Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

So, what has Arnold Schwarzenegger been up to since his role as the Governator? Besides his resurgence in Hollywood and spooking gym members as Howard Kleiner, he's getting culinary on us.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.
With millions of options to choose from in Google Play's expansive library of songs and albums, it can most definitely take a toll on the wallet after a while. As (slight) consolation, Google offers one free song a day, available for download straight from Google Play onto your Samsung Galaxy Note 2 or other Android device. Google's daily free song sure beats other services' free selections. Apple only offers one free single each week, and Amazon offers a decent selection of free songs from r...

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Tablets can be incredibly useful in many situations, and the kitchen is no exception. Whether you're following a recipe, using an app to convert cups to tablespoons, or getting your Gosling fix, there are a lot of reasons you might keep your tablet nearby while you're cooking.

When it comes to melee combat, two swords can definitely be better than one. Throw a stun gun on top of that and you've got a seriously terrifying weapon. That's exactly what YouTuber jonathanj9969 did with his homemade double-bladed stun sword.

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

Michael Faraday was awesome. He discovered electromagnetic induction, diamagnetism and electrolysis, and he invented the Bunsen burner (before it was the Bunsen burner). Because of his work, we can make suits that can withstand 1,000,000 volts of electricity and cases to protect our gadgets from nuclear attacks.

Most cars have them… keyless remote entry systems, and the newer Lincoln model cars have them, too. The Remote Keyless Entry System lets you unlock the doors and liftgate by simply pushing a button on the key fob. There is also a panic alarm on the key fob that flashes the parking lamps and sounds the horn. No more fumbling with car keys! Watch this video to see how to use the key fob on your 2010 Lincoln vehicle.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

This walkthrough guide will cover the complete Overload DLC mission pack for the Mass Effect 2 action role-playing game on the Xbox 360. Overload became available for download in June 2010 on Xbox Live Arcade (XBLA), and features four different missions. Watch this series for all the gameplay action from Mahalo.

Ten verses are in this level of the Xbox 360 game Bayonetta. In Chapter 9 - Paradiso - A Remembrance of Time, get ready to fight Golem. From the floating clock face you can jump to the yellow floating disk. Follow the path of floating objects to the floating courtyard garden.

There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.

See the whole backstory behind the Xbox 360 game Bayonetta. In the Prologue - The Vestibule, you see how to start playing. The first part of the game is an extended cut scene where you will learn the back story of Bayonetta. During some scenes you can control Bayonetta and fight the enemies you, but you don't have to. You don't have a health meter at this point in the game and can't die.

Need a little help with your L4D2 gameplay? Watch for some tips and tricks for Campaign 2: Dark Carnival - Barns. Grab supplies and go out the door. Make your way to the left, past the booths. You will see a bumper cars attraction to your right. Go inside here and back out to the alleyway. In order to get the gong show achievement you will need adrenaline and a melee weapon. If you have neither, you should be able to find a guitar and some adrenaline in the tent across from the bumper cars. N...

In Boca Al Lupo: The end is almost here. This is the last mission you will need to complete. Talk to Mario and he'll send you on your final mission, to assassinate Rodrigo Boriga in the Vatican in Rome. The mission is more linear than any other you've done up to this point, and it requires much stealthiness. But at first, it requires you break into the Vatican. Climb the wall to the west and use the beams sticking out from the wall to jump to a hanging platform to the south.

So you've made it this far, and there's only one man that is standing in your way, and that's the masked butcher. If his exploding barrels, or grapple attacks, are causing you more than a little bit of an ache, don't worry, it's easy to beat him. In this video you will learn the strategy you will need to be victorious!

Show the world just how resourceful you are next time you get a flat bike tire. With the help of some local plant life and some gusto you too can ride your bike to safety without the help of a standard repair kit.

Learn how to make the MAPAJET (most accurate paper attack jet); loads of office fun! This video origami tutorial shows how to fold an accurate paper airplane.

This video demonstrates how to select your weapon in Gears. The video walks you through switching weapons and performing melee attacks with different weapons.

Identify the proper time to throw a knee kick. If you are grappling with an opponent, look for an opening where you can knee-kick him in the ribs or side of the thigh. If an opponent is trying to tackle you around the waist or take you down by grabbing your legs, introduce his face to your knee. If the opponent is standing in front of you and there is not enough room to throw a fully extended kick, grab him and try a knee.

Watchout! Snowballs! You’re outside. You’re getting pummeled with snowballs. Time to build a snow fort and set-up teams... The snow war is on!

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

From forehands to backhands, volleys to attacks, squash success means practicing a variety of shots. Learn the basics of squash with drills from a squash instructor in this free video lesson.

In golf, chipping is an important technique that's used to attack the pin from all areas around the green. Learn some tips for chipping out of the rough from a professional golf instructor in this free golfing video.

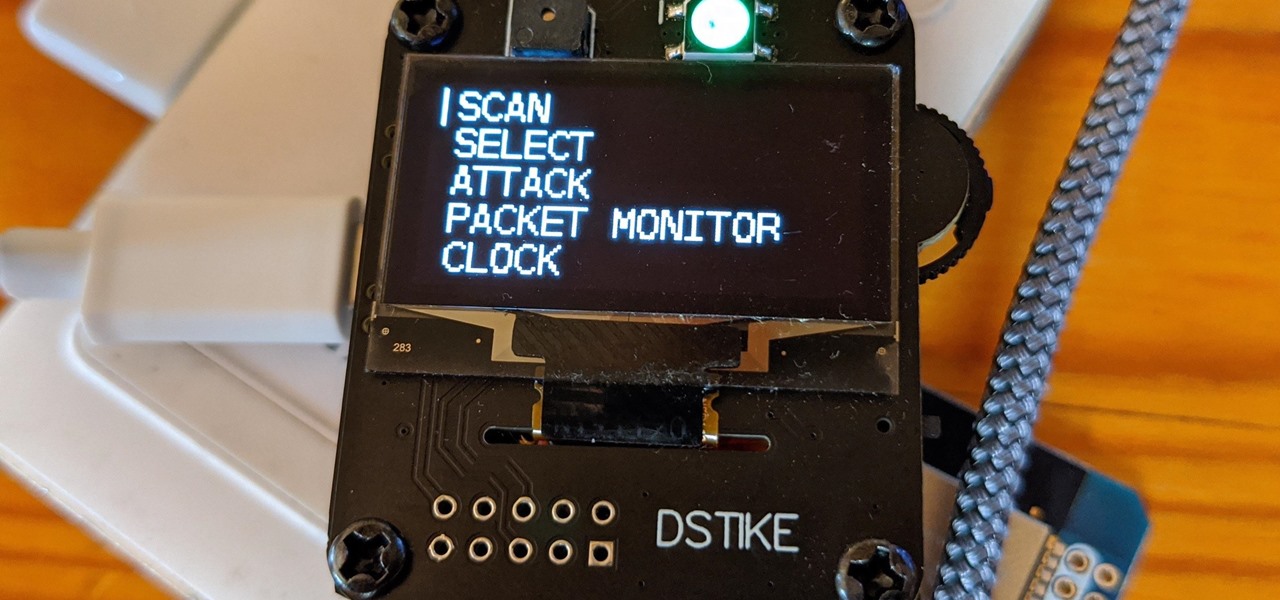
The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting things that the Wi-Fi Deauther can do without plugging it into a device.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.