
How To: Lead a double life
Whether you want to juggle two wives or keep you alter ego separate from your day job, here are the precautions you must take. Learn how to lead a double life.


Whether you want to juggle two wives or keep you alter ego separate from your day job, here are the precautions you must take. Learn how to lead a double life.

While you can't make a silk purse from a sow's ear, you can make a rose out of a single square of paper and call it whatever name you want. Origami is, of course, the traditional Japanese art of paper-folding to create any shape imaginable. Make a rose when you don't have the money to buy someone the real thing, or even as a gift that will last. Watch this video crafting tutorial and learn how to origami a folded paper rose.

Check out this instructional home repair video to learn how to identify and find your manufacturer's label and model number on your refrigerators and freezers. The model number is usually essential. People make the mistake of assuming that the name and number on the front panel is all you need. Many fridge and freezer manufacturers use the model number as well as the serial number. Most have the ID plate inside of the door by the salad bowl, while some hide it behind the kick plate at the bas...

Scosche Industries offers this instructional users guide for its TA07 radio replacement interface in a 2007 Toyota Tundra. The TA07 will work with select 2004 and up Toyota vehicles equipped with JBL and JBL Synthesis systems. The TA07SR radio replacement interface was designed to make installation of any brand name aftermarket head-unit simple. The TA07SR allows the customer to replace the factory head unit with an aftermarket head unit and utilize their factory amplifier without having to "...

Check out this cool video and learn how to create the Allassonic effect with a coffee cup, instant coffee and boiling water. When the bottom of a ceramic cup filled with boiling water and a heap of instant coffee is tapped at regular intervals the pitch of the sound heard slowly increases over time.

In this dance how to video, Larry Payne demonstrates the sissone a la seconde ferme (to the second position closed), then en avant (in front), finishing with a "changement." The step sissone is named for the person who invented it. ballet move. This is a basic move for the beginning ballet dancer. Follow along with this dance tutorial and you can do the sissone a la seconde ferme ballet move.

James Bond might have switched to margaritas if he had ever taken a sip of this cocktail. Never forget the ingredients, the drink name is an acronym. Tequila, orange liqueur (Cointreau), orange juice, 7-Up and lime make up the 007 margarita cocktail. Follow along with bartender Alex as he gives step by step directions for how to mix up this citrus-y specialty drink. Watch this video beverage making tutorial and learn how to mix the 007 margarita cocktail.

This tutorial cooking video will teach you to make Japanese Kaisendon, a Japanese Sashimi rice bowl.

This tutorial video will teach you how to make Bukkake Udon, also known as Japanese cold udon noodles.

This tutorial video will teach you to make Zenzai and Anko, two Japanese red bean sweet treats. Ingredients for Zenzai and Anko

Now give us a good reason why the grown-ups should be left out when the kids eat that yummy Mac ‘n’ Cheese! Here is a recipe for ‘Desi’ Mac (macaroni and cheese), as the name suggests, is full of flavor and other goodies that you will be proud to eat as well as serve your family! Watch this how to video and give macaroni and cheese a grown up Indian flavor.

Susie Henderson, owner of Auntie's Beads, explains how to be successful in the bead industry. Learn how to make up business cards, get the business name out there, display the product, have the product ready, and how to present the product nicely. Watch this instructional video series and follow along to pick up these great business tips.

Well, it's up to interpretation as to whether this video shows you how to solve the Rubik's cube the easiest way. Use the set of Rubik's cube algorithms shown to you in this how-to video:

This how-To video shows you how to make an attractive and romantic centerpiece for your wedding, engagement party, or shower. A lovely mirrored acrylic heart with the couple’s first names, also in mirrored acrylic, is the center point. Turn off the lights and light up the tea candles for that romantic moment! Coordinating ribbon, metallic paper poof flowers, and onion grass lend accents. This is also suitable for Valentine’s Day, Sweetest Day, anniversaries, and other romantic events.

Tamra Davis shows you how to make different coconut macaroons. Watch and see how simple it is to make these holiday cookies. They are so simple to make, all you need is three ingredients: egg whites, shredded coconuts, and sugar.

The BLT sandwich dates back to late Victorian Tea Sandwiches. The acronym, BLT comes from diner waitresses and cooks who abbreviated the sandwichs name at busy lunch counters across America. In its simplest form, the BLT brings together a delicious combination of flavors. To make my ultimate BLT you will need: thick-cut slab bacon - you can use turkey bacon for a leaner alternative, butter lettuce and arugula, red ripe tomato, your favorite bread, mayonnaise and blue cheese dressing. I think ...

Tech tends to move forward without looking back, but that doesn't mean new is always better. One feature that dominated mobile phones in the late '90s had made a comeback thanks to Apple, and you can take advantage of it on your iPhone when making calls.

Apple offers many ways to customize the Home Screen on your iPhone, from adding widgets and scheduling rotating wallpapers to hiding apps and entire pages. But some of the best ways to customize your Home Screen are options Apple won't even tell you about, either because they haven't become official features yet or because Apple is OK with the workarounds.
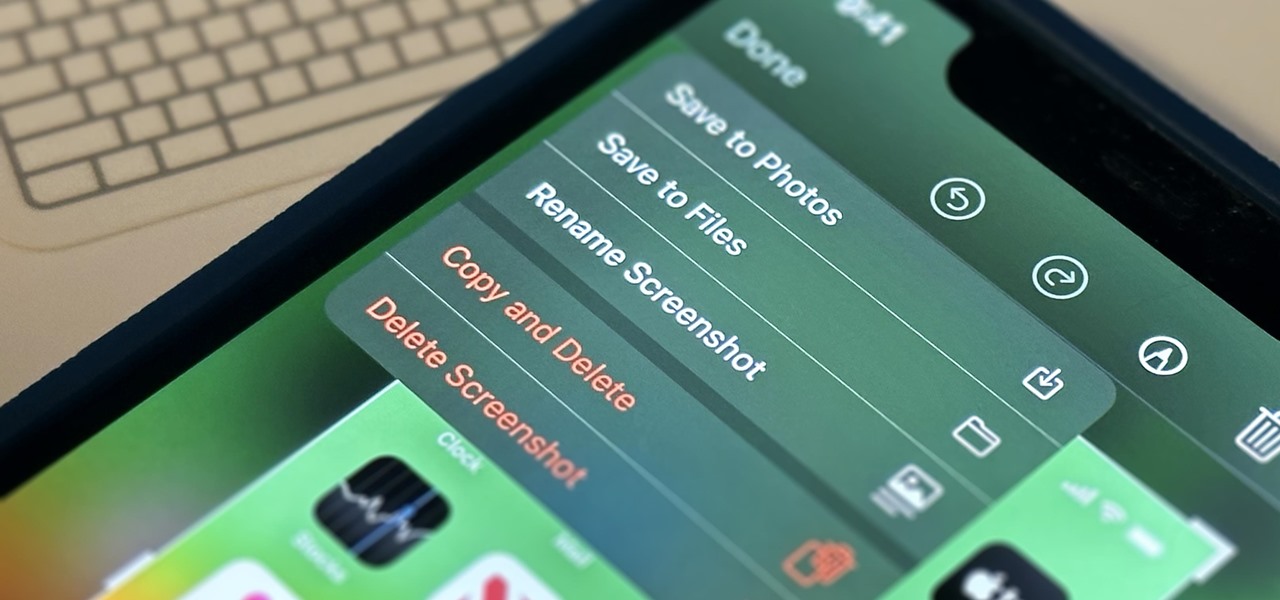
Apple's screenshot feature is a near-perfect tool for saving images of your iPhone's screen to keep for yourself or share with others. But iOS is missing one thing that would make it almost flawless: a way to rename your screenshots from their original IMG_1234.PNG file name.

In recent years, Apple has made it much easier to customize the Home Screen on your iPhone or iPad, and some of the newer tools are perfect for neat freaks. Nonetheless, a tidy Home Screen can still feel cluttered when iOS and iPadOS force widgets, apps, and folders to have names — but a few workarounds can help you remove some of those icon labels for good.

The initiative known as Project Aria has been the focus of curiosity around Facebook's augmented reality plans ever since Mark Zuckerberg revealed the device around this time last year.

One of the biggest bummers about Netflix is the inability to create different lists for your favorite movies and TV shows. Instead, you're only able to lump titles into the single default "My List," and that can be impossible to browse. It doesn't separate titles into categories or genres, and titles are arranged for you automatically, so there's not much room for customization.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.
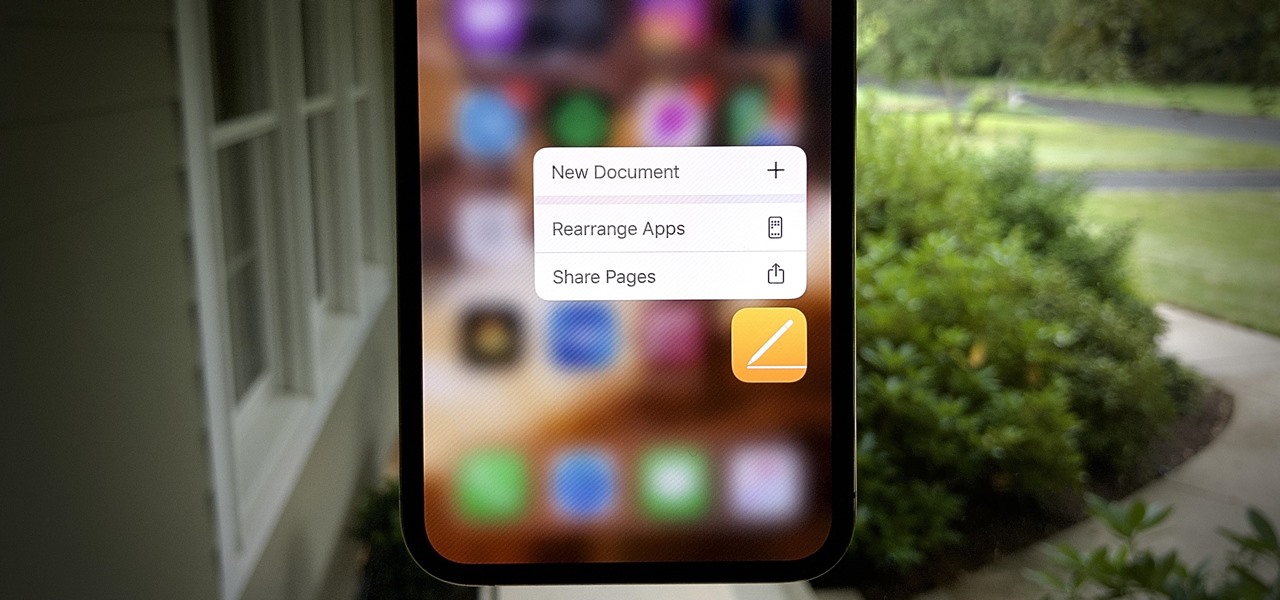
We're basically living in the future, so let's work like we are. For decades, we have, without question, opened a word processor like Pages, and clicked or tapped our way to starting a new document. What's wrong with that? It's unnecessary. We all have a digital assistant living in our iPhone, one that can start up a new Pages doc by verbal request.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.
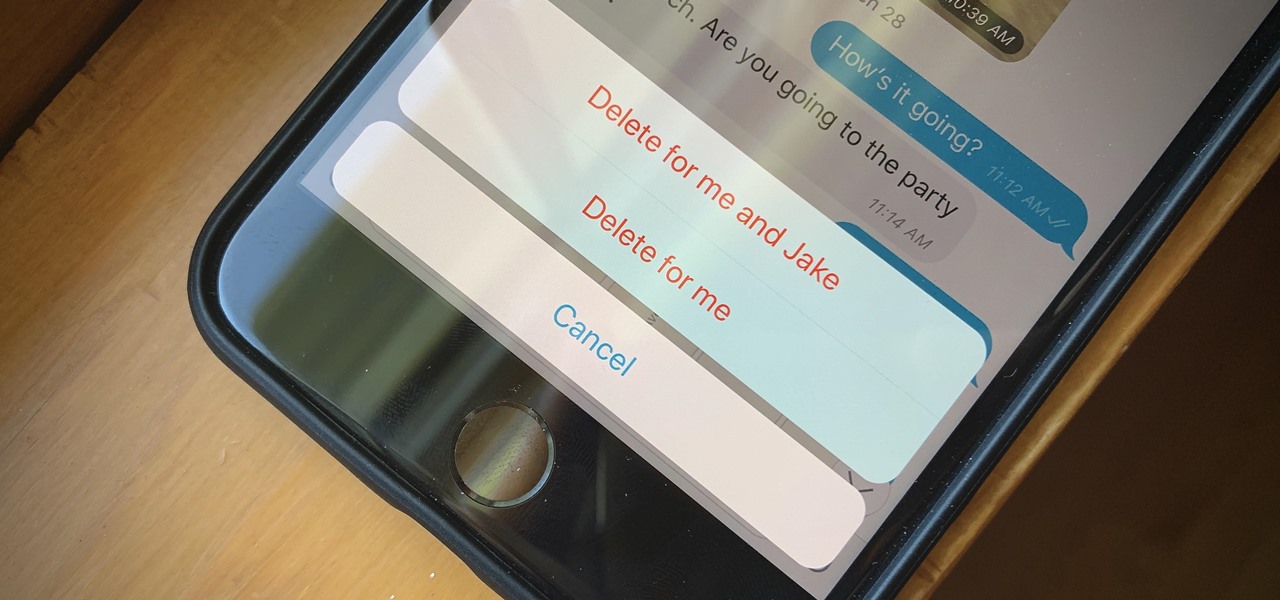
If you're looking to keep your conversations private, look no further than Telegram. Its cloud-based chats are secure and its optional end-to-end encrypted chats even more so, but you can't really prevent someone in the conversation from sharing your messages. However, you can lessen that chance by taking back your messages, deleting them for both you and the other end of the discussion.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.
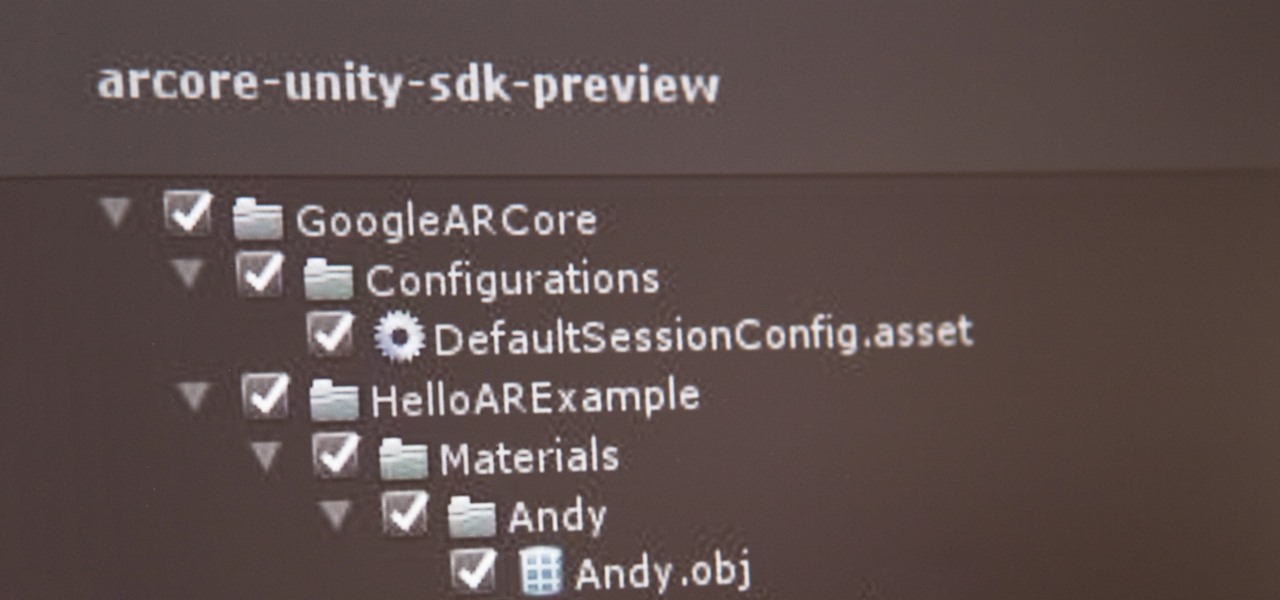
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.
If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...
When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.