This software tutorial will show you how to track a laptop if it gets stolen using free tracking software Adeona. Of course, it's a good idea to figure out how to keep your laptop from getting stolen, but if you lose it, you can use Adeona to find the location of your laptop.

Everyone and their moms are into Guitar Hero nowadays. If you can't afford this great game, check out this tutorial and learn how to create your own Guitar Hero clone using free software and a controller that you can make using parts that total around $22. The free software used in this instructional video is called Frets on Fire.

In this software tutorial you will see how to create a polaroid picture and make it look like it is pinned up on a wall using Inkscape. All you need for this creative pinned-up polaroid is a picture and the open source software Inkscape.
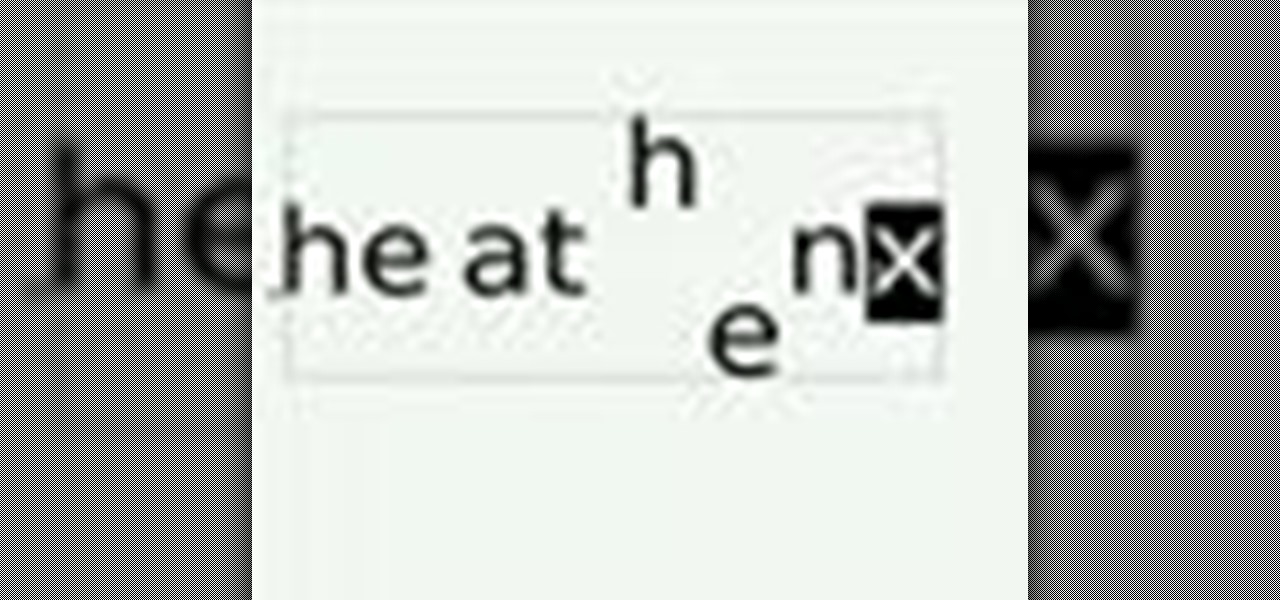
If you do any amount of graphic design or layout design, then you know the importance of using kerning when working with typeface. This Inkscape software tutorial shows you how to manually kern text within Inkscape. This isn't the best graphic design software, but it is open source and if you are using it for layout you may need to use text kerning and will find this video helpful.

In this software tutorial you will learn how to make a simple paperclip from scratch using the curve tools in Inkscape. Inkscape is an open source freeware software so it's easy to get ahold of and start using for your graphic design needs.
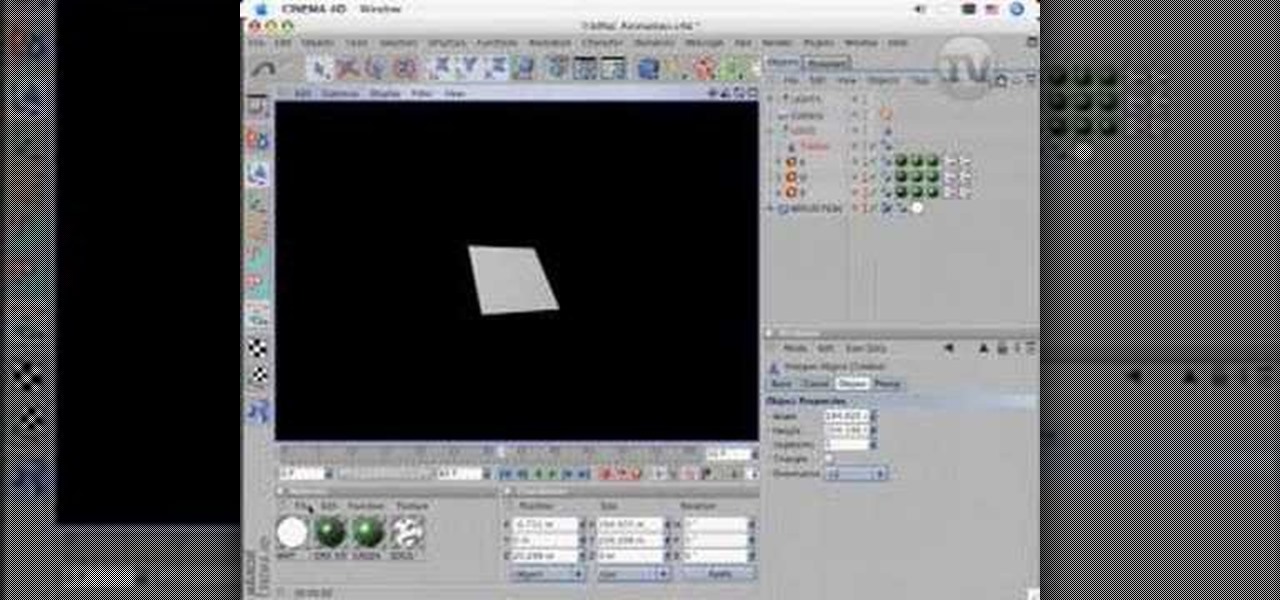
This software tutorial shows you how to build a luma track matte in Cinema 4D 3D modeling software and then help speed-up your compositing of the track matte in After Effects. Creating a spinning logo with video footage inside the logo, as shown in this tutorial is a great way to learn to use Cinema 4D and After Effects together.

Controllerism is a lot like turn table-ism, except through its exclusive use of controllers and music software. Take a look at this instructional video and learn how to turn a simple and inexpensive MIDI keyboard into a custom audio controller. First, you'll want to rearrange the keys to line up with the knobs. Then, cut up an old DVD case and a bicycle tube to glue the rubber onto the keys to make it more tactile. Lastly, you'll need to set up the software to assign the keys with controls on...

Check out this video tutorial for building a Bart PE CD with Part PE Builder made by Runtime Software. Make sure that you have Internet access, a blank CD, and a copy of your Windows XP compact disk with at least Service Pack 1 on it. This will help you creat a bootable CD-ROM for your computer.

This is a terrible prank to pull on a friend. Destroy their iPhone software with a couple of quick hacks.

This shows you how to use the free software to unlock the iPhone, to work with any GSM Carrier. It is a very detailed, and quirky tutorial, so pay attention.

Learn how to use Inkscape (an opensource software) to design a logo for your website. This tutorial gives an overview of the software by running you through an example logo.

Are you the go-to guy/girl whenever your friends and family need tech support? You might want to consider installng LogMeIn - remote desktop software. The Lab Rats, Andy Walker and Sean Carruthers, will show you the benefits of LogmeIn software.

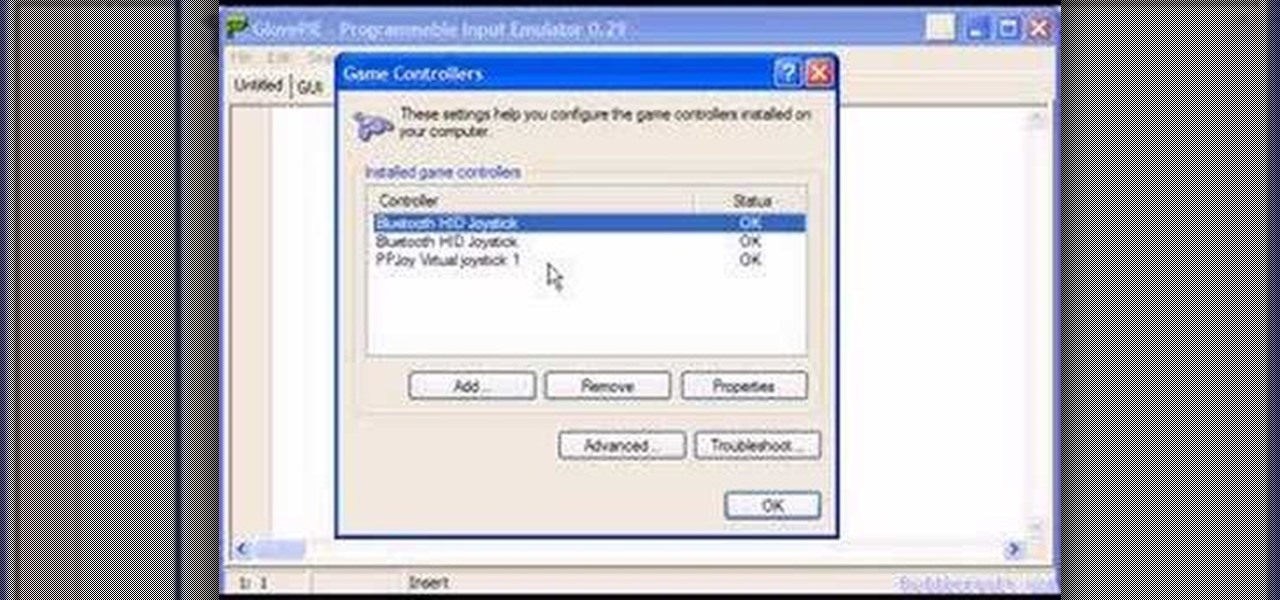
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to recognize analog input or joystick/joypad input from a Wiimote using GlovePie and another piece of software called PPJOY

The fourth room in the Color software that's part of the Final Cut Studio of Apple, is the ColorFX tab. This section of the software allows you to create different looks by combining different effects nodes.

Here is a supernatural how-to for all you spirit lovers. This is a step-by-step guide to create a fake ghost video with free software. The initial technique is simple, but with a few more tweaks, you can get video that can fake at least your grandmother. Use this as inspiration for one of your April Fools Day pranks!

Hello! My name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss the game can you read my mind. This game has a little bit of mystery flavor to it. You'll see what I mean. In this game, you need to utilize 2 rooms. In the first main room, you have all the guests of your party. Then later we'll instruct the guests we're going to play a game called can you read my mind and the goal...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. We're going to now talk about how to play the game think fast. This is a very simple game. Just use a ball that you have at home, go to your kids room, go to the toy box and choose an easy ball and you would like to line the guest of the party in a circle. Choose a theme. If it's a boy's party, you might want to go with Power Rangers, or spor...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to talk about group competition games. These make the party worth while. For example; if you have let's say about 14 party guest, you can divide them up into groups of 2, put 7 in one group and 7 in the other and have a different activity for each group competition. Let me show you an example. I purchased this bag of straws, M...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss another birthday game and this one also happens to be an oldie but goodie. And this game is called connect the dot. This is a perfect game if you want the kids in your birthday party to kind of calm down. Let's say after they've eaten, or even the birthday cake. But you want to draw about 4 lines of dots containing ...

Cool party trick to impress your friends!

Add a party favor to your next hosted New Year's Eve bash. Ring in the New Year wearing personalized party glasses! It's a fun project for kids and adults.

The automatic software update setting on your iPhone is nice, but you may not always want to install new iOS versions blindly. New updates could contain bugs and vulnerabilities, and your favorite features may even disappear. With the auto-update option turned off, you can manually download and install updates, but there are also hidden options to be more specific about how you want to do it.

In the midst of fending off legal challenges from Magic Leap and Epic Games, startup Nreal isn't retreating. Instead, the company is digging in its heels and pushing forward with its launch plan for its Nreal Light smartglasses.

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

Hours after iOS 11.4.1 beta 4 was released on Monday, June 25, Apple's webpage for its public beta software programs was unavailable because of an "update." Sure enough, that meant the public beta for iOS 12 was being prepped to drop shortly thereafter, which is exactly what happened. In other words, you can now install iOS 12 on your iPhone without a developer account!

Thanks to Samsung Experience 9.0 on the Galaxy S8 (AKA TouchWiz Oreo), we know the upcoming Galaxy S9 is going to enjoy some of the new keyboard changes coming to Samsung's iteration of Android 8.0. Those who preorder the device on March 2 or pick it up on March 16 can expect these changes out of the box, as the S9 will be running Samsung Experience 9.0 on day one.

Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

If you want to watch a movie on Netflix with a friend, family member, or significant other, but can't meet up in the same living room, the next best thing is doing it remotely from the comfort of your own homes.

Sometimes just drinking your alcohol can feel a little dull and boring. Eating your alcohol, however, is always a party.

Android's biggest selling point over alternatives like iOS or Windows Phone is the level of customization that it offers. If you don't like something about the UI, you can change it, whether it's as small as an icon set or as big as the entire home screen.

With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today.

Parties are a great way to celebrate and have fun with your good friends, so to make sure your next party rocks, I've assembled some of the biggest life-hackers on YouTube to bring you 10 outrageous party tricks your guests will not forget.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Panolapse is a simple and easy way to add rotational panning motion to timelapse videos. Video: .

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

It always sounds like a good idea to throw a party... until the party gets there. Next thing you know, you're running around hiding anything breakable, and once everyone leaves, you're stuck cleaning up the mess. But the worst part is footing the bill for everything, and if you don't charge at the door, your chances of getting anyone to chip in are slim to none once the party starts.

Make a cool confetti cannon that's great for concerts, parties and special events! Kipkay demonstrates how to hack together this high powered cannon. Confetti bombs are super fun, pay attention to learn how to make your own confetti cannon.