The truck in this video was having a misfire problem during routine service. This video for mechanics will show how to find the problem of this misfire. The first thing to look at is the lab scope. After that, comes time for the smoke machine test to identify a possible cylinder compression leak. Watch and learn. This is very similar for a lot of different automobiles.
YouTube is a great video service because it's free and has invaded the world… meaning, practically everybody has been on YouTube at one point or another. Another great aspect of YouTube is the ability to embed content on your website or blog… like your WordPress blog. You can also embed full YouTube playlists. This video will show you the steps to embedding YouTube playlists on your WordPress blog, and the principles can be applied for other sites as well.

It is never a good sign when the 'check engine' light comes up on your dashboard. In this tutorial, learn how to reset the light if it is not functioning properly. If you have already fixed the engine issue and wish to reset the warning light on your Saturn S-Series, this video will show you how quick and easy it is to do so.

This video tutorial from iWalous shows how to install Bossprefs on your jailbroken iPhone from Cydia.
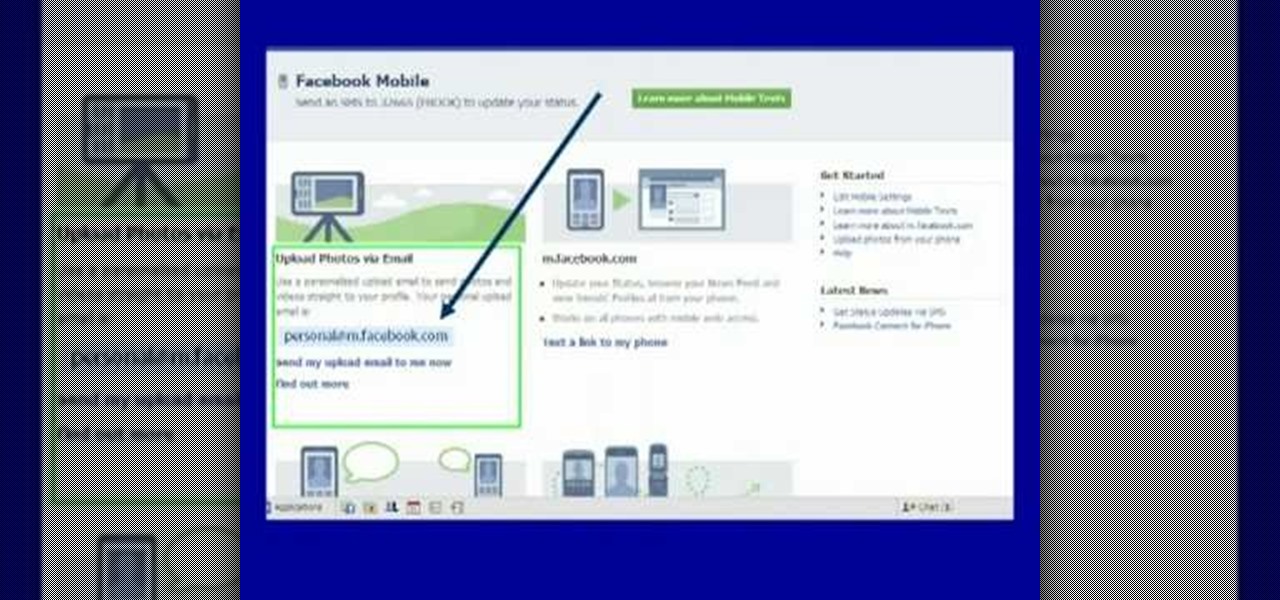
Moniquewade will show you how to upload photos and videos to Facebook by using email. The user has seven steps for you to follow in order to upload photos and videos to Facebook using email services very fast and easy. The first step starts out by telling you to go to Facebook.com. By following each of the seven steps that are provided, you should be able to send different types of photos and videos to your Facebook account just by using email.

In this video tutorial, you'll learn how to change a damaged belt or brushbar on the Vax V-026 Rapide Deluxe carpet washer.

In this video tutorial, you'll learn how to change a damaged belt/brushbar on the V-006 Turboforce vacuum cleaner

If you are interested in spa facial services, learn how an oxygen facial can make your skin softer and remove impurities with this free skin care video series.

In this first clip, Chef John shows the basic restaurant technique for poaching eggs. Due to the high-volume of a brunch service, it is almost impossible to poach eggs “to order.” They are poached ahead of time and held in cold water until final plating, when they are re-heated in simmering water for a few minutes. This method also works great at home for smaller batches as you’ll see. Once you’ve poached your eggs and have them in cold water you are free to set up the rest of the plate

Richard Buccola has been playing pool most of his life, and enjoys teaching it to others Trick shots in the game of pool are often associated with hustling, or sharking. During the mid-20th century pool halls were often given an unfair reputation as dangerous, seedy dens of sin (especially after the 1961 Paul Newman film “The Hustler”) where people would lose their money to unscrupulous pool sharks. But interest in the game has seen a rebirth of sorts in recent years, and most pool halls and ...

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

Your phone tracks your every move to some extent, and I'm not just talking about Google services. Smartphone manufacturers use telemetry services that run in the background to track how you use the device, mostly for ads or to improve their future products. You don't usually have a say in the matter, but if you have a rooted OnePlus, there's a way you can take control over it.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

OnePlus releases some unique and exciting features before they start catching on with everyone else. Their OxygenOS is often considered the cleanest and most useful variant of Android. However, there are still a few key features OnePlus has yet to bring to their devices. This includes a proper lift to wake option.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

As the COVID-19 virus continues to spread, counties, cities, and states are closing down businesses, events, and schools that aren't absolutely necessary. Some companies around the US are recommending or requiring employees to work from home during the coronavirus pandemic. If you're stuck at home, there are apps and services to help you make it through a lockdown.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

Did Google CEO Sundar Pichai kill Google Glass for non-enterprise users? That's the obvious first question following news that non-enterprise Glass users will no longer have access to Google's core apps after February 2020.

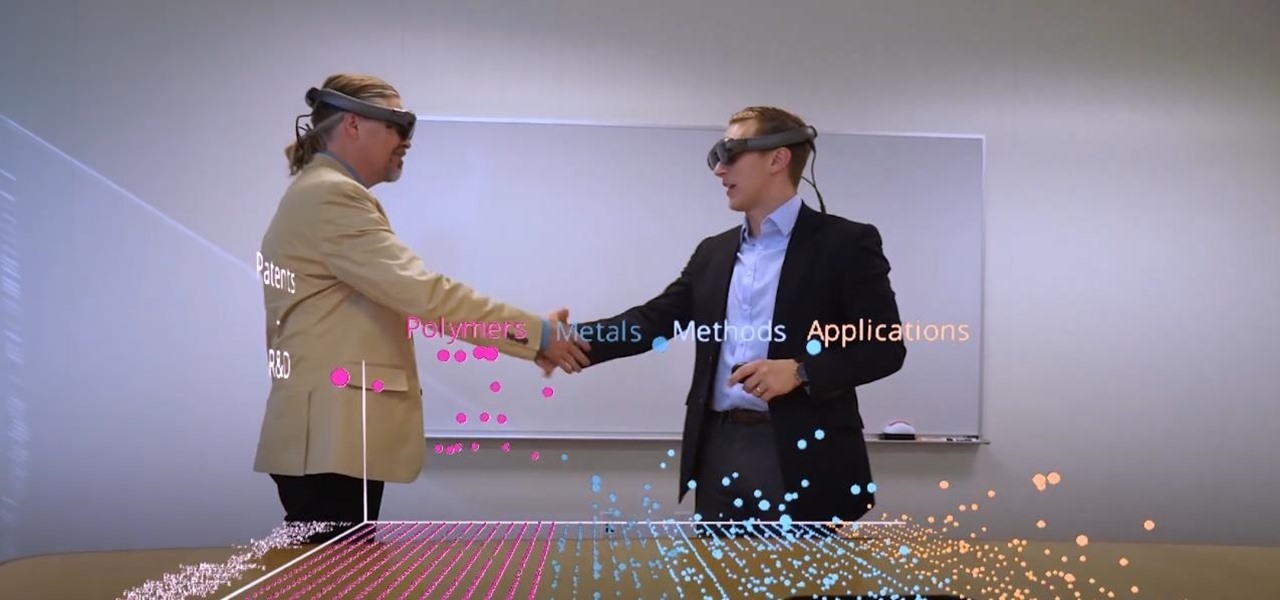
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

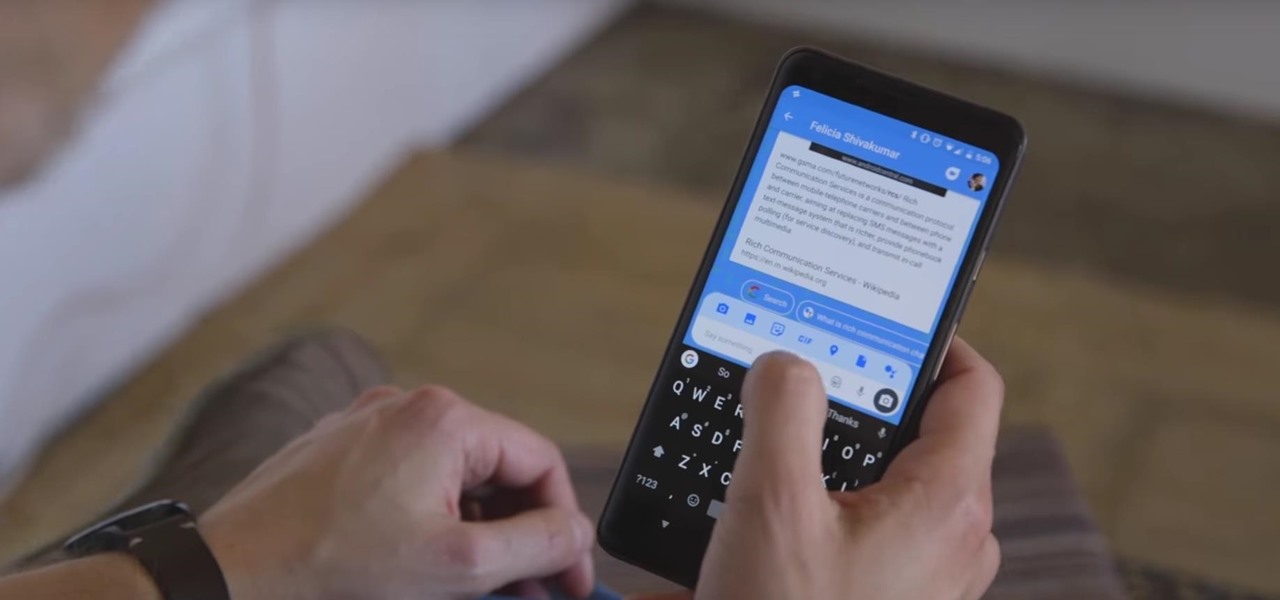
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

If you have devices that run different operating systems, you know how frustrating it is that Apple's Calendar app isn't available on other platforms. If you use Siri to quickly create an event on your iPhone or Mac, you're not going to see that event on your PC or Android tablet unless you sync your calendar to another service.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Samsung has the Bixby key, Pixels have the Google Assistant squeeze gesture. It's nice having a hardware button just for your assistant so you don't have to say "OK Google" or press an on-screen button. If your phone doesn't have such a shortcut, though, you can remap an existing hardware button to trigger the Google Assistant.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

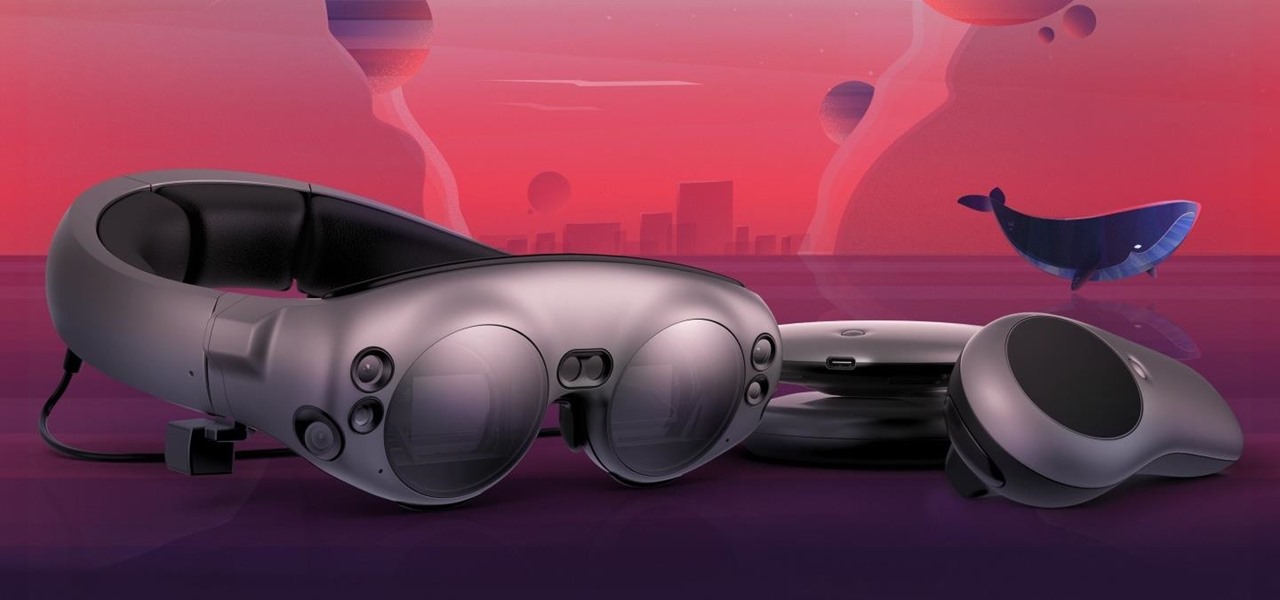
If you subscribe to notifications for Magic Leap CEO Rony Abovitz's Twitter feed, you'd think everyone in the world already has a Magic Leap One. Alas, that is not the case, but those not within the geographic areas of Magic Leap's LiftOff service now have a loophole through which they, too, can join the "Magicverse."

Look, we all like getting things for free. That's why we can stomach things like advertisements and optional purchases in freemium apps and games — we're willing to pay for our mobile experiences in every way but currency. Although freemium seems to be the model for the future of iPhone entertainment, it looks like a different scheme might win out in the end.

Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

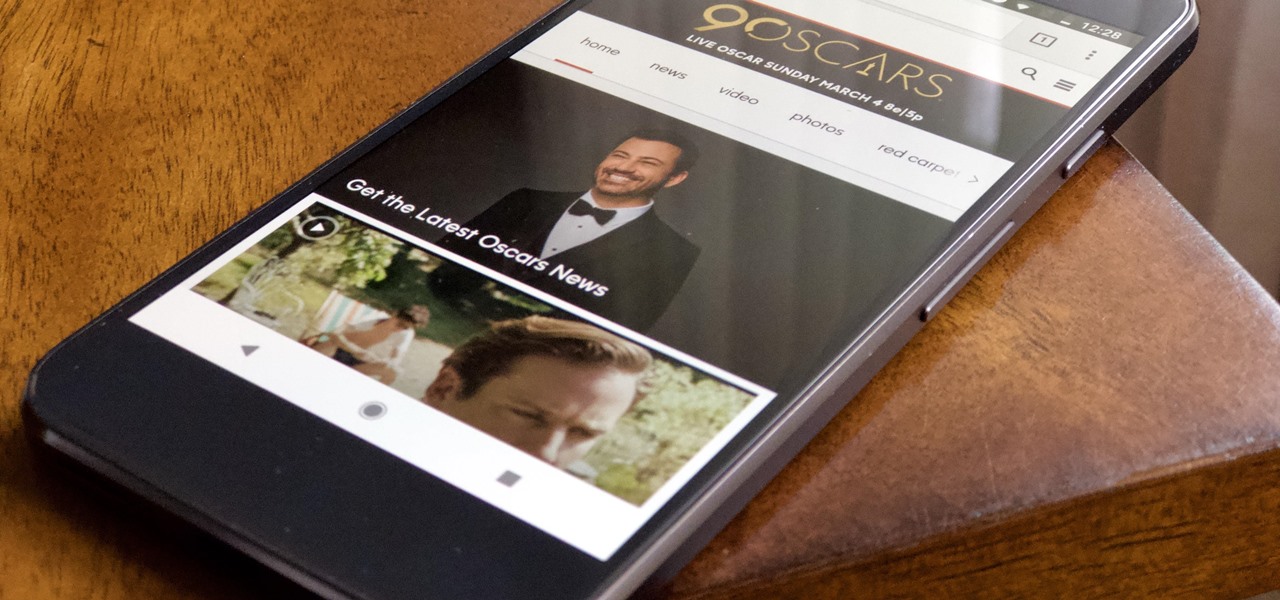
Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid any delays on the night itself, make sure to run through your viewing options here.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

During its third-quarter earnings call, Apple CEO Tim Cook said that "AR is going to change everything."

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Ride-sharing firm Lyft says it will continue to rely on drivers in the near and long term even as it replaces them with driverless cars, Taggart Matthiesen, Lyft's director of product, said during a Podcast with Recode.