Fighting Straga is the main boss fight In the Xbox 360 game Darksiders - The Black Throne. Can you beat him? Quickly shoot a portal onto one of the floor stations in front of Straga. Watch his mace carefully and you'll see another orange portal point on the side of it. Shoot a second portal onto the mace then wait for Straga to raise the mace back behind his head. When he does this, drop through the portal you made on the ground so your pop out of the portal on his mace and land on the platfo...

Get ready for car throwing in this Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

This Shadow Arena Challenge isn't the easiest in the Choking Ground on the Xbox 360 game Darksiders. Meet the requirements of each portal to free the Tormented Gate so that you may proceed.

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

In this level on the Xbox 360 game Bayonetta, make sure the bullet enters Balder's head. In Chapter 16 - The Lumen Sage, keep that bullet in line. Father Balder doesn't do much damage, but he tends to stay out of range. When you do have him in range do as much damage as you can. Keep fighting until you get his health meter down to zero and can do a climax attack. For more info, watch the whole gameplay.

Defeat Iustitia in this installment for the Xbox 360 game Bayonetta. In Chapter 11 - The Cardinal Virtue of Justice, attack the tongue. The first part of this fight is against one Ardor and a bunch of smaller enemies. After defeating them you'll see another cinematic and face the boss named Iustitia.

Fight Enchant Angels, Trash Mobs, and Fortitudo in the Xbox 360 game Bayonetta. In Chapter 2 - Vigrid, City of Deja Vu, it's time to shine as one mean mama-san. In the first battle you can walk on walls. To get back to the floor quickly press down on the left stick while jumping. Because this fight takes place on six different surfaces it can sometimes be hard to locate Jeanne (your opponent). If you don't know where she is, just shoot her. Your guns don't do any damage, but you will see wher...

Right off the bat you have a horrendously hard battle against Straga in the Xbox 360 game Darksiders. The Prologue battle with Straga is difficult, unless you have your car throwing skills down. Straga is a massive demon that looms over the streets and War. During the battle, hold the Focus Button to keep the camera locked on this massive creature which also gives you a nice wide perspective so you can really see your surroundings. You'll want to get used to using the Dash Button to dart left...

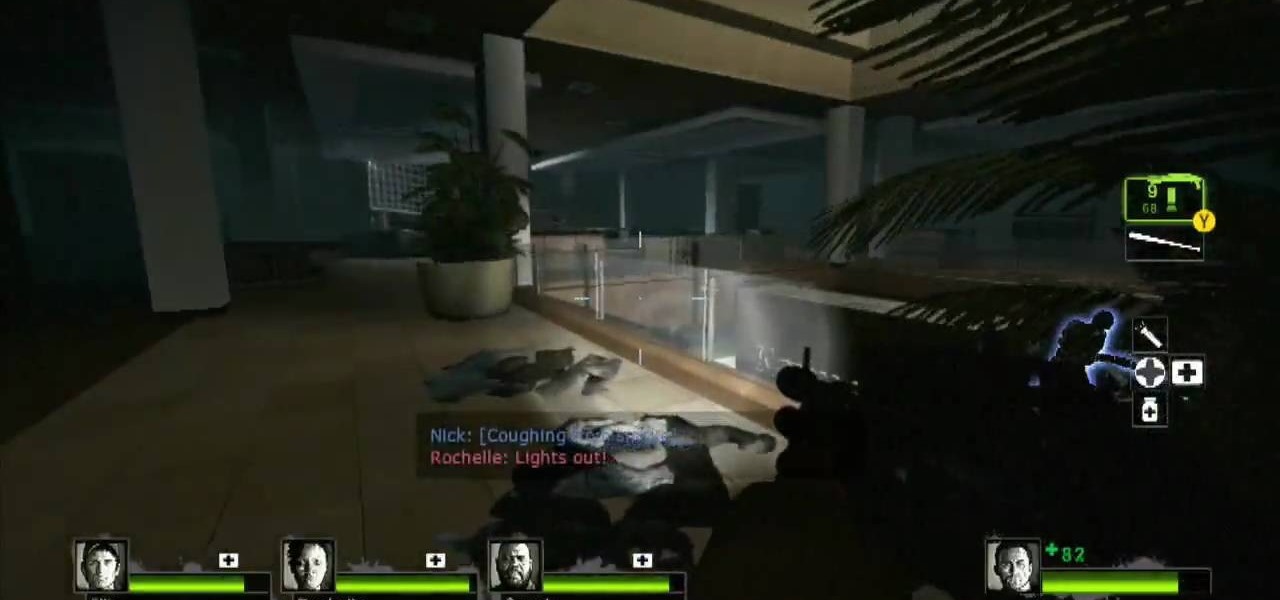
Prepare to delve into the world of L4D2 and check out the gameplay for Campaign 1: Dead Center - Streets. Stock up and open the safe house door. You should see a bunch of infected milling about here. Kill them and make your way straight up the hill past the port-o-potties. Turn right at the fence and take the street down. Watch out for zombie attacks from the walls to the left and right of you. They will drop down from above. Duck into the building on the right when you reach the fence at the...

L4D2: One of the best horror video games of all time. Check out the tips and gameplay for Campaign 1: Dead Center - Mall. Restock on supplies and head out of the safehouse. Feel free to kill any zombies trying to reach in the door before you unlock it. Hang right and make your way up the giant escalator in the middle of the floor. Loop around and exit Kappel's department store. Go down the first escalator you see. Watch out for zombie attacks from the floor above. They will jump down and catc...

Play Along: At the start of the mission, you simply need to follow the leader through the city. Do your best not to bump into anyone, as Ezio will drop the chest if you do. Eventually, you read the end of the trail and a cut scene takes over.

Ace Up My Sleeve: It's not a playing card though. Talk to Paola again and she'll give you the hookup with a cool weapon. Problem is, it doesn't work yet. You need to bring it to Leonardo da Vinci, who's just across town. Make your way to him and knock on his door for a lengthy cut scene.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

This is how to do the Manu Ginobili step back jumper! NBA hot shot show's us how to pull the step back jumpshot, one of his Signature Moves on Nike's series. First the long step and catch your balance. Then setup for the rim. Go behind the back and then see what you have in front of you.

Learn how to hold plank position while doing a cross kick under. Presented by Real Jock Gay Fitness Health & Life.

This debriefed game uses a queen/bishop castle attack. See hot to do it, or not do it. Just watch if you're a beginner, because who better to learn from than a beginner.

Greasy bacon is so delicious, but when it's too delicious it can be soggy, a heart attack just waiting to happy, or merely not as good as a less greasy, more crispy taste. But what if you don't have an oven or stove? How do you make crispy bacon without the mess? The microwave. Yes, believe it or not. Make crispy bacon in your microwave in just a few minutes without the greasy mess.

The narrator starts by asking the question, how do sumo wrestlers get so big. Most of his patients are seeking weight loss. Number one way to put on weigh is to sit breakfast. The reason behind this has got to do with you blood sugar levels. What sumos do is they wake up, skipping breakfast and that train for 5 hours. They then consume about 20,000 calories throughout the day and take naps in the afternoon. They then have a huge dinner. The sumo wrestler uses his metabolism to gain weigh. He ...

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Is your girlfriend or boyfriend always right? No matter what you say, they will always be right? Well, in this tutorial learn how you can win in an argument fair and square with a few simple techniques.

Warts can be embarrassing – as well as contagious. Help minimize the chance you'll spread them to other parts of your body, or other people.

Your sewing machine needs bobbin thread to create overlock stitches, so keep your machine going by learning to fill your bobbin.

Prepare for adventure on the high seas by making your very own pirate costume. You Will Need

When protecting your garden, you can stay green with some environmentally sound solutions. You Will Need

Make your upholstered furniture look like new again by getting out spots and stains. Learn how to remove stains from upholstered furniture with this how to video.

Beat the snack attacks with this healthy banana and peanut butter favorite. You'll love how simple and quick this fruit smoothie is to prepare. This cooking how-to video is part of Healthy Appetite with Ellie Krieger show hosted by Ellie Krieger. Cooking healthy food can be quick, easy, but most of all, delicious. Nutritionist and author Ellie Krieger has created fast and simple healthy recipes for the real world. She'll show you how simple it can be to stay on the healthy track no matter how...

Women's self defense strikes are extremely valuable in a world where women are attacked everyday. Learn self defense strikes, kicks and punches with tips from a martial arts expert in this free self defense video series.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

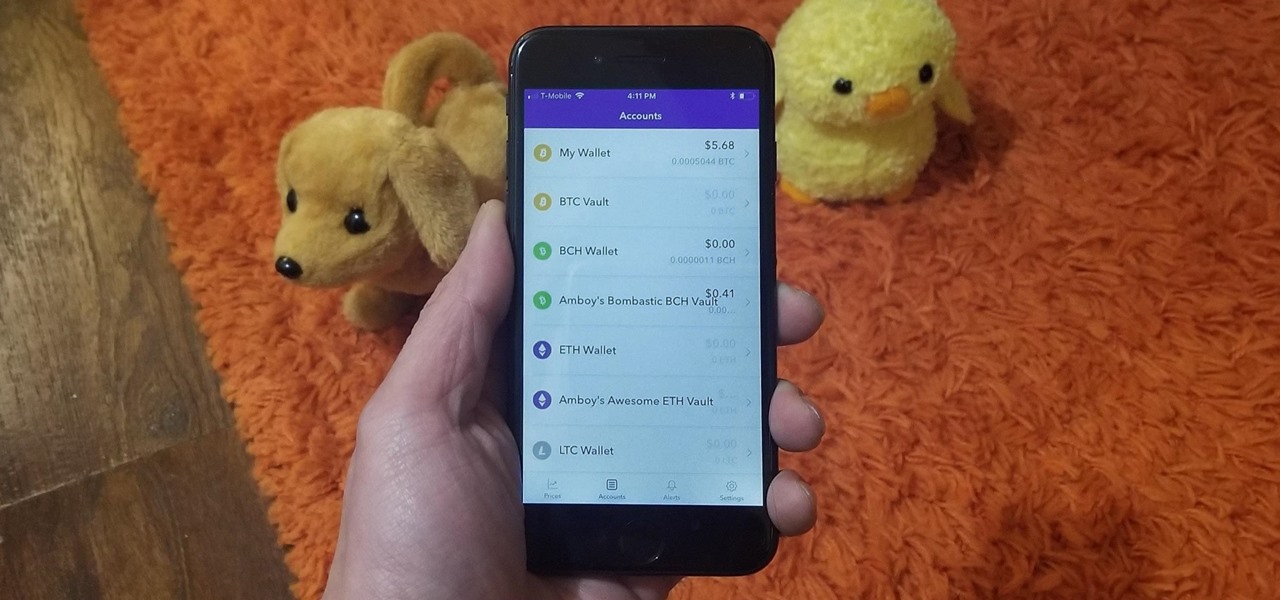
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

After watching Samsung's exploding phone fiasco this past year, I took comfort knowing that the likelihood my iPhone would suddenly combust was slim. However, after hearing about a recent incident in Wisconsin, iPhone owners may have reason to worry.

To celebrate its tenth anniversary, PornHub has just exposed all of our porn habits. All. Of. Them. Before you panic, no individual information has been released. Instead, PornHub has exposed the adult video trends and preferences of a variety of demographics.