Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.
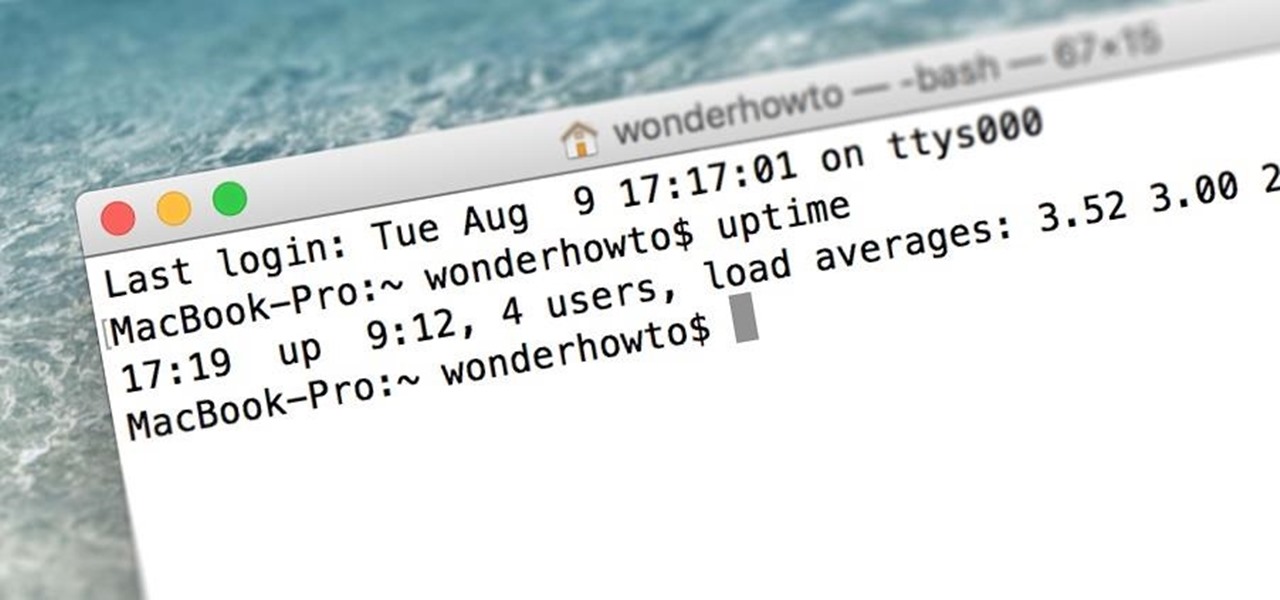
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

After a successful Kickstarter campaign, a new smartphone manufacturer named Nextbit emerged, then released its first flagship device—the Nextbit Robin. The headlining feature of this colorful gadget is its cloud-based app storage, but the phone itself comes with a very polished and sophisticated suite of software.

More proof is emerging that the iPhone 7 won't include a 3.5 mm headphone jack, and damn—it is not pretty. These third-party Lightning-to-3.5 mm dongles were spotted on Chinese site Tama, and they give us a glimpse into a horrifying future in which we have to attach one of these clunky monstrosities to an iPhone just to connect a set of standard headphones.

I've been an iPhone user in the iOS ecosystem for years now after a brief stint in the Android realm. But, I'm also enthusiastic about varying forms of technology in general; I realize that iOS is far from perfect and that healthy market competition is beneficial for all. So, naturally being curious about other platforms, I decided to take Windows Phone for an extended trial run.

For most Android phones, the system clock is set using a protocol called NITZ, which relies on a connection with your carrier to ensure that the time stays in sync. The trouble here is that this feature won't work when you're outside of cellular range, and a lot of times, the carriers themselves have technical difficulties that can result in your phone's clock being minutes or even hours out of sync.

Developers across the U.S. and Canada have started getting their augmented reality headset packages from Microsoft, and so far, everyone's raving about one gaming experience that shatters all doubts of just what the HoloLens can do... RoboRaid.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Virtual reality technology company Oculus VR announced that it will begin accepting preorders for its long-awaited Oculus Rift headset beginning Wednesday, January 6th, at 8 a.m. Pacific time.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).
Welcome back Hackers\Newbies!

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Whether it's delivery drones or getting the U.S. Postal Service to ship packages on Sundays, Amazon continues to remain innovative and ahead of the game, as further evidenced with their mobile app, Amazon Underground.

The day has finally come, and after quite a bit of hype and buildup, Windows 10 is now officially available. The update itself is on a staged rollout, which means it will be slowly becoming available to users over the coming weeks and months, so don't panic if you haven't already received an update notification. Besides, you have until July 29th, 2016 to download your free copy of Windows 10 if you're eligible, so there's plenty of time to get your ducks in a row.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Incredibly tiny in size, splinters can be frustratingly difficult to remove from your skin. If large and not completely embedded, a splinter can usually be extracted using tweezers, tape, or glue, but if it's small and in there pretty good, you'll have to get more creative.

In this episode of In the Kitchen with Matt, I will teach you how to make Amazing cinnamon rolls from scratch. Cinnamon rolls are one of my favorite treats. You can eat them for breakfast, you can eat cinnamon rolls for a snack or as a dessert! These cinnamon rolls are super tasty, super easy to make, and super cheap. Let's dive into the fantastic world of baking and bake some crazy awesome cinnamon rolls.

Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or right-click, but it usually requires special hardware to detect the amount of pressure you've applied.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Korean electronics giant LG maintained a large presence at CES 2015. While their TVs and home appliances were heavily showcased, my interest was primarily on one device—the new LG G Flex 2 Android phone.

Third-party keyboard support, introduced earlier this year by Apple with iOS 8, was initially pretty awesome. I loved playing around with all of the different options available in the iOS App Store, including SwiftKey, TouchPal, GIF Keyboard, and Swype.

If there was anything missing from the notorious YO app, it was Aaron Paul's character from Breaking Bad, Jesse Pinkman, calling me by his signature catch phrase—you know the one.

While the "Hey, Siri" feature in iOS 8 is useful for hands-free multitasking, you can only use the command when your device is actually charging.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

As a picky "liker" on Instagram, I make sure to only double-tap on the photos that I truly enjoy looking at: delicious cheeseburger shots, Siberian Husky snaps, music festivals photos, and obligatory baby pictures that my mom posts from my youth.

Finding a unique wallpaper can be extremely difficult, and even the most dynamic wallpapers become exhausted and boring to look at after a while. Searching for new, interesting wallpapers can become a tedious task, so instead, let's just make our own instead.

Google Now is a quick and intuitive way to tailor your device to work for you and, unlike other personal assistants, provide you with up-to-date information based on search habits, emails, and the general all-knowingness of Google.

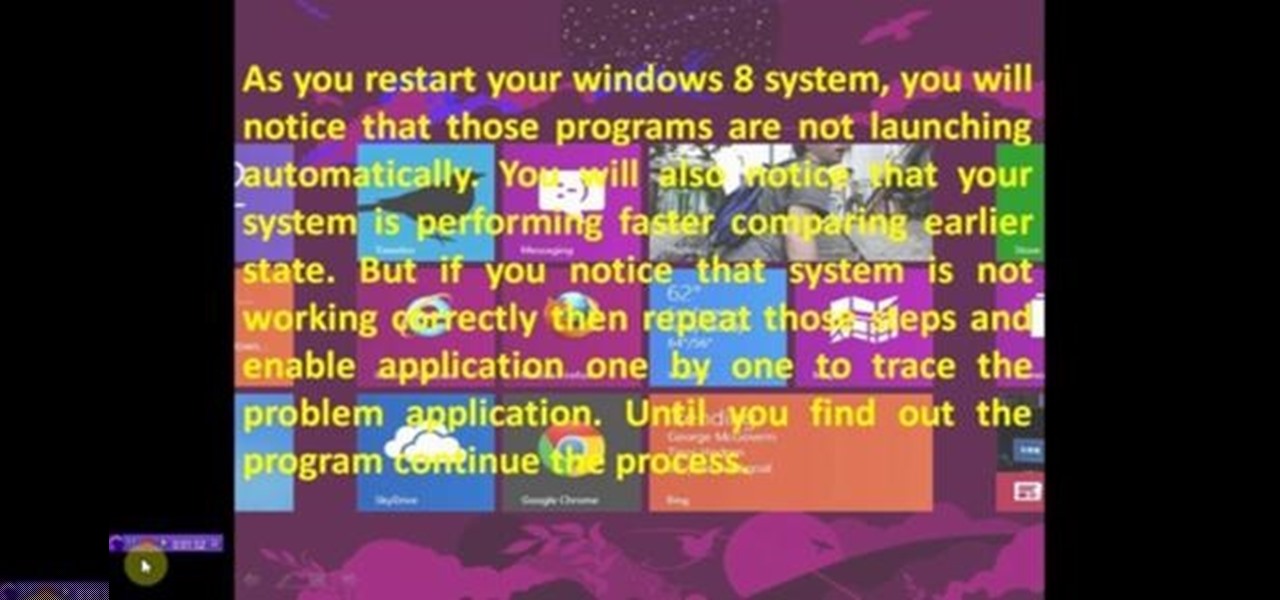
This video will show you how to Speed up Windows 8 System by Disabling Startup Program. This is mostly done by disabling few programs to launch at startup time. Be careful before disabling programs otherwise you may disable few important programs which will affect normal functioning of PC. Watch the video and follow all the steps.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

I don’t buy socks—I get a pack from my parents on Christmas Day, so I’ve got to make sure they last all year. Other than losing them mysteriously in the dryer, the biggest threat to my limited sock collection is a stretched out cuff. Nothing's more frustrating than a loose sock sliding down into your shoe.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

The new rail system might be a small (Read: BIG) problem for those who like using rail systems. See for your self! Check out BebopVox's video:

No matter which brand you buy, microwave popcorn never tastes as good as its movie theater counterpart. Even if you pop it yourself on the stovetop and drizzle it with real butter, it doesn't have the same flavor. That's because movie theaters don't use real butter—their popcorn has one secret ingredient that gives it that distinct taste.