Instagram just added another nail in the coffin for Snapchat. It looks like it's the AR platforms final hurrah as IG has snapped up the app's last good feature: its AR selfie filters.

In a series of news about the OnePlus 5, the company posted its first teaser of the upcoming device on its Weibo account. According to GSM Arena, the teaser doesn't show us any sneak peaks of what the phone might look like — co-founder Carl Pei took care of that — though, we are greeted with the caption "Hey Summer! Give me five!"

Last week, the internet was ablaze with talk about the Galaxy S8's home button, because it subtly changes positions without the phone alerting you. This feature was included to stop burn-in issues with the screen, and the general consensus from tech sites was the screens would not experience any burn-in at all.
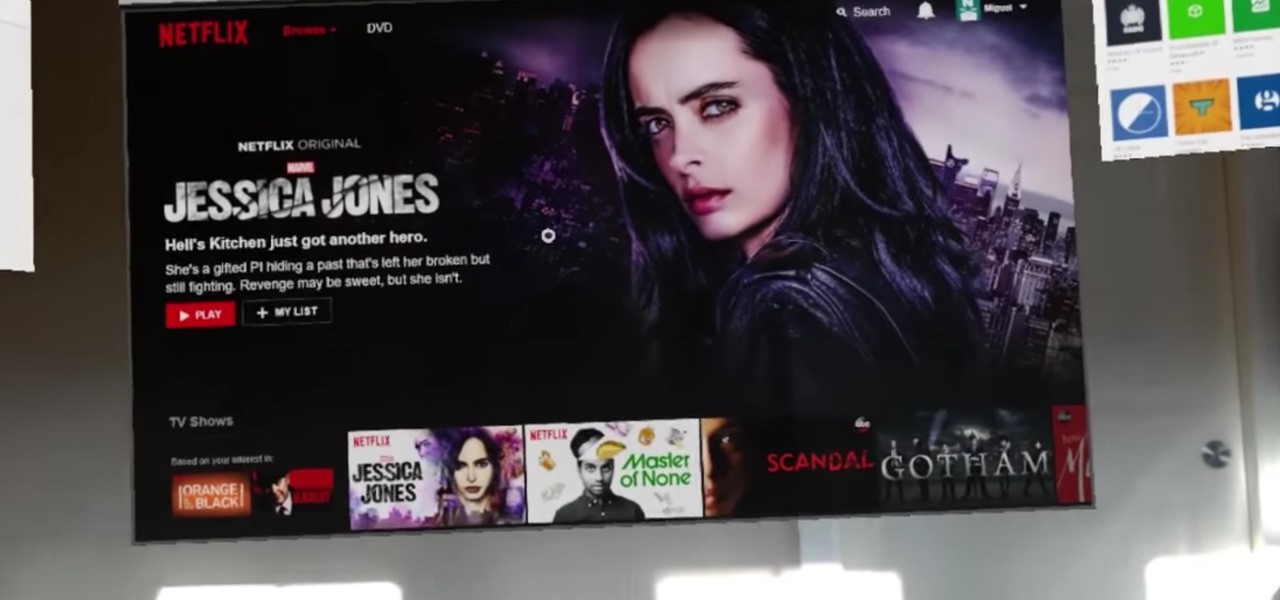
Alright, fellow HoloLens code wranglers, load up your word processor because it's time to spruce up your résumés. According to a report by Variety, Netflix is looking to hire a new Senior Software Engineer — and Windows and HoloLens were mentioned as an end point.

During the last few months, WhatsApp's Google Play Store ratings have been tanking—all the way down to an average of 3.4 stars from the instant messenger's usual average of 4.1. Within the last week, though, WhatsApp has received thousands of seemingly fake 5-star reviews that have bumped up the company's overall average to a 4.4.

In an early morning blog post, Microsoft announced the expansion of the Microsoft HoloLens Agency Readiness Partner Program. This announcement comes on the tail of an expanded HoloLens release over the last few months to many countries outside the initial US and Canada.

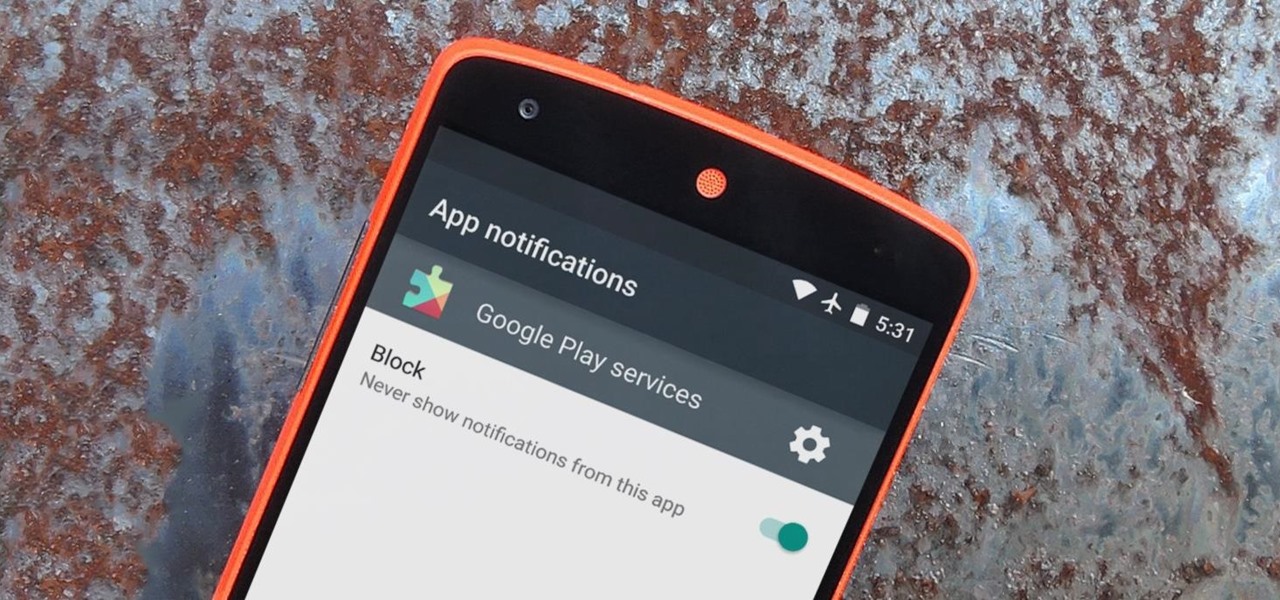
Android's notification system is quite robust, especially now that Google added bundled notifications and quick reply features to Android 7.0 Nougat. However, things can still get quite cluttered when you have several unread messages, which fills your status bar with icons and makes your notification tray take up half of the screen by itself.

Leave it to some lazy college kids to attempt to figure out a way to brew a pot of coffee without leaving the couch.

Frosty the Snowman is a fairy tale they say, but this microscopic snowman is very real and just broke the record for the world's smallest snowman. (Though, it's not Guinness-official yet.)

Immigration and immigration policy are some of the biggest discussions happening in international and domestic politics right now. From building walls to opening borders, a definitive plan has not been made about how to deal with the large number of people who are fleeing their home countries in hopes of a different life.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Have you ever had one of your Android games post a notification in a lame attempt to remind you to play? This is becoming a common practice these days, and to me, it's about as annoying as a Best Buy blue shirt when I'm just trying to check out the latest TVs.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

The bumper for bObsweep Pethair and Standard are installed the same way. It holds the sensors that allow Bob to see any obstacles in his path. If a repair of the wall detection sensors is needed, the steps for replacing the whole bumper are the same when working on either bObsweep model.

White rice is cheap, filling, and tasty. No wonder so many countries in the world rely on it as a mealtime staple, including most of East and Southeast Asia. Alas, because of its relative lack of nutrition and its high calorie count, consuming lots of white rice regularly also puts people at risk for diseases like diabetes and obesity.

Line breaks signify not only the ending of one line of thinking, but the beginning of another. We use them to emphasize points, to fragment information, to shift tone, and more. They're important in getting our message across properly, which is why I'm always disappointed when I can't insert a line break into my masterful Instagram caption.

In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

Reddit is home to tons of fun and unique content. A starting point for the various memes and videos that eventually make it into your Facebook feed, you could seriously spend all day just browsing different subreddits and not get bored.

It's time to enjoy one of America's longest lasting favorite pastimes. No, not baseball—pranking our friends! With the internet currently overrun with countless pictures and memes of cats, there's no way for your feline-hating friends to surf the web without coming across a kitten or two. But things can get worse for them. Way worse...

Love making gifts for your loved ones? Here is a tutorial that shows you how to make a play doh rose. It's really easy and fun to make.

If mainstream media has taught us anything, it's that being beautiful can get you ahead in life. The notion isn't necessarily correct, but it's what the general consensus accepts and it seems to hold quite a bit of weight (no pun intended) in the western world.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Facebook makes it easy to show how much you appreciate a funny status, great picture, or cool news article using their iconic "thumbs up" button, but what about those terrible jokes and annoying baby pictures? Where's the "thumbs down" for that crap?

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

While browsing the internet on your Samsung Galaxy S4, you've probably scrolled to the bottom of a very long webpage, Twitter feed, or down into the abyss of some other app. Depending just how far down you've scrolled, it can be a test of your patience (and fingertips) scrolling back up to the top.

The Google Play Store exists so you can download as many apps as your heart desires (and as your memory can hold). Sure, you may only use them once, but it's your choice—and isn't that what life is really about? With that said, the Samsung Galaxy Note 2 already comes with a ton of preloaded apps from Google, Samsung, and your device carrier, like Yellow Pages and Google Earth—both of which I never use. So why is it that Android won't let me remove or uninstall them?!