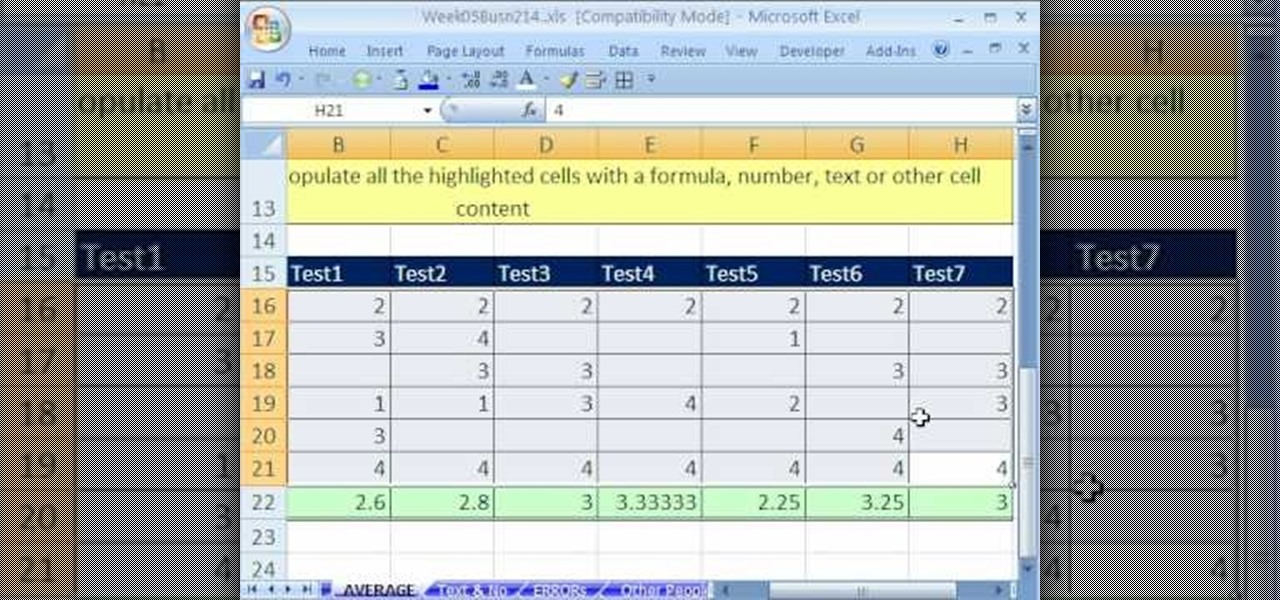
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 25th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to interpret and resolve the nine most common Excel formula errors — namely, ####, #NAME?, #N/A, #REF!, #VALUE!, #NUM!, #DIV/0!, Circular Reference, and #NULL!.
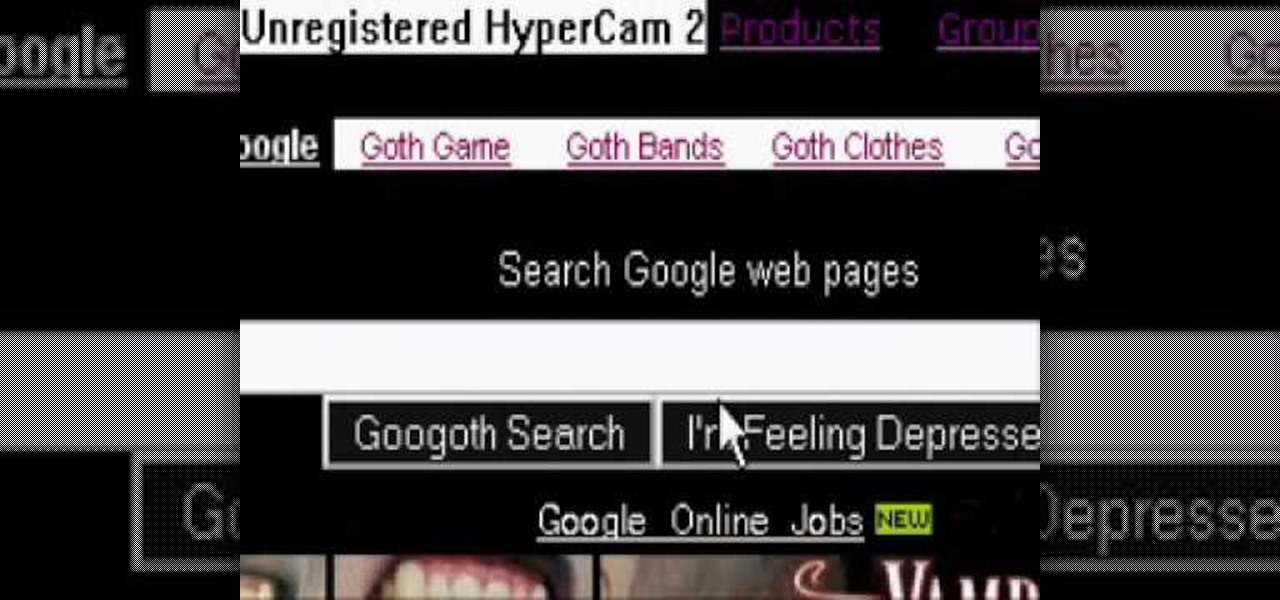
The Google logo is more than an image at the top of the website, it's a full blown brand. You can boost yourself to that status (at least on your own computer) by changing the logo to your name or anything else you want it to say. This video will show you the different ways you can change the Google logo.
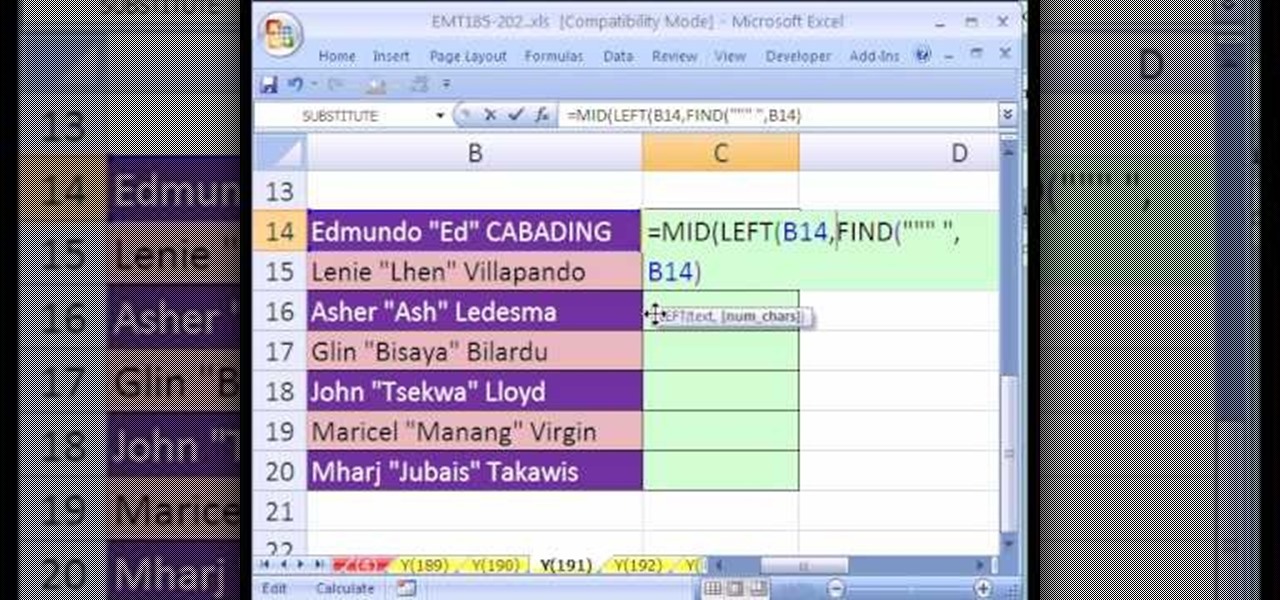
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 191st installment in their series of digital spreadsheet magic tricks, you'll learn how to how to extract part of a text string using a formula with the functions MID, LEFT and FIND.
In this video, we learn how to delete hidden driver viruses. First, scan your computer with anti-virus and try to delete the virus that is harming your computer. If you have done this and your anti-virus can't delete it, download HijackThis from Trend Secure. Go through the download stages and install the new software. Now, open up HijackThis on your desktop. Once it's opened, open up the "misc tools" section. After this, click on "delete a file on reboot". Now, write the virus location name ...
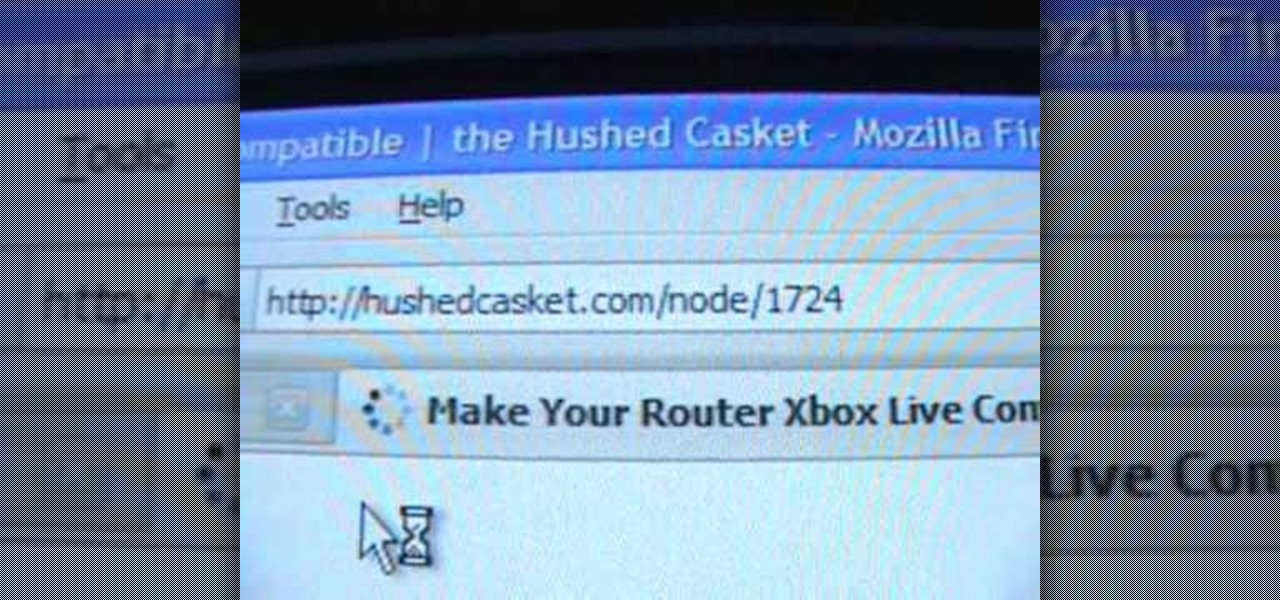
Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...
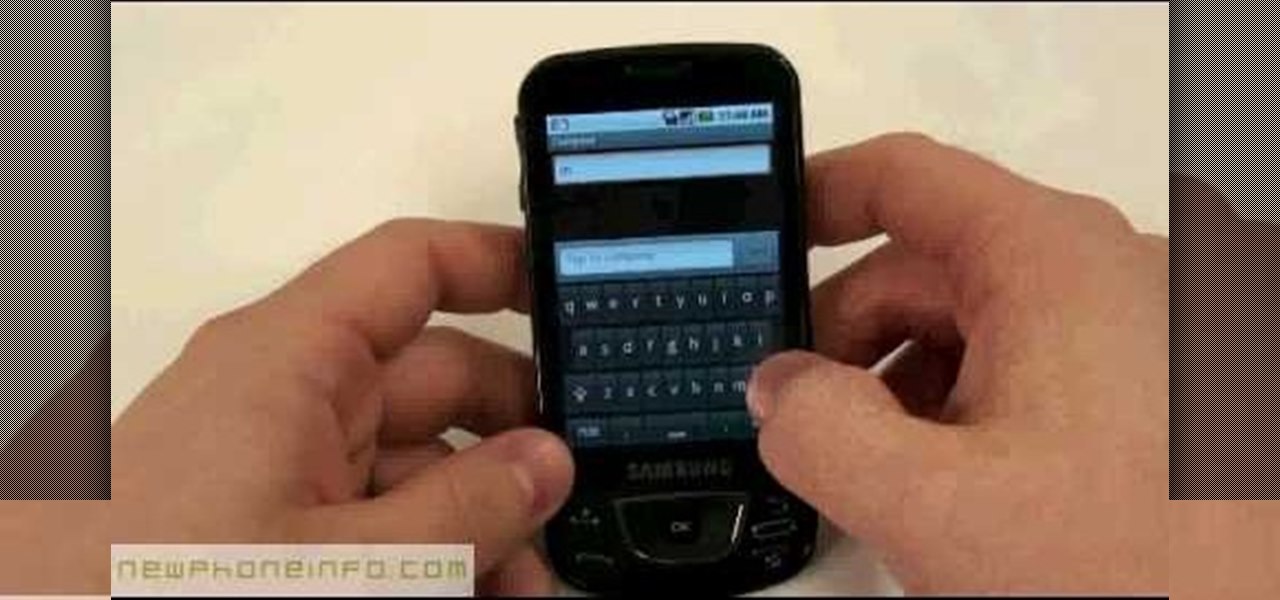
This video will show you how to send a text message with the Samsung Galaxy I7500. Just follow these simple steps to start sending text messages from your Samsung Galaxy I7500: From the home page, tap the messaging icon. Select "New Message" Tap the "To" field and enter either the name or the number of the person you wish to send a text to. Type in your message, and when you are done, tap the "Send" key.

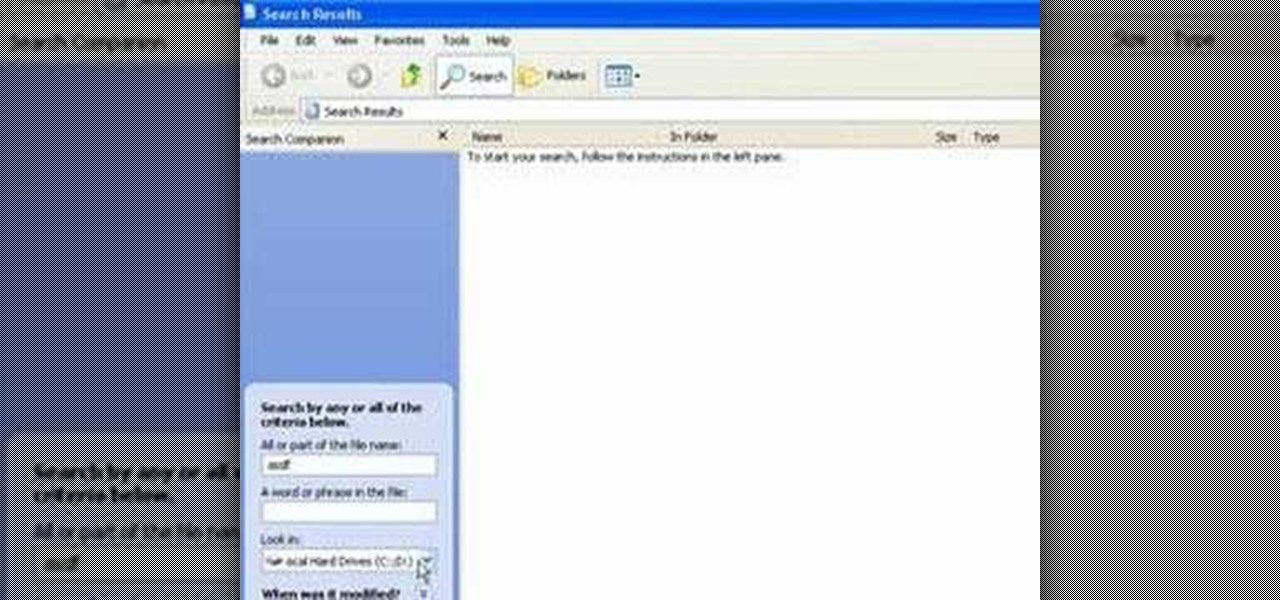
In this video tutorial, Mike shows how to find a missing file in Windows XP and Vista with three different options. In the first option, open Windows Explorer or My Computer. Then open the recycle bin to check for your missing files. If you don't see your file there, close the recycle bin and go to Start and then Search. Look for your file by searching for the file by name to find the location of your missing file. You don't have to know the entire file name to do a search. If that does not w...

Yorkshire pudding is an English side dish that is traditionally served with roast beef. But don't let the name fool you, it isn't a pudding at all, but a gorgeous fluffy bread / muffin.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.

We jumped on the bacon explosion bandwagon! The name says it all, it combines two of America's favorite things: bacon and explosions. This is the most unhealthy meal you can ever eat. It is made with bacon, ground beef and sausage, then deep fried.

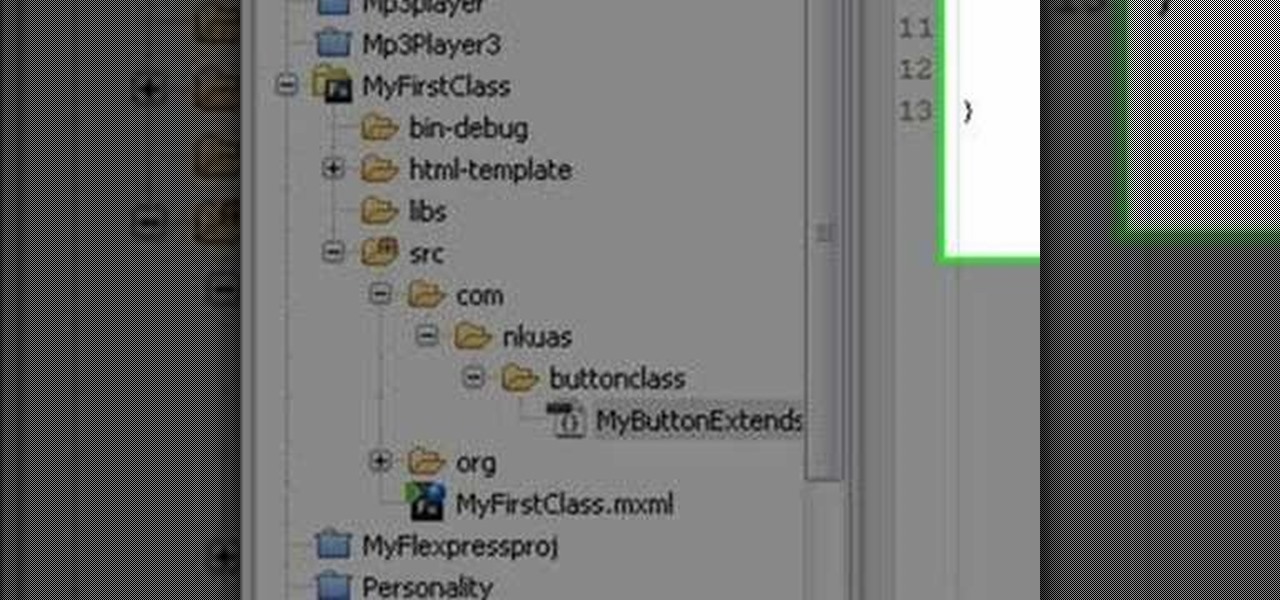
In this programming tutorial, Mike Lively of Northern Kentucky University explains the six parts of a Flex 3 class. He demonstrates how to create and extend a class using Flex 3, and how to bring that class into a Flex project using xmlns name space. Learn how to work with custom classes in this beginners Adobe Flex Builder 3 tutorial.

What are the names of basic picks? How do you use them? Check out this instructional con video that provides an overview of the basic pins used in lock picking. All picks can be put into two basic categories, raking picks and single pin picking picks. Learn the names of the various picks and how to use them with this tutorial video. Learn the basics and start lock picking like a pro!

Learn how to apply a makeup look inspired by Keira Knightley from the premier of Pirates of the Carribean: Dead Man's Chest. The products used for this look are Dark Brown Shadow (the palette's so old, the name's rubbed off... any dark brown shadow will do), Gold Shadow from the Profound Palette, Champagne Shadow from the Profound Palette, Maybelline Define-A-Line eyeliner in Ebony, MAX Factor Volume Couture Waterproof Mascara in Rich Black, Sonia Kashuk blush in Royal Rush, and Covergirl Lip...

This Zbrush 3.1 tutorial covers using layers and Alpha Shapes and a plugin named imageplane3 by Marcus at Pixologic.com to create a shield in Zbrush. You should already know the basics of working in Photoshop.

The buttonhole stitch is used in many types of hand embroidery - general surface embroidery, crazy quilting, whitework and cutwork, Mountmellick embroidery, needle lace, filet work - you name it, buttonhole stitch fits in somehow. It's a super versatile stitch, and once you have the basic stitch down, it's just a matter of applying it in a variety of ways. Watch this video from Needle 'n Thread to see how it's done.

The original daiquiri, a lime-and-rum drink invented in Cuba in the late 1800s, is named after a beach near the city of Santiago. Ah, what those sun-baked bathers would have given for this frosty version of the Cuban classic!

This will show you how to make a desktop icon that instantly shuts down your computer. If you change the picture and name of the icon it can be a great prank as well!

Watch to learn how to say the names of the days of the week in French. lundi - Monday

Elephant toothpaste is the name given to the catalyzed decomposition reaction of 30% hydrogen peroxide that uses soap to collect the oxgen gas that is produced. It is a favorite of most students at chemistry shows.

Learn how to say some basic expressions in French, including "what's your name?" and "I don't know." The instructor is a native French speaker.

When it comes to powerful punches, sangria—which takes its name from the Spanish word for "blood"—packs a truly wicked wallop. But don't take our word for it; mix up a batch and let the fiesta begin.

This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.

If you don't have one of those fancy brand name stain removers you could always use 100 ml of milk to get rid of that red wine stain on you shirt. It works on white clothes as well.

Board game enthusiast Scott Nicholson reviews a new game each week showing you the pieces and rules of play, as well and demonstrating the game with friends. This weeks game, Mah Jong, is an ancient Chinese game about collecting sets. Don't confuse this with the tile picking game on your computer of the same name!

Sosh and Gina continue your Lindy Hop education. This clip will teach you how to communicate with your partner. The front to front, the sling shot, the scissor kick, the swing out, the big turn, are all dance moves distinct to the Lindy Hop. It was named for Charles Lindbergh and his Atlantic crossing in 1927. Black communities invented the moves, and the popularity spread throughout the world.

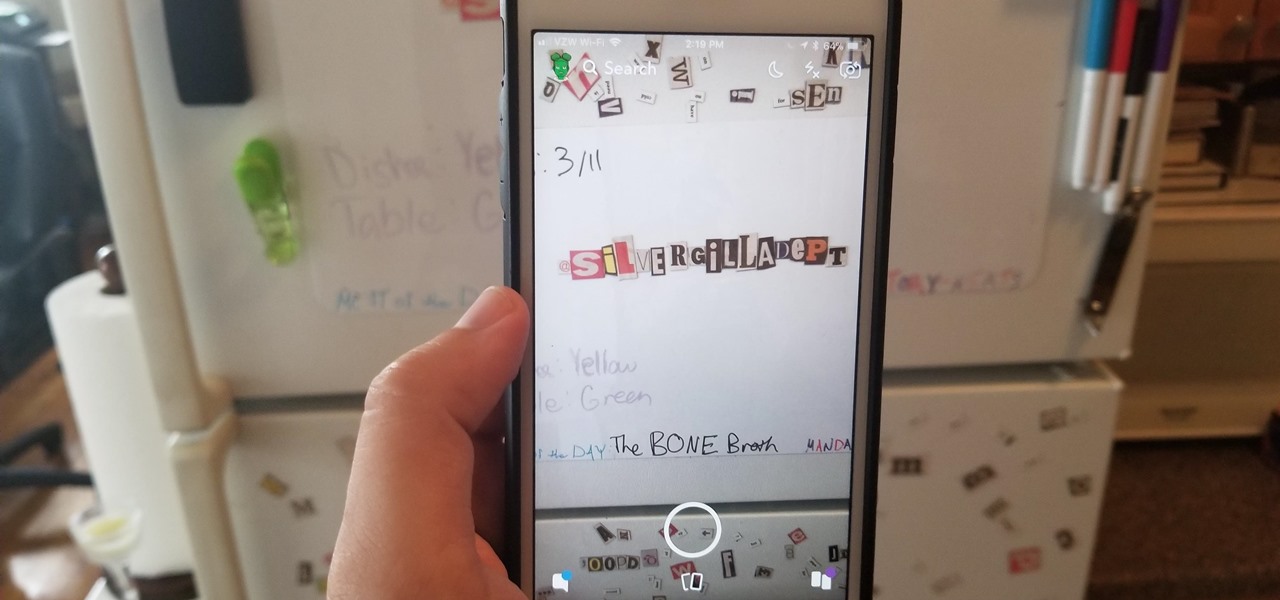
Along with the awesome early-2018 addition of Giphy GIFs in Snapchat, you can now share other people's Snapchat handles and tag them in a way that lets others reach those people easily — something you couldn't do before in the app.

Playlists are a vital feature for any music streaming service. For many, the ability to add and organize songs into the perfect order is a deciding factor in which streaming service to choose. The folks at Tidal (including owner Jay-Z) certainly recognize this, as they've provided users with the tools to not only create perfect playlists, but edit them as well.

Google loves to play games. That's just what they did when they went ahead and teased us with a few Android O hints after Reddit user Zitroney unlocked an Easter egg in a Google Creative Lab developer's app ShortStories.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

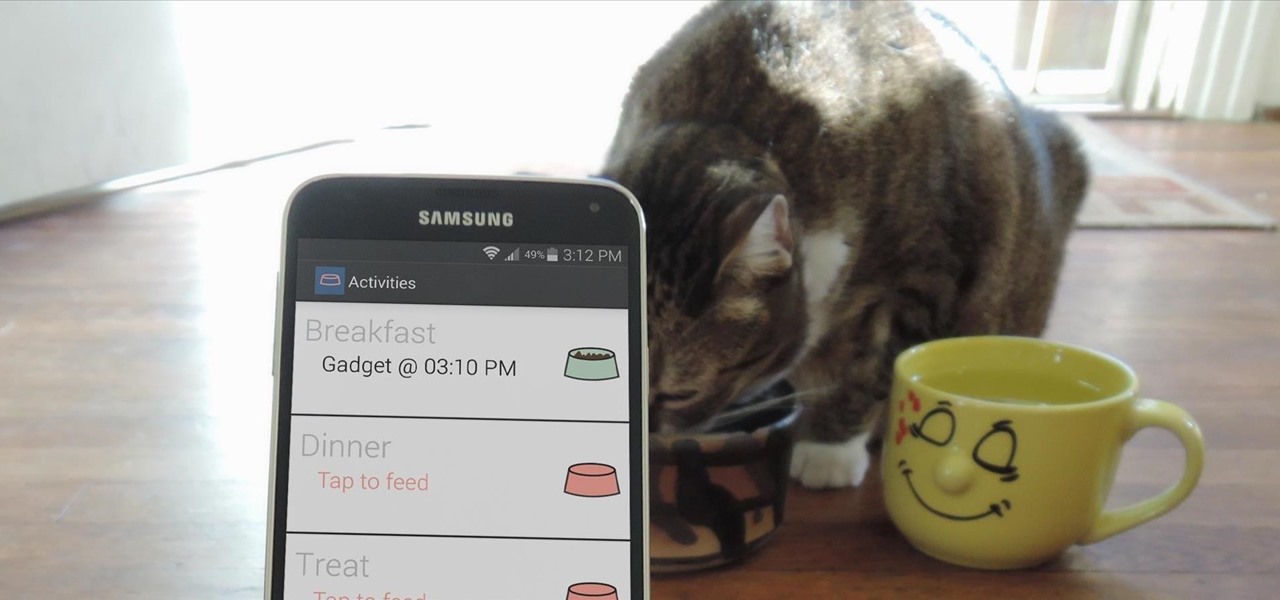
Pets are one of the biggest sources of joy in life, but keeping track of their daily activities can easily become a chore. When you have a roommate or spouse that also likes to feed the cat or walk the dog, miscommunication can lead to double-feeding or an under-exercised pet.

Since the release of the Galaxy S5 back in April, the process of converting older models, like the Galaxy S4, to replicate the look and feel of the newest S-family member was inevitable. Galaxy users didn't want to be left out, and for good reason. The revamped interface of the S5 introduced a new color palette that was a definite improvement from the flat boring colors on older models.

Amid rumors of a 6-inch phablet Nexus and the impending release of Android "L", Google posted—then quickly removed—a trio of ads for their industry-leading mobile OS.

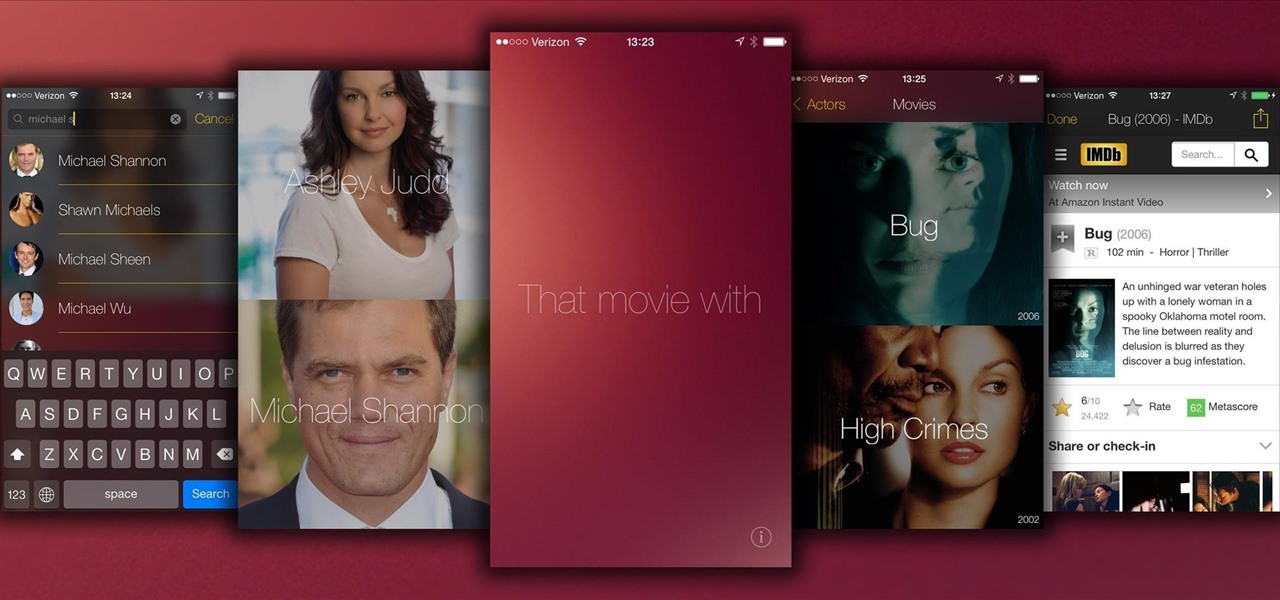
There have been countless times where I'd be racking my brain over the name of a movie I saw, and I don't like giving up. Usually, a few specifics can be remembered, but not enough to come up with a title on my own.
This how to will show you how to program a fairly simple Hacking bat file. First open notepad.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Some of my Facebook status updates are absolutely hilarious, and sometimes (though rarely) even my friends updates can get me on the floor laughing. And like most of you, I'm sure, when you come across something funny—you have to share it.

Mining is an important part of Minecraft, after all, it's in the name. This video will show you how to build a basic mine cart station. Mine carts are a great way to move objects through your world, or you can hop on and take a ride yourself.

Kate Middleton may have to wait to get married before she's called "Princess" but she has already been named a fashion icon. You can follow in her fashionable footsteps- watch this video to learn how to get Kate's elegant look.