This video series shows you how to race on SyKart indoor kart track in Tigard Oregon. The first video takes you on a warmup lap and explains each turn, the second video shows you the proper line to follow, the third video shows you how to go quick and the last video shows you how to pass.

Learn how to design a defense to stop dribbling penetration or passes to the middle. If you're a basketball coach, you'll definitely want to utilize this two-three zone defense.

Why pay for a movie when you can get it for free? Thanks to Movies Anywhere, you can claim and download a video for your digital film collection right now at no cost. And getting your freebie flick couldn't be any easier.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.
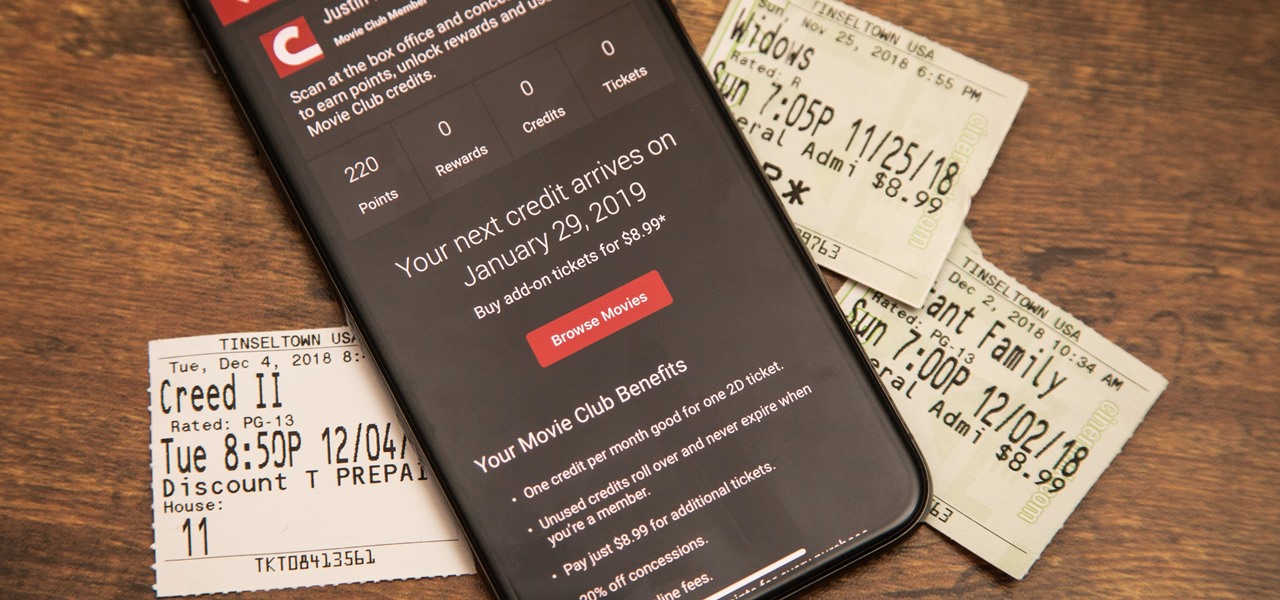
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan worth it?

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Now that Fyre Festival co-founder Billy McFarland is charged with fraud, this is the perfect time to list off those top 15 influencers who promoted tickets to the disastrous event to their loyal followers, right?

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

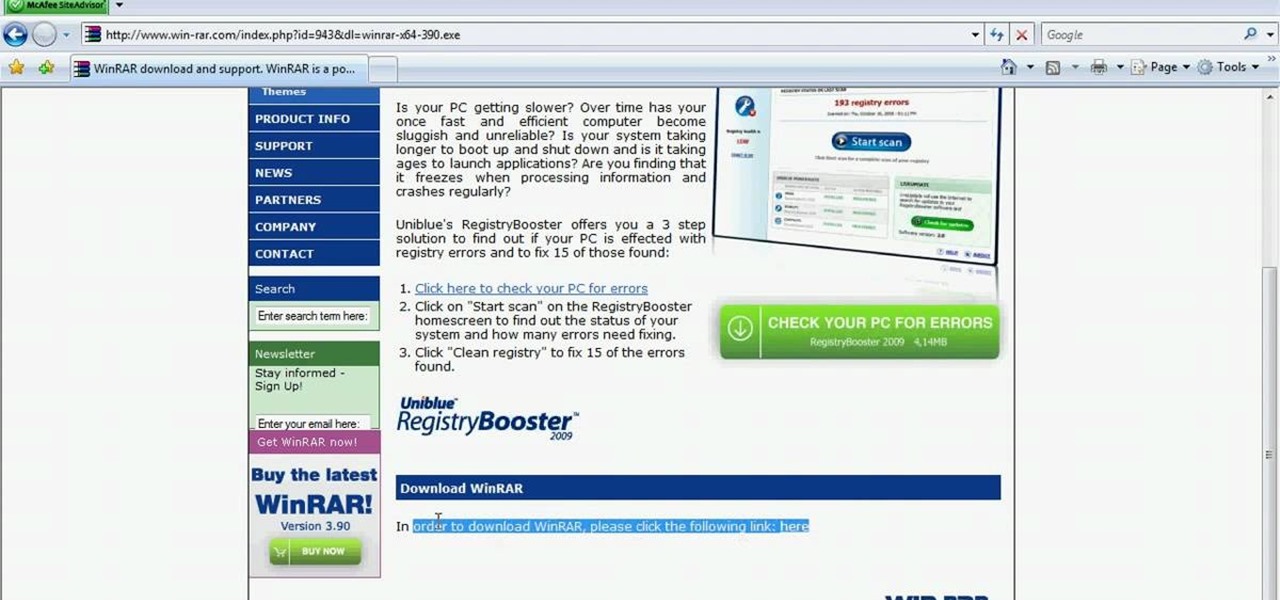
In this video tutorial, viewers learn how to unzip .rar files using Winrar program. Begin by opening your internet browser and download the program from the link in the video description. Wait for the time to pass and click Download. Select 32 bit or 64 bit, depending on your computer. Open the file and install the program by following the instructions. Once it's installed, select the file that you want to unzip. Right-click on the file and select Extract All Files. This video will benefit th...

Access your computer's BIOS settings

When hitting a fade shot in a golf game, it is important to remember this is only for shots that are about five to eight yards. Ten through twenty yards would be a slice. When you're coming to the impact area, the face of the club should be just slightly behind your hands. Fades seem to land more softly on the fareway and has more carry to it than the hook. The club should be slightly open when it comes in contact with the ball. If the club passes your hands on impact, the ball is going to drop.

It is a video about how to apply three eye shadows. For that start with a small eye shadow brush. Then apply the shadow to the inner part of the eye. Eye shadow should stop where your pupil starts. After that take a bigger eye shadow brush and apply the second color, which should go passed your iris of the eye. The second color is applied over the eyelid. Now take an angled eye shadow brush. The angle will help to apply the color in to the crease. Third color is applied over the left part of ...

Although mainly demonstrational, this video shows you how to play the "Fingerbuster" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

Playing backline in rugby is an important position on the field. Learn how to play rugby, including rules and skills, in this video rugby lesson.

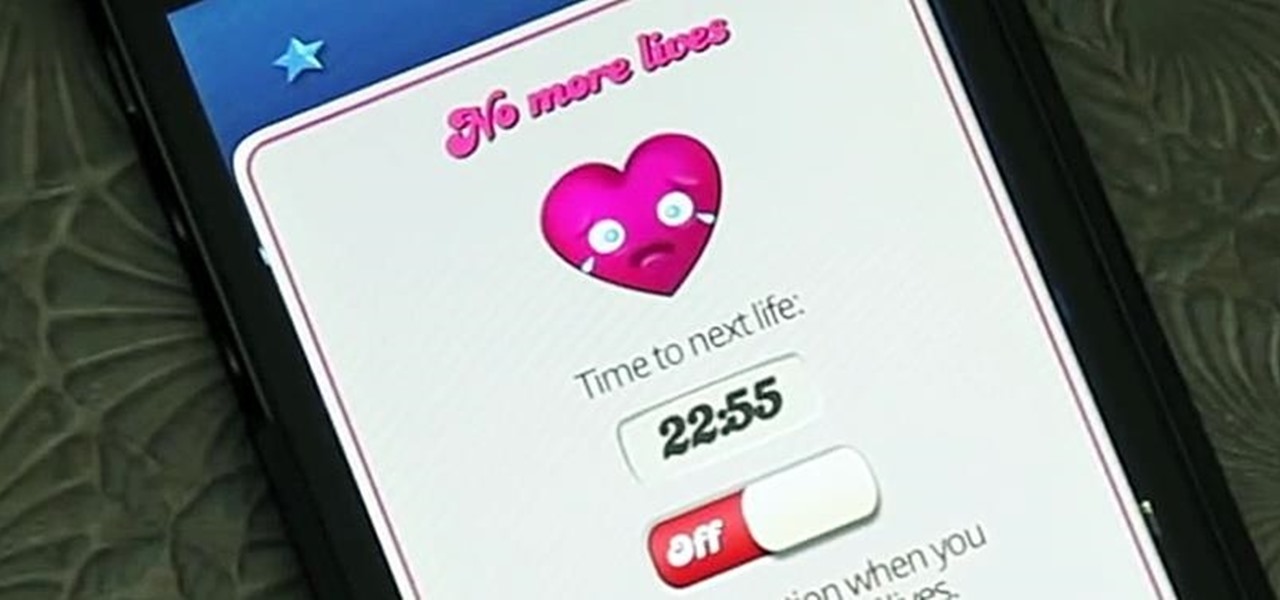
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

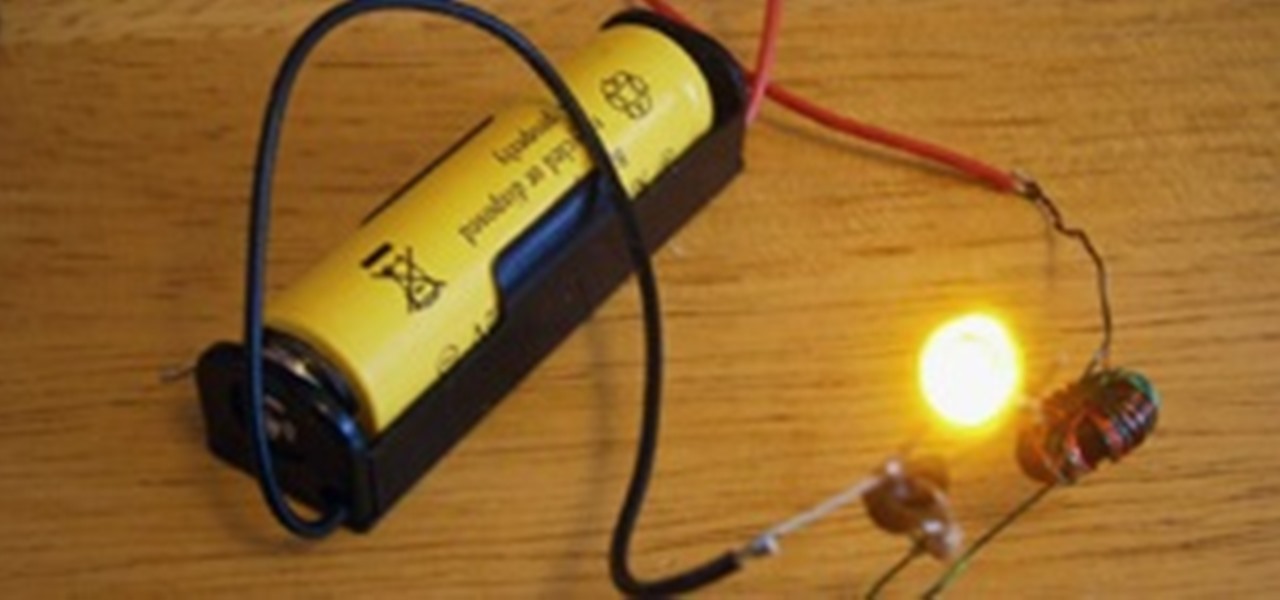
Just about every household gadget we own runs on 1.5 volt batteries of one size or another. Wouldn't it be great if you could reuse all of those dead AA, AAA, and D batteries after they've passed on? It turns out you can make a simple circuit called a "Joule Thief" to reanimate the undead flesh of your deceased batteries and create a zombie battery.

If you need some help rigging a soft plastic fishing bait, this quick video can help. Use tandem rigging to get it done. The tandem rigging is liked when short strikes become an issue. As baits get increasingly longer, the second hook becomes increasingly important. Particularly recommend is tandem rigging on longer baits, such as 14” and 18” models.

Wireless headphones are convenient, comfortable, and more common than ever before. With the massive proliferation of wireless earbuds, it's hard to identify which ones are good and which ones just want to look like they're worth the price. Avanca T1 Bluetooth Wireless Earbuds are high-quality wireless earbuds with excellent functionality and a low price of $29.95 now that they're 50% off.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

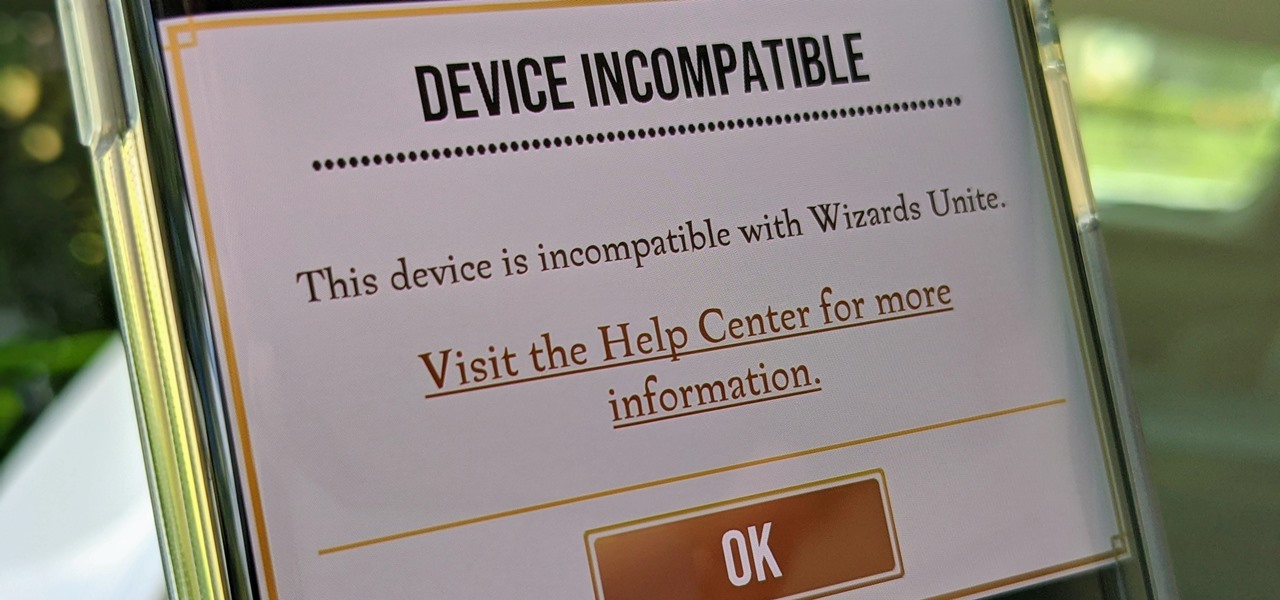
Harry Potter: Wizards Unite has gained quite the fan base since its launch, but not without a few bumps along the way. Niantic, the game's developer, has a long-running history with trying to block all root users on Android. The methods will vary for each game, but this time around with Wizards Unite, they appear to have a new detection feature at play from the recent 2.9.0 update. Let's find out what's going on.

I'm a new parent and I just moved into a new home. The first thing I wanted to do was ensure my toddler's safety in his new digs. That meant buying a bunch of baby-proofing products from Amazon, realizing most were junk, then buying some more until I found solutions for all my needs.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

A relatively unknown musician from the early-'70s that's gained popularity stateside over the last ten years just got the remastered treatment with two new reissues available on CD and 180-gram vinyl. And they're available right now.

After playing Mario Kart Tour for a little while, you'll notice it's a bit different from previous games in the series. The biggest change is how they've deferred to new players by automating many of the controls. But what if you want the traditional experience? We've got you covered.

It happens to all of us. You're ahead of the pack, clearly in first place, when someone launches the Spiny Shell (aka, the blue shell). It catches up and circles you before crashing into your kart, and there's seemingly nothing you can do about it. But what if I told you there are two ways to avoid this fate in Mario Kart Tour?

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

Four months have passed since Mojo Vision emerged from stealth, and we are no closer to seeing exactly what its "invisible computing" technology looks like.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

Back in 2018, Spotify began testing a new mobile feature that has grown very tiresome: three to eight-second looping videos that take over the entire screen. Known as Canvases, they effectively hide the cover art and lyrics of the current song — and they're still very much around to annoy and distract the hell out of you. Thankfully, Spotify has also included a way to get rid of these things.