Fries are such a killer food. They're beloved as the favorite "vegetable" of kids and adults everywhere, yet they are one of the absolute worst foods you can eat if you want to, you know, live past 40, containing high levels of saturated and trans fats that clog your arteries and lead to lots of gnarly diseases.
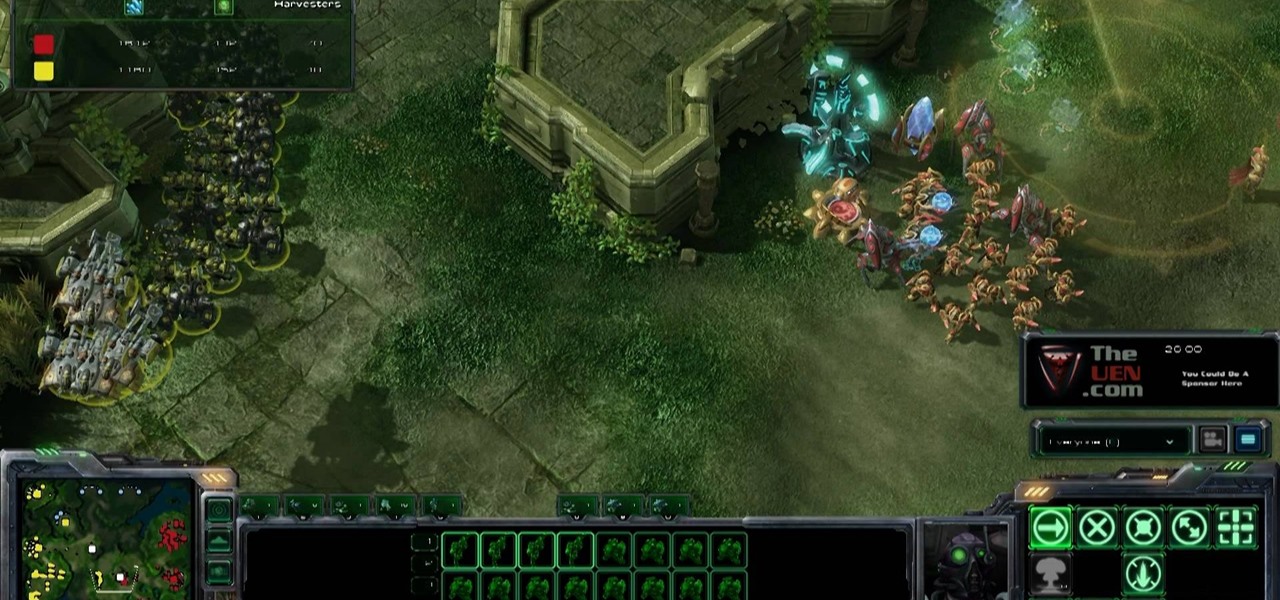
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to use the Protoss High Templar's Psionic Storm ability most effecti...

In this video, we learn how to defeat Aster Protoflorian in Final fantasy XIII. First, activate the aerosol to make yourself stronger. Now, switch over to medic anytime you get hurt from the monster. Take hits where you can and use your different tools to help attack him further. Slash and burn when you can, then use double doses. Libra him when you get a chance, then Libra him again and he will turn red. Now he will have different weaknesses, so watch out for these. The best way to defeat hi...

This video makes suggestions in how to choose colorful flowers and shrubs in your garden. Bowle’s Mauve is a purple flowering plant that will grow and bloom until fall. It will become bushy. Another colorful choice is the Rock Rose, a pinkish flower. The Blue Salvia has blue flowers. A Bank’s Rose, only bloom for a short time. It has yellow or white flowers. Aphids tend to attack it, but it is hearty.

This video is demonstrated completely through visual movement and accompanied with a brief written description. A young man speeds down the soccer field with a ball and scores a goal. His signature move leading up to the goal is broken down into very specific methods of movement, the first of which is a high speed attack as he races down the field. The next method to this signature move is the weight shift, in which the goal scorer shifts his weight, along with the ball, from foot to foot to ...
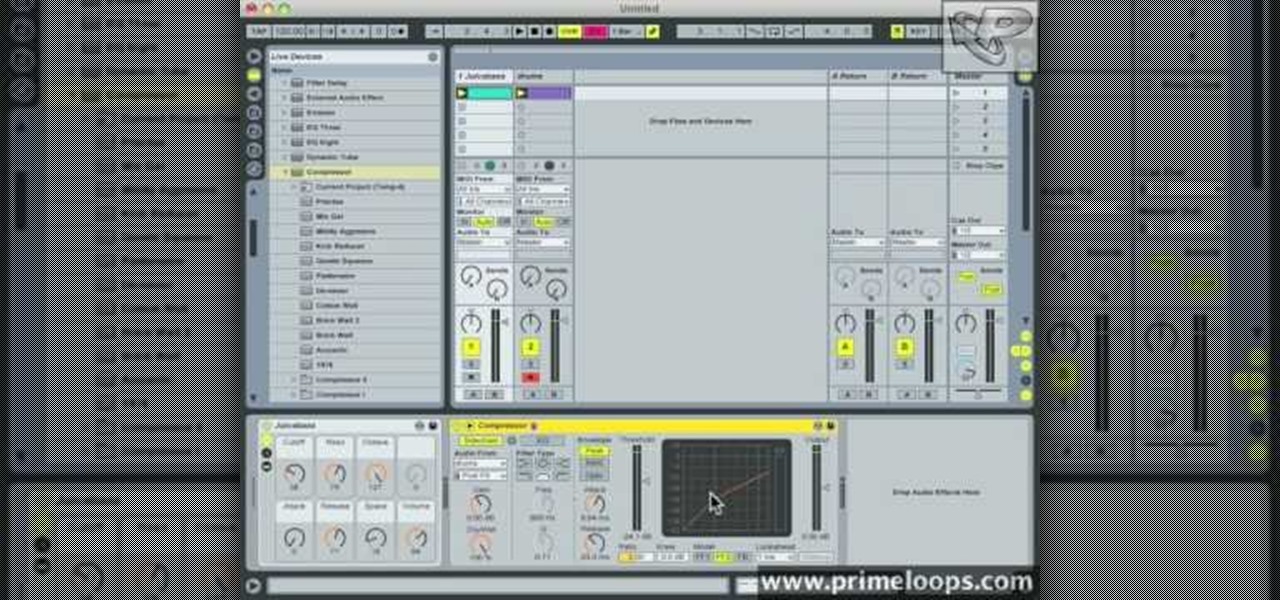
This video shows how to do audio side chain compression to improve your production audio mix. Side chain compression is an easy way to balance the base and the drums. Using a compressor, you can cause your base to drop in volume when the drums are hitting so that one is not over-powering the other. This video walks you through step by step instructions for configuring your compressor to balance based on threshold level, the attack time, and release time. This is an excellent source of audio p...

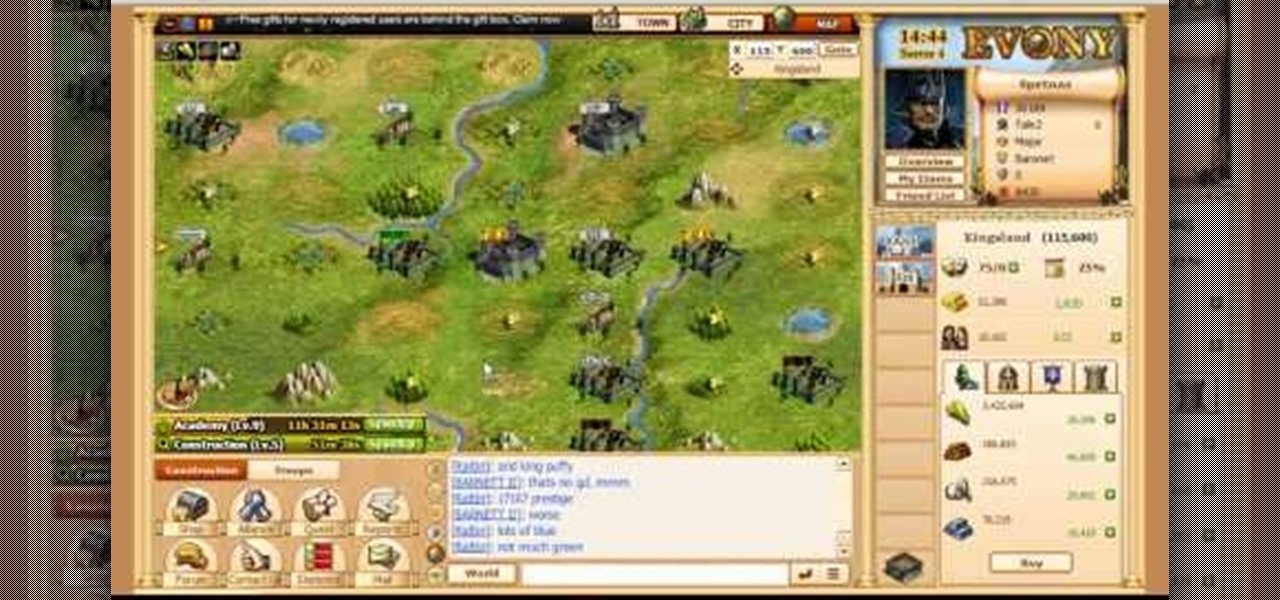
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony - military domination. See exactly what the game Evony is!

You'll find yourself in Kadessa and Deningrad in this installment of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are exploring Kadessa, they fight and defeat the Grand Jewel for possession over the Dragon Block Staff, the party leaves Kadessa just as the Divine Dragon is launching an attack upon Deningrad, the Winglies try to teleport the party to Deningrad but they are too late to stop the attack, the party rush to the castle and make s...

Africanized honeybees, also called killer bees, can be far more aggressive than other types. Here's how to survive when they're on the rampage.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

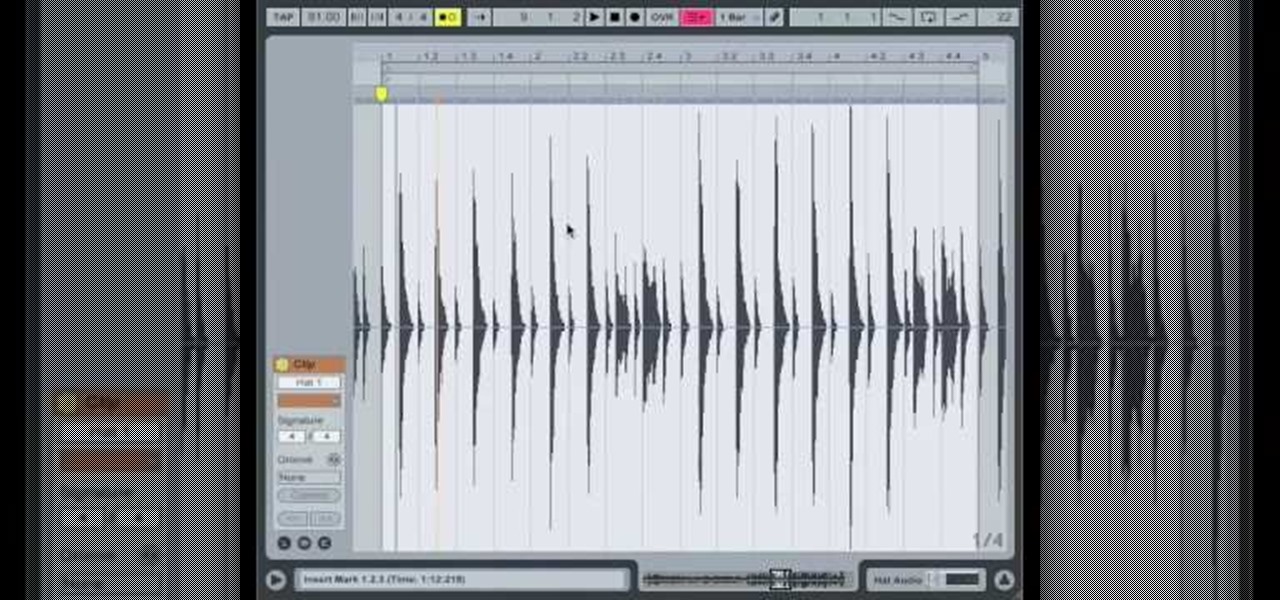
In this video, we learn how to use Ableton Live 8: Quantizing audio. To find the bars you want to use, find the up and down arrow keys. These will jump the loops back and forth based on the width of the loop race itself. Press play to search around for the best four bar section in your music. Now, set your first attack in your loop by zooming in on the hit. Hover over the audio and create a warp marker to drag from each of the bars. Label it as the beginning of your clip to the end, then save...

In this video tutorial, viewers learn how to bow the Erhu. When playing this instrument, keep the shoulders and both arms relaxed. The elbow moves the arm, the arm moves the wrist, the wrist moves the fingers and the fingers move the bow. There is a slight twitch of the wrist on attack of each stroke. The only pressure point is where you hold the bow. Practice bowing the whole length of the bow. Practice with various speeds. This video will benefit those viewers who are interested in playing ...

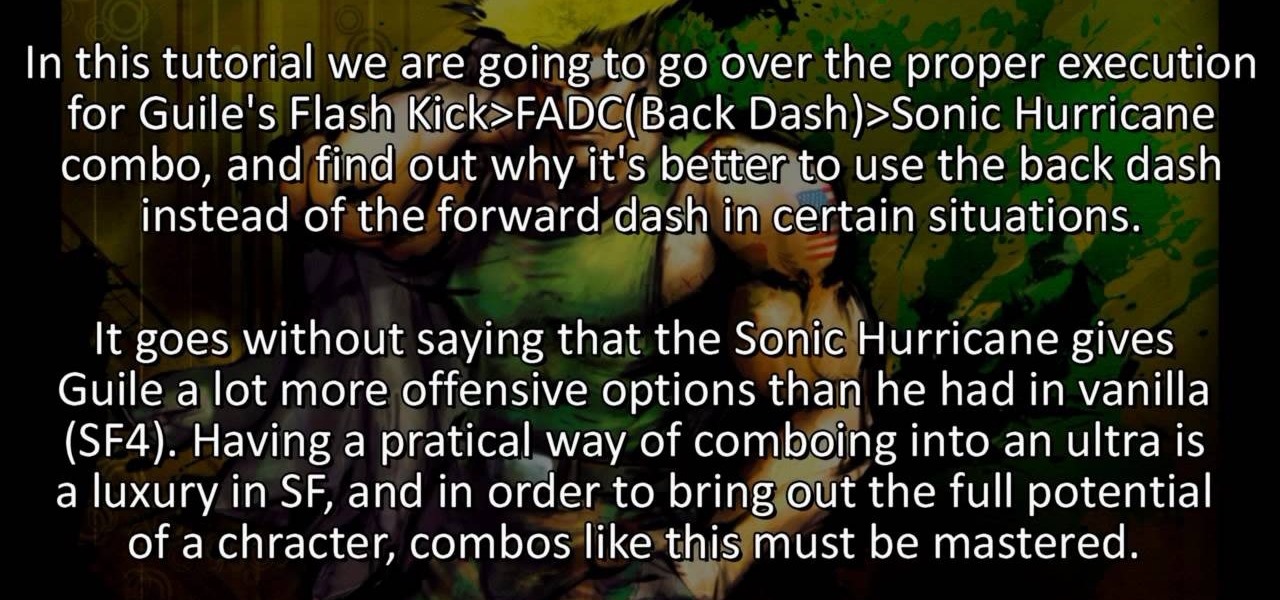
This might be the single best combo that Guile can do in Street Fighter 4, and you're gonna learn how to do it. It's a Flash Kick - Focus Attack Dash - Sonic Hurricane combo that is devastating and can be done quite fast with practice. Which is what you should be doing as soon as this video is over and you can get to the arcade. Unless you're watching this on your phone AT an arcade, you 21st century digital person.

Attention achievement hunters! In this next tutorial, you'll be finding out how to get the Crackshot achievement in the game Dead Space for the Xbox 360. To get it, you must achieve a perect score in the Shooting Gallery in the game.

Burgers are beloved by most Americans for the fact that there's a burger style for every person. Some people like their burgers without meat, some like them without cheese, and some want three times the meat for three times the juicy, heart attack goodness.

"Blah, I vant to suck your blood!" One of the most common and overused vampire lines out there! But who could blame them? Vampires are pretty interesting and cool creatures that have been around for centuries. What makes them so unique and different is that instead of preying on victims during the day, they use the night to hunt and attack its prey, feeding off their fear of the dark. Well at least in movies. In real life vampires don't exist. But it doesn't mean you can't dress or look like ...