Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

Is this what happens when lightning hits sand? It turns out that when lightning hits sand, it makes little holes in it. Sadly, this picture was part of an internet hoax that circulated in 2013.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

One shrinks their nose when the name of Durian fruit is brought up but are you aware of all the health benefits it can provide? The Durian fruit on its own can help control Blood pressure, blood sugar, Anaemia and depression. Not only this, the fruit has the miraculous qualities that can prevent cardiovascular diseases, better the digestive system, better the Libido and provide instant energy. For all the skin conscious people, here's news for you! The fruit can delay ageing process and make ...

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

To play Minecraft with mods you will need to install Forge. Most people think this is hard to do, not so. It is very simple and in less than 5 minutes you can be playing Modded Minecraft.

A man by the name of Marc Kerger is out to prove that he's the number one fan of the game TETRIS by building a playable TETRIS shirt for the game's 30th anniversary.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

This is for people who are already proficient at doing basic pull-ups and chin-ups and want to take their training to the next level. It's also pretty funny for anyone who enjoys a bit of gym humor.

Learn how to make a paper origami teo flower instructions. This origami flower is my improvisation, and I haven't seen any similar flower from the nature. I named the flower to my wife Teofila (Teo) because i gave to her the first model of a complete paper flower :). The model is easy and the stamens make the flower looks one idea more beautiful :)

Say "hola!" to the independent Finnish phone company, Jolla, and its new eponymous smartphone of the same name.

On June 5th, robotics firm Aldebaran and SoftBank Corp., the Japanese giant that owns Sprint (and possibly T-Mobile), unveiled an emotion-sensing robot named Pepper.

Video: . Iconici Tv MMA Host Naiya Marcelo caught up with with Bellator middleweight fighter Brian Rogers "The Professional Predator" at Factory X Muay Thai/MMA/BJJ Gym in Englewood CO.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

This magical, glowing mixture is very strange, with an equally strange name (Oobleck), because it feels like moldable pizza dough in your hands one second, and like liquified goo the next.

Video: . How to Remove a Callous from your Feet.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

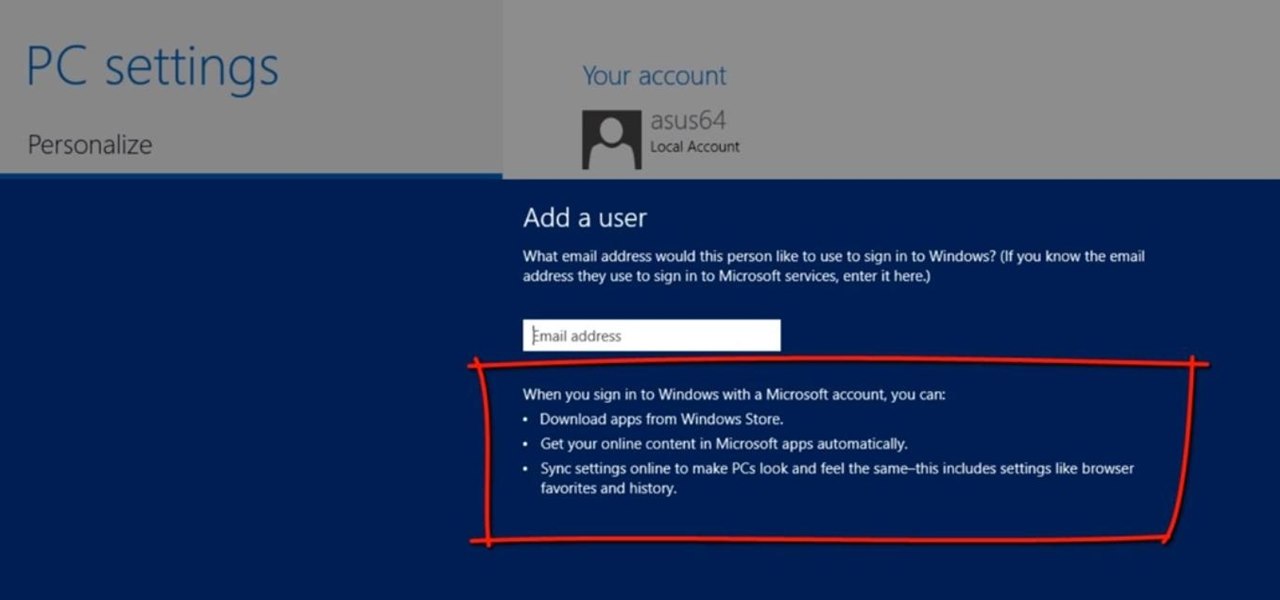
This Windows 8 tutorial will show you how to create a local user account on your PC. When you create a local user PC account, you will only have access to your account from that individual computer. A local Windows 8 user account uses a user name and password to login.

Video: . Steel wool fire Photography

When I started this nail design, I really didnt know what I was going to end up with, and much later till the design was posted, I didnt know what to call it either ! But a viewer noted that it is a very christian style because of the cross and the arches that look like the windows of a church, and lots of others talked about the cross on the ring finger . With a bit of help and lots of ideas, I eventually names this design Christian Dior Nails - Blue Cross Glam Nail Art Design with Easy Abst...

RonyaSoft Poster Designer software includes lots of different ready-to-use templates. You can freely change anything you want in the template or you can just print it as it is, if you don’t want to puzzle over it. Moreover, you can create your own poster from scratch.

In this video series, CGI Animator will teach you how to make a waving flag using the computer program Cinema 4D. Learn all about particles and deformations, planes and cylinders, how to build a leaf, how to run the wind emitter, how to form a flag, and how to integrate all the processes.

As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.

This how to video shows you how to make a name centerpiece for your bar or bat mitzvah, wedding or engagement party, corporate event, etc. Get your name out in front where it can be admired with this table decoration tutorial.

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

Bowling is such a fun group activity and is perfect for birthdays and other types of gatherings. However, if you are not a pro bowler the scoring system can be pretty confusing. This tutorial will walk you through the steps of keeping score so you will know a strike from a spare and everything in between.

Bid Whist can be a fun game for family or friends. It's challenging enough for adults, but enjoyable for kids too. Bidding and predicting wins are what make playing Bid Whist fun and exciting, whether you win or lose.

The last time the English language for Siri received new voices was in iOS 14.5, and there was one new male and one new female selection, bringing the total to four available options. In the iOS 15.4 update, there's a fifth one, and it may work better as a gender-neutral middle ground between the low-pitched male voices and high-pitched female ones.

One of the oldest electronic musical instruments is the theremin, a synthesizer that generates sound based on hand gestures, as featured in the classic "Good Vibrations" by the Beach Boys.

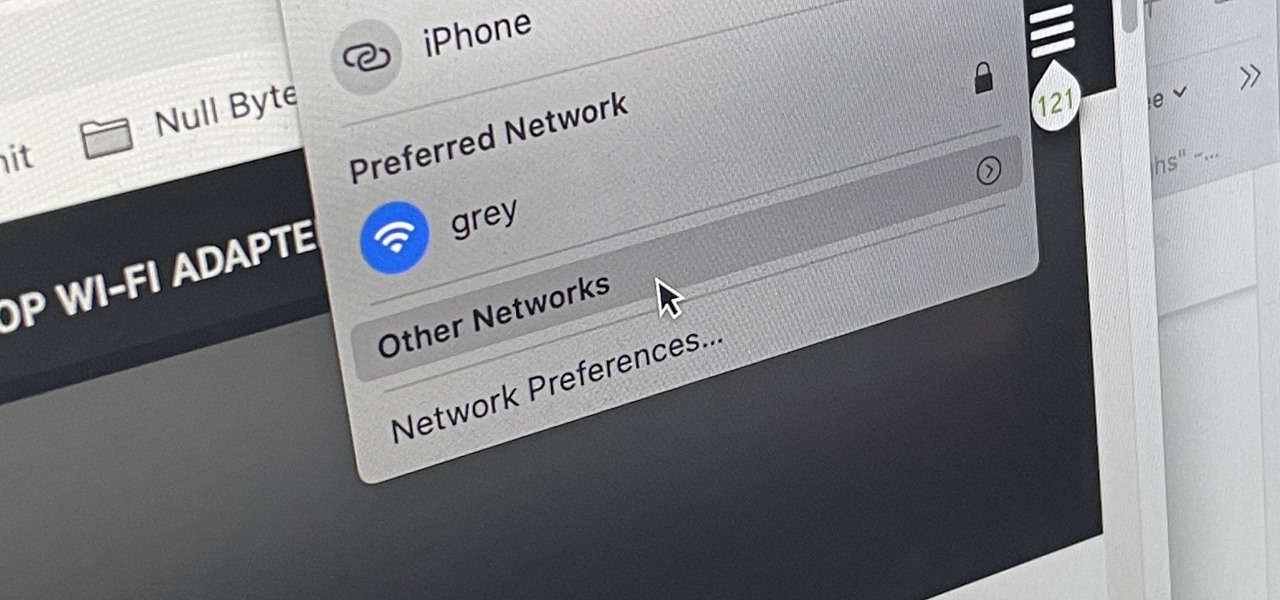
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

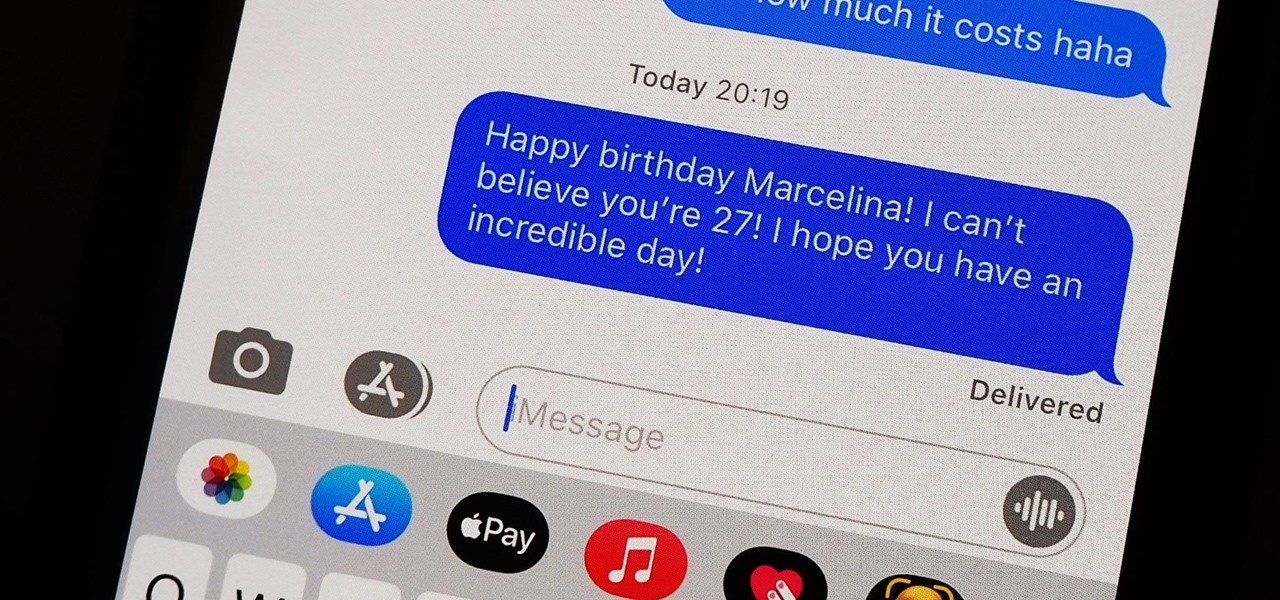
You should know the birthday for a parent, sibling, child, or significant other, but there are just too many people in your family and contacts to remember everybody's yearly birth anniversary. Still, everyone expects you to remember their birthday. To stop looking like a jerk, go a step further than putting birthdays in your calendar and make your iPhone help you send birthday wishes when their big day pops up.

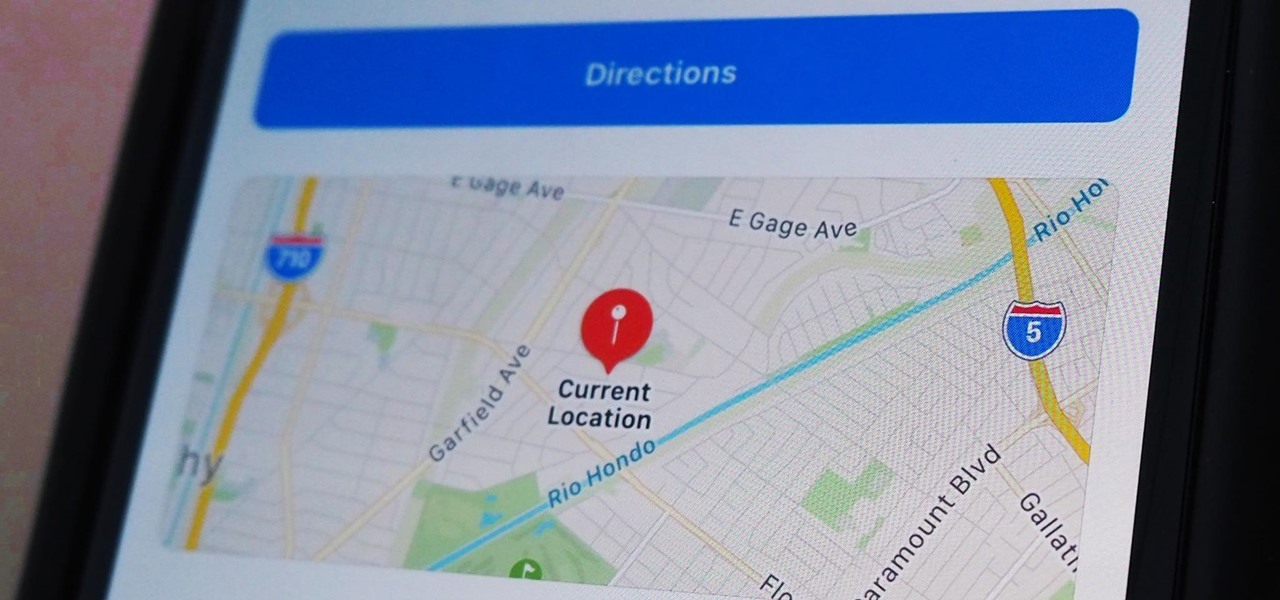
Apple makes it simple to share your location with your family and friends using tools built into the "info" page for each conversation thread in Messages. With those tools, you can send your current location or share trackable real-time coordinates. But iOS always has a few hidden tricks to make things easier than they seem, and that's precisely the case if all you need to do is share your current location.

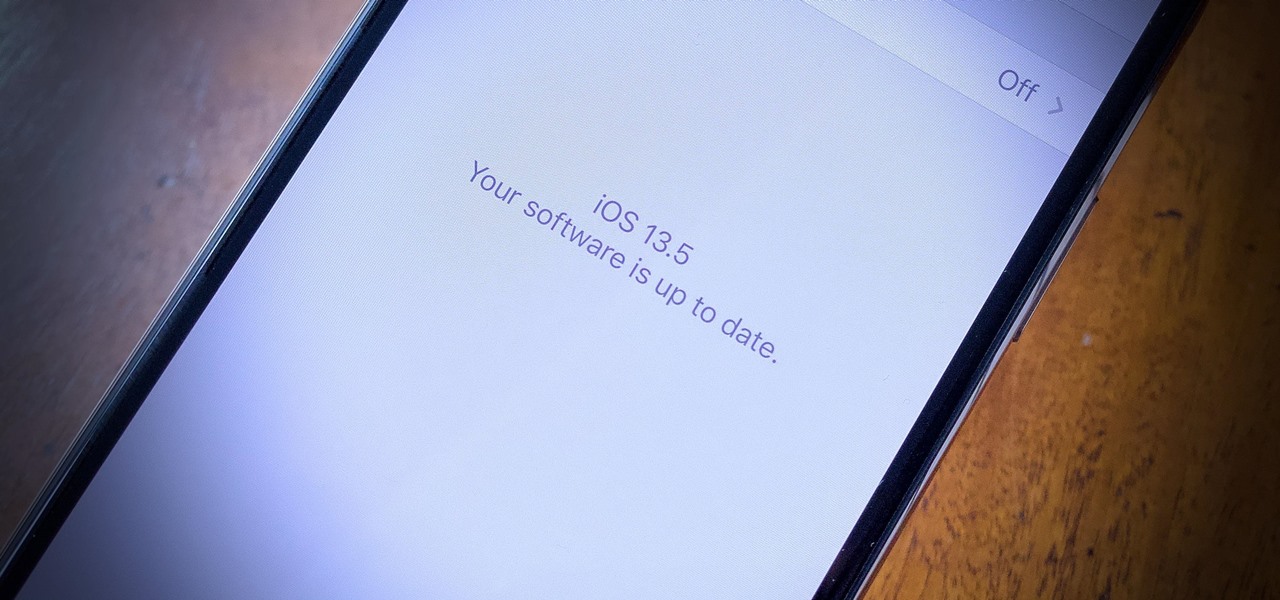
Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.

If you're a public beta tester, you woke up this morning with your iPhone running iOS 13.4.5. Today, Apple released the second beta for iOS 13.5. No, Apple didn't skip a version — 13.5 public beta 2 is essentially 13.4.5 public beta 2. So why the name change? Apple included the first API for its joint COVID-19 contact-tracing and exposure notification program with Google.

If you're considering purchasing Apple's new 2020 iPhone SE, which brings many modern components into the compact body of an iPhone 8, you should know what its dust and water resistance rating means. Just how dirty and wet can the iPhone SE get without breaking any functionality?

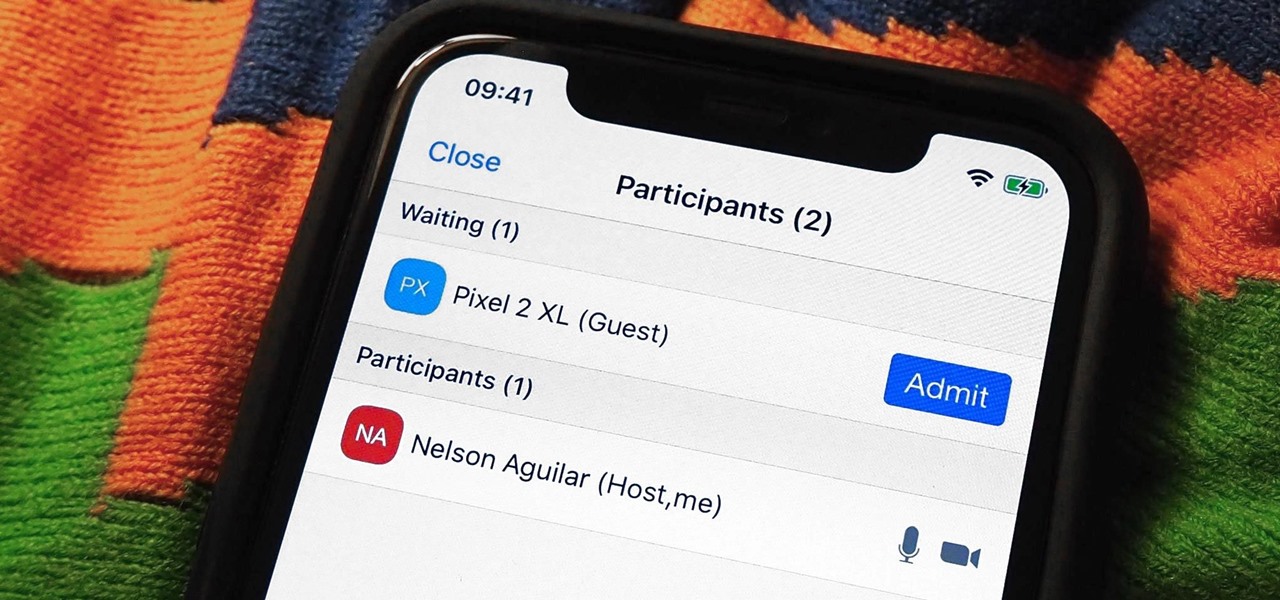
During a meeting in real life, you could ask non-essentials to exit the room temporarily so that you can speak to just a few privately, but now that conferences exist online, it requires a bit more finesse. You could start a new video call on Zoom or remove individual participants, but that makes it hard for those who left to join again. But there is a feature where you can just put some users on hold.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.