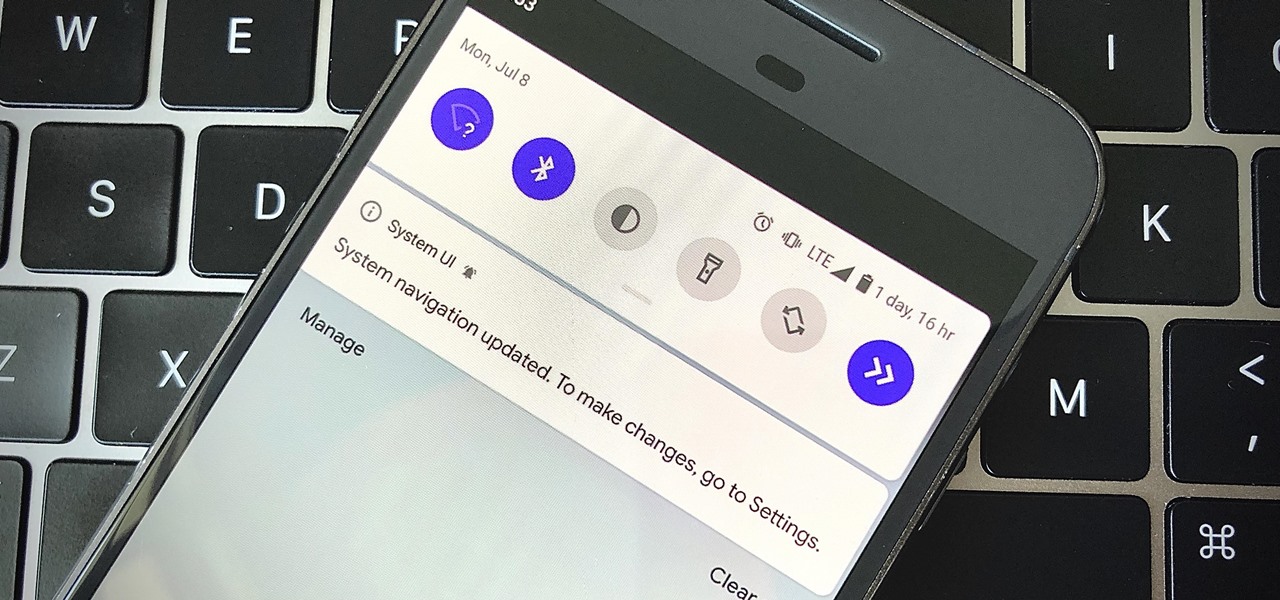
Check out this overclocking tutorial from HotHardware.com! Intel's Core i7 processor offers a significant performance increase over previous generation Core 2 processors. In addition, like the legacy Core 2 architecture, the new Core i7 also has a bunch more headroom for wringing upside performance out of the chip, maximizing value, power and return on your investment with overclocking. In fact, Intel actually built-in a predefined overclocking feature called "Turbo Mode". We explain how not ...

Check out this video to learn how to use the paste laminating system and three part mold-making techniques. This is an advanced process that is not for beginners. This process is for working on medium to large projects, this is a labor-saving process for those who need a large, strong tool in the least amount of time possible. This video also demonstrates three-part mold construction. This process can be used in automotive, mechanical, fine art and film special effects uses.

Patti, the Garden Girl, shows you how to build your own seed starting system in this video series. This system would cost twice as much to buy already made. It is simple and very effective.

In this video tutorial, viewers learn how to quickly troubleshoot memory problems in Windows. Begin by clicking on the Start menu. Type "mdsched" into the search bar and press Enter. The Windows Memory Diagnostic window will then appear. Click on "Restart now and check for problems". Your machine will then be rebooted and will run its memory diagnostics tool. It will look for any issues that may cause problems for your system. Advanced users can press F1 when it starts to specify certain opti...

Taking screenshots in Windows isn't as easy as taking screengrabs in Mac OS X, but Microsoft sure is trying to resolve this issue. Their idea -- Snipping Tool. The Snipping Tool is available for both Windows Vista and Windows 7 operating systems.
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

How to install an aquaduct water cooling system into a PC.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

So, you just updated to Android 10, ready to explore all of the new features Google has to offer. There's just one hiccup — those gesture controls everyone talks about? They don't work. In fact, the option is completely grayed out, taunting you from the get-go. What's going on here, and how can you restore functionality to a staple Android Q feature?

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

The last few months have delivered some great new Magic Leap releases, but that doesn't mean the development team is resting on its laurels when it comes to the platform itself.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Samsung's Galaxy S9 is officially on sale, so we ran through its best software features and even took a look at a few hidden things you might not know about. A new phone is always exciting, but there are a few annoying issues with any device. One such issue is the new persistent Android System notifications in Android Oreo on the Galaxy S9.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

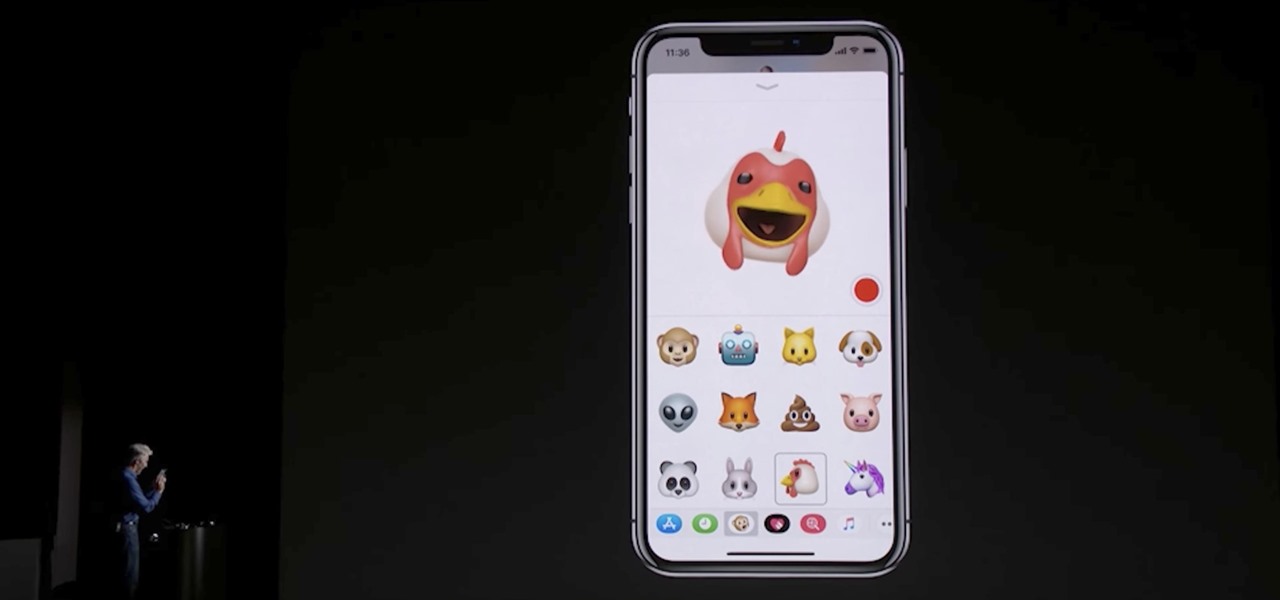
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis may seem at first, the tech behind them is undeniably impressive. In fact, it's possibly the most technically advanced feature of the iPhone X.

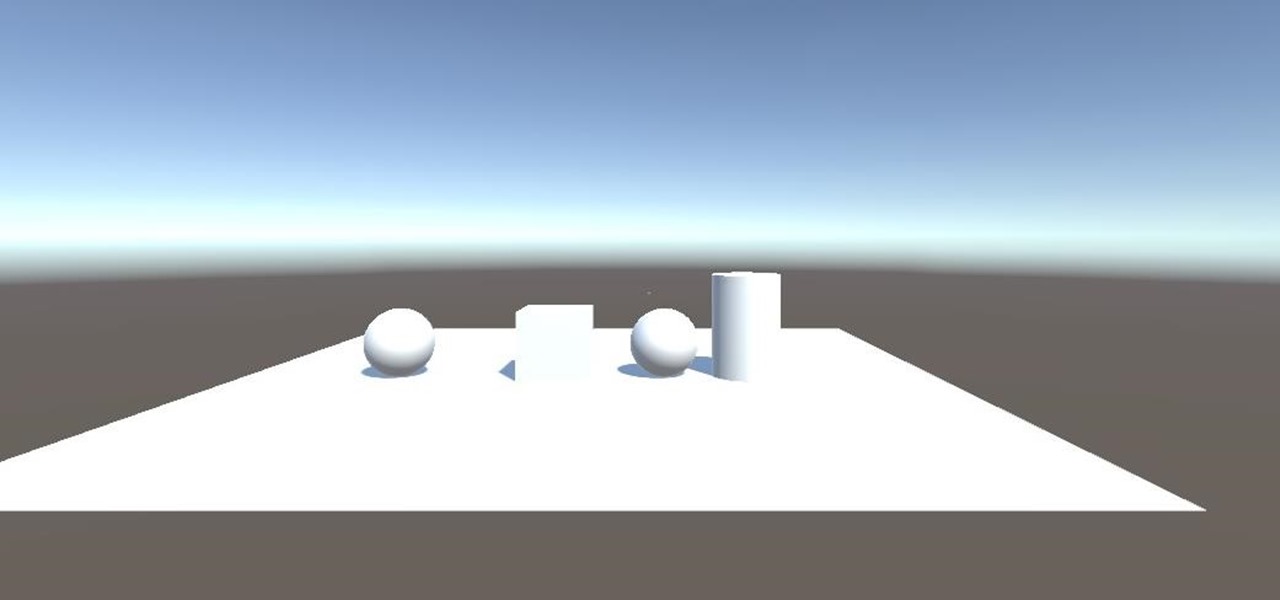
Now that we have installed the toolkit, set up our prefabs, and prepared Unity for export to HoloLens, we can proceed with the fun stuff involved in building a dynamic user interface. In this section, we will build the system manager.

Nintendo's Super NES Classic system, a pint-sized version of the iconic Super NES from the '90s, is highly anticipated in the gaming world. The retro system has already met its fair share of controversies and it's been a long journey to preorder. Finally, the Super NES Classic is officially available for preorder, but it's selling out fast.

Augmented reality headset maker DAQRI has collaborated with the US Navy to outfit the company's Smart Helmet device for use on battleships.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

Waymo revealed more clues about its future business model after it said yesterday it plans to kill its Firefly pod-like car project and focus more closely on offering driverless systems for commercially available car and truck models.

Viral infections have been the focus of attention in the development of autoimmune diseases—diseases where the body's immune system reacts to the body's own cells—because they trigger the immune system into action.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and '90s.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Now that Android Auto and Apple CarPlay have finally arrived, the days of clunky in-dash infotainment systems are coming to an end. Instead of using software created by an automotive company to get directions, stream music, or take calls, we can now get the best user experience Silicon Valley has to offer—all while sitting comfortably in the driver's seat.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.