Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go to an Apple Store to have it fixed? This brief article will help you weigh your options.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Tim Boucher is head soccer coach at LaSalle Academy in South Bend, Indiana and in this youth soccer video series, learn some fundamental soccer skills and moves. Our coach will lead you through some of the basic soccer drills you need to practice to get good at the game. Learn how to dribble, how to pass, how to shoot, how to trap the ball, how to juggle, and how to properly throw the ball in. Also learn some techniques for playing various soccer positions, including goalie. These sports vide...

In this online video series, learn from expert mechanic Nathan McCullough as he teaches and demonstrates how to replace the strut mounts on your vehicle. Learn strut mount replacement fundamentals such as how to locate the strut mount; what are some common problems that can occur as a result of strut mount breakage or failure; how to break the lugs and jack up the vehicle; how to remove the tire; how to stake the lower strut to the suspension knuckle; how to remove the caliper; how to remove ...

It's Black Friday time, and in 2020, that means a lot of online deals to make up for more stores closing on Thanksgiving, as well as everyone avoiding in-person shopping because of the coronavirus. But while you may wish to grab a better 65-inch 4K TV, the new PlayStation 5, or some hacker hardware on sale, Black Friday is also the best time to invest in your programming and cybersecurity education.

Toymaker Lego has been on board with building AR into its playsets and mobile apps since the launch of ARKit.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

If there's been one signature design element for Apple's iPhones, it was the circular Home button. It served as the "everything" button for each iPhone model until last year's iPhone X, but now, it's completely absent from the iPhone XS, XS Max, and XR. Should you be worried? Short answer: No.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Today is the 10-year anniversary of the death of Apple co-founder and former CEO Steve Jobs. To commemorate the occasion, Apple has posted a message and a mini-documentary on its website.

The last few weeks were fairly busy in the realm of augmented reality and remote meetings developments. Most of that activity was generated by some mammoth announcements from Snap and its Spectacles AR smartglasses, and Google, with its Project Starline experimental holographic video conferencing system.

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

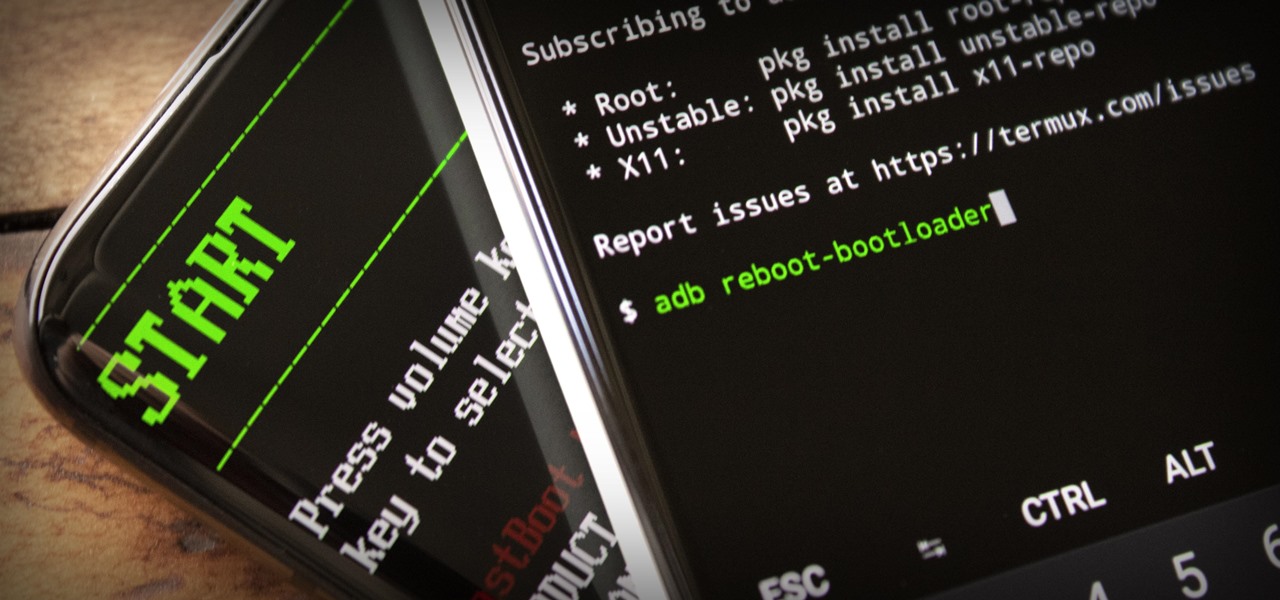
ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.