
News: Neurable Planning to Bring Brainwave Controls to AR Headsets Later This Year
Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).


Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

As a self-proclaimed chocoholic, any day with chocolate mousse in it is a good day in my book. And thanks to prominent chemist Hervé This, one of the founding fathers of molecular gastronomy, chocolate mousse is not only easy to make every single day—but only requires two ingredients.

Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

Making yogurt at home doesn't sound like an easy task at first. We initially saw it as detailed, hands-on, and precise—a process that required special equipment, specialized (and expensive) live-culture bacteria, and loads of yogurt knowledge.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

We here at Food Hacks are all about saving you, our wonderful readers, time and trouble in the kitchen. So when I saw that Barilla had come out with their Pronto line of "One Pan, No Boil, No Drain" pasta, I had to give it a try. While no-boil lasagna noodles have been around for a while and allow the pasta to essentially cook en casserole, this relatively new addition to the pasta scene includes elbow, penne, spaghetti, and rotini varieties that allow for usage in a greater variety of pasta ...

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Oven space is scarce on that fated fourth Thursday of November. Even if you can find a spare space for pumpkin pie on the bottom shelf, you risk turkey drippings overflowing from above and ruining your beautiful dessert — not to mention a burnt crust from different temperature requirements. The bottom line is: oven real estate is valuable, and it's tough to multitask cooking for Thanksgiving when every dish requires baking or roasting.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.
Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

The idea of a no-churn ice cream seems like the ultimate dessert hack. But, in fact, this concept has been around for at least the past 100 years in what Italians call semifreddo.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Sometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead. It's all up to you.
Spiders are common pests that typically prefer to live outdoors. However, insects and warmth will eventually attract them into our houses. They like to spin their webs in corners, crevices and unused areas of your house. Most species are harmless and even act as a natural repellent for getting rid of other insects. However, in some cases, spiders can be very dangerous. Whichever the case may be, they are scary and people are always looking for natural ways to get rid of them.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Whittling has been around for years and years and doesn't require a great amount of skill to perform. What it does require is patience, a steady hand, and a creative mind. This tutorial focuses on how to start of whittling a wooden bird. So sit back, pay attention, and enjoy!

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

Are you an avid gardener who tends to your plans on a daily basis? Then before you step foot outside the door today, check out this video to learn a plethora of tips for going green with your gardening.

Papel picado is a traditional Mexican paper crafting (perforated paper), and it can sometimes be difficult to cut, especially when you are trying to cut fifty layers at once. To make cutting easy, you can use a chisel, and this video shows you how to make one with papel picado in mind.

Putting music on your iPod using Windows normally require having to use iTunes, which can be a real pain in the but if you hate using extra software for something that should be as easy and dragging and dropping.

If you're not into pork, you probably won't like this particular recipe, and if you're not into raw meat, you may want to avoid this, too. Because this video recipe covers a meal that requires Parma ham, which is ham that is eaten uncooked. You could always dive in and try it out anyway, because it's well worth the experimenting! Plus, there's prawns, fresh salad and lemon juice.

In this video Donnie Smith shows you how to apply primer surfacer. In addition to the visual instructions on the video, you can follow along with the instructions below from Donnie himself. After watching this video, you'll be an expert on primer surfacing!

We're the ultimate foodies, but when it comes to preparing shellfish we get more than a little intimidated. Requiring heavy duty shell removal using knives and knick knacks that look like they belong in a doctor's office, the task is usually one who choose to skip.

We've all heard that death comes in threes. In our tireless hours of prank research here at Wonderhowto, we've observed that pranks often do as well. By stringing three simple pranks together, you can achieve all of the annoyance and laughter of a much more elaborate / expensive / dangerous prank. In this video, you will learn how to set up one combination prank that requires only simple things:

Write a fraction as a decimal
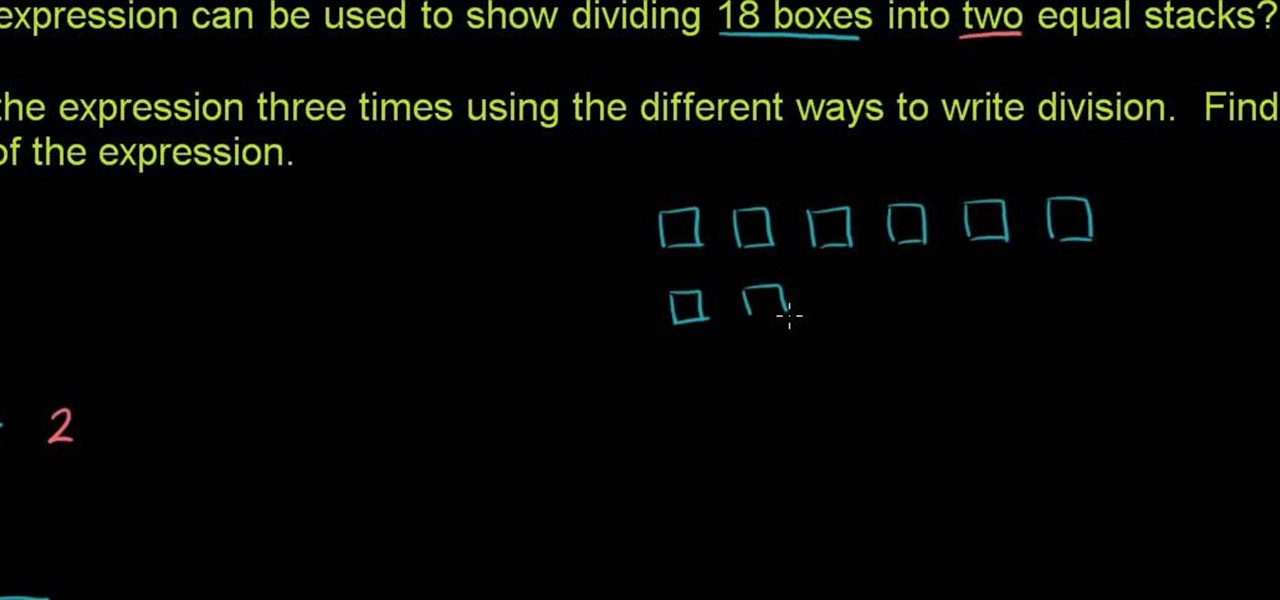
From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to unpack and solve word problems that require you to divide whole numbers.

In this tutorial, we learn how to draw small faces on paper. This is best for drawing on comic books, because the faces are smaller than on regular drawings. First, give yourself a scale size to see how large you want the faces on the paper to be. If you are new at drawing, use the square method to learn how to measure the face and learn how to draw the face so the body is scaled to the size of the head. Start out by drawing the head and adding in shading details. You will start with the guid...

In order to find the best drill bits to drill in metal, you should look at the angle of the bit. It will need to have a center point. Bits only cut on the ends. The grooves on the sides are made to remove the excess. The point on the end determines how it will cut. Titanium bits last a long time, but cobalt bits last even longer. They will all eventually become blunt. They will require sharpening.