This is the end of the Xbox 360 game Darksiders. It's the last level, the last quest, your last mission… the Destroyer. You'll need to summon Ruin to stand a chance against the Destroyer. Hold the Focus button to target lock onto the creature so you can keep in in view as you move around. The idea is for you to ride in close enough to the dragon and slash it with your Armageddon Blade. Watch out when you see the Destroyer's front claws glow red as this means he's coming to slash at you. Eithe...

A car that needs to be jump started is going to make a clicking noise but things such as the lights and radio will not turn on. To jump start the car first you need to line the cars up so that the batteries are in line with each other. You will need a working car to jump the car that has the dead battery and a set of working jumper cables. Make sure both cars are completely turned off. Make sure that you keep the two sides of the jumper cables a part. You don't want the two sides of the cable...

Defeating the Ashland level of Darksiders on the Xbox 360 means getting past Tower A, Tower B, Tower C, Tower D, The Caverns, The Ash Field, Fracture Cannon, The Arena, Abyssal Gladiator, Leviathan's Drift, Stygian and lastly… the Soul Bridge. Before you lies an ash field. This ash is to thin for you to Dash in and makes moving around in it difficult. On top of that, a giant sand worm or Ash Titan, roams around freely. This massive creature will home in War as soon as he touches the ash groun...

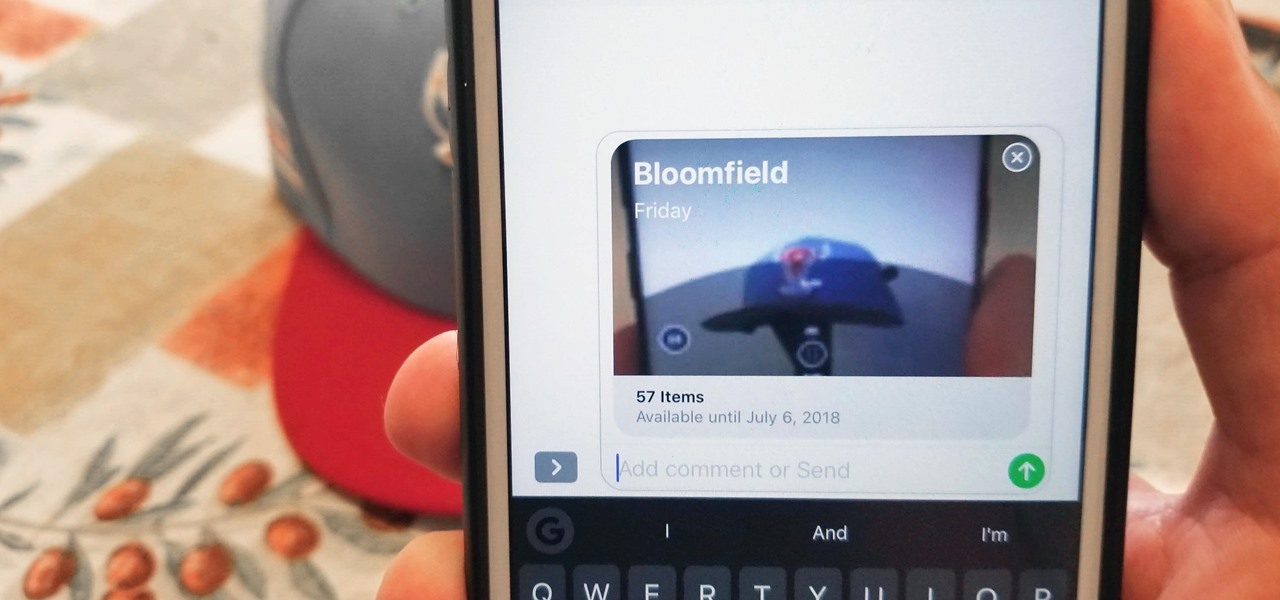
In the Xbox 360 game Darksiders, you'll eventually have to play the Iron Canopy level, which consists of The Seesaw, Webbed Floor, Two Lifts 1 Bomb, Loom Wardens, Broodmother, Silitha and Return Silitha's Heart. War will be ambushed and captured as he enters the Iron Canopy. When he comes to, you'll find him hanging from a spider web. Tap the Action button to break free. Make your way around to the left to discover a Soul Chest in hidden nook behind your starting location. Now cross the webbe...
There's plenty of action on this level of the Xbox 360 game Darksiders. In the Hollows, there's Gas Mains, Tremor Gauntlet, Three Platform Room, Turntables, Pump Room, Griever, and Chronomancer. You enter way looks to have once been a train station. As you approach the Redemption lying on the ground you'll be ambushed by the Griever. Quickly pick up Redemption and begin to alternate between rapid fire shots and charge shots. You need to aim for the blue glowing belly of the monster. Dash arou...

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Keeping your friends up to date is one of the reasons chat apps exist in the first place, but sometimes we're not available to respond to every message or to let all of our contacts know what we're up to. That's where status updates come in handy, and the feature has finally found its way to Signal Private Messenger.

You don't need to take screenshots or make screen recordings to save photos and videos from other users on Instagram. While Instagram doesn't offer an official way to download others' posted content, dozens of shortcuts are available for iPhone that can do just that. But which one should you pick?

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

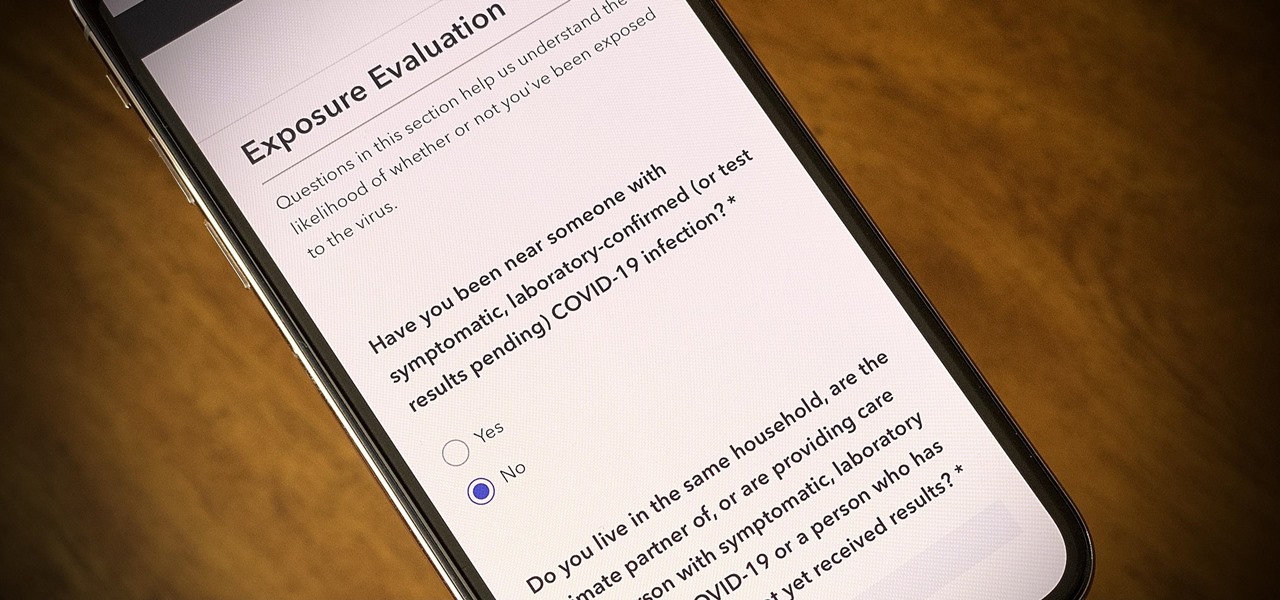
One of the scariest things about the COVID-19 virus is that you can show no symptoms but still be infected (and contagious). Naturally, we all want to know whether we're carrying the new coronavirus, but if you're showing signs of COVID-19, how can you be tested to know for sure? Websites are popping up to help with that, screening for symptoms, and directing you to a testing site if needed.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

Just when we thought the AT&T partnership with Magic Leap wouldn't really take off until the latter launched a true consumer edition of the Magic Leap One, the dynamic duo jumped into action this week to offer the current generation headset to customers.

When you need to know how to get somewhere, Google Maps is the app to beat, but the king of navigation doesn't want to stop there. Google aims to make its navigation app for more than just directions, as made clear by its recent feature that lets you follow businesses in the app. Combining timely news and events posted by local businesses with real-time transit seems like the perfect match.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

Niantic's most successful app, Pokémon GO, has become the first app to integrate the company's Real World Platform, the developer's AR cloud technology that enables multiplayer AR, persistent content, and occlusion with physical objects.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

While there aren't as many improvements compared to iOS 11's Photos additions, the tabs menu in Apple's updated Photos app for iOS 12 was revamped to include "Memories" inside a new "For You" tab that also houses featured photos and effects suggestions. This is also where you see sharing suggestions and all of the albums others have shared with you.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

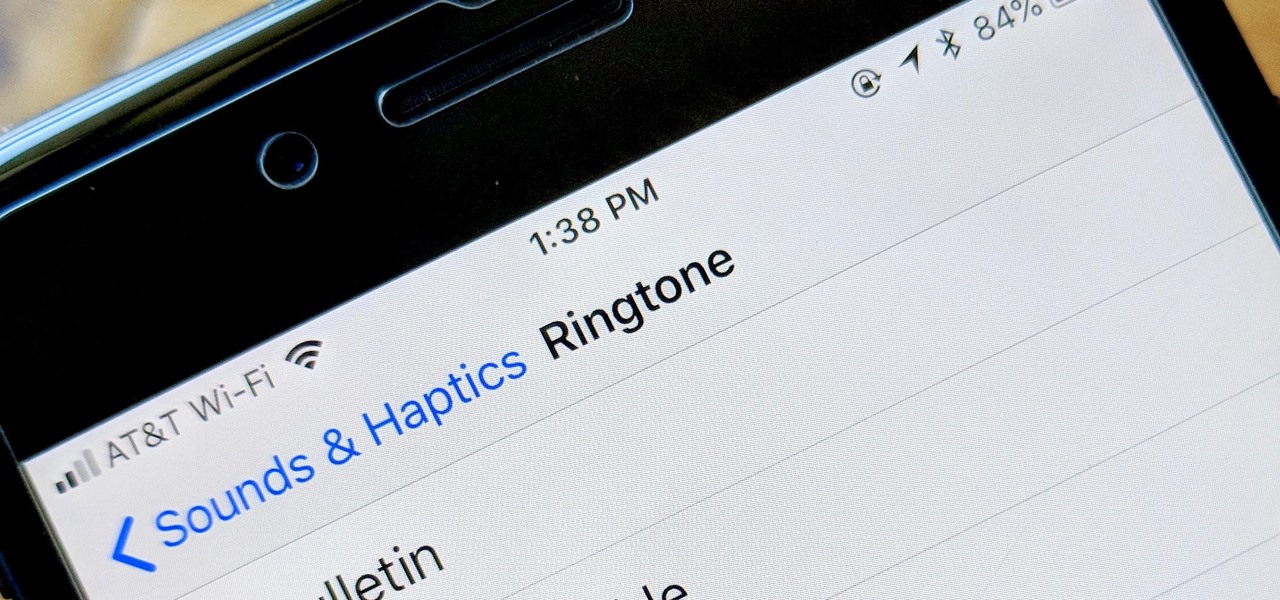
With the exception of "Reflection" on the iPhone X, Apple hasn't updated their catalog of ringtones and alarms since iOS 7 dropped back in 2013. Since then, the company has come a long way with the quality of the iPhone's speakers, but their tones haven't adapted to meet those changes. That's left an opening for others to create their own ringtones mastered for the iPhone.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

With Mobile World Congress fast approaching, all eyes in the industry are set on Samsung's Galaxy S9 announcement on February 25. While leaks and rumors about the S9 and S9+ have been flooding in for quite some time, we're getting a much clearer picture of these handsets as the announcement draws near.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

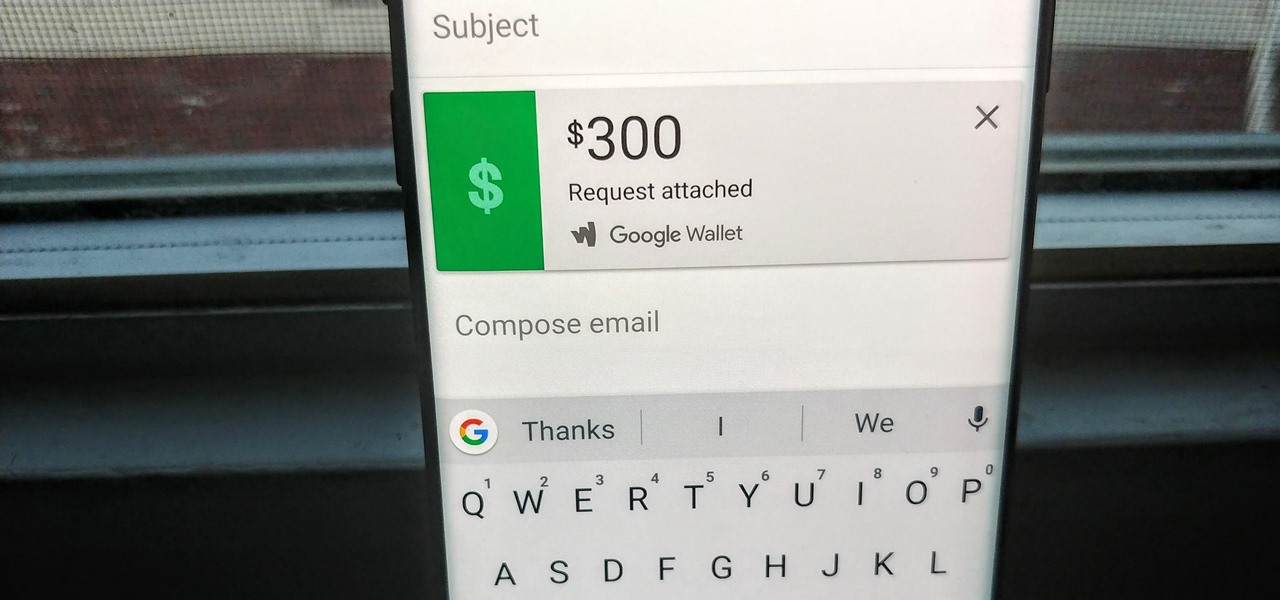
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Shortly after we detailed several indicators that the Galaxy S8 Oreo Beta Program would begin rolling out in the month of November, we now have a full changelog for the update.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.