex CP4 chipset cooler into a PC.