All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Imagine you're holding a cookout with family and friends. You're having a good time—the grass is green, the sun is shining, and the smell of the burgers sizzling on the grill is irresistible. There's creamy potato salad, mountains of golden brown chips, and a hefty watermelon chilling on the table, but you forgot something—the drinks!

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

LEGOs are more than just a toy for young children— it's an emerging art form combining photography, stop-motion (i.e., brickfilms), and imitative models that portray today's pop culture as it is. It's something visual culture analysts are sure to be studying over the next decade, and Chris McVeigh, from Halifax, Nova Scotia, is sure to be studied for his LEGO mastery.

When you're experiencing an anxiety attack, there's almost nothing you can do to calm yourself down. At least, nothing that has worked for you yet. In this video, Chantilliscious offers up five of her tips for diversion tactics against anxiety. These are really simple tips, but when you're having an anxiety attack, the obvious is always elusive.

Is a Bridezilla driving you crazy? Whether the bride gone wild is your sister, daughter, or BFF, you can stop the insanity. Here are some tips offered on how to deal with an out-of-her-mind bride.

Shane Benedict explains key techniques to an effective boof. Everybody wants to know how to boof. The boof is, without a doubt, the most essential weapon in your creeking arsenal. There are several key points to making this move effective; approach, stroke, and body placement are the three that we are going to focus on in this segment. We’ll allow Shane to explain…

Learn sabre parry and defense moves in sabre fencing, including beat touch, missed attack, and more with expert fencing tips in this free sabre fencing video series.

Wireless emergency alerts help warn mobile phone users of imminent threats to life or property, such as extreme weather and natural disasters. These alerts target affected geographic areas and come with a loud sound scary enough to make you want to turn off emergency alerts altogether on your iPhone, but there's a way to keep emergency alerts without the ear-splitting, intrusive sound.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

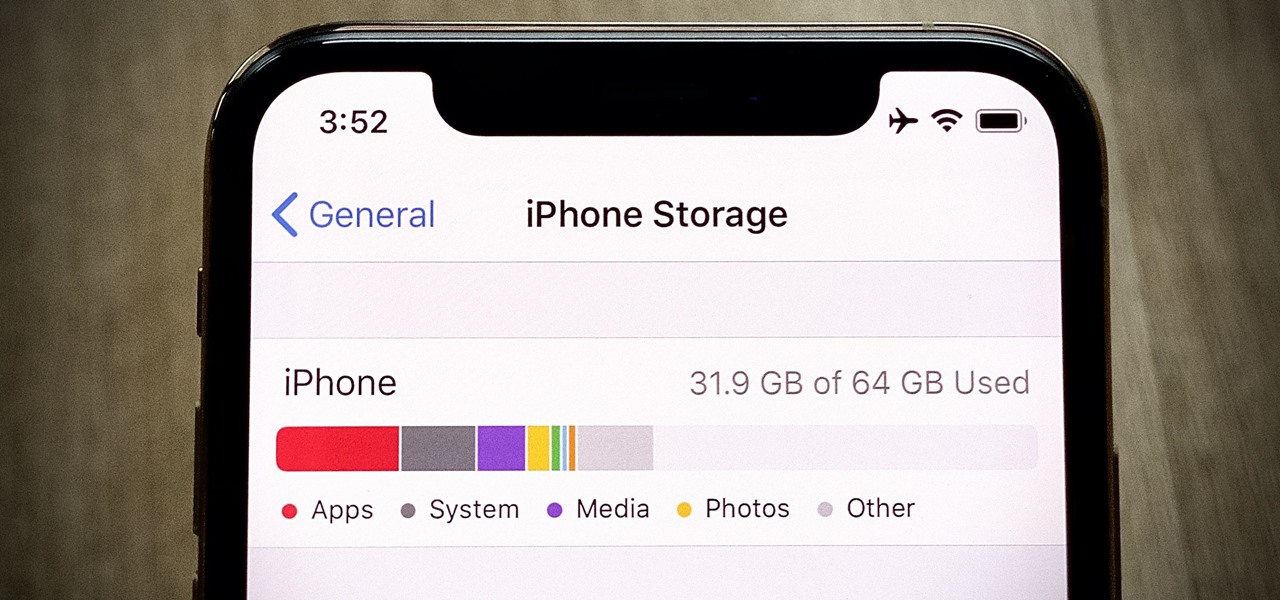
If you've ever run out of storage on your iPhone, you know how much work it can be to free up space. But all that work isn't necessary. Your iPhone can remove content automatically so you won't get any "storage full" warnings anymore — as long as you enable the option first.

Everyone seems to be talking about Elon Musk's new futuristic Tesla Cybertruck, the vehicle that either looks like a cool moon rover or an outlandish video game replica, depending on your tastes.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

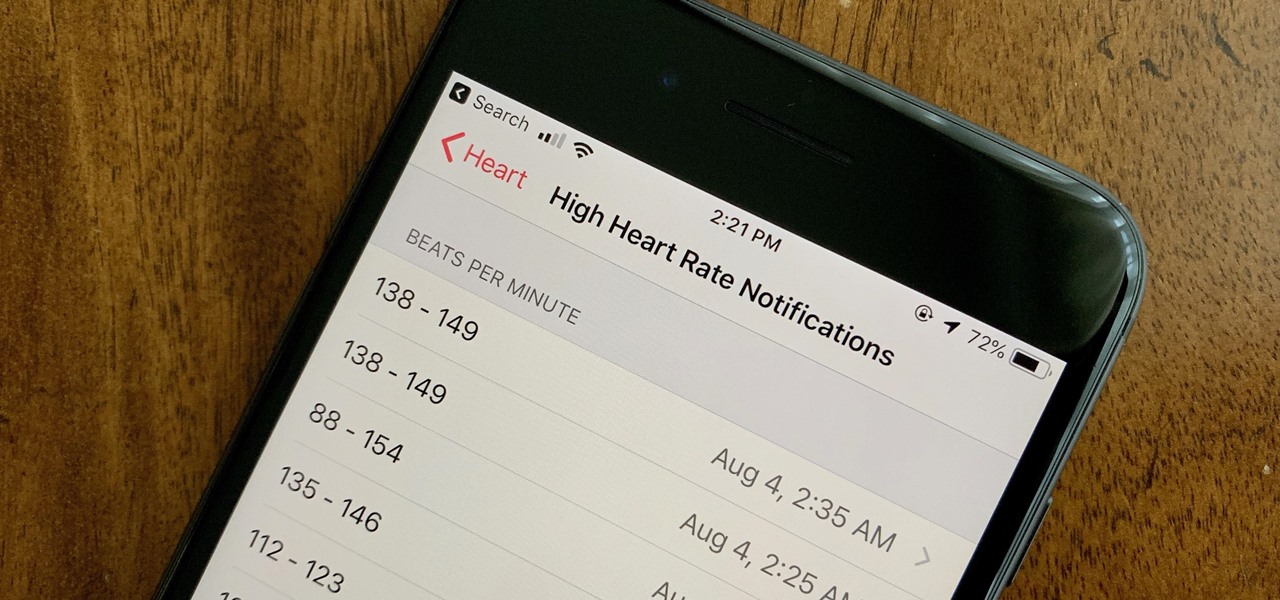
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

To promote Battle of Azeroth, the latest expansion for the World of Warcraft franchise, Blizzard Entertainment has conjured a Shoppable AR Lens that is now available in Snapchat's app carousel.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

If you've ever wanted to hone your paintball skills, without spending a ton of money and making a huge mess, Show Me Virtual and Apple's ARKit have an app for you.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

Sending fleets of ships into battle as an ancient Nordic god? Sign me up.

It's safe to say that mobile developers are excited about the prospects of Apple's ARKit, with demos popping up seemingly on the hour on YouTube, Twitter, etc.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

If there's one thing you'd never think to play music on, it's probably a coffee stirrer, right? But that didn't stop this guy from playing one of my favorite theme songs on one — "Darth Vader's Theme," aka "The Imperial March."

LARPing, or live action role-playing, can look a little silly because it requires a lot of imagination to suspend reality. But mixed reality technology like the Microsoft HoloLens can change all of that with voice commands and special effects.

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

The HoloLens can do some pretty crazy things such as create a robot invasion in your walls, but it can also help you do simple stuff, like hanging frames, paintings, or anything else on those walls—after you repair them from the robot attack, of course.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.