
How To: Service a Porsche 944
This video gives a step by step tutorial how to service a Porsche 944. The service is demonstrated on an S2, but most steps are very similar for other versions.


This video gives a step by step tutorial how to service a Porsche 944. The service is demonstrated on an S2, but most steps are very similar for other versions.

The Javorek complex - what is it? It's an exercise for your shoulders. Men's Health gives you a perfect demonstration of how the "Javorek complex" is supposed to be done. This is an all-round shoulder exercise.

Consistently used in many forms of physical training, the push up has been considered one of the best physical tests of muscular fitness and endurance. Namely known for its use in the military as well as other physically demanding activities such as boxing and the martial arts, the push up is necessary for any physical examination in which many struggle with.

The improved clinch knot… why is it improved? Well, the improved version of this popular fisherman's knot includes an extra tuck under the final turn. If you want to learn how to tie the improved clinch knot, just watch this video with Wade Bourne of MyOutdoorTV.
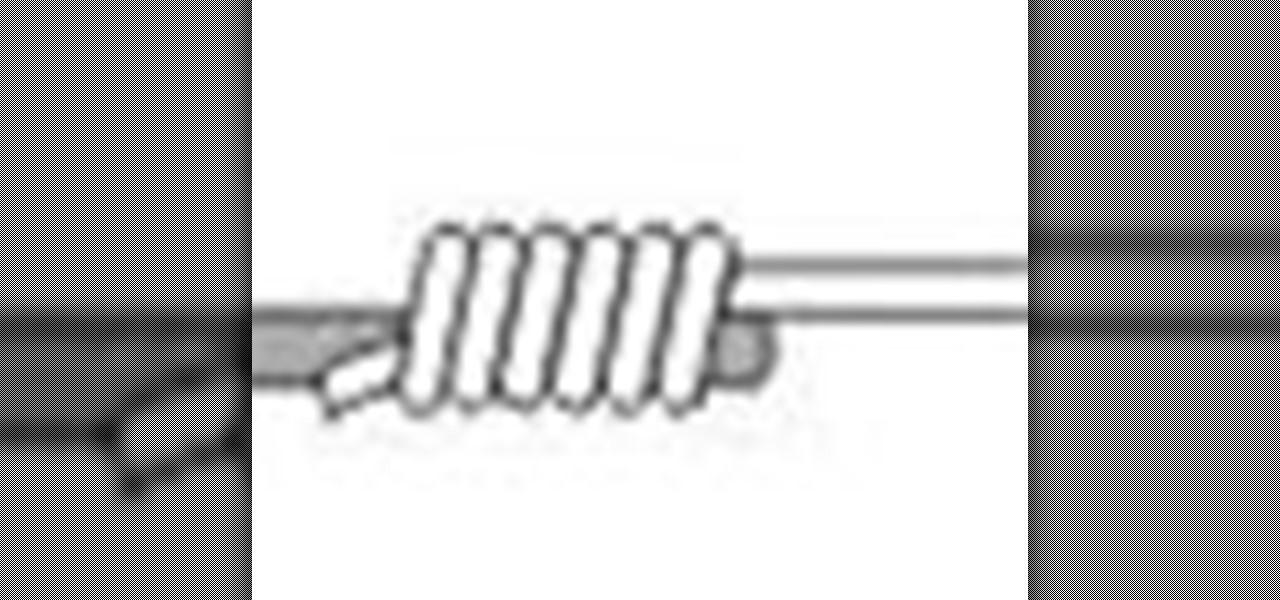
Learn how to tie the nail fishing knot with this knot tying instructional video. The nail knot is a popular and time tested fishing knot to join fly line to leader. Use of a hollow tube instead of a nail makes for easier tying. 1. Lay a nail or hollow tube against the end of a fly line. Set the butt section of a leader against the line and the tube or nail. Leave an aextra 10" - 12" of it's tag end to tie the fishing knot. 2a. Hold all three pieces together with left thumb and forefinger and ...

Watch this knot tying instructional video and learn how to tie the improved clinch knot for fishing. The improved clinch knot has become one one of the most popular fishing knots for tying terminal tackle connections. It is quick and easy to tie and is strong and reliable. The improved clinch knot can be difficult to tie in lines in excess of 30 lb test. Five+ turns around the standing line is generally recommended, four can be used in heavy line. This fishing knot is not recommended with bra...

How to bake a chocolate cake Make a tasty homemade chocolate cake that everyone will love.

Hi : ) This is version 2 of chloroform surprise (as version 1 submitted was a bit too dangerous) . This time we have a professional anesthesiologist to help anaesthesia. He/She will use a pre tested knock out cocktail that suits each jackass individually, so that this remains safe for everyone in the team!

One of the easiest ways to cook potatoes is by simply throwing them on the fire. Okay, you don' want to throw them directly in the flame, but in the coals, it cooks them perfectly. What better time to roast potatoes than when you've got something cooking on a grill or in your smoker? Mark Patuto shares his tips for foil-wrapping your spuds and tossing them on the fire. Doesn't get any easier. They'll pick up the smoky-scented goodness from whatever you've got cooking. And clean-up? None!

Prepare all the materials and tools needed for the process. Prepare a circuit tester, an electrical tape, a flathead screwdriver, a pair of scissors, and an electric sealers kit. Then, make sure that you turn off the power at the main circuit box. Place a piece of electrical tape over the circuit breaker that goes to the circuit that you are going to work on. Unscrew the screws that are holding the plate cover of the outlets to the wall. Test the outlet using the circuit tester to make sure t...

Want to learn how to play soccer like the pros? Watch this UEFA Training Ground video to learn the actual ball control drills used by the Spanish Football Federation.

Try out this sweet dessert pie for your after dinner treat. Just watch the full video to see the recipe for this delicious custard pie. Just like grandma used to make. Sure to be a favorite.

In this four-part programming lesson from the Absolute Beginner's Series of Visual Web Developer C#/ASP.NET video tutorials, you'll learn how to build a quiz engine.

Soap suds aren't just for dishwashing! Blow away your family and friends with this cool science experiment.

Watch this video from This Old House to learn how to install a gas fireplace. Steps:

Hobby rockets are tons of fun. Vicarious astronaut adventures abound with every launch. What if you want to be closer to the action though? What if you want to feel what it's like to be in a rocket at takeoff? With the discovery of tiny keychain cameras, we have technology small and cheap enough to fit inside a model rocket!

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

I finally got around to trying out another one of Will's mad science experiments and found out that this one was actually more satisfying (and less frustrating) than my slightly uncooperative jar jet. There's something very pleasing about making potassium nitrate at home in the kitchen and then watching the transformation from semitransparent liquid to spiky, frozen crystals. That was the best part for me, second only to igniting it with its sugar companion.

There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

In this article, I'll show you how to make a glowing orb. The orb is a fun, round flashlight useful for lighting your path in a magical way. Consisting simply of LEDs, a tennis ball, a battery and a switch, it's a great simple project for beginners with electronics. Here's a video of it in action: Tools and Materials

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

Last week I had a quick look at V.I.K.T.O.R, the anthropomorphized automated editing app that lives on your iPhone, and today it’s time to put it to work.

Can a free cloud-based video editor that lives in your browser replace iMovie? In three words: yes, it can. But whether you should use it instead of iMovie or an equivalent depends not on the functionality of the editor you need, as WeVideo can do what most of what iMovie does, but on what you need to do with your videos once they're finished.
This week's review roundup is a diverse lot. They really only have two things in common—their indie origins and puzzle elements. Otherwise, they come from France, Spain and the U.S., a few from unknown designers and one by the guy who inspired Minecraft.
To go Open Source or go proprietary? There is a common conception that open-source is unsafe and insecure and therefore companies should rather go for proprietary solutions. They think that because software is termed "open-source", that the world can see the vulnerabilities of the software and might exploit it, and less informed people tend to think that open-source software can be modified while it is running.

In Google definitions a macro is defined as "a single computer instruction that results in a series of instructions in machine language". Basically a macro is a programming script that tells the computer what to do. You can tell a computer (via a macro) to move a mouse, click, type or do any task that a computer can do with automation. There are also many (primitive) computer viruses that are coded entirely in a macro script. There are many ways to create a macro script but I will only go ove...

Warnings Warning! These links are not all approved by Zynga. You use them at your own risk!

I’m terrified of you. Yes, you- Director of Photography (DP). Your framing is beautiful, but your lighting could kill me, and my career. I am the Makeup Artist, and I don’t believe we’ve met.

Serious Eats' Burger Lab offers an extensive guide to making sliders at home. For those who have not sampled the beloved American classic, a slider is NOT just a mini hamburger. Nope, there's much more to it than that.

The job market has bounced back slightly in recent months, yet it appears that working remotely will be a way of life for many of us moving forward. With many industries disappearing, app development looks like it's here to stay.