
How To: Everything You Need to Know About Mulled Cider
When it's frigid outside, all you can think about is getting inside and shutting out the cold. But sometimes even the largest house can get a bit, well, stuffy.


When it's frigid outside, all you can think about is getting inside and shutting out the cold. But sometimes even the largest house can get a bit, well, stuffy.

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

So, how does someone keep their hacking life completely secret? What This Is:
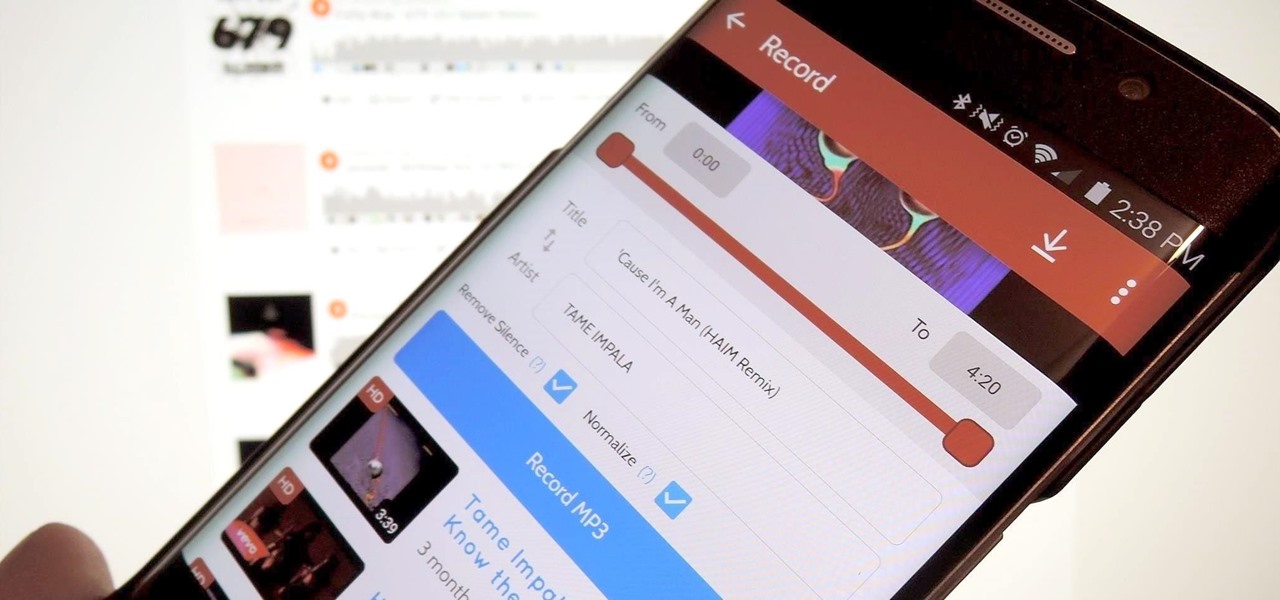
A growing trend for many artists (most recently Kanye West) is to offer exclusive or experimental tracks on music streaming sites like SoundCloud or YouTube before releasing them anywhere else. On rare occasions, some of these great songs never make their way onto an official album, which can be disappointing for die-hard fans who need to download every song available from their favorite artist or band.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

I record close-cropped videos and take macro still shots with my smartphones on a daily basis, so as you would expect, I spend a lot of time cleaning these devices. Over the course of a couple years, I've fine-tuned my cleaning regimen, and at this point, it's down to a near-science.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Cortana, Microsoft's personal assistant for its Windows Phones and Windows 10, will soon be released for Android. That is, officially released. It's hard to keep a good thing locked away, and to that end, Cortana for Android has been leaked, thanks to APK Mirror.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

As it stands, Firefox OS isn't a very popular third-party operating system for Android devices, especially when compared to others like CyanogenMod, but Mozilla developer Fabrice Desré is attempting to change that.

Even the most unadventurous eaters can usually be coaxed to take a bite of an exotic fruit (except, perhaps, the notoriously stinky durian). After all, fruit is sweet, juicy, and filled with natural sugars.

Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.
Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.
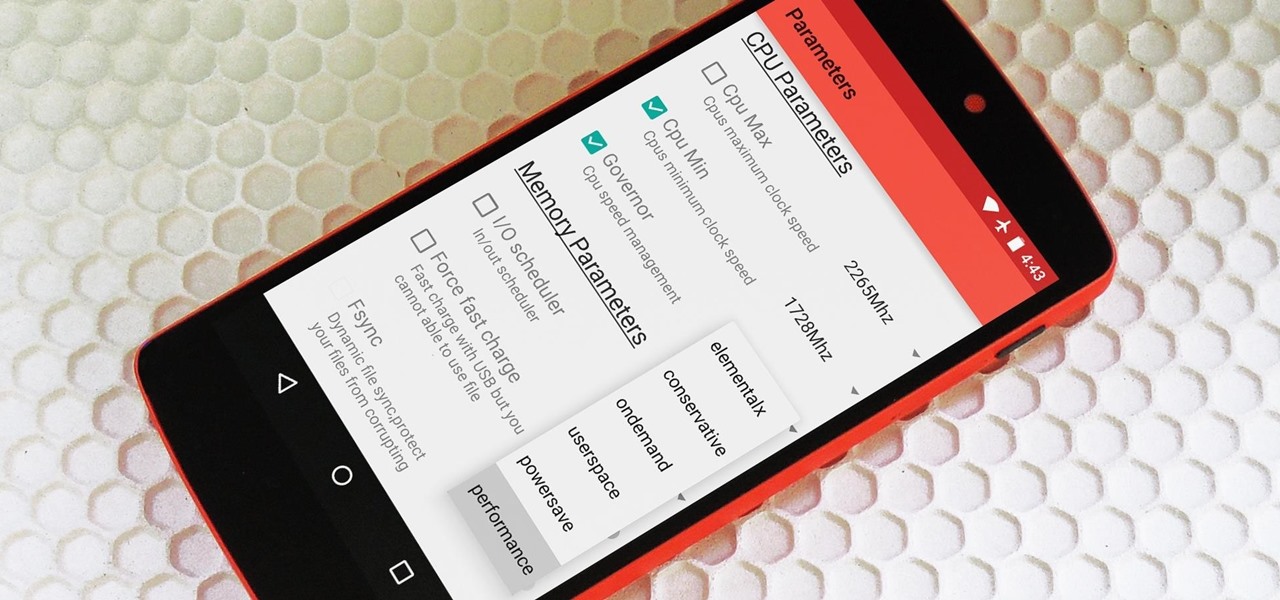
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

Back in the '80s, recording live radio was as simple as popping a cassette tape into your boombox and pressing the record button. While we've come along way with regard to accessing radio stations thanks to websites and apps that stream live broadcasts over the internet, it's no longer quite as easy to record.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.
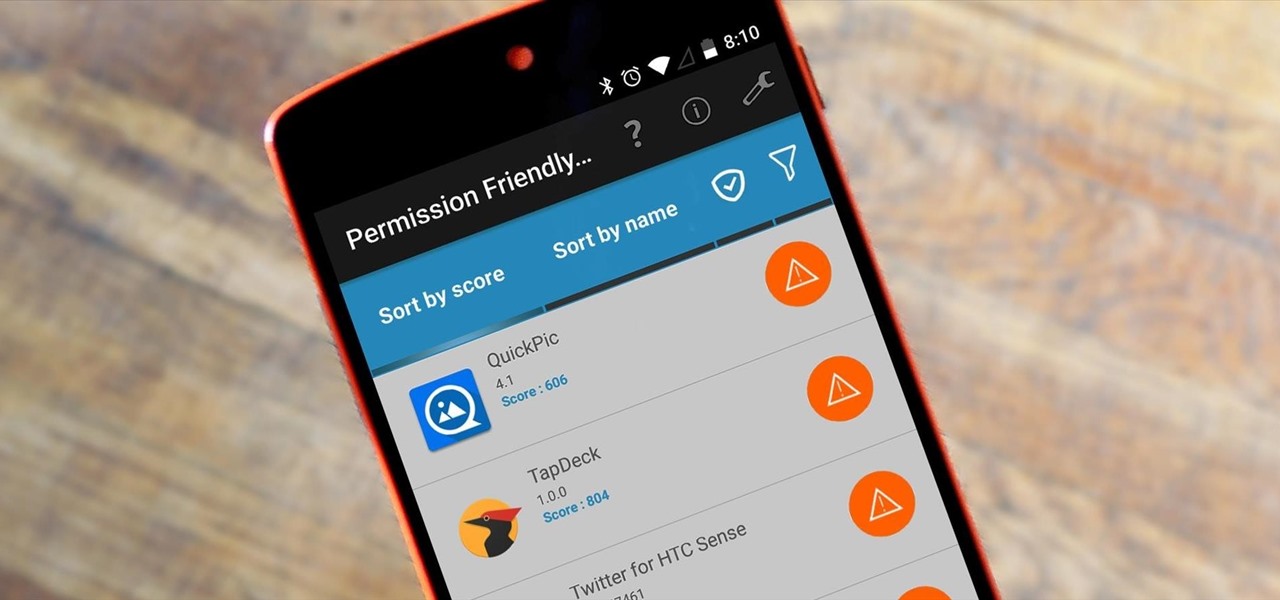
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.

Step 1: Introduction: Hello! Hackers
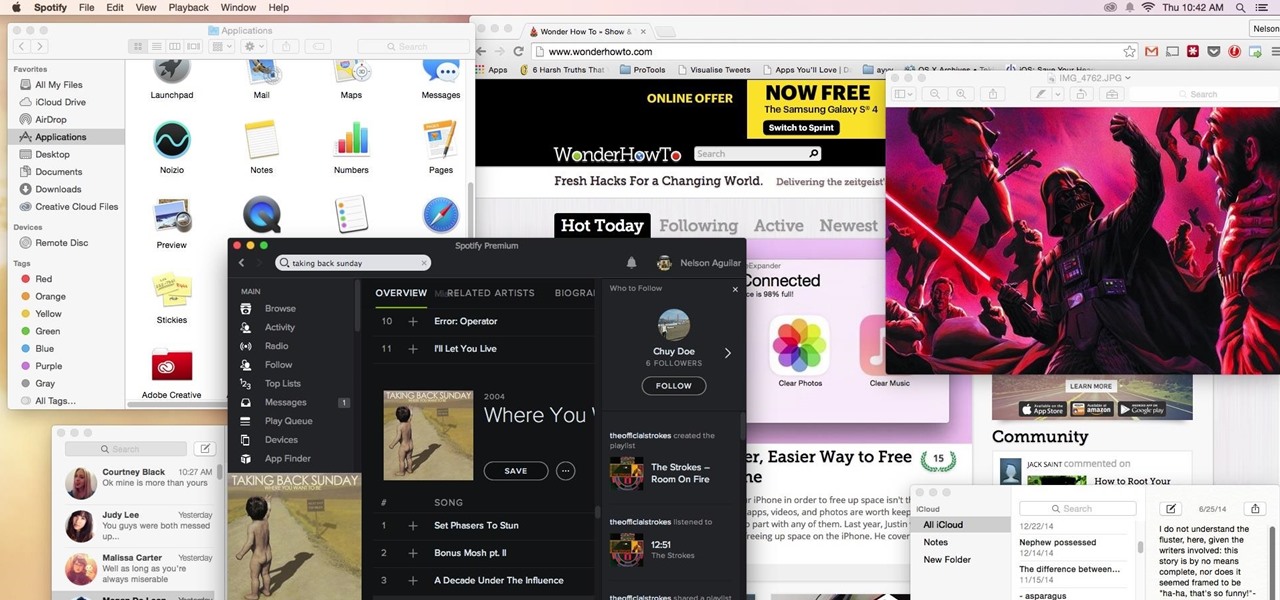
Normally, if you want to close all of the open apps on your Mac, you'd have to either quit them all one by one or restart, shut down, or log out while making sure to deselect “Reopen windows when logging back in." The latter option is great, but it doesn't always work in Mac OS X, and what if you don't want to restart, shut down, or log out?
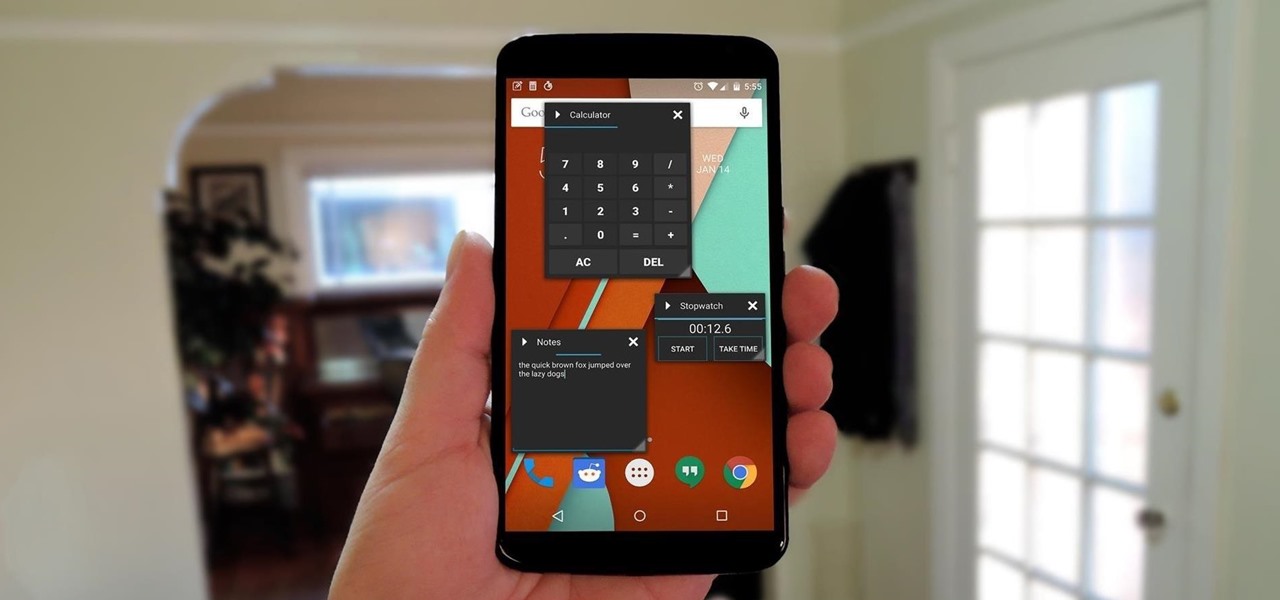
With Android devices getting bigger by the year, you'd think there would be a native multitasking solution by now. While Samsung and LG have included such features in their customized builds of Android, the stock base that manufacturers start with still doesn't include multitasking support.
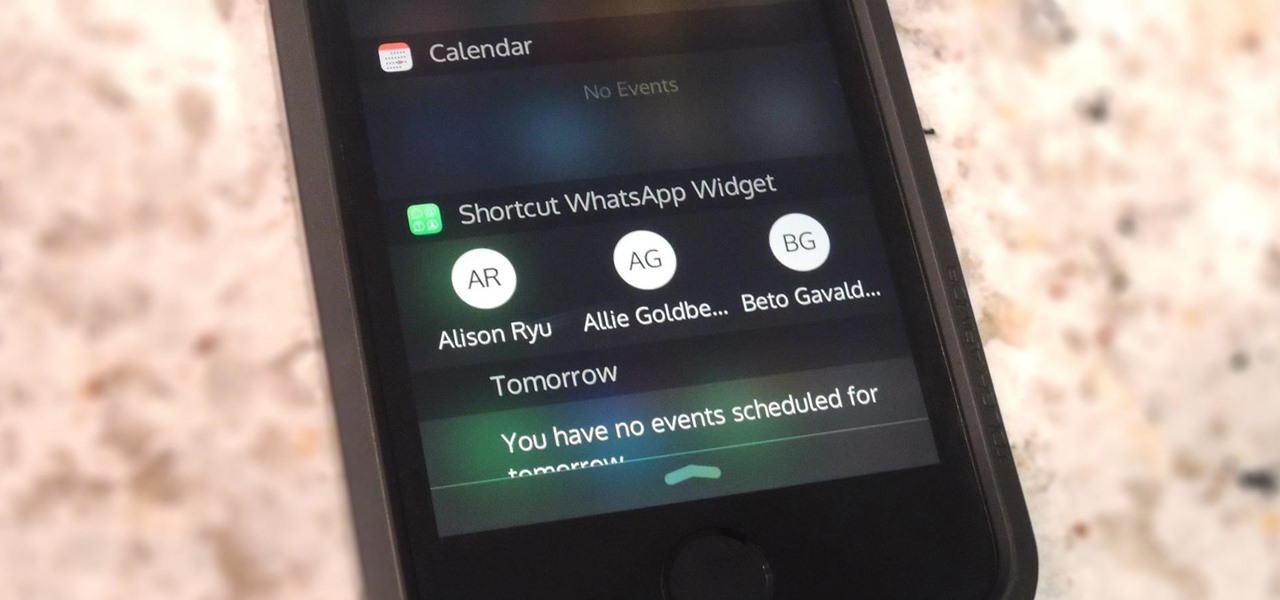
WhatsApp is the go-to application for sending a message (or 100) to friends at home and abroad. And the best thing is, the service has remained true to its roots after Facebook acquired the company for $19 billion.

OnePlus changed the way we think about high-end phones. Their "Never Settle" motto led me to ditch my high-cost smartphone for their flagship One, which not only packs some pretty impressive hardware, but won't break the bank. Now that OnePlus has made a name for themselves with the One, they're trying their hands at ROMs, too.
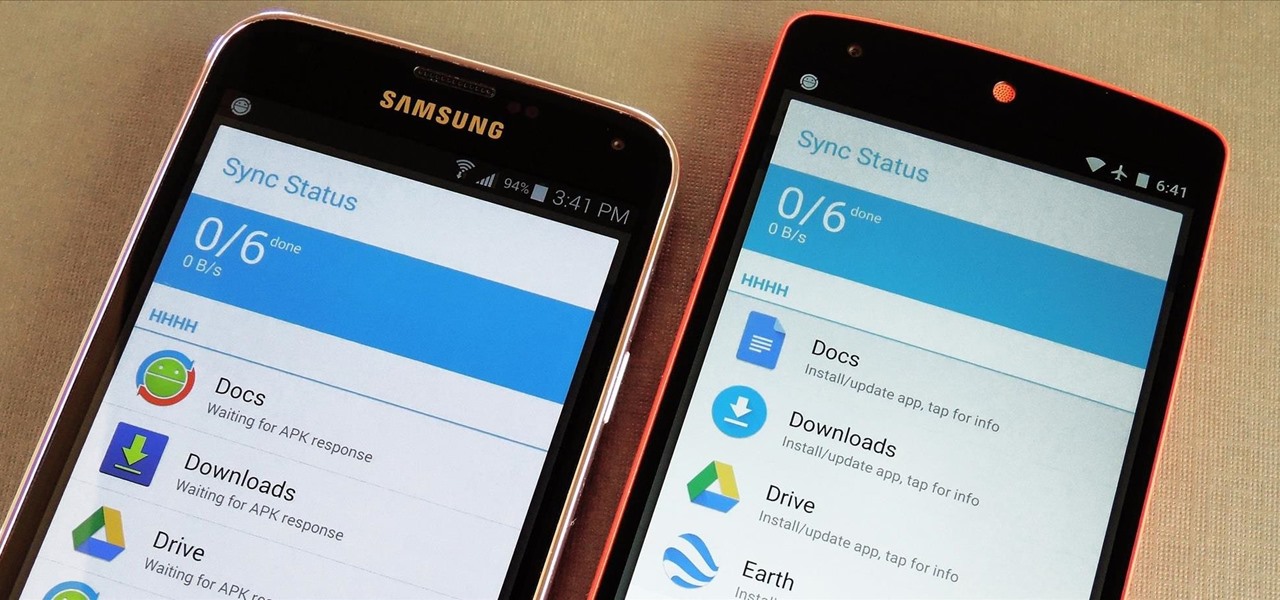
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

Somehow, we end up with a pile of leftover candy canes at the end of every December. Yet just because the enthusiastic holiday commercials are gone and the Christmas cards are on discount doesn't mean you have to let the minty sweets go to waste.

Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't work as advertised.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

The attention to detail and build quality that Motorola put into the new Nexus 6 is amazing. Its curved backplate fits the hand like a glove, and fingers slide effortlessly across the rounded edge of its glass front, making the swipe gesture for side navigation menus feel more natural than ever—even for its huge, nearly six inch display.

Every time my Galaxy Note 3 boots up, I'm greeted by the monotonous and slightly annoying AT&T sound. If you're as tired of the stock boot up sound as I am, then follow along with me below to see how to change it to whatever sound you want, no matter what carrier version you have.

It's been a long time coming, but Google's Calendar app for Android has finally received a visual makeover. In the spirit of Android Lollipop, Google's new Material Design permeates throughout the update.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...