This instructional video demonstrates how to make a strawberry pie. She starts with a frozen pie shell. Let the pie crust thaw for about 10 minutes. To make it look homemade, pinch the fluted edges so they are not perfectly even. Next, poke holes all over the bottom and sides of the crust with a fork. Bake the plain pie crust in a 350 degree oven for about 15 minutes. To prepare the filling, put 1 cup of sugar and 1 cup of water into a pan on the stove, mix 2 tablespoons of cornstarch with a ...

Things You'll Need: Measuring spoons, 5 zipper plastic sandwich bags, 1 oz. lagniappe water, 4 large cloves of garlic (cut in half), Zatarain's Garlic and Onion Liquid Shrimp and Crab Boil, 3 bay leaves, measuring cup, 2 lemons, 5 oz. salt, ice, large pot, 5 lbs. large shrimp (2 to 3 oz.), cayenne pepper to taste, 1/2 stick butter (4 tbsp.). Step 1: Fill the pot 2/3 of the way full with water and place it on the stove. Step 2: Turn the heat on the stove up to the highest level. Step 3: Rinse ...

Make a Kraft Philadelphia New York Cheesecake with this video tutorial! First, line a pan with foil. Pre-heat your oven to 325.

Paula creates a no-bake tiramisu dessert, perfect as a summer treat. Follow along and get this delectable recipe for a lime blueberry tiramisu that doesn't require you to turn on the oven. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting. You'll lo...

Lemon chicken over fettuccine noodles with plenty of fresh basil, now that makes for a great salad. Follow along with this cooking how to video as Paula Deen shows you one of her favorite pasta recipes. Try making this recipe for chicken fettuccini pasta salad.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

You have an abundance (or scarcity) of alcohol, liqueurs, and chasers, but don't know how to combine or mix them together to produce some kind of enjoyable concoction for friends. What do you do? Mix things you think will taste good together? They probably won't. There's rules about clear alcohol vs. dark alcohol and how they pair with juices and sodas, so what's the best way to know what goes well with what?

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

Welcome back my fellow hackerians, Today i'm going to tell a bit more about the famous DDOS thing. And on top of that we're going to DDOS a website.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

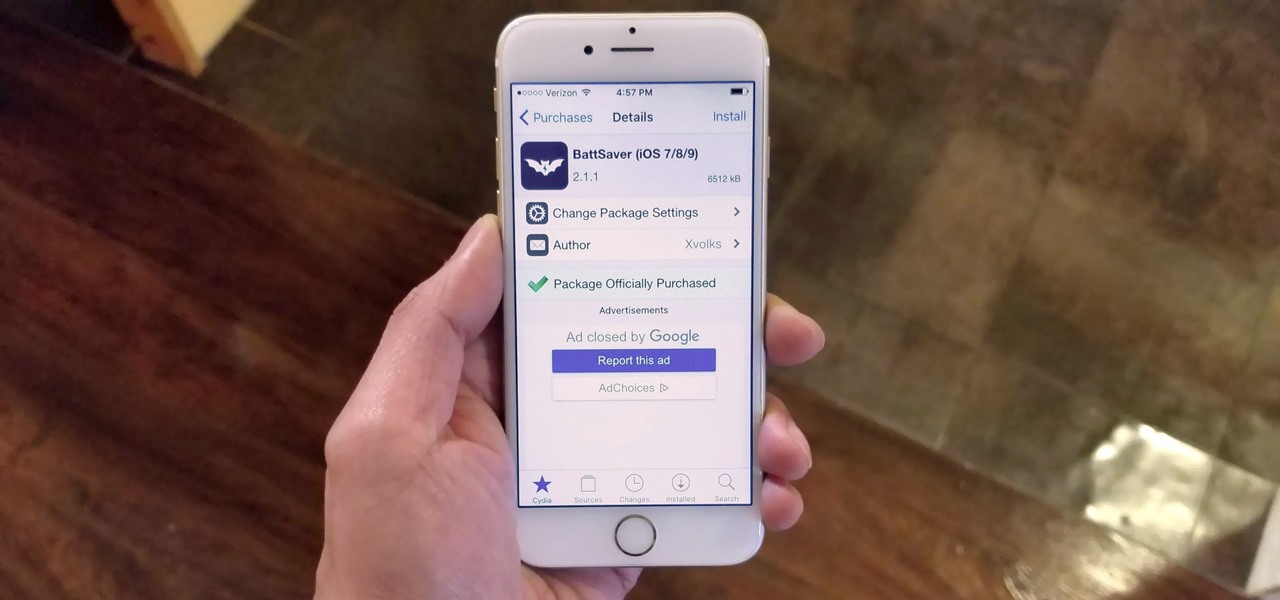
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

No offense to T-Mobile, but if you head over to their support page for the Samsung Galaxy Gear, you get the information below on how to take a screenshot of your smartwatch. Oh, thank you for that.

It doesn't matter if you're a chocolate lover or just a casual chocolate eater, these chocolate brownie trifles are extremely addictive! If you whip up a batch of these trifles, you're sure to be the king (or queen) of the potluck or dinner party. No doubt about it. Everyone can enjoy a sweet chocolaty dessert.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

For as long as I can remember, I've always sucked at wrapping presents. No matter how careful I am, my gift-wrapping usually ends up looking like a toddler did it, so I'm always looking for easy ways to spruce up my packages.

Checkra1n is by far the best way to jailbreak A7- through A11-powered iPhones on iOS 13 and later, but it's not without its downsides. Besides the lack of Windows support, the tool limits your choices to Cydia alone. With a little elbow grease, however, you can easily replace the app with Sileo for a more streamlined jailbreak experience.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Learn how to make UVs in Blender and import the new UVs to Zbrush's High res model. This is important since Zbrush uses AUV's which are not recognizable by other packages or game engines. Once you have proper UV's, you will learn how to create the clothes (superhero costume) for a character.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Since Android is an open source operating system, that means anyone with a little know-how can download, view, and even alter its underlying code base. Manufacturers do it all the time, which is how we end up with skins like TouchWiz and Sense. But when Android's awesome third-party development community gets their hands on this code, we end up with custom ROMs like LineageOS and MIUI.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

Verto Studio 3D is a 3D modeling package that has been in the works for a while now by Michael Farrell, the owner of Verto Studio LLC. Farrell has been working toward bridging the gap between XR 3D modeling and what we have become accustomed to with desktop 3D modeling packages like 3D Studio Max, Maya, and Blender.

Carrier-branded Galaxy S8 models come with a ton of bloatware that you usually can't get rid of without rooting. If you dig a little deeper, however, there is a way to debloat your S8, and it's relatively hassle-free.

Frosting, for many, is the best part of the cake. There's not much to dislike about it, after all—there's a type of frosting for every person. Whipped frostings for those who like it light, dense buttercream for indulgent sugar fans, cream cheese frosting for the tangy crowd... and so on. But I'll bet you've never made or tried frosting made with Jell-O packages before! Infusing your frosting with the sweetness and bright color of Jell-O changes both its taste and appearance, and using Jell-O...

Exclusive to the Samsung Galaxy S6 Edge, "Information stream" is a screen feature that lets you see quick, at-a-glance information with a simple swipe while the screen is off. It also supports plug-ins, or additional streams of information that can come from third-party sources. So developers are starting to come up with nifty little add-ons for Information stream, and the team at 3C has some cool new system feeds that might come in handy.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Your smartphone has a ton of ringtone options built in, but ringtones haven't really changed much in the past decade, and it's definitely not cool to hear someone in the supermarket with the same lame ringer. While replacing the stock sounds with a song of your choosing is the best way to keep your phone personalized, why not go a step further using a video?

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

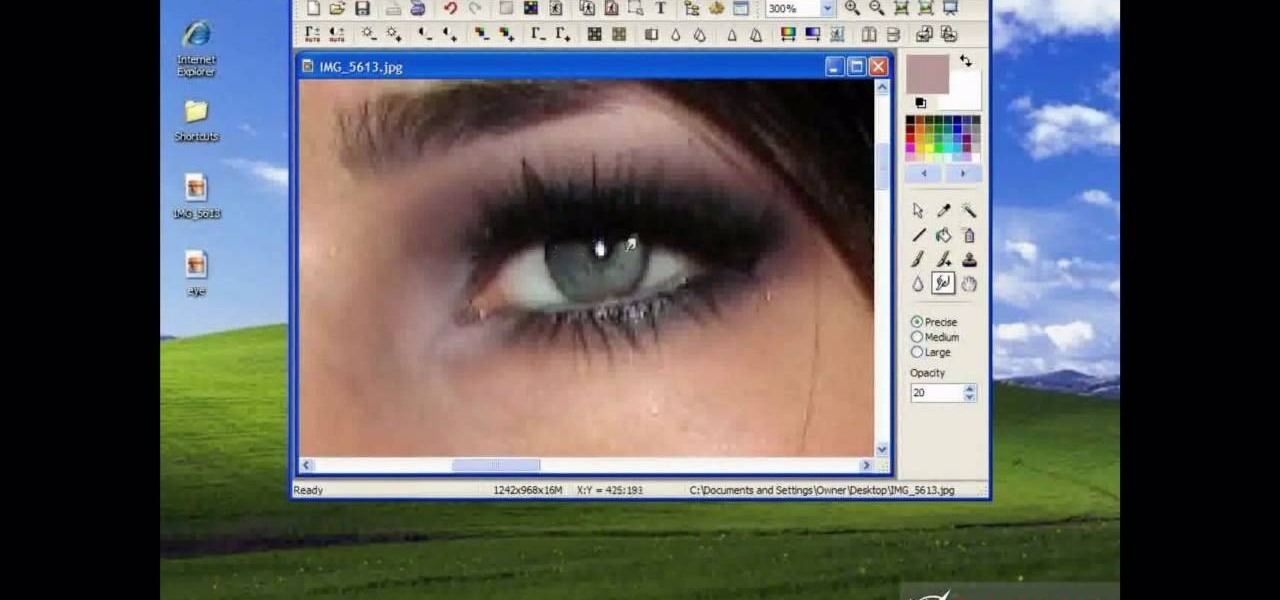
Why waste money on color contacts when you can change your eye color on a software program called Photofiltre? Photofiltre is free and you can manipulate your eye color to whatever shade you'd like in a few easy steps.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.