
HoloLens Dev 102: How to Install & Set Up Vuforia in Unity
In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.


In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.
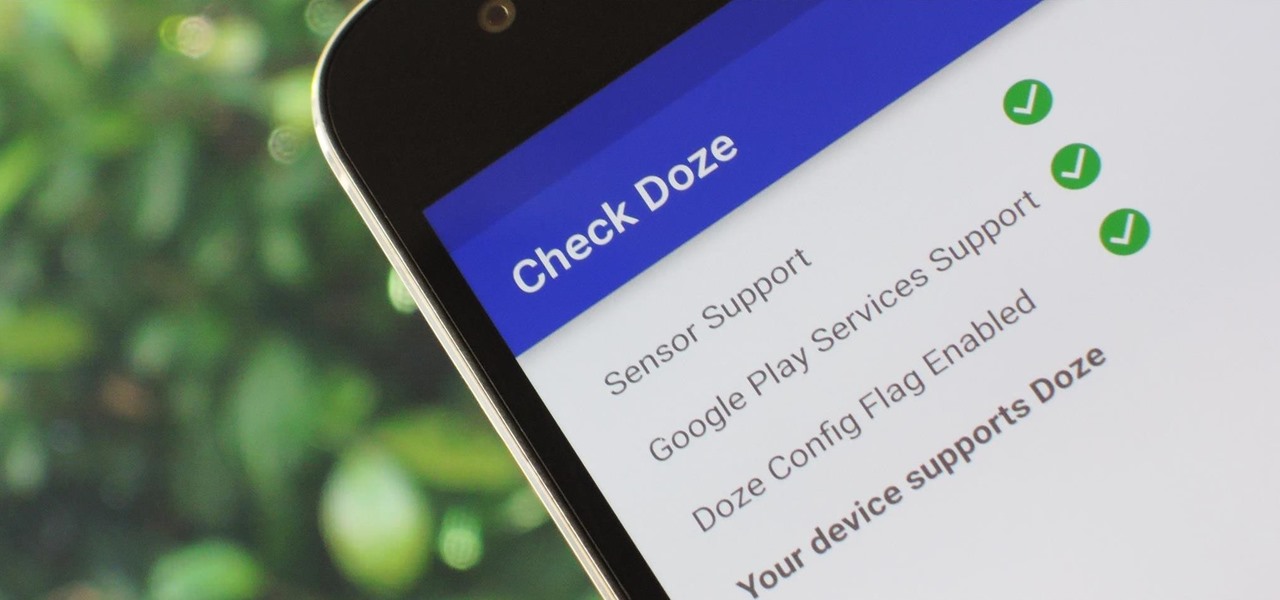
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.
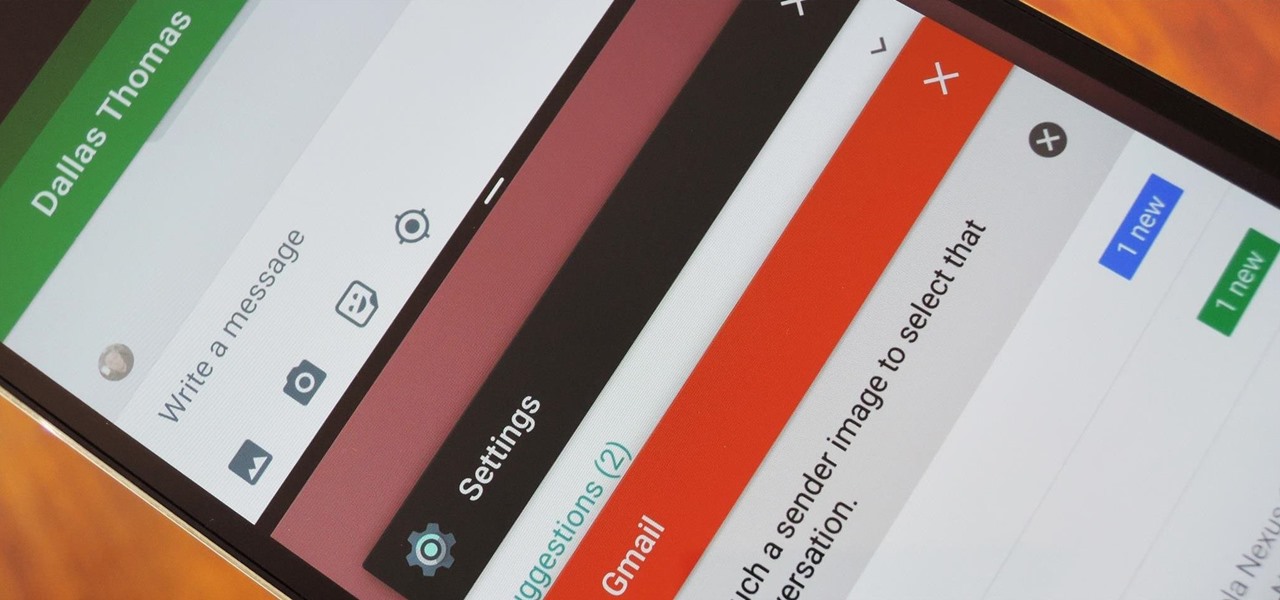
We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!
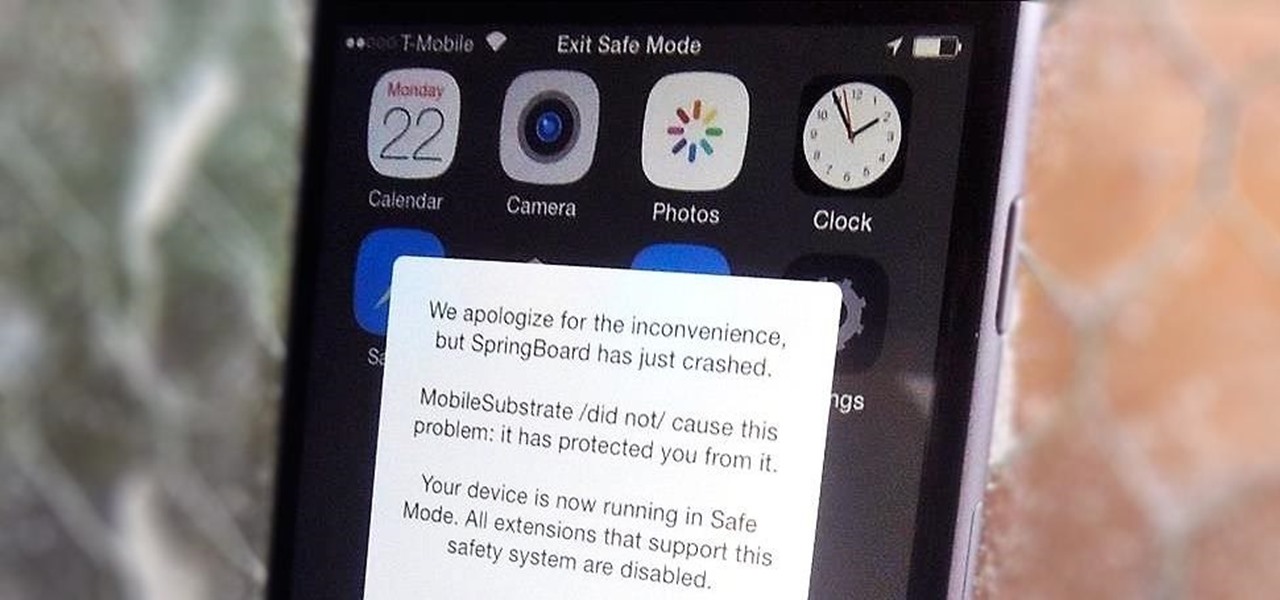
Installing tweaks or themes onto your jailbroken iOS device is a pretty fun and exciting experience, but if you do it for long enough, you're bound to come across a bug that will cause your operating system to crash.

The vague 90-day release window for CyanogenMod 12 has done nothing to stop my craving for Lollipop on my OnePlus One. Luckily, there are other "unofficial" means of getting my hands on it. Since CyanogenMod still gives users a way of building their own variants of their ROM, we can install user-compiled versions of CM 12 pretty easily.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

Every year I wait until the last minute to wrap Christmas presents. I always tell myself I'm going to get it done ahead of time, but it never happens. And the worst thing that can happen when you put it off is running out of Scotch tape.
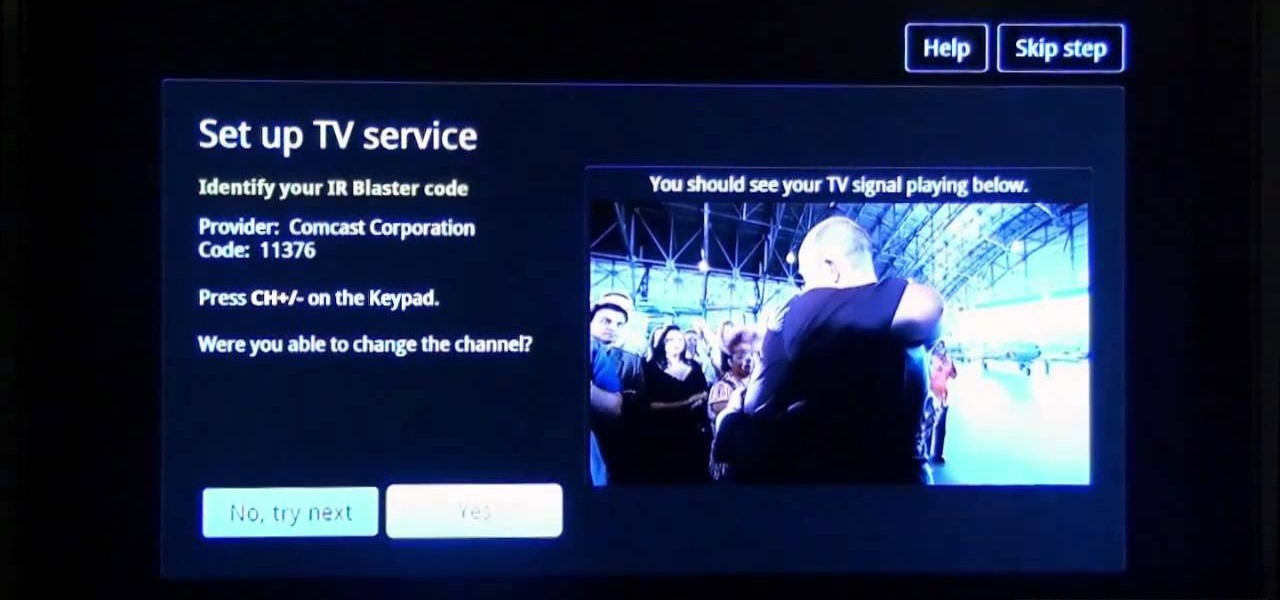
Sony's new Internet TV combines the power of Google TV and television into a neat and accessible package. And setting up your new Google TV is a cinch. This video walks you through the quick setup process for getting your Google TV system going. The player in this video is model NSZ-GT1.

Some people hate wallpaper, but some people love it inside their homes. Those that do will eventually have to deal with wallpaper that will lose it's attachment. It will eventually bubble and curl. Curling wallpaper seams ruin the decorative effect of wallpaper. Eliminate the ugly signs of aging wallpaper with these steps.
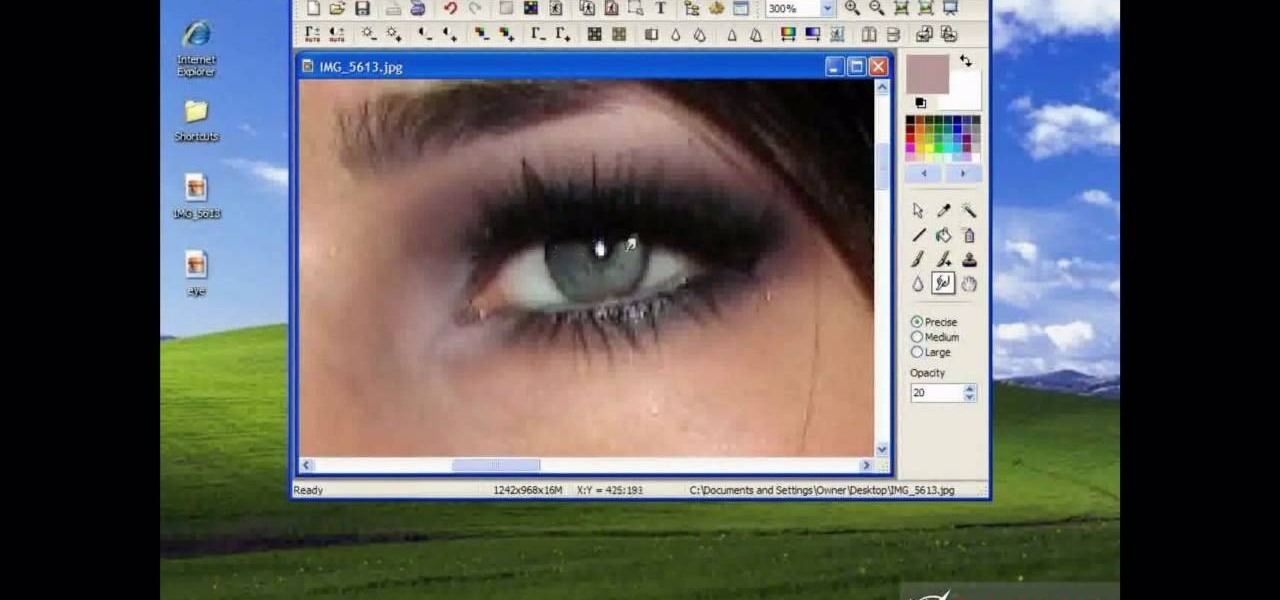
Why waste money on color contacts when you can change your eye color on a software program called Photofiltre? Photofiltre is free and you can manipulate your eye color to whatever shade you'd like in a few easy steps.

In this video tutorial, viewers learn how to make fried shrimp won-tons. The ingredients required for this recipe are: 1 package of won-ton wrapper, 2 cups of chopped shrimp, 1 cup of chopped cabbage, 1/2 tsp of salt, pinch of black pepper, 1 tbsp of corn or tapioca starch. Begin by mixing the copped cabbage, chopped shrimp, salt and black pepper together. Add 1/2 tsp of water to the mix. Users may also add one minced garlic clove. Wetting the won-ton wrap and add in 1/2 tsp of the stuffing. ...

Getting gum in your hair is a huge bummer; its an icky sticky mess to clean. Luckily, the days of cutting the gum out of your hair and ruining your style are behind you! This tutorial will show you how to get that gross wad out with a few products found in your kitchen.

Here is a great idea for gifts for absolutely any holiday, give the gift that everyone likes, delicious homemade chocolate chip cookies! Make these cookies with the whole family and then package in a decorative tin.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now let's talk about another group competition game. This game is known as stack the chair. You can easily get this at one of your local Mal-Mart's, K-Mart's, or Target. These chairs came in a package. Don't forget to divide the group of party guest in half. So let's say you have 20 guests, 10 in one group, 10 in the other and their goal is t...

Watch this video to learn how to make a very easy recipe for homemade pizza. This homemade dough gives great results.
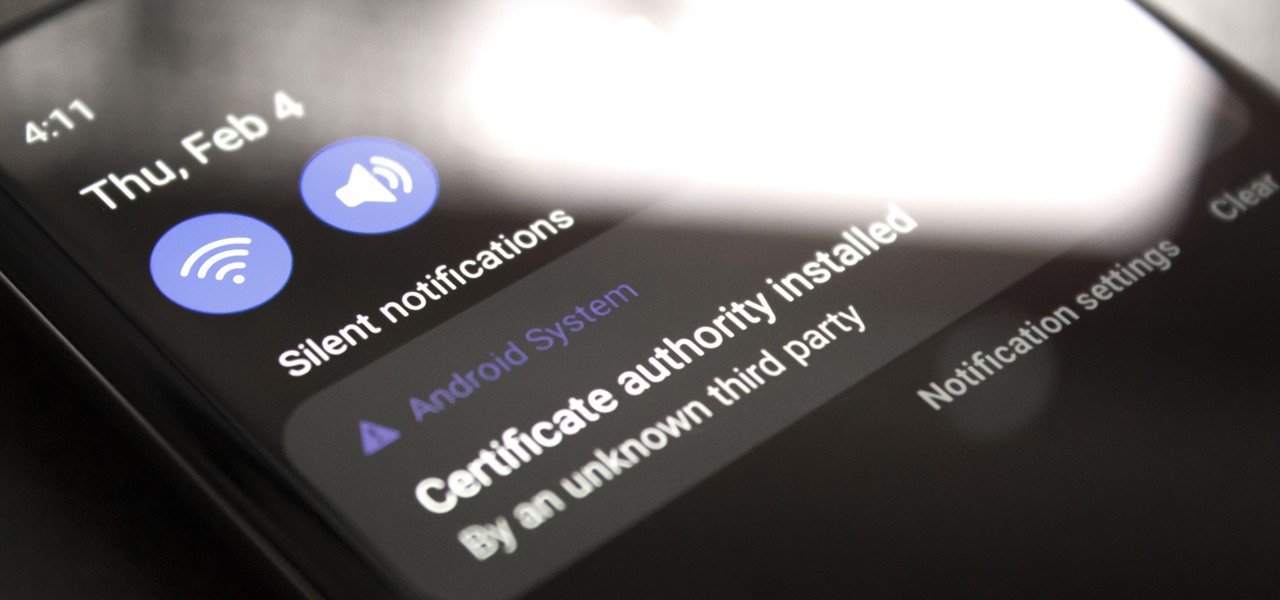
If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

There's an easy way to take your PC to the next level — without any need for a hardware upgrade. The secret is in software that unlocks uses and productivity hacks you never knew you needed. Even better, right now, The Power User PC Software Bundle is on sale for just $59.99. That's 90% off the regular price of $614.
If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.
Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.
Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

The emerging narrative as CES begins is that consumer-grade smartglasses require a heavy compromise in functionality in order to arrive at a form factor and price point that appeal to mainstream customers.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

You may have heard that Samsung Push is an incredible service that all Android users absolutely love. For one, Push provides extremely useful notifications for Samsung apps to assist you in all aspects of your life.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
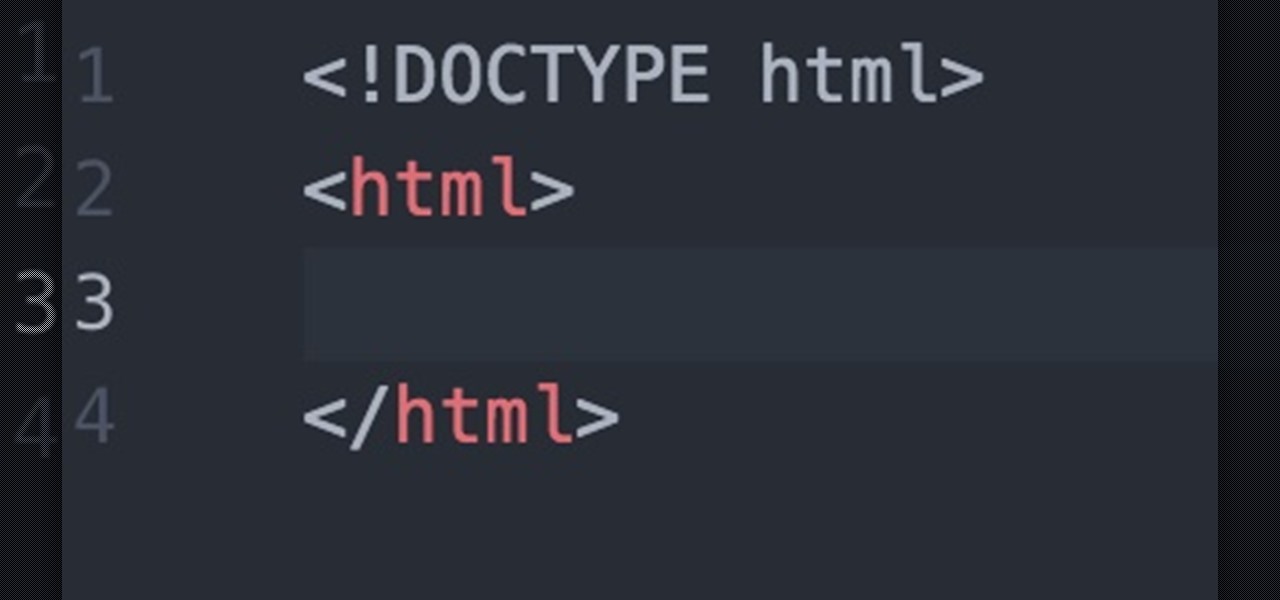
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

As Android's de facto virtual assistant, Google Now lets us speak directly to our phones in plain English to answer our questions and perform many basic tasks. With the app open, just say "Okay Google," then wait for the beep, and ask almost any question.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Finally! A media box that gives you everything you want, in one tiny package. The EzeeCube will allow you to view your pictures and videos while staying organized at the same time.

Sony is ready to get into the micro-console gaming fight, with its PlayStation TV set to debut this fall.

Baked goods are always a popular gift during the holidays. Whether you love to bake or just don't know what else to give someone, homemade goodies are almost always well-received.
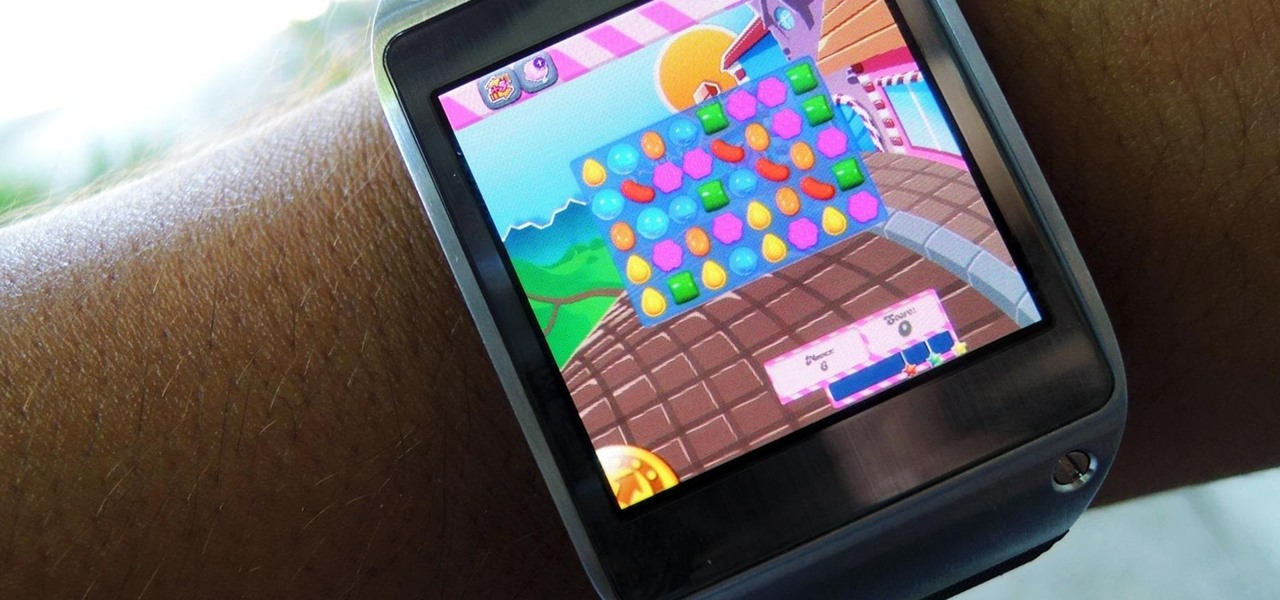
With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.
