There are few things that make me smile more than ice cream… or bread! So why not combine them for double the happiness? We've discussed the art of making ice cream bread before, but not everyone has the time (or, let's face it—the patience) to bake bread in the oven, no matter how few ingredients the recipe may take.

The grill isn't just a place for burgers, dogs, and corn anymore. Fresh fruit has made its way into barbecue territory, with results so good, you'll think twice about settling for fruit salad. While some fruits are common enough on the grill (like pineapple), these six are more off the beaten trail: peaches, watermelon, strawberries, mango, and pears.

Pickles are one of those rare foods that most people love, but never even think of making. Most home cooks shy away from making pickles because they take time and patience, and because the grocery store option is both cheap and delicious.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Laminate floor planks look beautiful and add elegance to a home. However, if a plank gets damaged, it detracts from the beauty of the flooring. Do you call in a professional and pay tons of money to replace the plank? Thankfully, no. There actually is an easy way to replace a damaged laminate plank if you are ready to spend some time and have a little bit of patience.

Getting on the phone for customer service can be extremely frustrating. First you've got to find the correct phone number for your region (good luck trying to get customer service from a sales department), then you have to listen to the annoying automated system to navigate your way to the department you want. More often than not, you'll be stuck with some elevator music while you wait to speak to an actual human.

Losing important data is the modern-day equivalent of misplacing your wallet or keys. We have tons of vital information stored in our digital worlds, and losing any of it can be devastating. But if you've accidentally deleted something important from your Android device, there's still hope.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

The wait is almost over. The sixth season of Game of Thrones kicks off this Sunday, April 24th at 9 p.m. (PT) on HBO, or at 5:57 p.m. (PT) on HBO GO and HBO NOW, with the first episode "The Red Woman."

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

So Christmas is coming up, and you want to make a couple of presents for your friends and family, who you don't really feel like splurging on- but want to make something from the heart. You've tried other stuff, and you totally failed at the Cross-stitch from last year, have you tried Knitting?! Well here's a beginners guide to the simple knitting technique- an easy one!

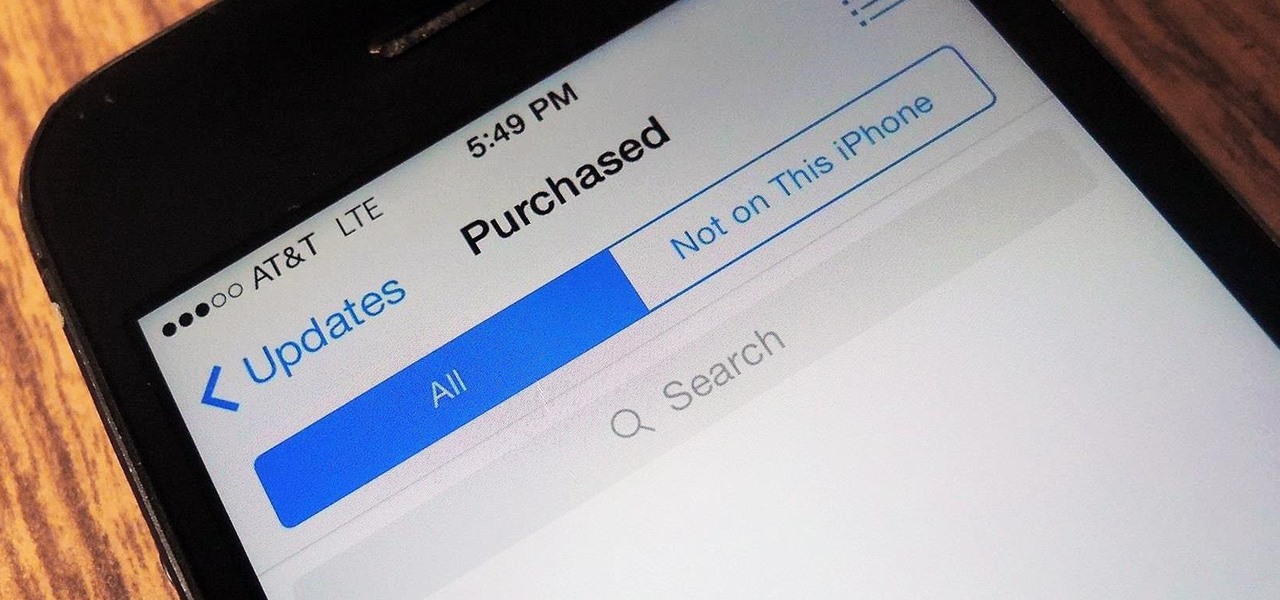
With the release of iOS 7, the entire Internet was abuzz with what's the exact opposite of excitement as Apple's servers were overloaded, causing many download fails of the new operating system. Since then, many other bugs and issues have arisen that are fairly common with new Apple software updates, like iMessage fails and wallpaper complaints (to only name a few).

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

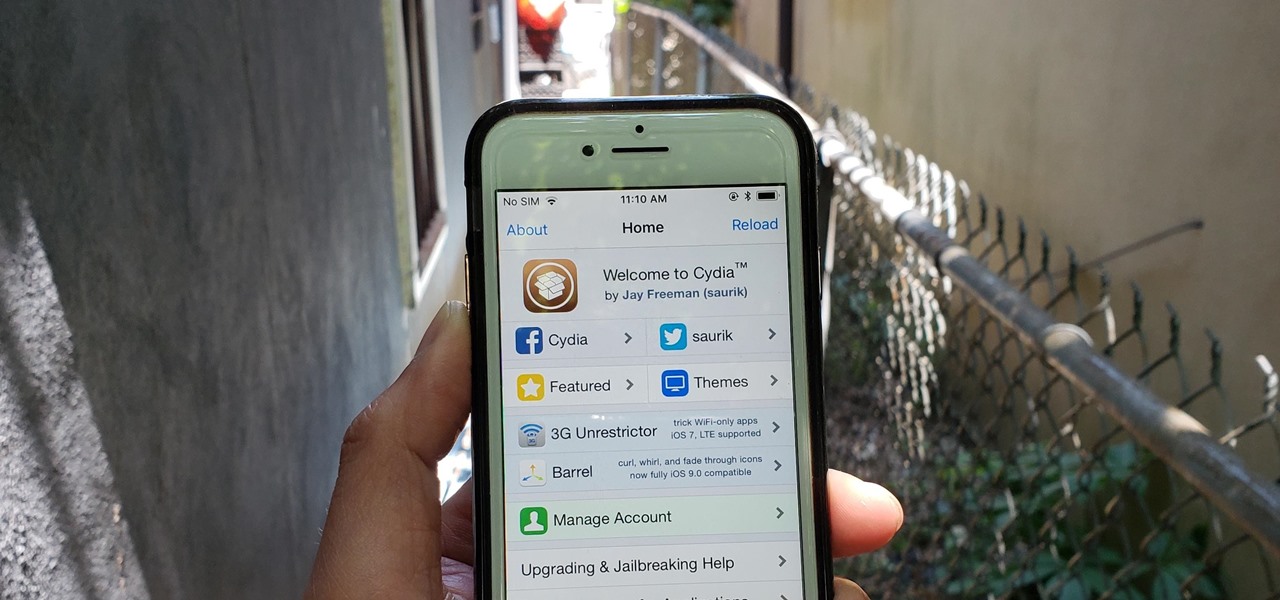
It's been a long road, but the guys over at CoolStar have finally come up with a stable, semi-untethered jailbreak for 64-bit iPhones, iPads, and iPad touches running on iOS 11.2 up to 11.3.1, with the latest update extending coverage to 11.4 beta 3. So if you've held off on updating to the latest iOS 11.4.1, your patience has finally paid off.

Google Chrome is an incredibly popular web browser on both iOS and Android devices, just like its desktop version. That's why it's number one browser in both the iOS App Store and Google Play Store. But for those of you who want even more features, you can test drive the Chrome Beta and get new updates first.

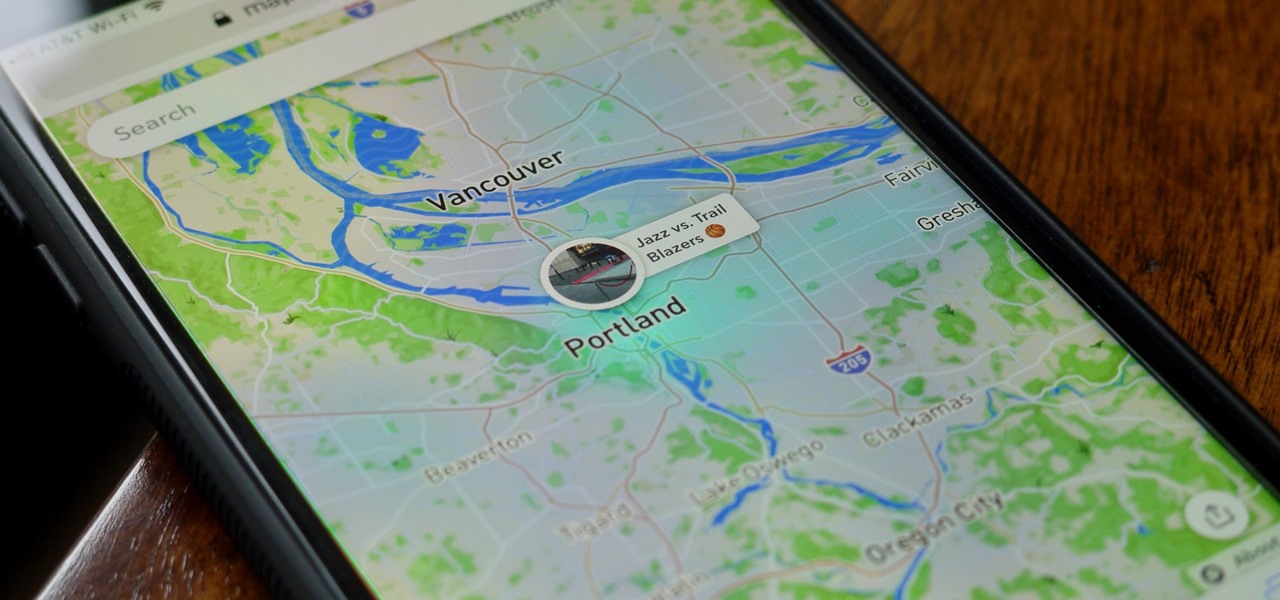
While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

The Guardians of the Galaxy have to be the most fun superhero team to have at a Halloween party. They dance, they break the rules, and they definitely have the grooviest music. So the Guardians are a great bunch to pick from for your Halloween costume — or even for a themed group costume. Just imagine the badass vibe when you all walk into a venue together with Star-Lord blasting "Cherry Bomb" from a portable speaker. Here's a roundup of some of the best Guardians of the Galaxy costume guides...

There are many different ways and many different apps that allow you to censor a racy photo and then share it to Instagram or Facebook. If you're in a time crunch and don't have the time or the patience to deal with something like Photoshop, then Snapseed is a great and easy app that will blur out your raunchy images in a quickie.

Wheat toast. White toast. Sweet potato toast. Okay, one of these things is not like the others... Don't Miss:

If you're here, you're probably one of the seven people dedicated to making Mac n' Cheetos a permanent part of the Burger King menu.

The sprouts, they're alive! Alive, I tell you—aaaaaaliiiiiive! (Cue dramatic music.) It's true: sprouts are a living food, and they're packed with more nutritional benefits than some raw vegetables. It's easy and fun to grow your own sprouts from seeds, legumes, and grains. Plus, watching them grow is incredibly satisfying—you're bringing new life into the world (and onto your plate)!

With the warm summer months right around the corner, just the thought of having to bake anything in your oven may have you perspiring profusely. But you don't want to give up dessert, especially not luscious, layered cakes, so what's a sweaty sweets-lover to do?

Desserts always taste better when they are sugar-coated—and even more so when they're coated in powdered sugar. In particular, crinkle cookies—cake-y cookies that are chewy on the inside and crispy on the outside—are famous for the powdered sugar that creates their cracked appearance.

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

At-home cooks tend to be scared of soufflés. Either they don't rise at all or they end up all sad and lopsided. However, when successful, the end product cannot be matched in impressing your guests.

Cheesecake is pretty awesome. It's super versatile, allowing you to change crust bases and toppings quite dramatically and still end up with something that's elegant and delicious. Which is why it's a great dish to add to your dessert repertoire! There are a number of approaches to making a cheesecake base: classic, new york style and no-bake. Today we're going to go down the more classic route.

One of the best things about summertime is that there's lots of outdoor cooking, whether you're on a camping trip or grilling. And what better way to end your meal than with the classic dessert, s'mores?

The launch of Android 4.4 KitKat alongside the Nexus 5 was met with much fanfare from Android enthusiasts. Unfortunately, if you don't have a Nexus device or are still awaiting the 4.4 update, you may feel a bit left behind.

It seems nowadays the word "easy" has taken on an alternate meaning. When I see "easy," I expect a quick and painless process, but when it comes to flashing or installing a custom ROM, easy means anything but.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

For those of you still using a BlackBerry smartphone, this article will show you the tips and tricks to installing emulators and playing some classic Game Boy Advanced games on your device. You can find a few tutorials and videos out there on getting Game Boy Color or NES games on an Android device, but the most elusive mobile emulator is for Game Boy Advanced (GBA) on a BlackBerry.

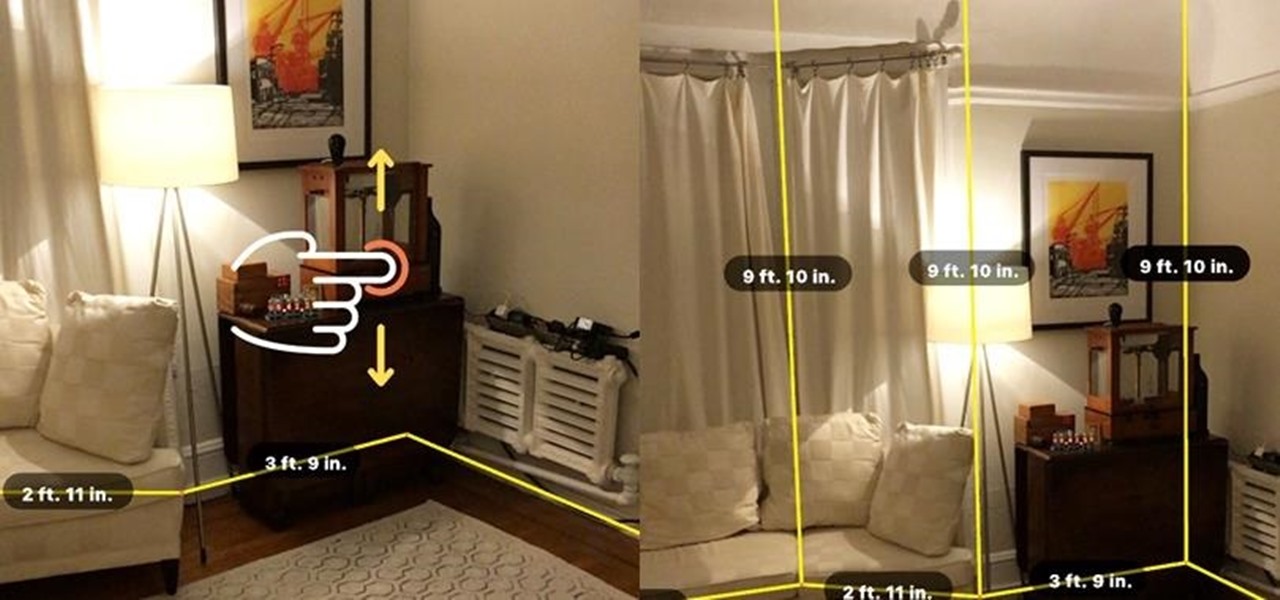
The long wait is over — the best augmented reality device on the planet is finally available.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.