Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Instagram stories are a great way to share your day-to-day experiences with your followers. However, it can be disappointing to see them go after 24 hours, especially if you shared something really special. Now, Instagram has a way for you and your followers to relive those great stories you've created with a new feature called Story Highlights.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

It's not the bacteria itself that takes lives and limbs during invasive flesh-eating bacteria infections. It's the toxins secreted by the group A Streptococcus bacteria invading the body that causes the most damage.

The Centers for Disease Control and Prevention (CDC) just reported some upsettingly high numbers of human papillomavirus (HPV) in adults. In data retrieved from 2013–2014, 22.7% of US adults in the 18–59 range were found to have the types of high-risk genital HPV that cause certain cancers.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

Some bacteria can already do it—generate electric current, that is—and those microbes are called "electrogenic." Now, thanks to the work of a research group from the University of California, Santa Barbara, we know how to easily turn non-electrogenic bacteria into electricity producers.

Any developer working with the HoloLens knows that the fight for polygons is a very real conflict. For all of the magic it creates, the HoloLens is a high-powered mobile device that has all the typical processing limitations of a mobile device.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Smelly foods are what make my culinary world "go 'round," so to speak. I grew up with fish sauce, learned to cook with and love fermented beans and veggies, and am one of the biggest garlic advocates I know... other than my husband, who thankfully shares the same smelly food sensibilities. (Let's put it this way: anyone that can stomach stinky tofu can handle anything I could possibly cook up.)

Whether your holidays are cause for celebration or exhaustion from over-celebrating, alcohol is more often than not involved in the merrymaking. We at Food Hacks are very fond of enjoying this particular indulgence in lots of different ways.

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Cooking Steak directly on the coals with no grill. Given many different names including caveman steaks or dirty steaks, this method involves placing the steak directly on red-hot lump charcoal to obtain a fantastic texture & taste that's as good as most restaurants.

Whether you drive a new or used car, discovering a new dent, scratch, or scuff mark can send you into a frustration spiral. While there are many DIY ways to deal with dents, scratches and scuff marks are trickier because using the wrong stuff could make your car's paint job look even worse.

For some odd reason, the Netflix app likes to disable the Nexus Player's built-in screensaver. It doesn't use its own, it simply keeps your screen on indefinitely, which of course can lead to screen burn-in. This is not just an Android TV issue, as the Netflix app does the same thing on Roku and smart TVs.

This video has 7 fraction hacks that can save you time when working with fractions. The hacks are: Adding fractions without a LCM

Hello, my name is PortalsUnite I made a mod review about a awesome minecraft mod called The Incredibles mod. I would appreciate it if you checked it out, liked, shared and subscribed. Feedback is always welcome!

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

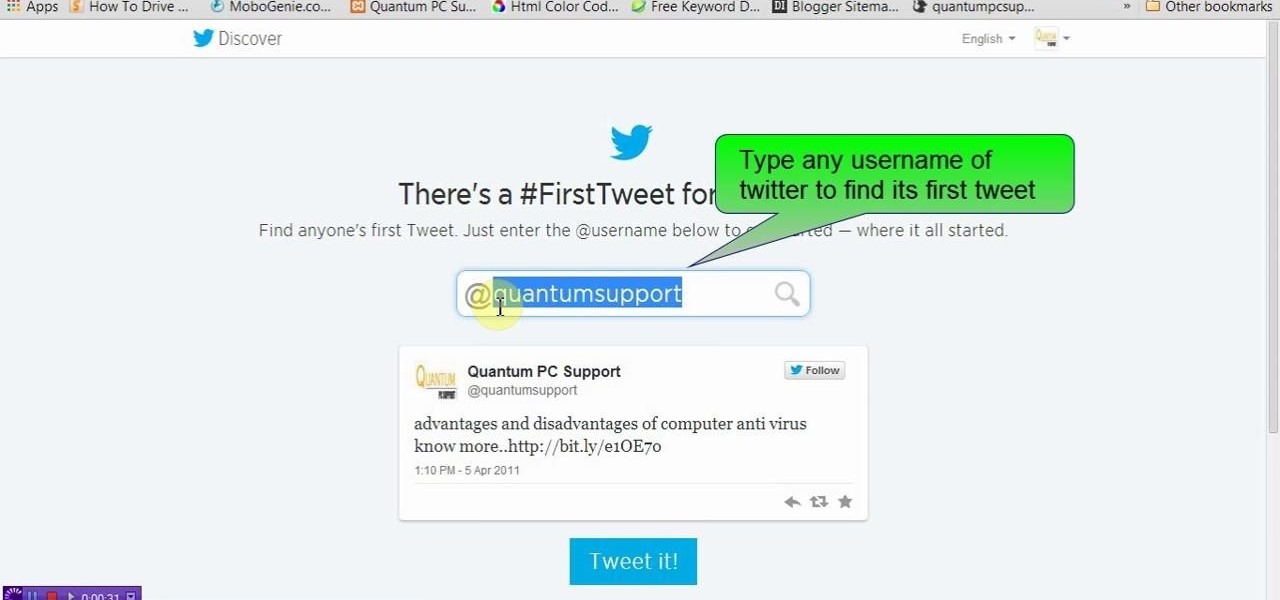
This tutorial video will show you how to find first tweet of any user in Twitter. You have to type first-tweets.com in address bar of your browser. The site will be redirected to discover.twitter.com/first-tweet page. Just type any user name and twitter will show the first twit of that user. Watch the video and try it yourself.

This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

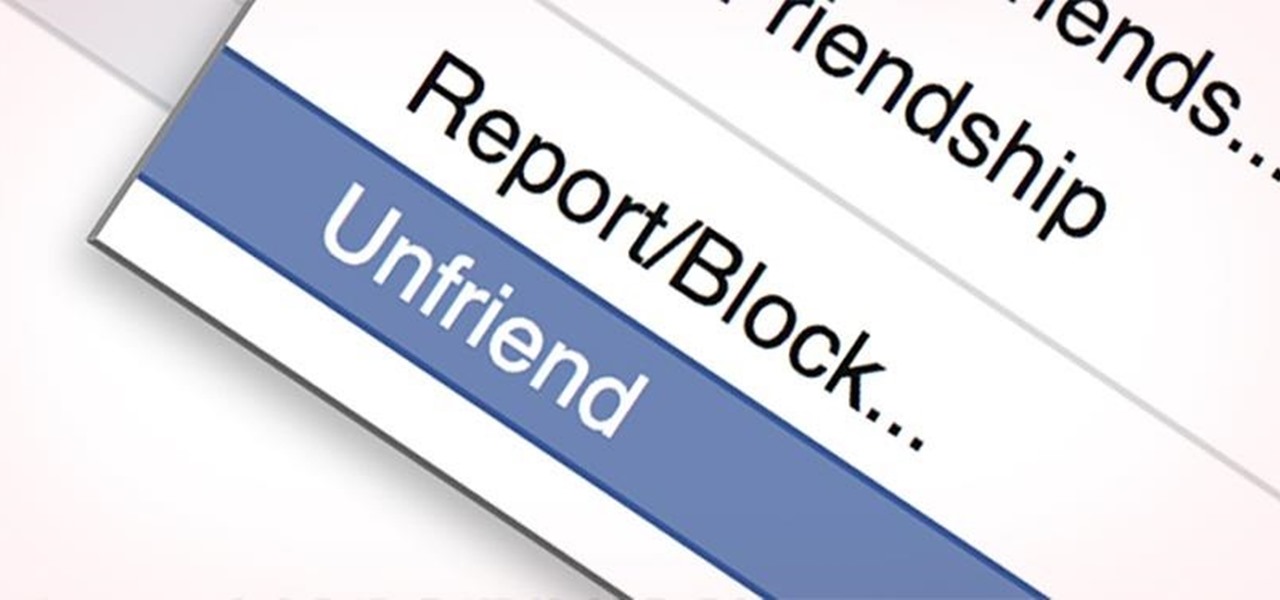
Admit it: you haven't talked to more than 70 percent of your Facebook friends in the last year. Whether you barely know the names crowding your friends list, or have vague memories of high school Spanish class with them, Facebook friends are easy to find and difficult to get rid of.

In this video I'm turning the pages of a magazine about Macrame. Relax, unwind, and enjoy this old journal about Macrame. I hope some ideas from the Magazine come in handy. (Name of this journal: "Masche Die Makramee" 1984)

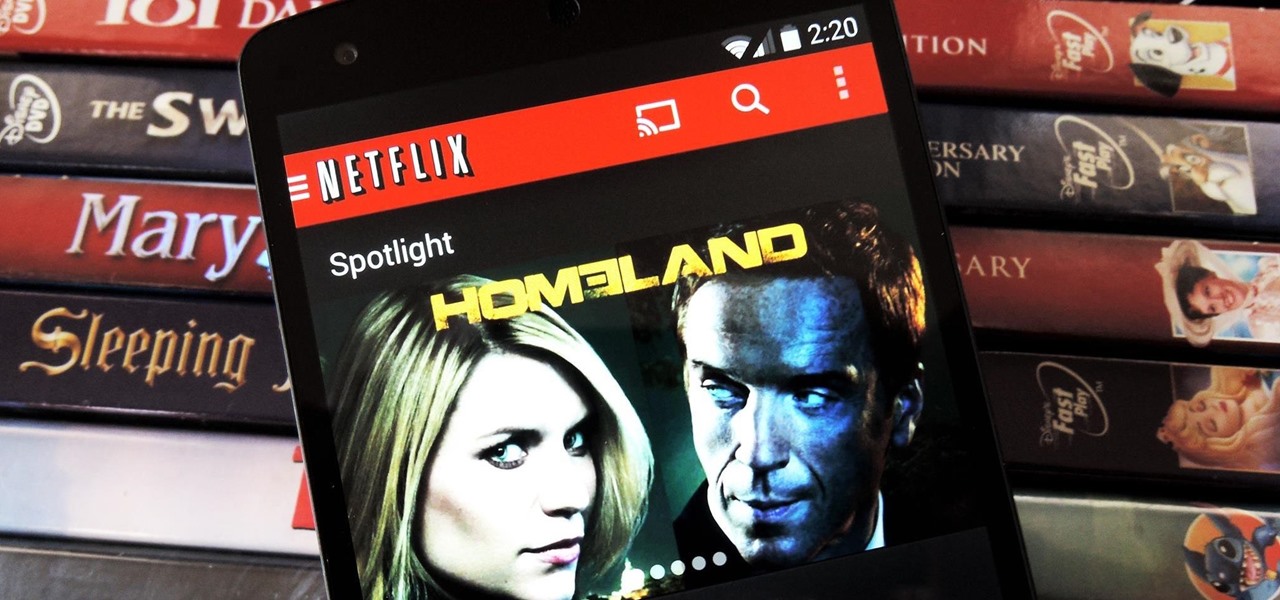
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Hi again everyone, this lesson will be about the names of body parts in Lebanese Arabic. I hope you will enjoy it and find it interesting. Have fun and don't forget to share it if you like it :)

The Alternating Half Hitch is tied to form a chain, also called a sennit. Other name of this knot is the Chain Stitch or Zig-Zag braid. This knot can be used to make a simple bracelet or necklace and other items can also be made with this knot.

in this Zipper bracelet is used Half Hitch knot or oldest name - Basket Stitch. They can be used as part of plant hangers, or to make belts, bracelets, and other items. This is very easy to make (: can be used as a friendship bracelet and good for beginners :)

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

Matthew Whelan changed his name to "His Royal Majesty Body Art, King of Ink Land" and he is a strong supporter of body branding and face branding. He even got his eyeball tattooed!