One the leading game developers for the PlayStation 4 and Oculus Rift platforms, Insomniac Games, is finally releasing its first major augmented reality title: Seedling for the Magic Leap One.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

WaveOptics, makers of diffractive waveguides, has inched closer toward getting products featuring its technology to market through a production partnership with a consumer electronics company whose clients include Google, Microsoft, and Sony.

At its annual MAX event kicking off on Monday in Los Angeles, Adobe gave the audience a new preview of its forthcoming Project Aero augmented reality authoring tool during the keynote presentation.

Rumors are swirling today that NASA's Jet Propulsion Laboratory (JPL) may have shown us the first public glimpse of the next-generation HoloLens. Are they real? Or just a prototype? We've been digging in all day to find the answers.

The game wizards at Insomniac take pride in diving deep when it comes to world-building, and the same is true for the studio's latest title for Magic Leap One called Seedling.

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Microsoft is adding another important piece to its growing immersive computing arsenal by putting its newest Mixed Reality Capture Studio in the center of the movie business: Hollywood.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

I don't know about you, but nothing is more annoying than when my phone hits 15% and I'm nowhere near a charger. Not just because I know my phone will die soon, but until I reach a charger, I have to deal with the annoying low battery notification and LED light. Well, with Android 9.0 Pie, we finally can escape this.

The mainstreaming of augmented reality won't happen overnight, but it's becoming increasingly clear that traditional media is leading the charge in the effort to introduce the public to immersive computing. A recent example came from none other than USA Today via its 321 Launch app.

Magic Leap has earned a reputation for overt secrecy, but as it nears the highly-anticipated launch of the Magic Leap One, the company is spilling some of the beans. This week, we get a heaping helping of information on the Lumin OS, as well as a couple of great demos.

If you're not impressed with the current crop of AR content, and you're worried this may put a damper on the industry's growth, these stories should give you cause for some optimism.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

Magic Leap shows up in the weirdest places. Last week, right at the start of World Cup fever, for some reason, the Magic Leap One appeared on a Brazilian television show.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Confirming a previous report from last week, Qualcomm announced its Snapdragon X1 platform designed for augmented and virtual reality devices during an event at the Augmented World Expo in Santa Clara on Tuesday, with Meta and Vuzix among the first manufacturers to adopt it.

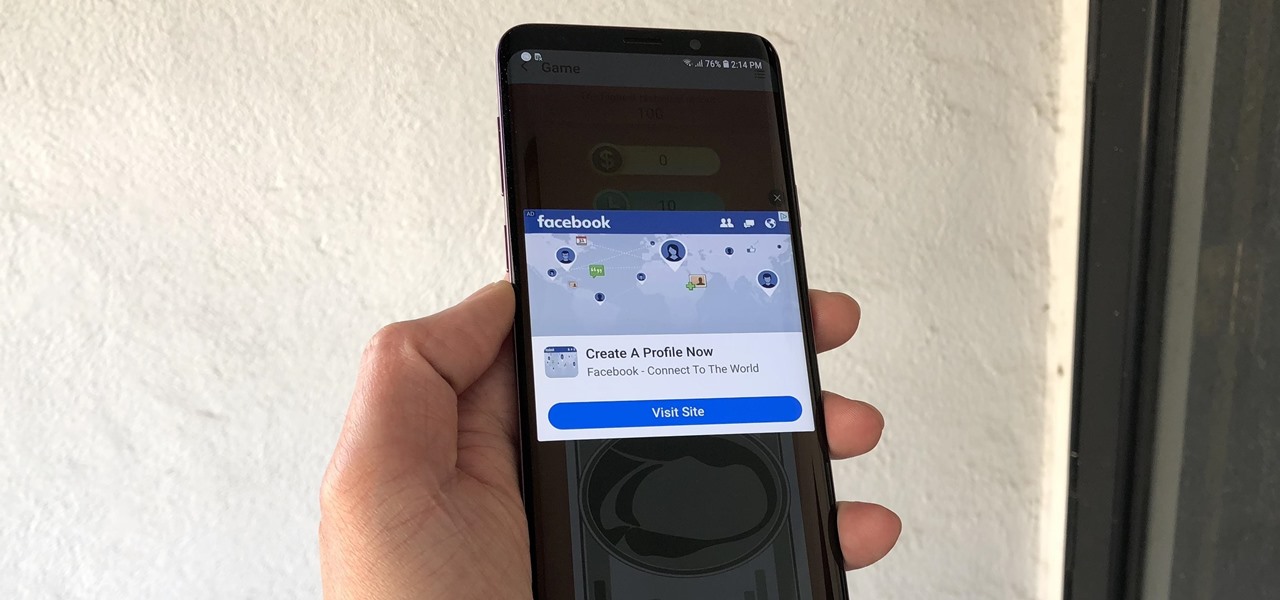
Android has gotten significantly better at handling intrusive ads over the years. Things have gotten to the point to where these nuisances are largely a non-issue for most of us. However, there are still a few ad-laden apps that fall through the cracks — particularly the kind that bombard your lock screen with ads.

It will likely take a few more years before smartglasses are ready for primetime as component makers achieve the innovations necessary for consumer-centric device designs. Nevertheless, two technology companies are making steps in that direction as Qualcomm is rumored to be working on a chip dedicated to AR & VR headsets, while DigiLens has reduced the size of its waveguide displays for motorcycle helmets.

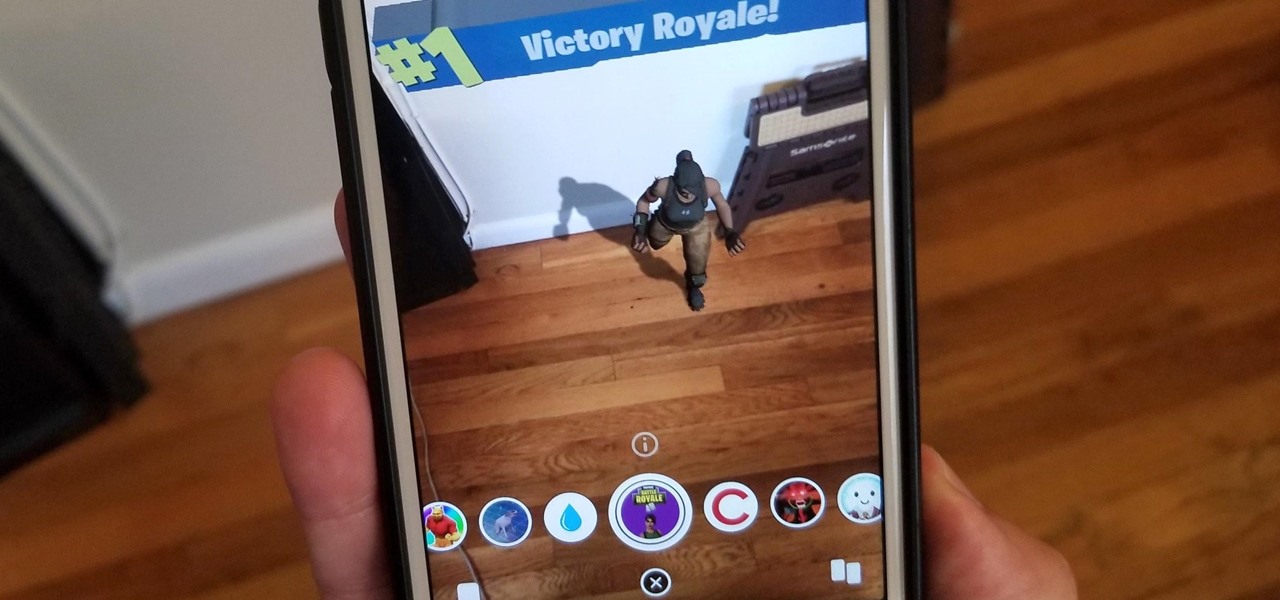
With April coming to a close, there's a fresh group of augmented reality Snapchat lenses you should try out while they're still hot. We've got a prank lens, gamer-oriented ones for Fortnite and Fallout, and ones for the memesters out there.

Upon Google's release of ARCore in February, the platform wasn't only playing catch-up with Apple and ARKit in terms of downloads, but it also lagged in capabilities, as Apple already had vertical surface recognition and image recognition on the way with ARKit 1.5 for a March release.

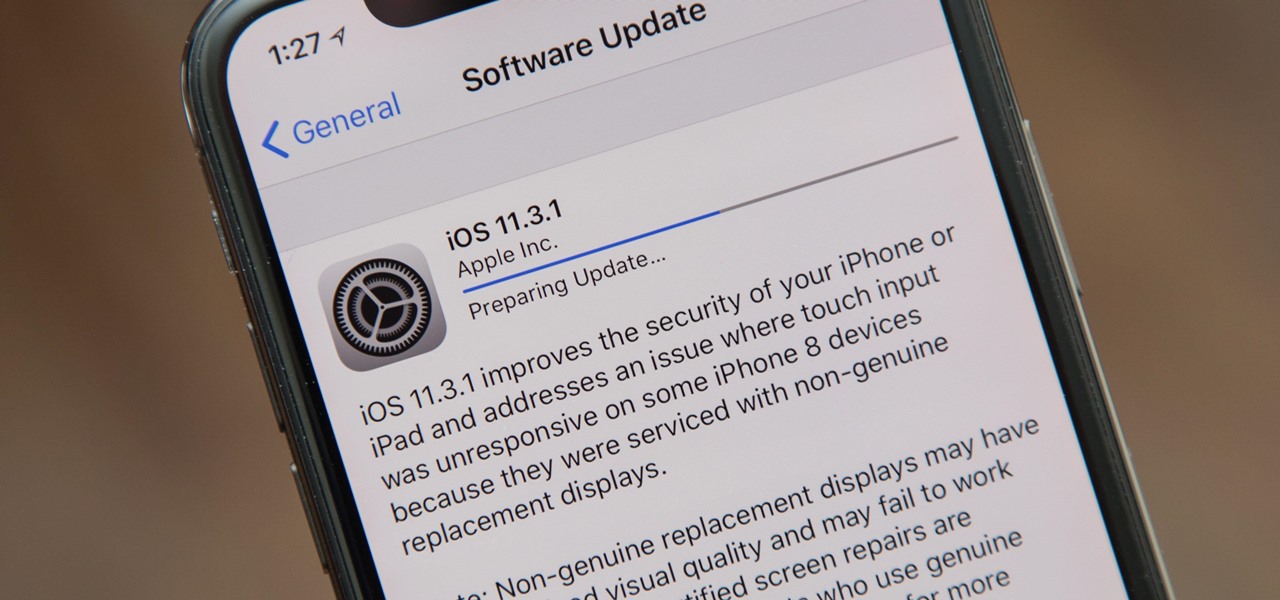
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.

In an effort to help its advertising partners close sales with its sponsored augmented reality camera effects, Snapchat has launched a set of e-commerce tools designed to encourage users to buy products directly in the app.

While you were slaving away at work or school or whatever you were so busy doing over the last seven days, people have been hard at work creating a variety of new Snapchat lenses for your enjoyment. These lenses are hot off the presses, and I'm honestly really impressed with this week's crop.

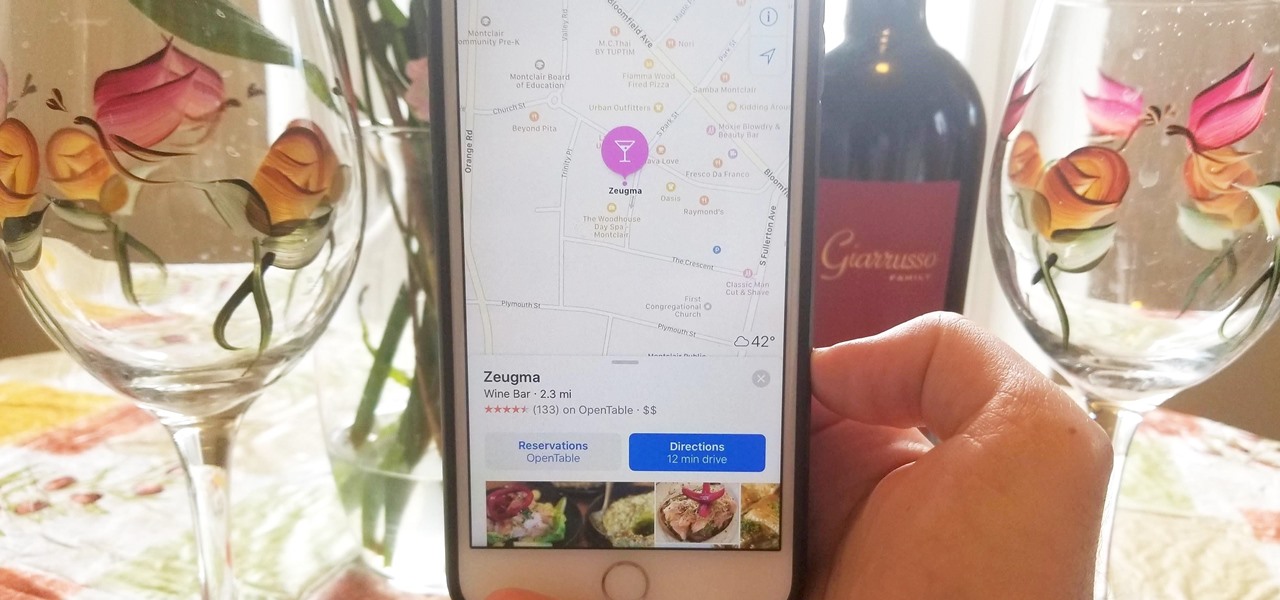
Apple has taken great strides to ensure that iPhone users are having an Apple Maps experience on par or even better than Google Maps can provide. One of the factors powering this is extensions, which adds functionality to certain apps by giving them permission to interact. Among all the possibilities, one extension will let you reserve dinner tables right from inside Apple Maps.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

While you were busy browsing Instagram, composing tweets, or chasing Snapchat updates, an eight-year-old ARKit developer was hard at work on her first step toward taking over the tech world via augmented reality.

In the weeks following Google's AR toolkit launch last month, the availability of quality ARCore apps has been somewhat limited. That changed on Tuesday, as a flurry of new and updated apps arrived on the Play Store, including some AR experiences available exclusively on Android.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

A funny thing happened on the way to the release of the virtual reality epic Ready Player One — augmented reality grabbed a major piece of the spotlight. Specifically, Microsoft's HoloLens.

Not content to just be a provider of rugged smartglasses for enterprise users, DAQRI has made the jump into the AR software side of the industry with its new Worksense productivity suite.

If you're not looking closely, it's easy to mistake last year's Galaxy S8 for the brand new Galaxy S9. Design, build materials, screen size, software — it's all virtually identical, save for a few exceptions. But those minor differences can add up.