
How To: Set your default printer on a Mac
Thanks to Apple's awesome user interface, it is extraordinarily easy to set your default printer. Instead of guessing which printer your document printed to, be certain of where it is every time.


Thanks to Apple's awesome user interface, it is extraordinarily easy to set your default printer. Instead of guessing which printer your document printed to, be certain of where it is every time.

If you're not technologically savvy, don't stress. You probably want to jump right into the game, so check out this video on how to properly install your Playstation 3.

Spidering enables you to maintain a position of power, where you can pass, shoot or move quickly. Spidering is the position where one hand is sculling, and both legs are doing eggbeaters. This is a standard water polo position for both attack and defense.

Shooting in water polo is a basic skill for attackers. Water polo shot requires good height out of the water, arm position, shoulder rotation, and head stall. Shot strategy is important to building your water polo game. Concentrate on improving your rotation to follow through and speed up the shot. This is an attack focused water polo drill.

Don’t panic if you’ve got a budding Picasso at home—cleaning crayon off of painted walls is simple. Check out this Howcast video tutorial on how to clean crayon marks off of painted walls.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.
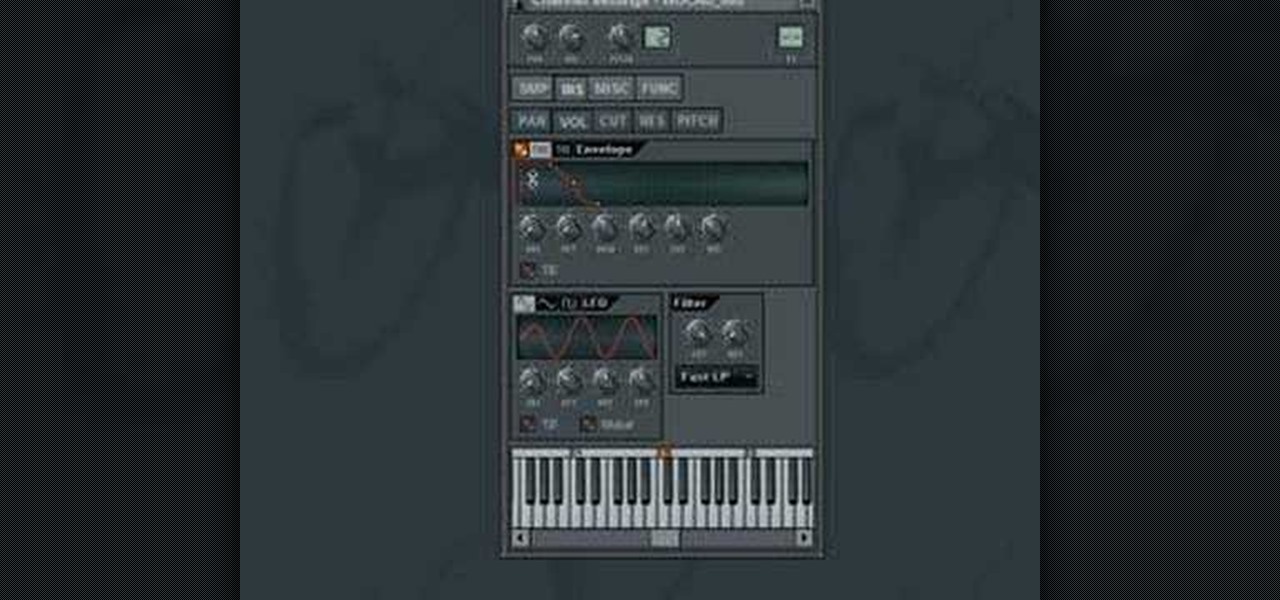
The famous ADSR Envelope (Attack, Decay, Sustain and Release)... It's seen in almost every virtual instrument or software synthesizer from Albino to Halion to SampleTank to Z3ta but do you know what it does?

Perform the basic two handed spiral poi move with tips from this how-to video. This poi how-to video is for beginners and those at the intermediate level. The basic two handed spiral poi move is also known as hand spirals, spiral wraps, and double hand-wraps. To do this poi move, you need to have good split-time and wall-plane control.

This is the set up I use for the straight jacket submission when someone defends the gogoplata. This submission attacks the shoulders depending on how flexible you are. There are a couple of ways to set this up.
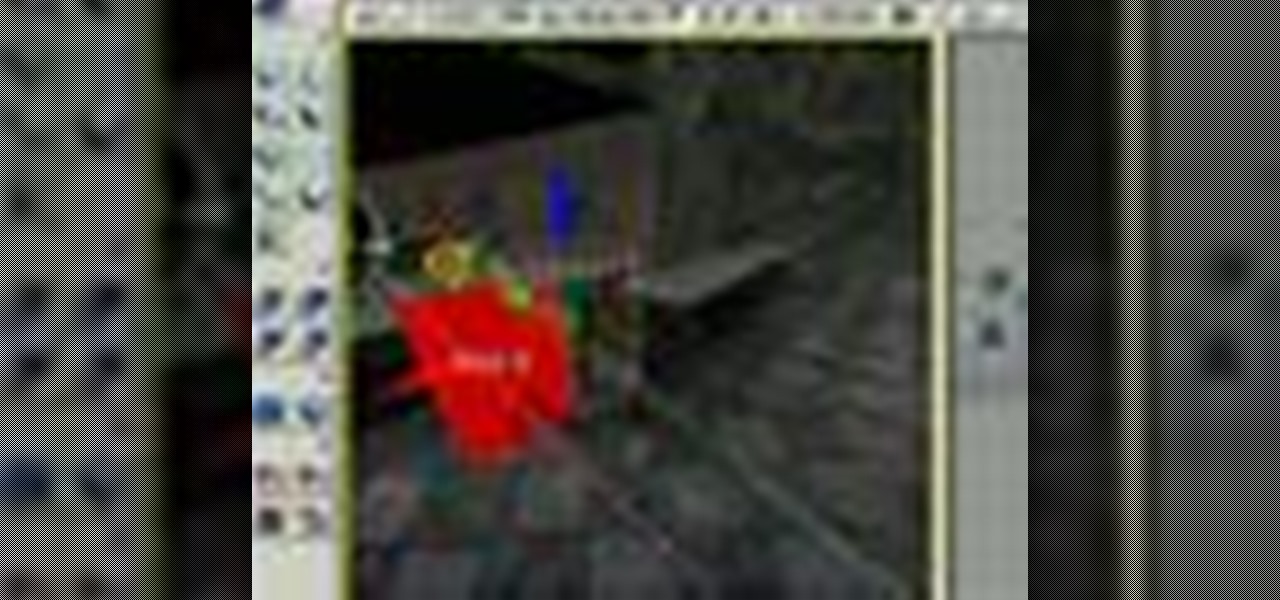
This tutorial shows you how to path Artificial Intelligence monsters in Unreal Engine 3 for Gears of War. This allows them to move around and get them to attack players.

It's Jaws! No it's just face paint, but watch this video to learn the tricks and tips to apply face paint and look like a shark!

Today's word is "thwart". This is a verb which means to prevent from accomplishing a purpose or a plan. For example, you can say "The police thwarted three terrorist attacks at LAX last month."

After a series of quarte disengage attacks, Bijan takes several counter-ripostes before finishing with a fleche. (For those striving for perfection--He's too close when I'm coming forward/hand is too far back in his sixte parry & he's not fully stretched in the fleche--Aside from these things, I think Bijan has admirable form but I'm his coach & biased...)
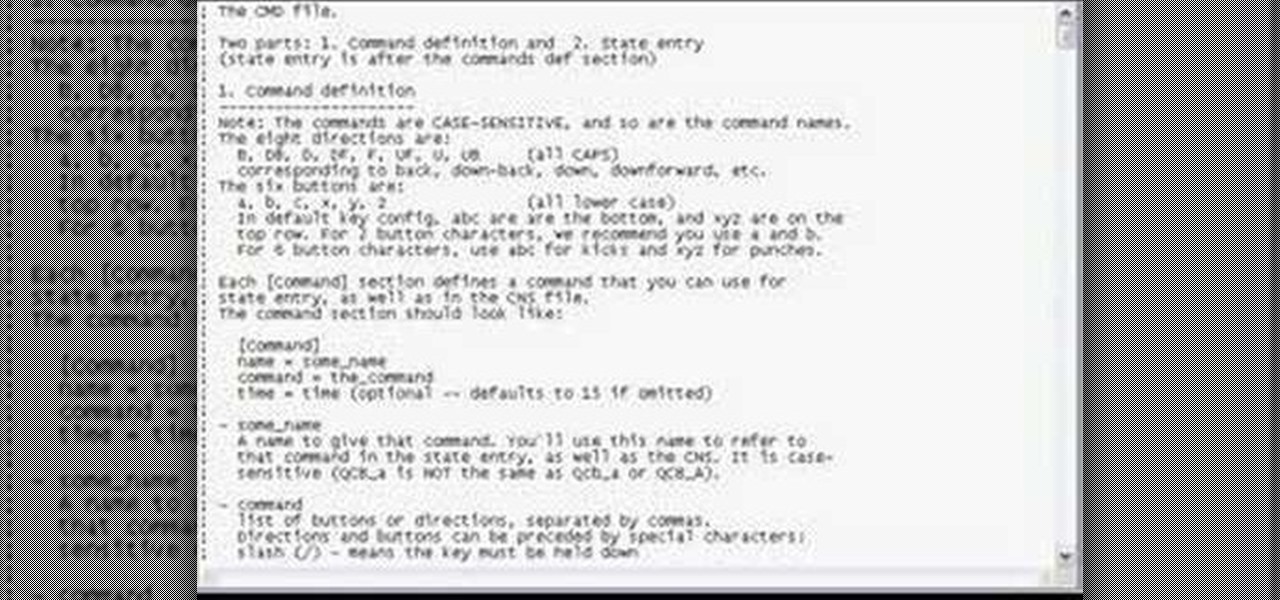
This is a tutorial on how to access characters command list in Mugen - the custom PC game engine - to see how to perform special attacks and basic moves.

This video will teach you the basics of ping pong. Includes simple strokes and attacking and defending strategy.

This video is a step-by-step analysis of each of the moves of the first bo kata, shu shi no kon, including what attack you are blocking and striking point on the opponent. A great way to learn these moves.

This ice hockey tutorial shows you how to do a slap shot. This is an excellent attack play, but be warned, it is the hardest shot a player can generate, requiring full windup with the stick.

Jesse Hubbard discusses the mechanics of shooting and discusses and illustrates the different lacrosse shots. These are the sidearm shot, the 3/4 arm shot, sidearm shot, overhand shot and outside shot, and bounce shot. He also discusses how to shoot on the run. Tips appear throughout the video in the form of pop-ups and are summarized with sidebars.
Worried about a zombie apocalypse? Of course you are, we all are! This tongue in cheek video divulges the steps you'll need to take should zombies begin roaming the earth. Using clips from horror movies, this video shows you the right way to hide from zombies and even explains who you can trust. Learn what weapons work on zombies and how to cripple them and most importantly, destroy their brain! Nobody wants to get bitten by a zombie, learn how to escape, travel and even how to recognize if o...

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

There have been enough music artists releasing Snapchat AR experiences over the past week to fill a small festival. Count them with me: Bruno Mars. Gucci Mane. Kodak Black. Missy Elliot. Imagine Dragons. Panic! At the Disco.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Last week, the first possible image of the upcoming OnePlus 6 leaked. It was met with mixed reactions, most notably for its apparent iPhone X-style "notch." OnePlus fans seem concerned that the company is implementing a design choice based on what it thinks is trending, not necessarily what's best for the product. If you're one of those uneasy about OnePlus' future, don't be. At least not yet.

So, it's Halloween time, and you feel like playing around with some augmented reality apps? Well, you've come to the right place — if you have an iOS device.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.
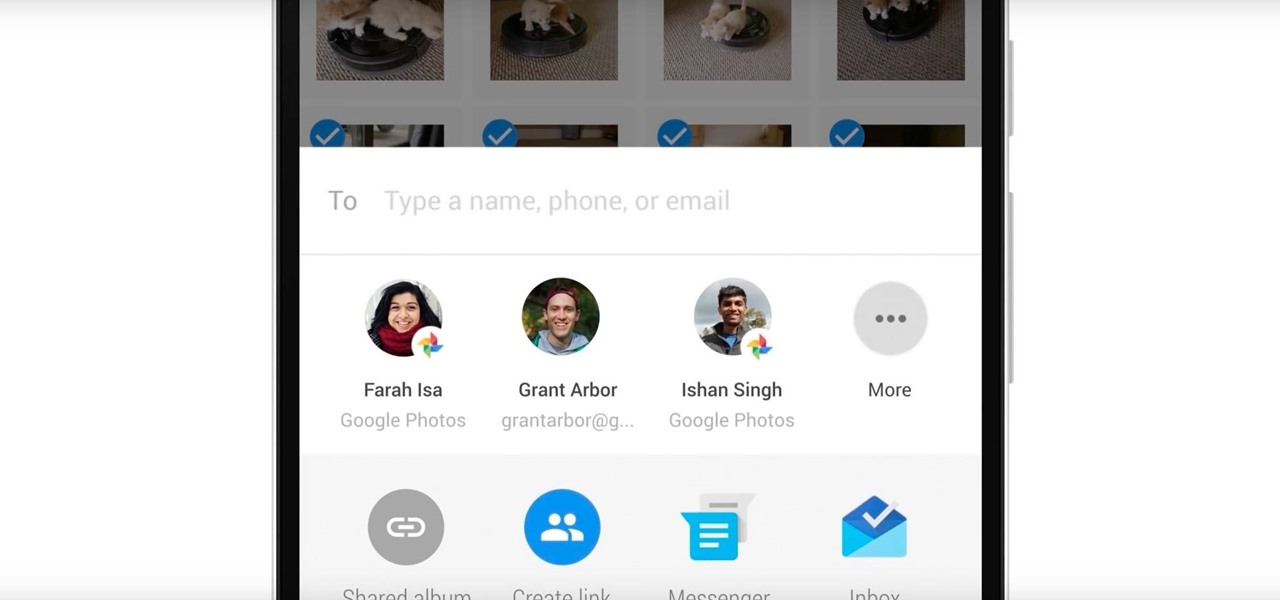
In case Google Photos didn't recognize your face enough, they're now rolling out a new AI feature who uses facial recognition for easy photo sharing.
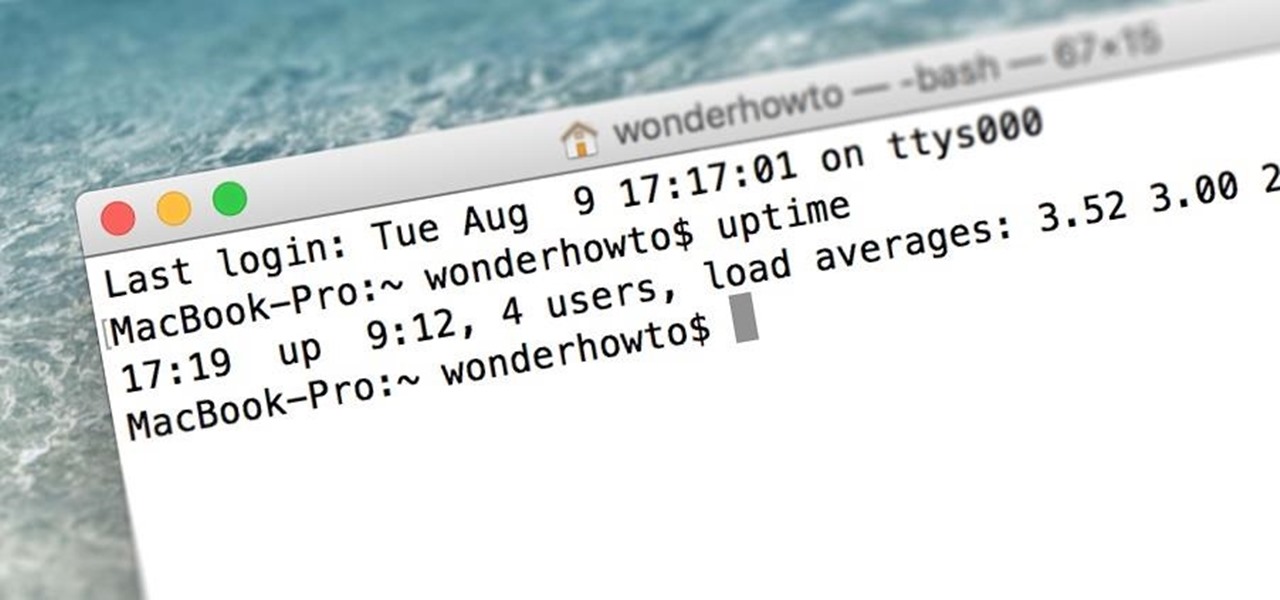
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

If you like to carry your team by doing a ton of damage, and you like the idea of flying around in a flying machine, try out Corki, the Daring Bombadier in League of Legends. In this champion spotlight, Phreak from Riot Games builds Corki with a Trinity Force to do a ton of damage and attack quick. He also overviews what abilties, masteries, and runes to get on Corki.

If you play Elder Dragon Highlander, the awesome Magic: The Gathering variant, check out this video for a guide to building a cat-based deck that will ravage people. Cat attack! If you haven't played EDH, check out the link above and come back.

A bug out bag, or BOB, is a prepared bag, usually a backpack, designed to sustain you for up to 72 hours while your escape wherever you are in case of a natural disaster, terrorist attack, or other catastrophe. This video will teach you everything you need to know to prepare an effective BOB that will help ensure your survival.