
News: Wacom Video Shows Off More of Magic Leap's Upcoming Design & Drawing Software Spacebridge
The collaboration between Magic Leap and Wacom, which was first announced during last year's L.E.A.P. conference is progressing rapidly.


The collaboration between Magic Leap and Wacom, which was first announced during last year's L.E.A.P. conference is progressing rapidly.

At its F8 developer's conference in 2016, Facebook went on record with a roadmap that called for augmented reality integration into Oculus within 10 years. Now, it appears as though Facebook is accelerating those plans.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

After a little more than a year at motion tracking technology maker Leap Motion, Keiichi Matsuda has resigned his position as vice president of design and global creative director, the company announced on Wednesday.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

Microsoft's Monday keynote introduced the fourth generation of the company's Kinect sensor during Build 2018 in Seattle.
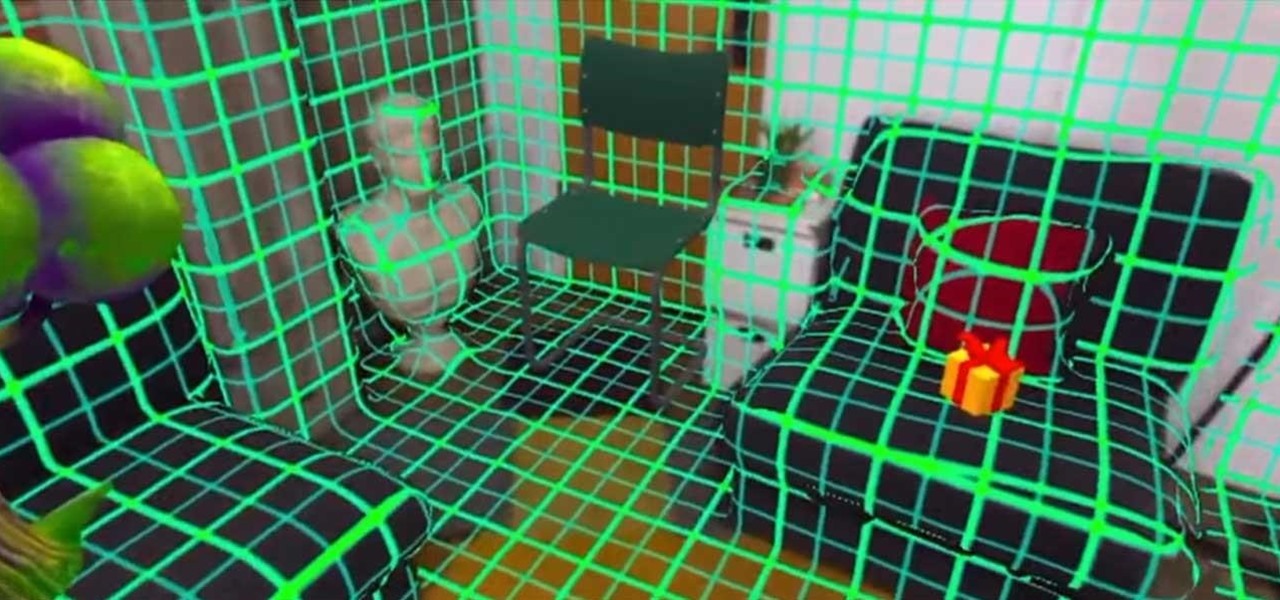
San Francisco-based 6D.ai is preparing to launch a beta of its AR cloud platform that's capable of constructing a real-time dense mesh from crowdsourced data for use in 3D mapping and multi-user AR experiences.

With today's augmented reality experiences, we can see and hear virtual content, but Ultrahaptics wants you to be able to feel those experiences, too.

Researchers at Disney have demonstrated the ability to render virtual characters in augmented reality that are able interact autonomously with its surrounding physical environment.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.
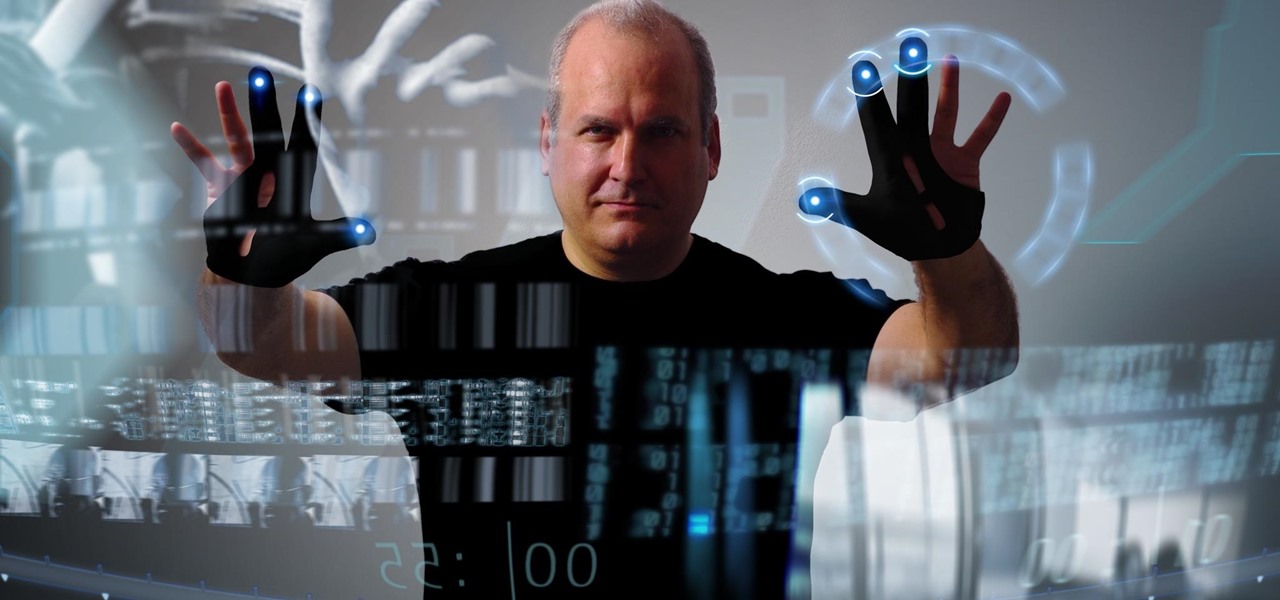
Based on newly surfaced information, transparent smartphones like those teased in Iron Man 2 and those hand-tracking monitors made famous in Minority Report may eventually end up being "designed by Apple in California."

IKEA won't be alone among ARKit apps for visualizing home décor and improvements when iOS 11 arrives next week.

During Google Developer Days, taking place now at the ICE Congress Center in Krakow, Poland, an introductory session on ARCore provides some insights on how the platform operates.
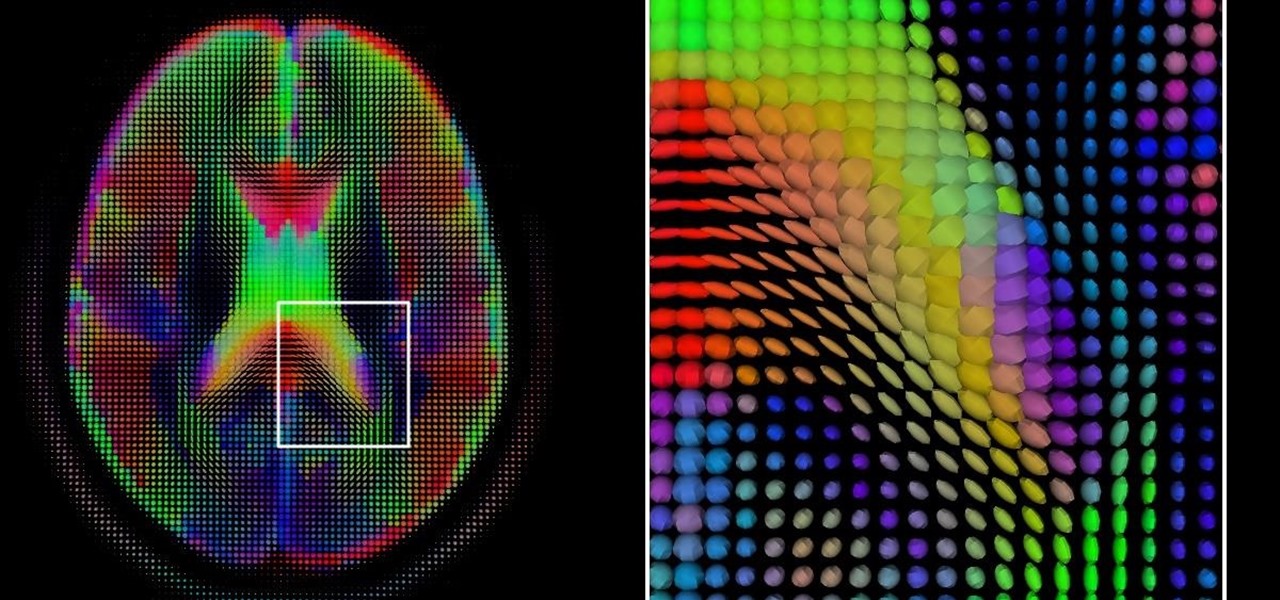
The world is a massive place, especially when you consider the field of view of your smartglasses or mobile device. To fulfill the potential promise of augmented reality, we must find a way to fill that view with useful and contextual information. Of course, the job of creating contextual, valuable information, to fill the massive space that is the planet earth, is a daunting task to take on. Machine learning seems to be one solution many are moving toward.
The laws and regulations in place in the US for driverless vehicles are a mess, but Republican congressional members say they can fix it.
Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use.
The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

It turns out that the new Galaxy Samsung S8 Active (codenamed Cruiser) will be headed for AT&T in the US later this year, just like previous Active models. SamMobile revealed that the device would be exclusive to the network with a model number SM-G892A.

We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

When it comes time to buy a new smartphone, the sheer amount of options on the market can make you feel overwhelmed. There are Android devices of all shapes and sizes with different functionalities and price points, and now, even Apple has three unique iPhone models to fit various budgets.
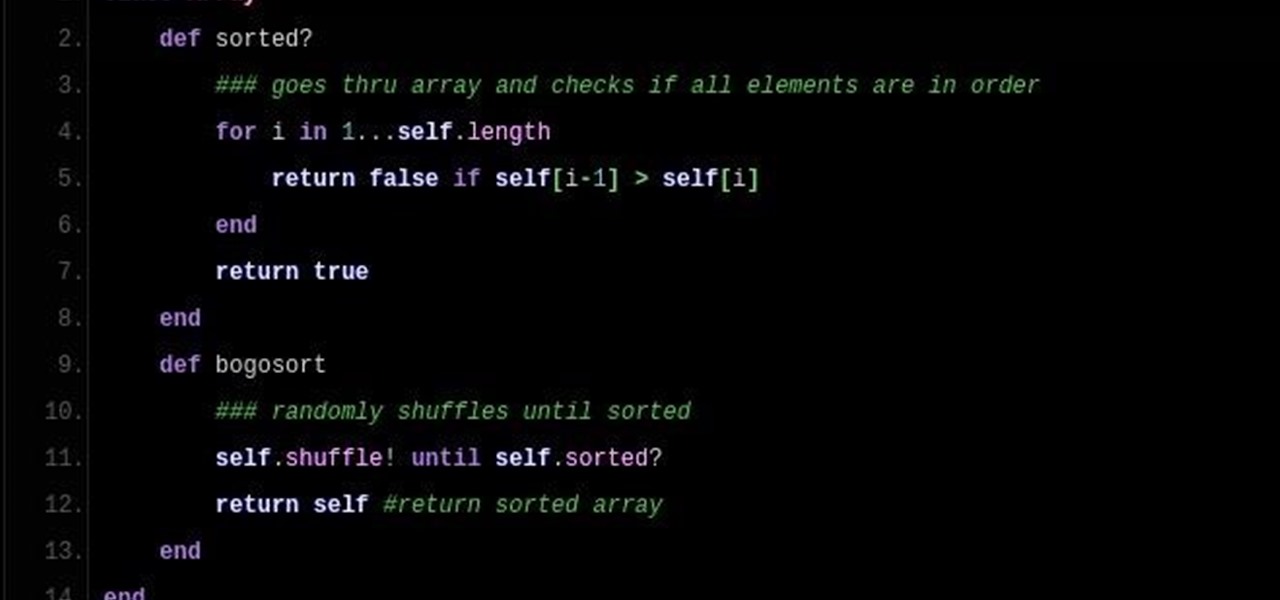
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.
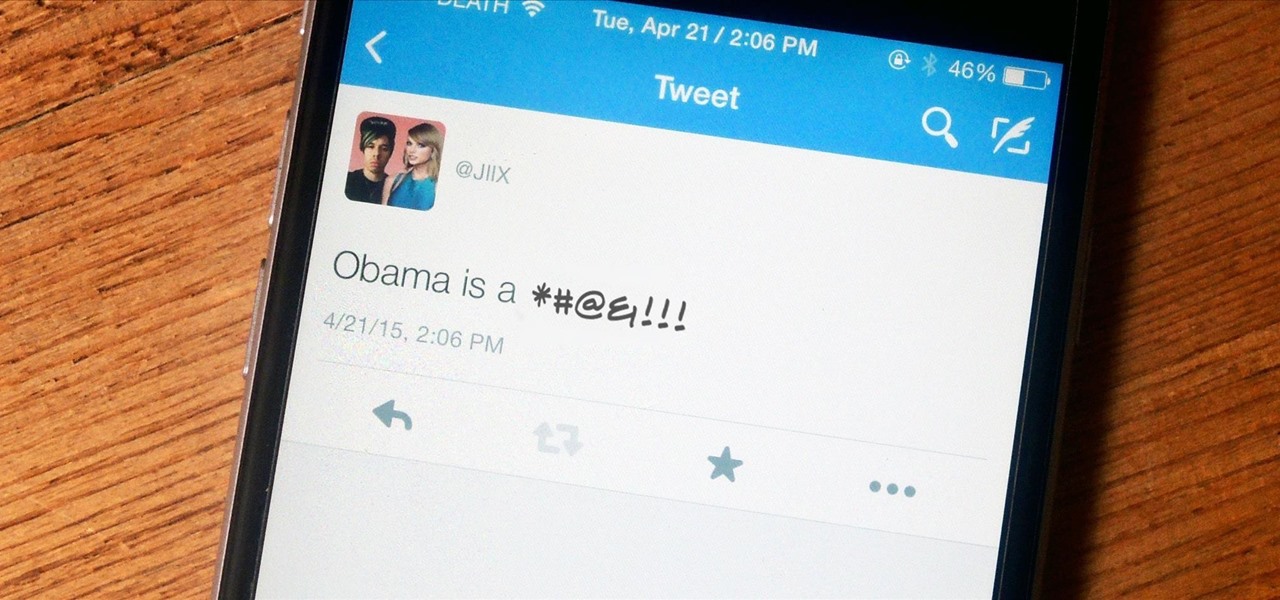
One tweet can get your fired from your job. At least, in the cases of Gilbert Gottfried, Rashard Mendenhall, Ozzie Guillen, and Mike Bacsik, who were all either fired or forced to resign from their jobs after posting regrettable tweets online.
I wrote this about two years ago to help people make realistic passwords. The best part was while writing it I realized I encrypted the list in a manner only the maker would know.... on to the show

Did you know that your face shows others how much alcohol you drink? Whether you've never had a sip of booze with those around you or you're known as the party animal of the group, the genes that shape your appearance also show others just how much you enjoy liquor. Pinpointing the big drinker in any setting is easy to determine: you just need to make eye contact.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.
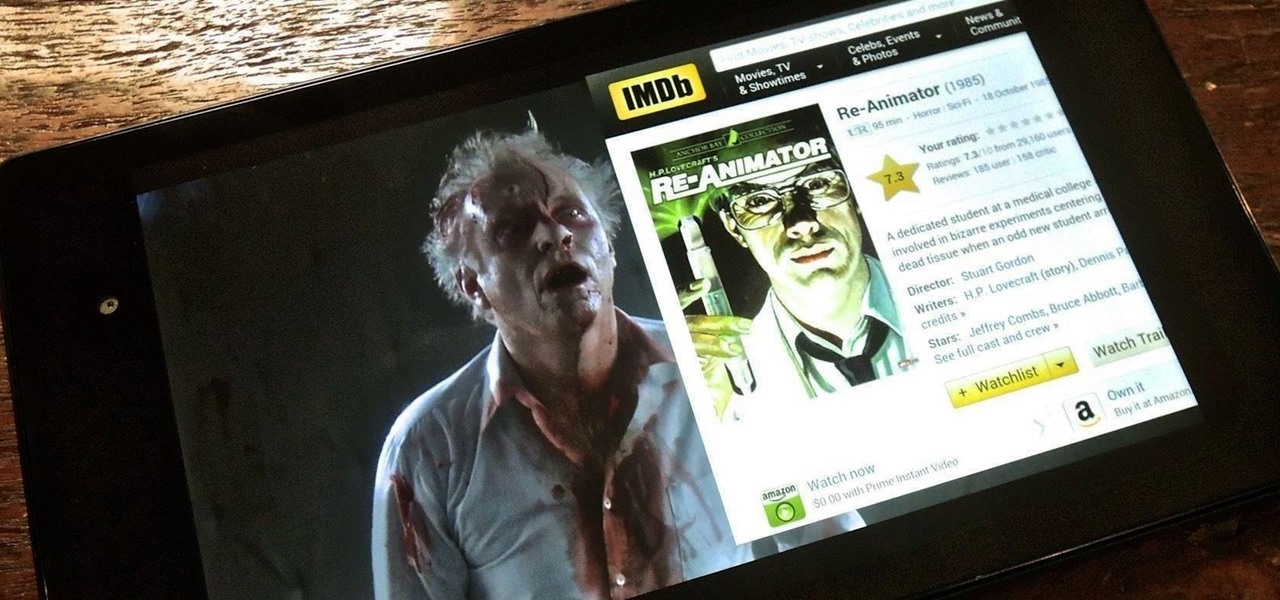
Efficiency is one integral attribute that I need from my Android device. I want to be able to multitask like a maniac and do things on the fly. While multitasking itself is nothing new, actually being able to watch Netflix while scrolling through IMDB at the same damn time was reserved mainly for newer Samsung-ier devices.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

If you are willing to teach online, you might have thought of making online courses. But if you found it too hard, you can start with micro-courses, that can be created in 10 to 30 minutes. Step 1: Define 5-7 Main Points That You Will Cover in Separate Lessons.