Most of us have already had an encounter with the Epstein-Barr virus, or EBV, for short. As part of the herpes family, it's one of the most common disease-causing viruses in humans. We get the disease with (or without) some nasty symptoms, then we recover. However, EBV stays in our body after the illness has ended, and it's one of the few viruses known to cause cancer.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

Three variants of the Pixel 2 have appeared in Google's Android Open Source Project (AOSP) code, confirming various suspicions about which processor will power the Pixel 2.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

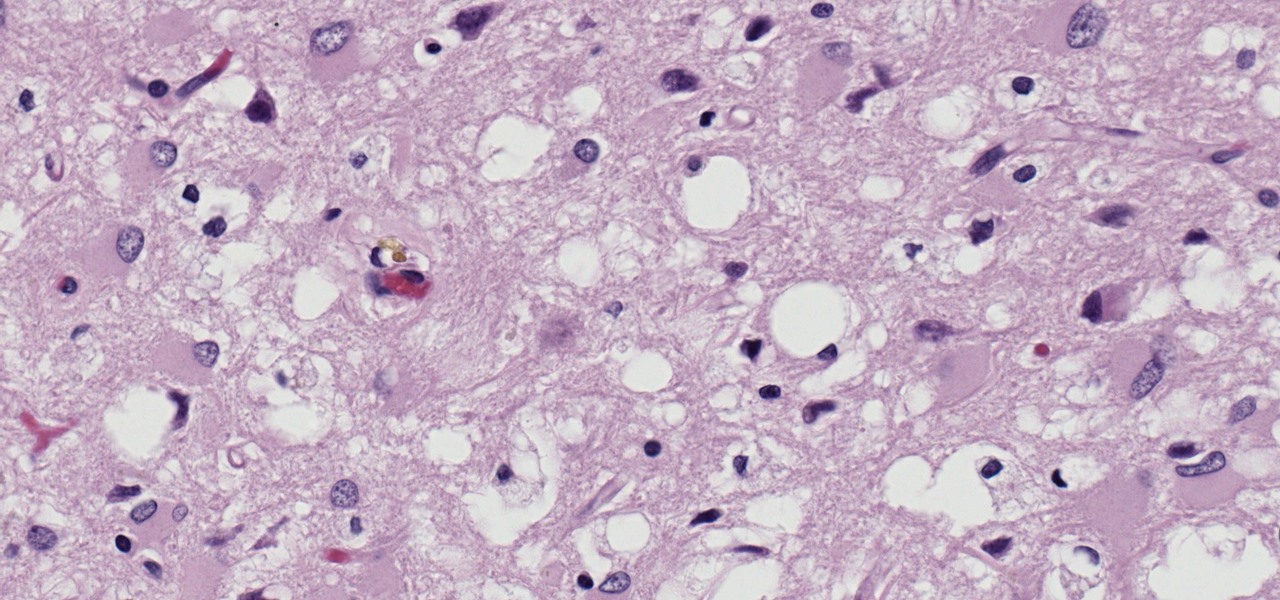
Prion diseases are a group of infectious brain diseases that causes extensive tissue damage, resulting in sponge-like spaces in brain tissue. Prions include Creutzfeldt-Jakob disease in humans, bovine spongiform encephalopathy (often called mad cow disease), and chronic wasting disease in hoofed ruminant mammals.

You know the signs—sneezing, fever, nagging cough, no energy, no appetite. It's the flu, but this time, it's your dog who's down and out. Yes, dogs get the flu, too. However, a team from the University of Rochester Medical Center and their collaborators have developed a new vaccine that may make the doggy flu a thing of the past.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

A company known as Cyanogen, Inc. has been in the news numerous times over the past year, and almost every time their name is brought up, it's amid reports of an impending doom. The writing is on the wall for the makers of Cyanogen OS, as it appears that there is little that can be done to prevent the company from going belly-up in the near future.

The freezer section at your local grocery store may have plenty of popsicle flavors, but they're mostly going to be the same old fruit-flavored varities you've been shoving in your mouths for years. None of those will truly get your tastebuds rolling like some creative homemade versions will. We've already shown you some crazy sounding ones made with Oreos, veggies, and coconut flakes, but now we're back with some more chilling ideas. Just wait until you get down to the corn one!

Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

The sprouts, they're alive! Alive, I tell you—aaaaaaliiiiiive! (Cue dramatic music.) It's true: sprouts are a living food, and they're packed with more nutritional benefits than some raw vegetables. It's easy and fun to grow your own sprouts from seeds, legumes, and grains. Plus, watching them grow is incredibly satisfying—you're bringing new life into the world (and onto your plate)!

Hummus seems like it should be easy to make, but creating that ideal creamy consistency can be pretty difficult. Often it comes out too chunky, which means your hummus won't be good for dipping into. Luckily, there is one trick that will help you create the creamiest consistency and make you never want to go near store-bought hummus again: add baking soda.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

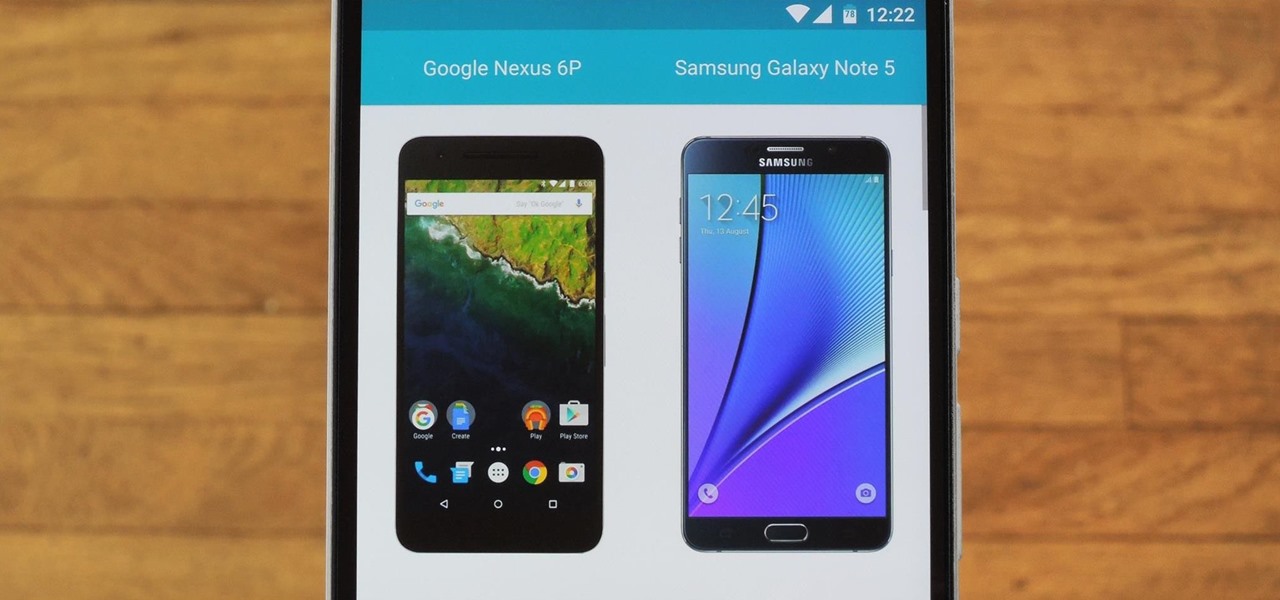
Shopping for a new phone is an entire ordeal. Even when you've narrowed it down to a few choices, comparing the finalists can be difficult, because specs and prices are scattered around on various different manufacturer websites, and if you're trying to do this on your current phone, most of these websites aren't optimized for mobile viewing.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

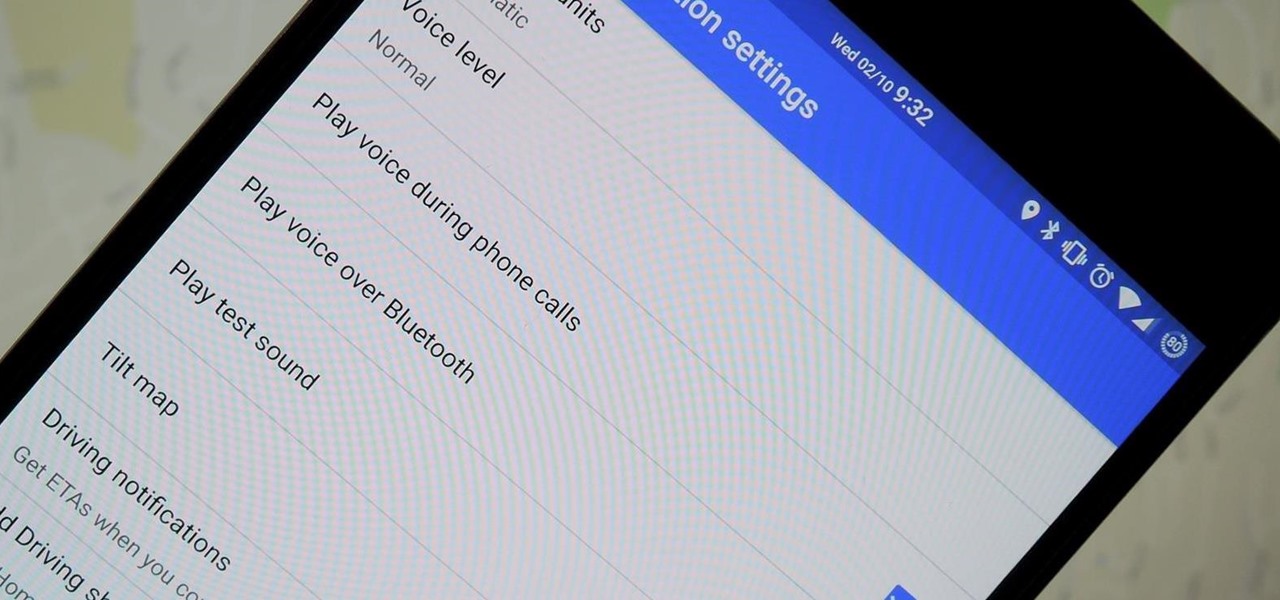
We've all been there. You're driving along with Google Maps pointing the way when you get a call from your friend asking you how much longer it'll be until you show up. You try to offer some lame excuse about how something came up last-minute, but you're interrupted, quite rudely, by Maps's voice guidance. The voice butts in again, and again, and again, to the point that you consider having Maps navigate you to the nearest cliff so that you can drive off it.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Android's main UI is looking so good these days that you hardly ever see developers spend time creating themes anymore. But even with the beauty of Material Design working in our favor now, there's always room for improvement, right?

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

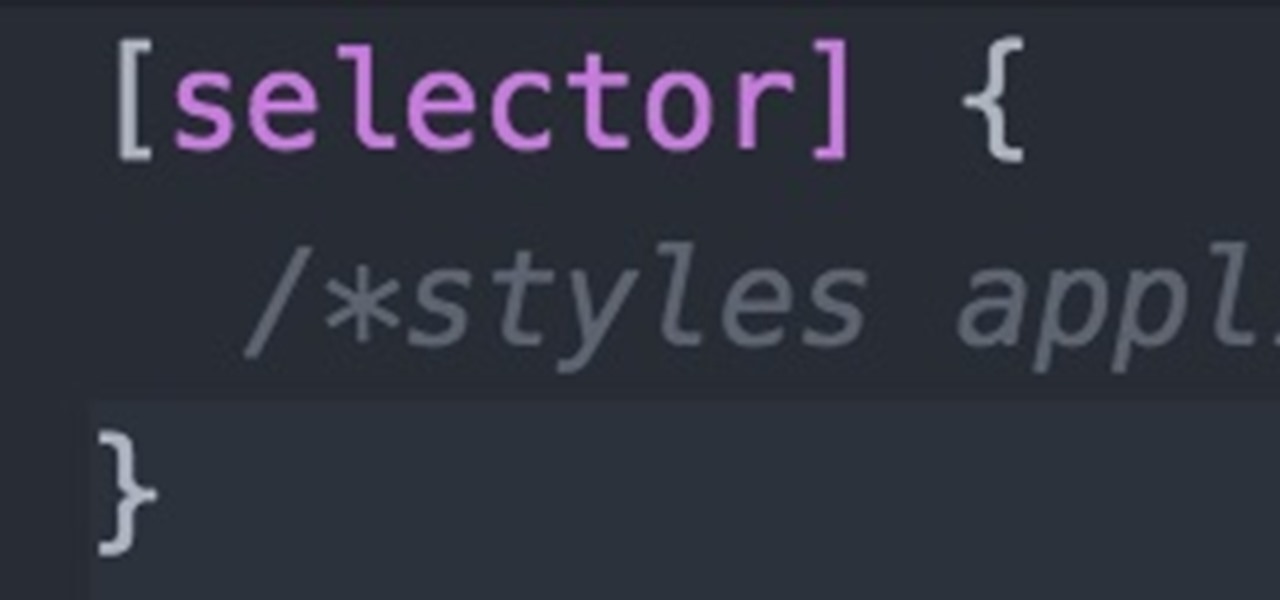
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

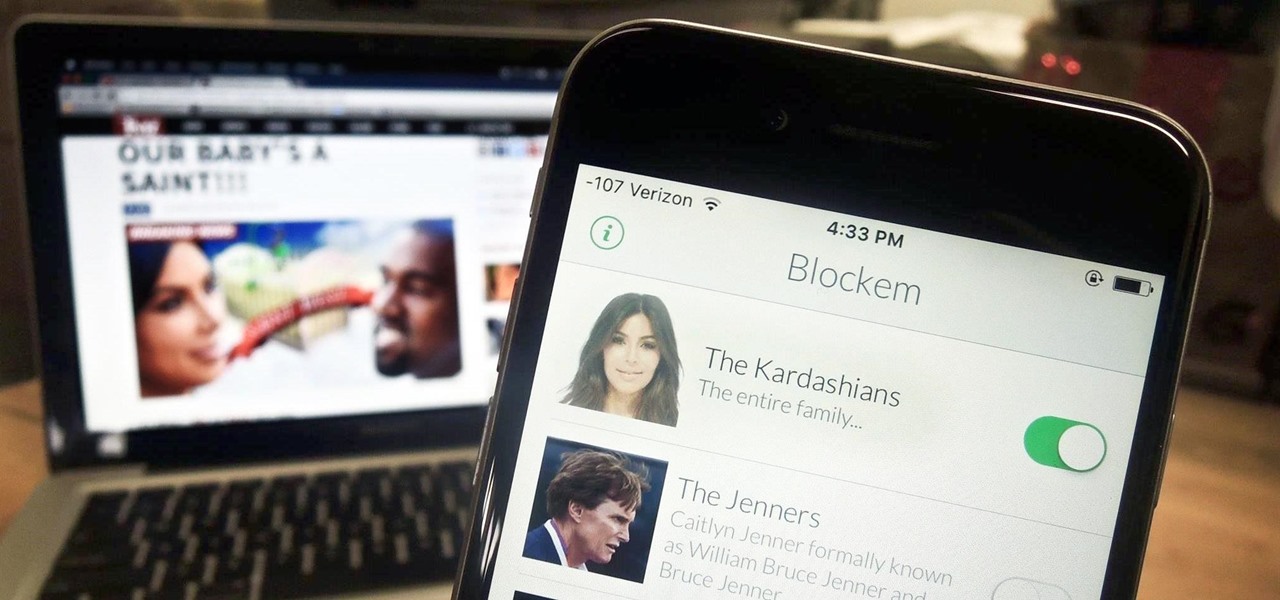
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

When there's a crappy stock app you want to hide, the easiest thing to do is just bury it in the back of a miscellaneous folder. But what if there's an app you want to hide on your home screen that you actually use? For instance, what if you don't want everybody in eyeshot to see what banks you use, or don't want anyone to know about your "dating" apps or porn shortcuts?