This style of chicken biryani is called the ‘Pakki-Biryani’, where the chicken and the rice are cooked separately and then combined in the final step. There are a lot of different ways of making biryani and here is one simple, easy and yet incredibly delicious recipe that is just ‘too good’ and we had to pass it on. Watch the how-to video to learn how to make Indian style chicken biryani.

Play this Pass through to Score soccer game in teams of two, to improve your passing game. The second video shows you a playoff variation.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.
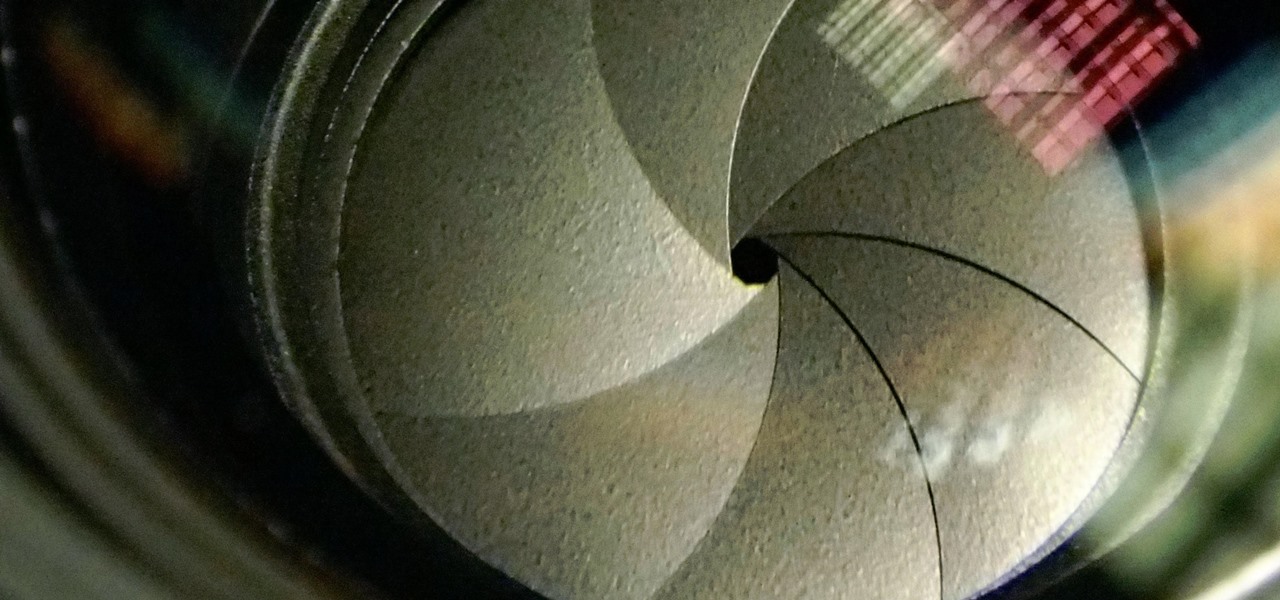
The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.
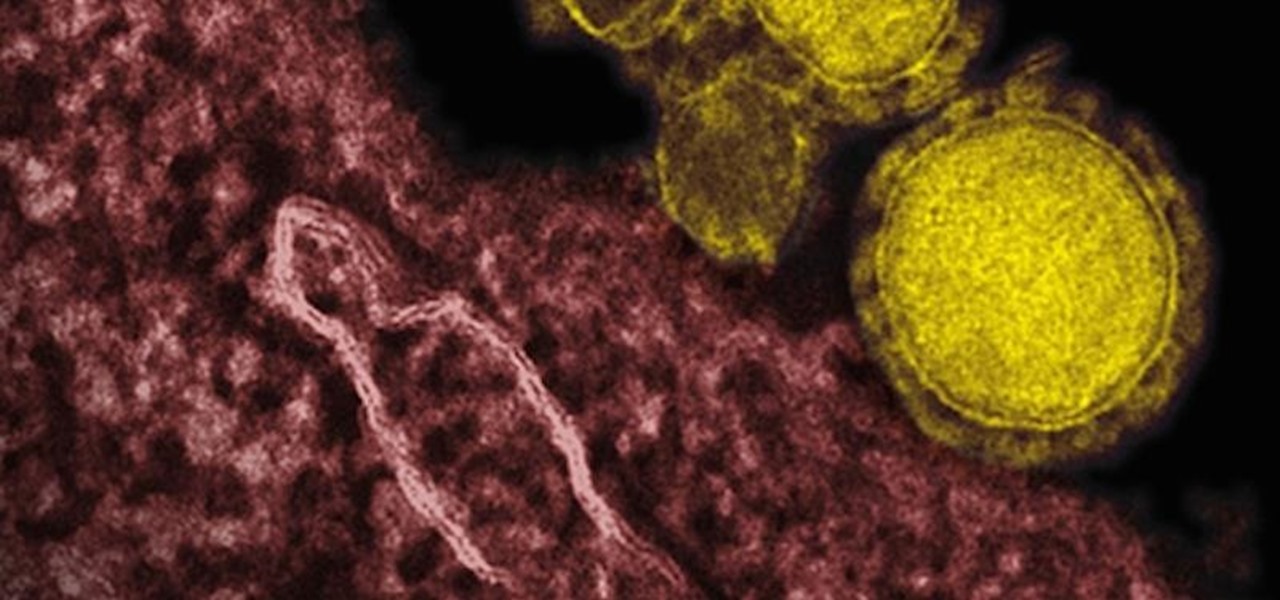
Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

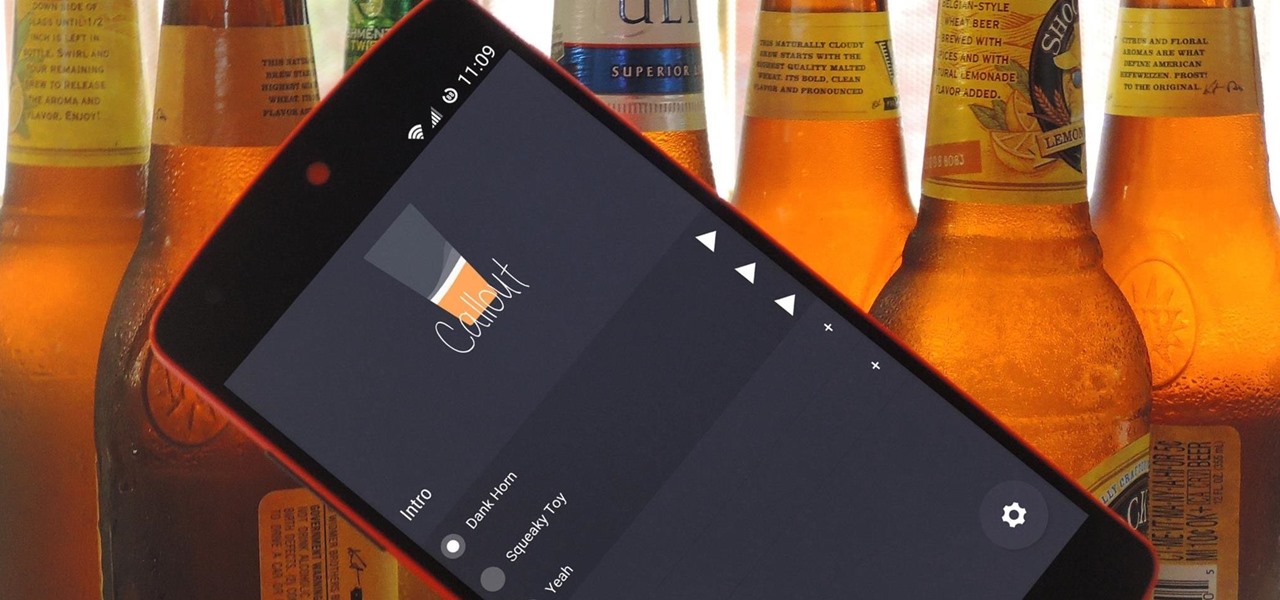
Samsung began offering Android 7.0 Nougat to users in its beta program on November 10, 2016. The beta came to a close last month after the fifth and final version was pushed out to users under the build number ending in 1ZPLN. This update was released a couple of days after Christmas and fixed a couple of bugs, including a fairly annoying one that caused your device to randomly reboot.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

If you ever need to spice up a party, drinking games can really get things started quickly. The objectives are generally to complete tasks or challenges, but it's really all a thinly-veiled excuse for increasing everyone's alcohol intake in a hurry while testing levels of inebriation.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Creating a haunted house for Halloween was a big deal when I was growing up, and the neighborhood kids were always coming up with ways to try and out-do each other when it came to this frightful night. One beloved game was to blindfold the participants and play the Withered Corpse.

Here is a tutorial to show you how you can easily make this much loved Frozen character with Play-Doh. Using some simple techniques and clever tricks, you can make your very own Olaf.

How to drill a hole in a ceramic wall tile. How to tile.Wall tiling. Bathroom wall tiling.

Learn how to teach your basketball players passing skills with the help of this passing conditioning drill.

Play the chip pass drill by yourself in order to work on your passing game for soccer.

Bid Whist can be a fun game for family or friends. It's challenging enough for adults, but enjoyable for kids too. Bidding and predicting wins are what make playing Bid Whist fun and exciting, whether you win or lose.

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

Have you ever noticed that when you put your iPhone to sleep, it takes an extra second longer than it probably should for the screen to go black? It's a bit strange and forces you to wait another moment until your iPhone locks. But most of you can avoid the small delay entirely by just changing one setting.

Following its dominance as a provider of silicon for smartphones, Qualcomm is eager to replicate that ubiquity with not only processors for augmented reality headsets but also reference designs to give device makers a head start.

The last few months have delivered some great new Magic Leap releases, but that doesn't mean the development team is resting on its laurels when it comes to the platform itself.

Less than four months after Snapchat introduced its Snappables platform, Facebook has met the challenge with its own AR gaming feature that surpasses the originator.

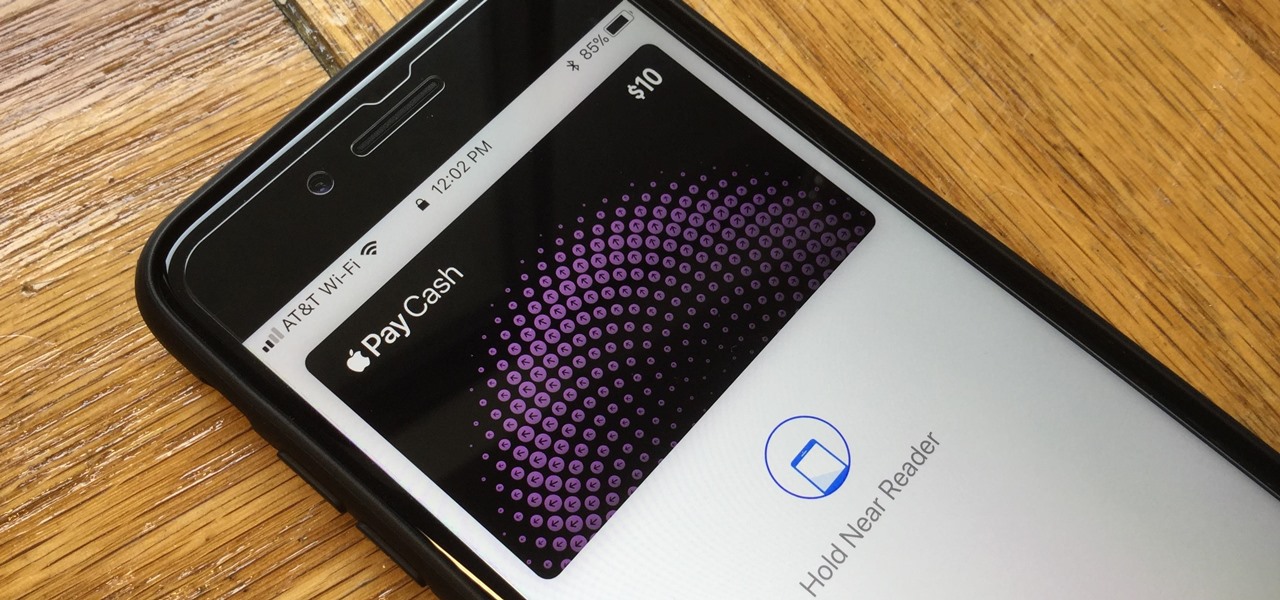
With Apple Pay Cash in iOS 11.2, your iPhone potentially becomes the only form of payment you need. Whether you're sending money to a friend via iMessage or paying for your groceries, you can use Apple Pay Cash to complete those transactions. It makes sense, then, that Apple would allow you to add your Apple Pay Cash card to the lock screen, for quick access wherever you are.

All the Driverless news you need to know from the past 24 hours, bundled together in a tightly written package, about Uber, London delivery services, capital investments, and kangaroos.

If you thought the selfie would only ever be used to bombard your feed on Instagram, you were wrong. Dead wrong. JetBlue is looking to take those selfies and use them to check you in for your next flight.

For all of its drama, Uber's driverless program has states like Arizona excited for the future of self-driving vehicles. But it's not Arizona alone that supports the driverless craze; the Illinois House of Representatives will hear a bill that would allow driverless cars on the road with or without human operators.

Some Montana inhabitants have been making impassioned pleas to legalize raw milk this week. The debate took place during a hearing on House Bill 325, which was held by the Senate Agriculture, Livestock, and Irrigation Committee on Tuesday, March 21.

Pennies may only be worth $0.01, but if you want a coin with everyone's favorite donut-eating dad on it, you're going to need to shell out a little bit more.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone.

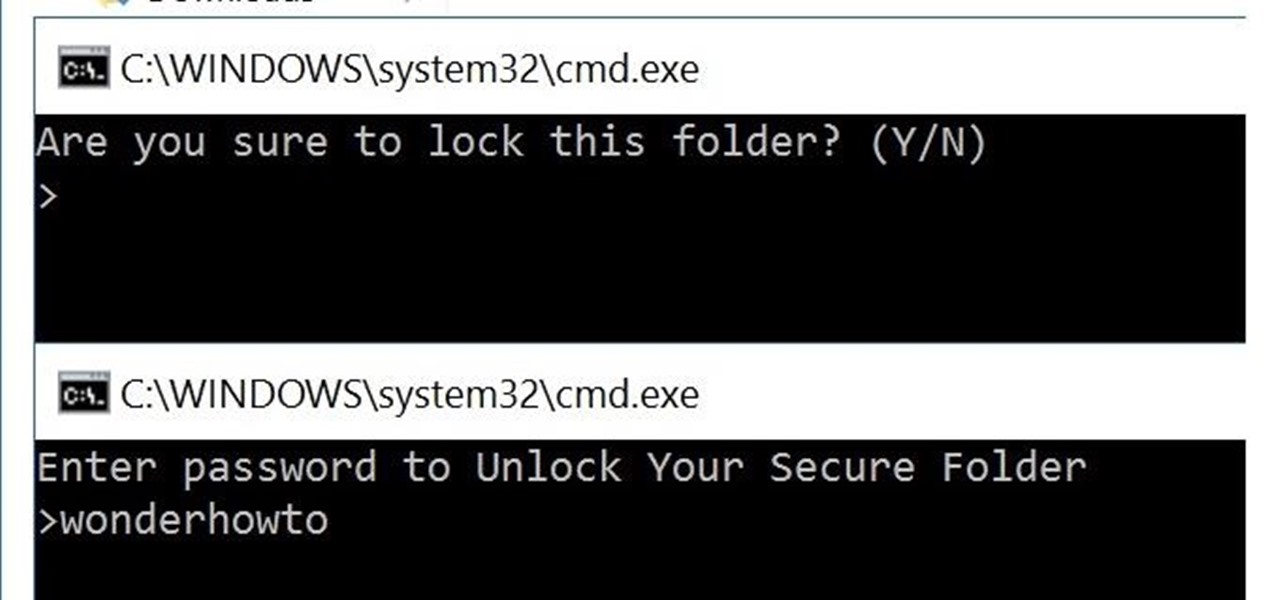
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

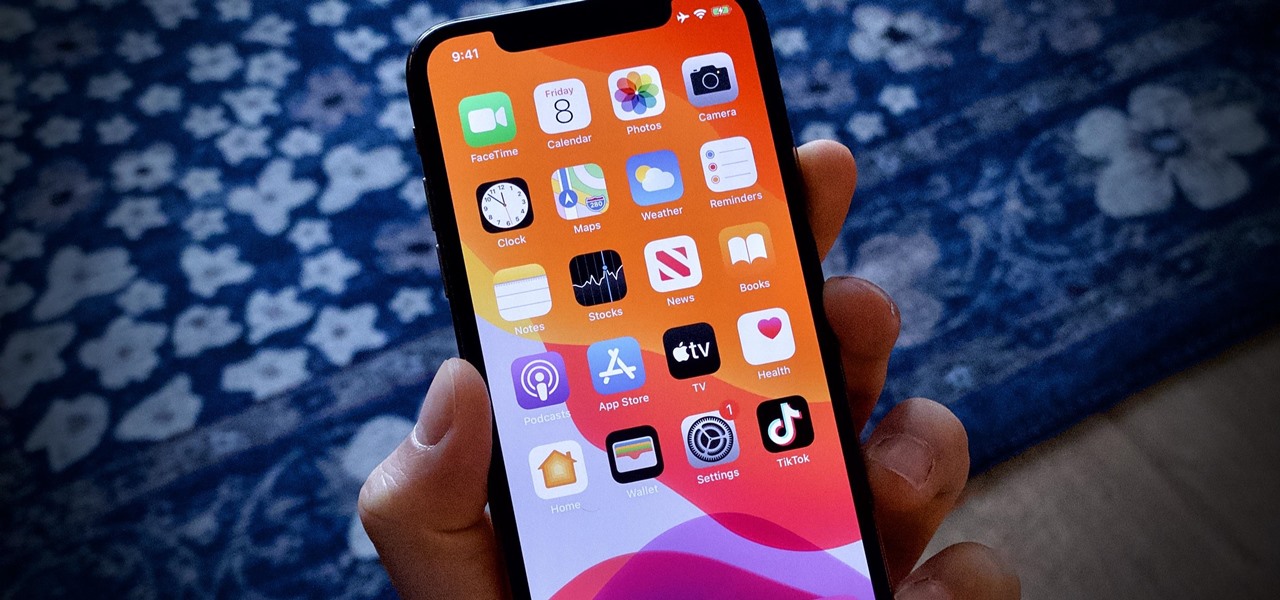
At first glance, the iOS home screen looks nearly identical to the original release back in 2007. Though those experienced with the evolving iterations of iOS will tell you that the features have changed. Furthermore, with the App Store continuing to explode with (lets face it) better options than the stock software, these included applications are only causing clutter across the springboard.

European roulette tables are slightly different than the kind you find in Vegas or Atlantic City. In this tutorial, professional Euro gambler and TV presenter, Richie Litchfield, explains the various positions to place your chips on a European Roulette table.

Play this game with your wall and a ball so you can become a better player. The second video shows you how to do a timed version of wall passing drills.

Have you ever found something in your suitcase that wasn't yours? Maybe it was, but you're almost certain it wasn't. Maybe a friend slipped something in your baggage before your departure flight? Maybe the TSA was playing a joke on you, since they have all the master keys for your approved travel locks?

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

General Motors acquired Cruise Automation in March 2016 for a reported $1 billion (well, at least $581 million). GM President Dan Ammann made a point of being in the press release photograph with Cruise founders Kyle Vogt and Daniel Kan (see photo below). On January 19, 2017, Vogt posted on Twitter: "Took GM Pres. Dan Ammann for a ride in a Cruise AV."

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.