I've been involved in the Android scene for a very long time and have grown to develop a love/hate relationship with CyanogenMod. While I do like the stability they offer in their custom ROMs, they don't always include the flashy features on top of their vanilla Android base.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

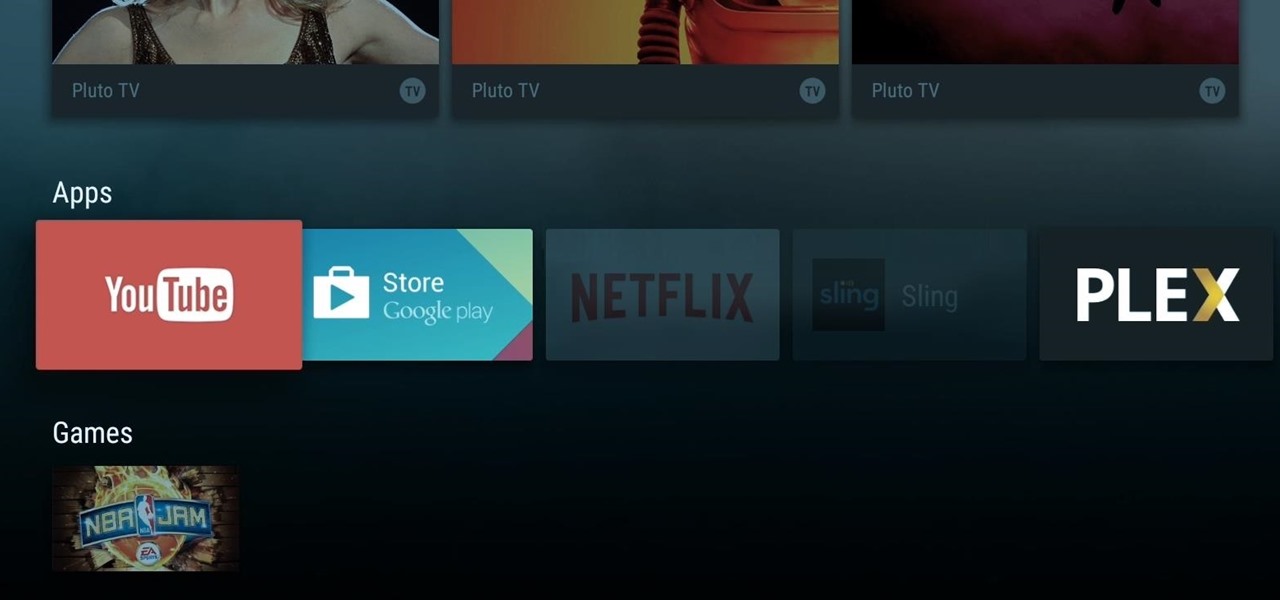
When Google announced its new Android TV platform, one of the features they advertised was a home screen that automatically reorganized your apps based on how frequently you used them. Unfortunately, this feature either didn't make the cut, or is still under development, since the home screen on the Nexus Player always remains static.

Mac keyboards are great when listening to music or watching a movie, since you can control what's playing without going back into iTunes or QuickTime Player. However, when you're using an app like Photoshop that uses the F7, F8, and F9 as shortcuts, it gets pretty annoying to have to hold down the Fn key. Why can't you just hit the back, play/pause, and skip buttons alone?

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

As much as app developers would like to simplify things with icons and visual cues, text is still a huge part of a smartphone's interface. Much of our media consumption is text-based, and while Google's Roboto font is a beautiful typeface, a little variety here and there certainly wouldn't hurt.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

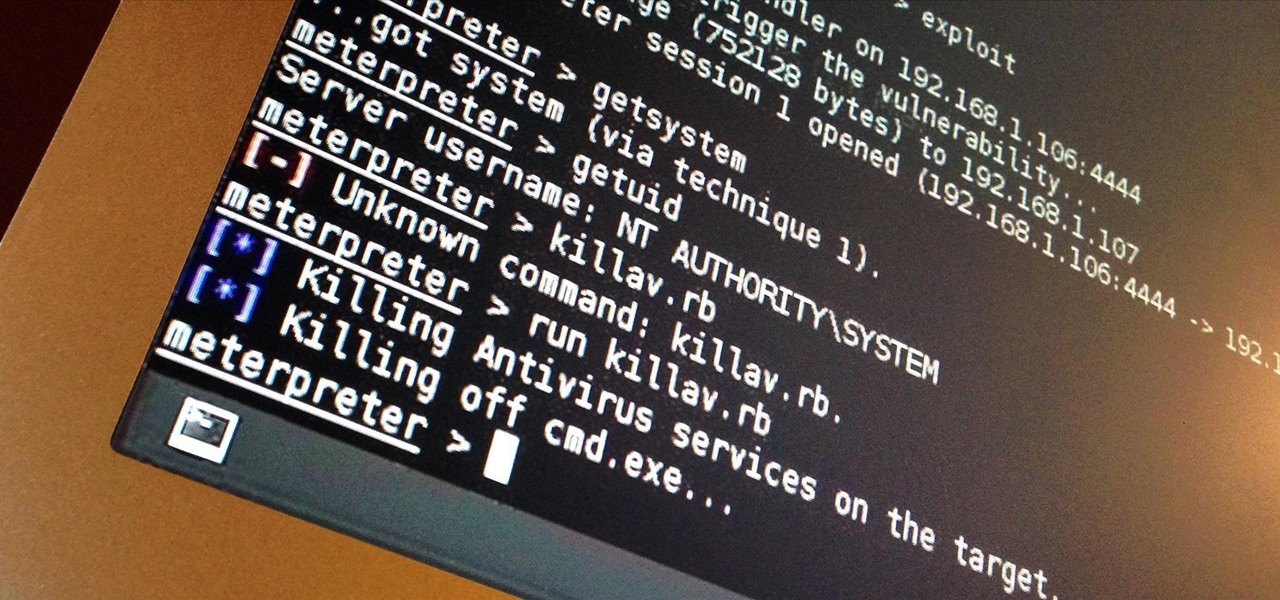
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear Store.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Imagine two stakes in your backyard. Now draw an east-west, north-south coordinate system on your lawn. Measure the east-west distance between the stakes and also the north-south distance. Take the square root of the sum of the squares of the two measurements and, voilà, you end up with the "distance" between the two stakes.

Keys are on the way out. They're clunky, take up precious space, and slow you down when you have tons of identical-looking gold ones on your keyring. Everything we can open with keys can now also be opened with wireless technology in just a click—so why use keys anymore? Sure, you can pay hundreds of dollars for an automated lock system on your house—but why do that when you can build it yourself!

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

In this video we learn how to tie an easy fishing knot system. First, put the line through the hook and pull. Then, take the end of the line and make it come through the loop. Bring this over and then you will have a hole at the bottom of the string. Take the end of the line and put it through the hole around six to eight times to get a strong knot. Then, pull on the main line and you will see the knot glide up to the hook, To go lower, just pull it down. This creates a strong and efficient k...

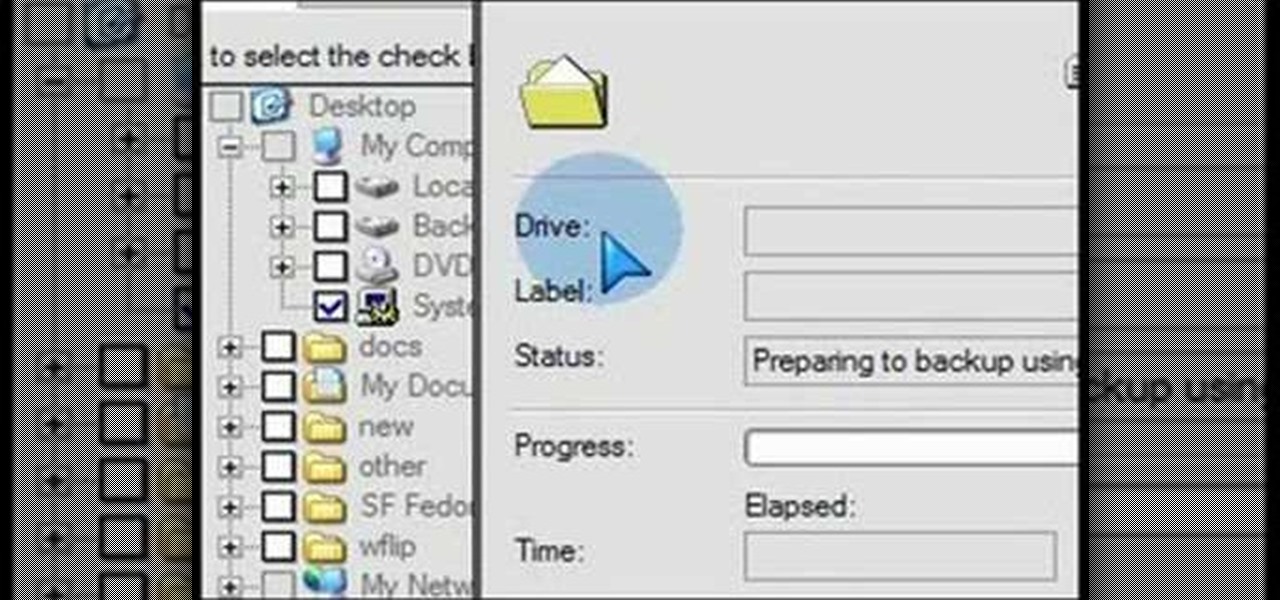
What if your PC crashed? What would you do? Everything would be gone, erased forever, and you'd be in a horrible and stressful situation, especially if all of you homework or work files were stored on your Windows PC. But why even enable yourself to be in that situation? In Windows XP, it's not uncommon to have experienced a corrupt registry or a missing DLL file, or having a blue screen of death.

In this tutorial, we learn how to build your own hydroponics system. To do this, you will need: square line rain gutter, 6x end caps, 3x gutter running outlet, 1x small pond pump, 2 meters pond pump tubing, timber for framework, large plastic container, and gutter leaf guard. When you start, you will need to measure out how tall your pump will need to be, then build the framework to surround it. Then, grab all your gutter parts and put them together. Once you do this, start to set up all the ...

System of a Down. Motley Crue. No matter who you are, a heavy metal song is almost instantaneously recognizable, with bands as diverse as System of a Down and Motley Crue banging out deep, distorted guitar riffs and emphatic beats. The muscal genre of heavy metal is a headache for adults and a form of rebellion for kids, which is why you'll always seen teens rebelling by blaring this music on full volume.

Do you think that you have a vacuum or boost leak on your Porsche 944 Turbo? Would you like to know, but not pay a mehanic a ton of money on something you can do easily? Then are you in luck! This next video tutorial is just what you need.

If you have a damaged sprayer in your dishwasher, don't go looking for a repairman or plumber. This is something that can easily be taken care of in no time at all and is very inexpensive.