Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

UPDATE: A patch to fix the exploit has been released. Download it here.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible.

'Loose Change' is cool secondary quest in Dragon Age 2 that varies depending on whether you chose to be a smuggler or a mercenary when you enter Kirkwall. This video will walk you thorough the mercenary version of the quest, allowing you to, in fact, tie up your loose ends.

If you're a God of Mount Olympis, you may want to leave town, because Kratos is still angry in God of War 3 for the PS3. Killing Gods and defiling women are just a couple of his his hobbies. The other is treasure hunting. And in this IGN Strategize video, you'll find the locations of all ten Godly Possessions in God of War III. The Godly Possessions are more than just conversation pieces. Each has a special power you'll be able to use after beating the game once. You'll also get a gold trophy...

After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to use the 4 Gate Protoss build, which is one of the best and most b...

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create a WoW-like camera and control scheme in the SC2 editor, allowing for WASD control of your uni...

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The volleyball attack can excite the crowd and devastate the opposing team. The approach, jump and landing are the basic aspects of a successful volleyball attack. Learn how to attack in this volleyball video tutorial.

For a field hockey offense to score, their attacking must be better than the defense's tackling. Speed and accuracy are essential for an effective field hockey attack. Learn how to attack in field hockey in this video tutorial.

Watch this trainer wrestle with two full grown tigers, while showing tips and tricks to survive a real tiger attack in the wild. It's amazing how tame these obviously domestic tigers are, even when full-grown!

Personification of the Infinite Consciousness. Lord of Hosts. Master of the Universe. These are just three of the hundred-odd titles of the Hindu god Ganesha. Luckily, drawing the Hindu deity Ganesha isn't so complicated.

California is struck by earthquakes everyday, but the biggest ones, on average, appear every 150 years, just south of the San Gabriel Mountains. The last super-destructive earthquake in California was over 300 years ago, which could mean a long overdue Californian earthquake is on the horizon.

Kipkay is at it again with his pranks. In this video, he shares four fun and easy pranks that anyone can do to drive their friends (or victims) crazy! Their all very simple. They include a cell phone prank, a floss prank, and more!

Dispatch your enemies with a single sword strike. This cheater's guide will show you how to smite even the toughest of opponents with a single hit (and a few keystrokes in Cheat Engine 5.5).

In this how-to video, you will learn how to win at Chess in two moves. First, you will need a chessboard. Pawns go up twice at the start or once. They attack diagonally. Otherwise they just go up once. The castle, or rook, go up and down or side to side. The bishop goes diagonally in both directions. The knight moves in an L shape in any direction. The queen can go sideways, diagonally, forward, and backward. The king can move only once space at a time. Once the board is set up, you are ready...

The video explains how to hack the game Agony: The portal. First he clicked the start game and created new character by entering the name as test dummy and set the difficulty level as normal. The he clicked the start campaign. While entering the game he skipped the tutorial and directly he went into the game.

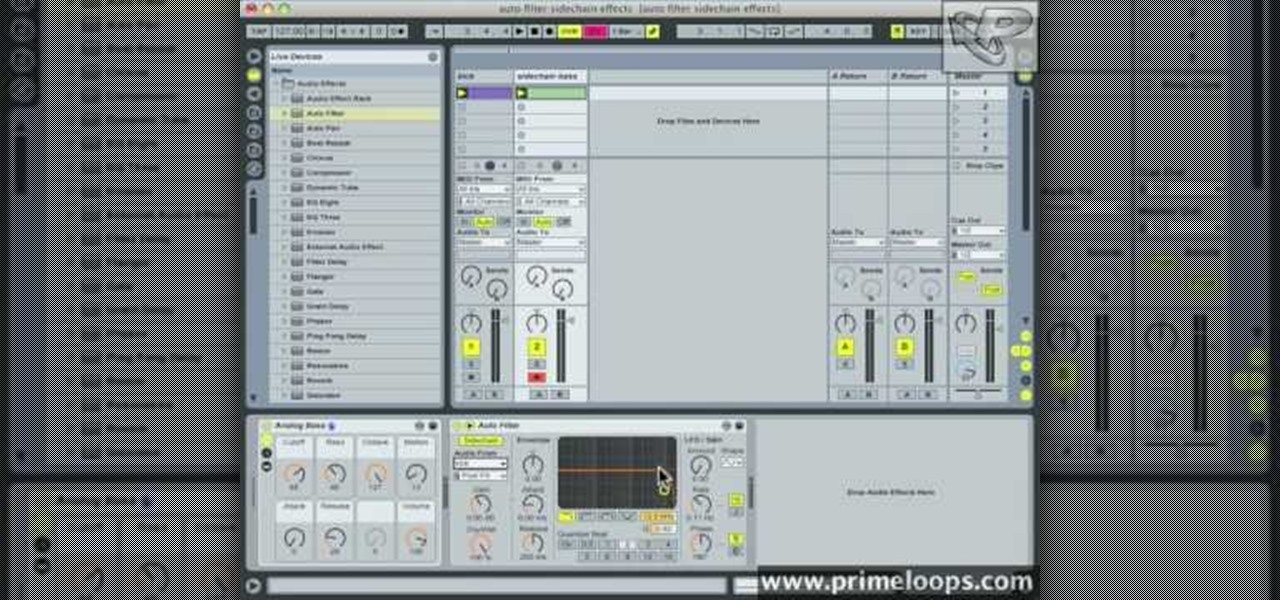
Open your program to a new live set. By using three keys (in Ableton Live), Command (Ctrl), Shift and t, you can create a short cut. Create two new midi tracks making one for (side chain) bass and one for (side chain) kick. To rename a track choose the two keys Command (Ctrl) and r. Next, you can load up the presets, located on the side bar list, one a bass, and, then a basic kick drum by opening up impulse, electronics and Tremor 1994. Now create a couple of patterns. To do this go an empty ...