In this tutorial, we learn how to force an iPhone or iPod touch to turn off. First, hold the power button ( at the top of the device) and home button (one the bottom middle) at the same time and wait until the screen turns completely off. To turn back on, press the power button that is located at the top of the device. You will see an Apple logo pop up and it will stay on the screen for several seconds. After it's loaded, it will re-boot as normal and your regular home page will show up as it...

This video shows the viewer how to ‘hit down on a golf swing’. The idea of hitting down on a gold swing is that when you take your club back you do not move backwards. You stay ‘over the ball’ and simply rotate back using your hips. You then rotate forwards with your hips as you hit the ball and extend your arms. The club should connect with the lower half of the ball. This seems counter intuitive but the angle of the club should appear to be ‘down’ on the ball – this is where the term comes ...

This video teaches the viewer how to multiply fractions with mixed numbers. You would first need to multiply the denominator by the whole number, and then add the product to the numerator. This number is your new numerator and the new denominator is the same as before. For example, 2 1/5 = 11/5. Now you have an equation with fractions and no whole numbers. You may now proceed to multiply straight across. Multiply the numerators together to create a new numerator and do the same for the denomi...

The mother's body can be the source of delivery complications like placenta previa or uterine rupture. If delivery problems do occur, your doctor can usually help you manage these childbirth complications with medication or an emergency cesarean section.

Watch this instructional video to learn how to use buzz bait. Buzz baiting uses counter rotating pepper jigs buzz bait with a drop down head. What you'll want to do with this one is just make a good long casts. You want to get it tightly covered as you can right along the edges and breaks, bounce it over rocks, go right through the middle of the brush. It'll stay fairly weaveless as long as you'll keep it moving, and be aggressive with it. Fish it where you don't think you can get anything el...

The COVID-19 pandemic has created a frenzy for news and information that is nearly unprecedented in the smartphone era, with a major side effect of misinformation. Now, major tech companies are making it easier to ask for advice about novel coronavirus from their respective digital assistants. Results may vary, but Apple and Google are the most useful at the moment.

Whenever the name Magic Leap comes up, the talk inevitably seems to turn to the company's big-name backers and "unicorn-level" amounts of cash poured into the venture. And if it's not that, observers tend to focus on the company's market strategy and overall prospects.

OnePlus is known for making a quality products with their line of smartphones, but as with most, they have their own specific customizations that you can't get anywhere else. Font types, boot animations, sounds, and proprietary apps — they are all unique to each different skin of Android. The good news, though? There's an effortless way you can grab some of that OxygenOS goodness right now.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

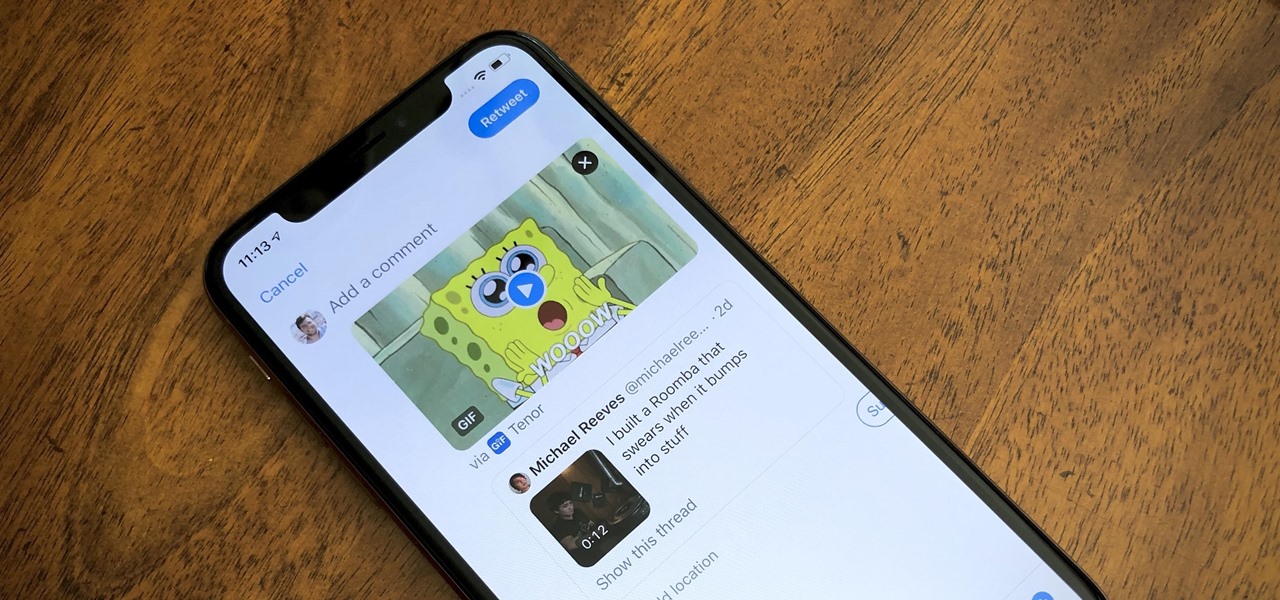
On Twitter, quote retweets are a great way to share someone else's tweet with your view of their message. Twitter has expanded on this idea by giving us the ability to attach images, video, and GIFs to quote retweets. With these extra options, you should have no problem adding your own unique perspective on that funny, serious, or professional tweet.

As the opening act to the grand unveiling of the long-awaited HoloLens 2 at Mobile World Congress Barcelona on Sunday, Microsoft showed off the standalone Azure Kinect time of flight sensor, which also happens to supply the improved human and environmental understanding capabilities of the next-generation augmented reality headset.

Fresh off shipping an augmented reality game for Magic Leap, Resolution Games has farmed another $7.5 million in funding through a Series B round.

So far, consumer augmented reality headsets haven't found mainstream success. That's primarily because no manufacturer has managed to hit the sweet spot between slim form factor, performance, and affordability.

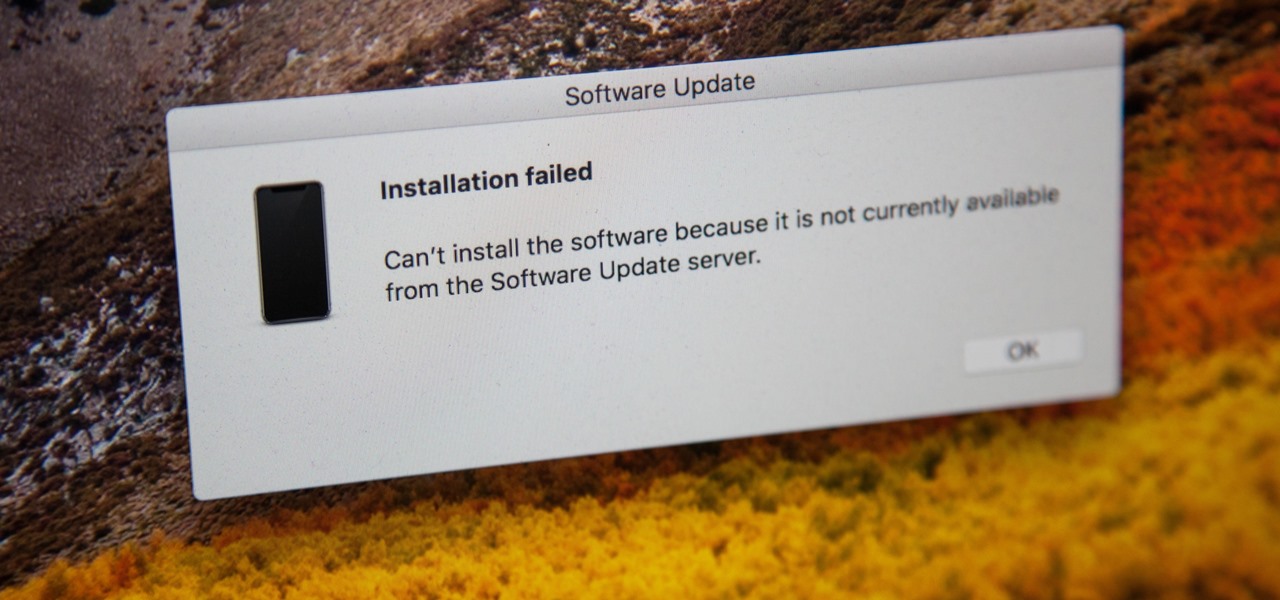
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

Using a passcode on your Apple Watch is a good way to keep other people out of your data, but what happens when you see that "Wrong Passcode" screen yourself? You can, of course, try again in a minute, but if you've forgotten it for good, there's still a way to get back into your Apple Watch.

On May 17 2018, Valve released the Android beta version of their Steam Link app, which allows you to stream Steam games from your computer directly to your phone. You'll probably also want to connect your favorite controller to your phone, but you may run into some issues if you prefer Valve's own Steam Controller.

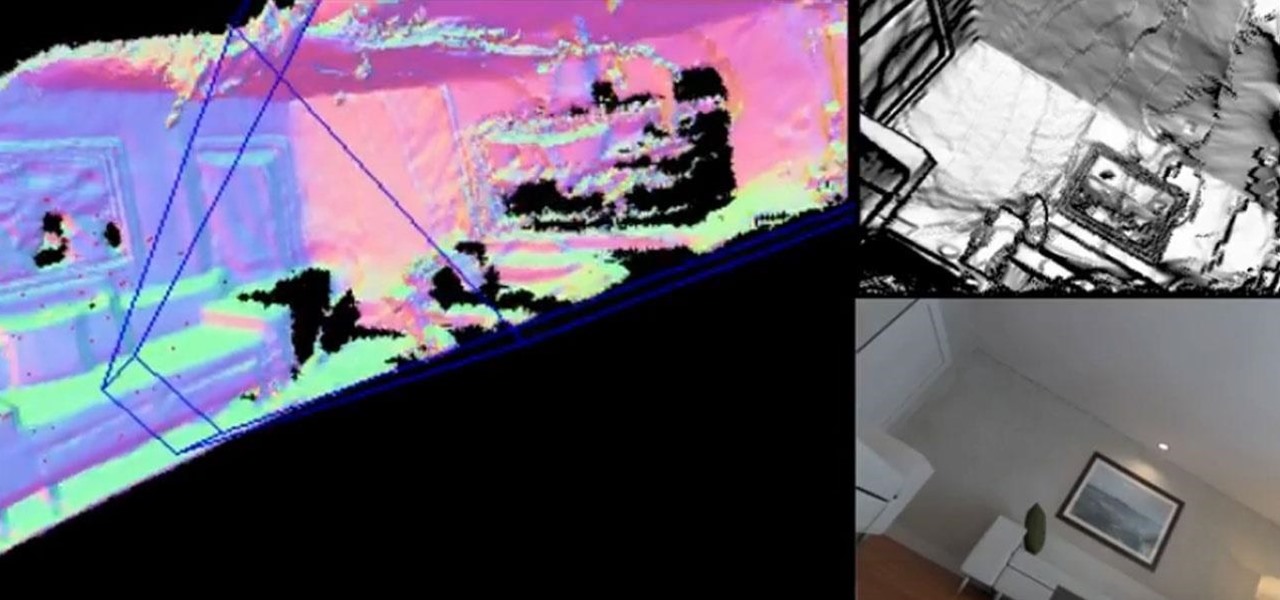
Augmented reality startup 6D.ai is now accepting applicants for the closed beta of its 6D SDK. While operating in the background on a smartphone, the computer vision platform captures a dense 3D mesh in real time using just the device's camera (such a feat typically requires a depth sensor).

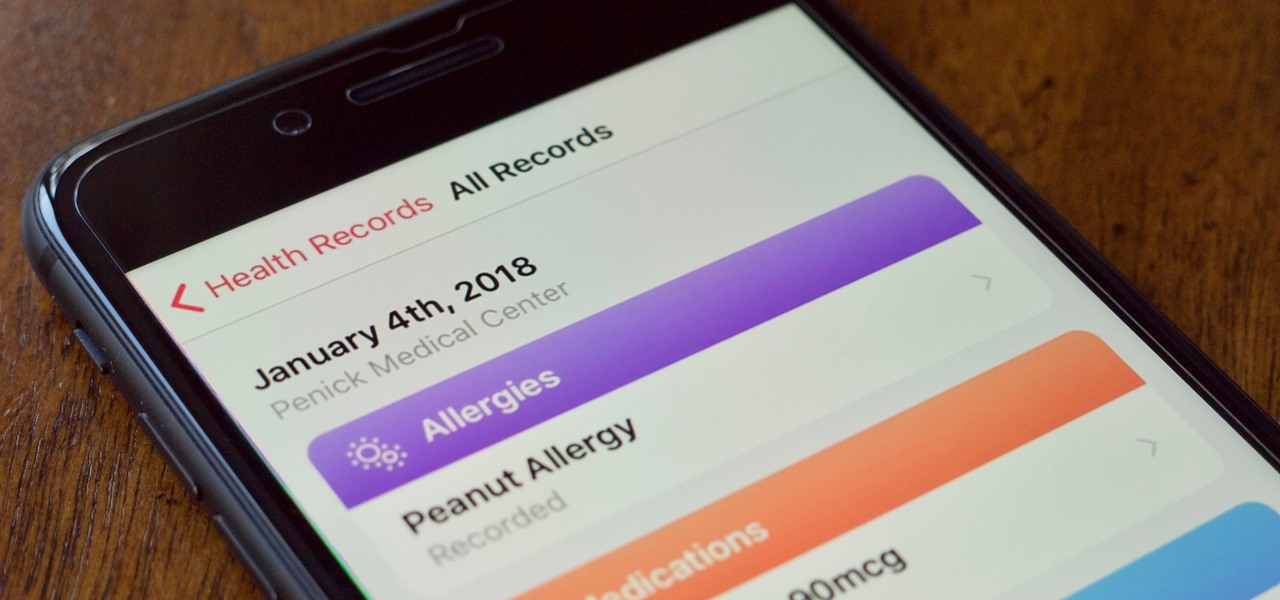
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Considered by many (perhaps unfairly) to be a very public failure, Google Glass can add another plot point to its comeback story, this time as a tool to teach social skills to children and adults with autism.

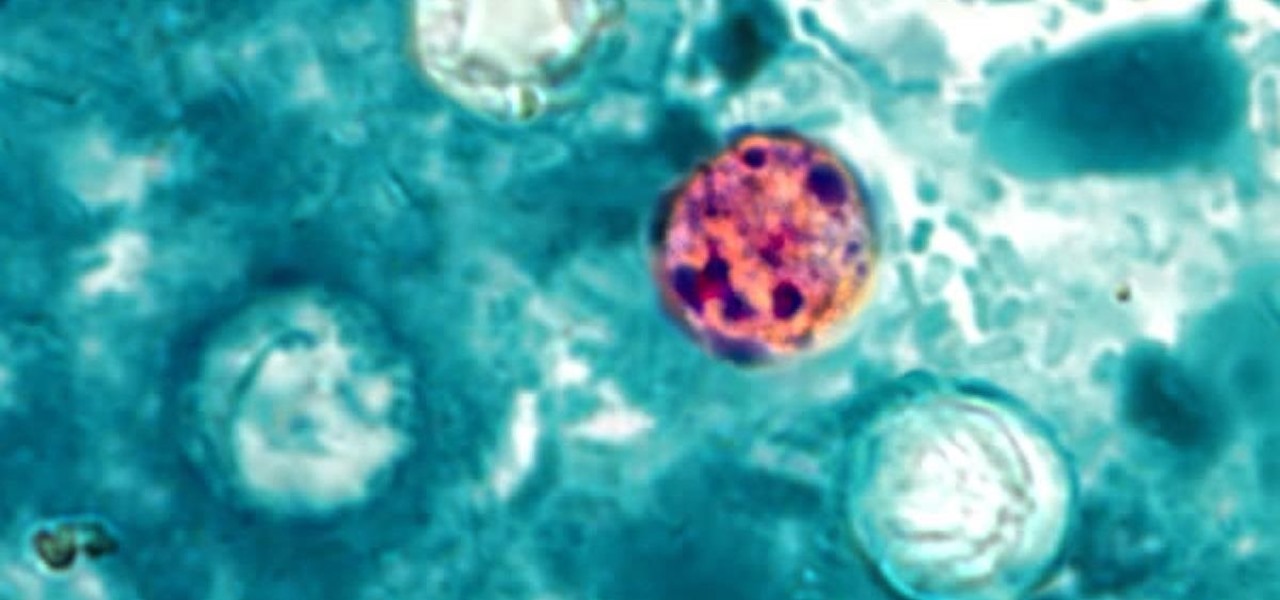
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

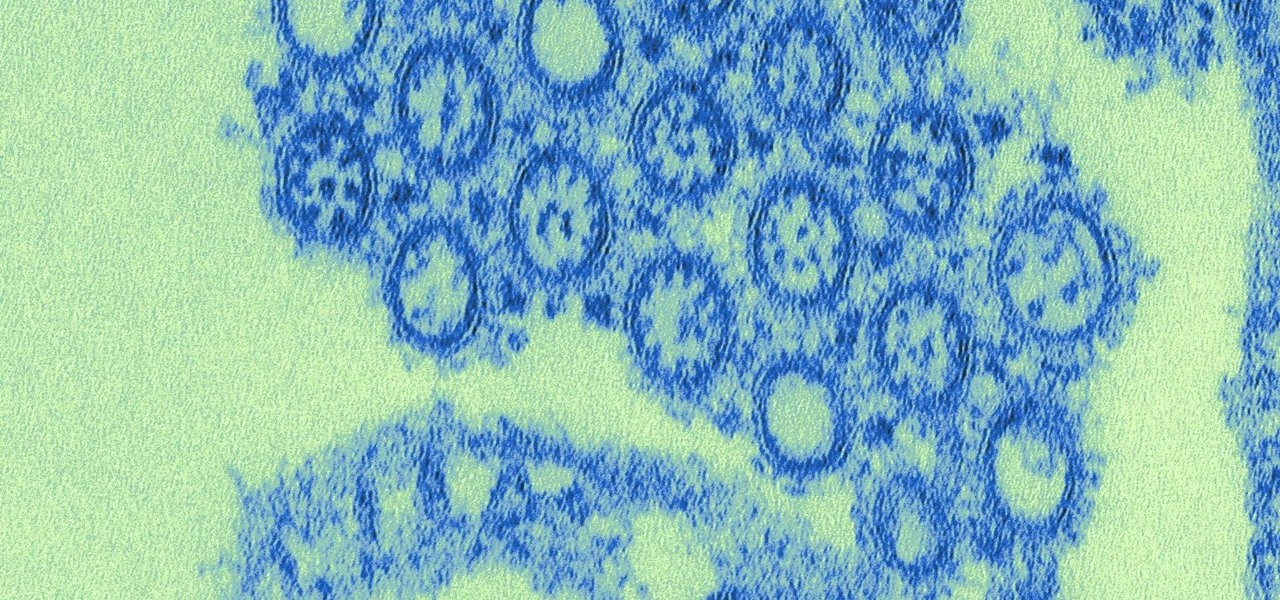
A new study shows the Zika virus is present in saliva — but it may not be enough to make you sick. The Centers for Disease Control and Prevention notes there is "no evidence that Zika can be transmitted through saliva during deep kissing." Given the results of research published in the journal, Nature Communications," the agency may need to revise its guidance.

Growing evidence suggests that neurodegenerative diseases like Parkinson's may develop in part due to environmental factors, including infections that can cause inflammation in the nervous system. New research from investigators from Jude Children's Research Hospital and Thomas Jefferson University has strengthened that connection.

Perhaps in tribute to the season premiere of Game of Thrones, Google Glass is demonstrating that what is dead may never die, as Alphabet's X (formerly Googlex) has revealed that the Enterprise Edition of the smart glasses are now available to businesses.

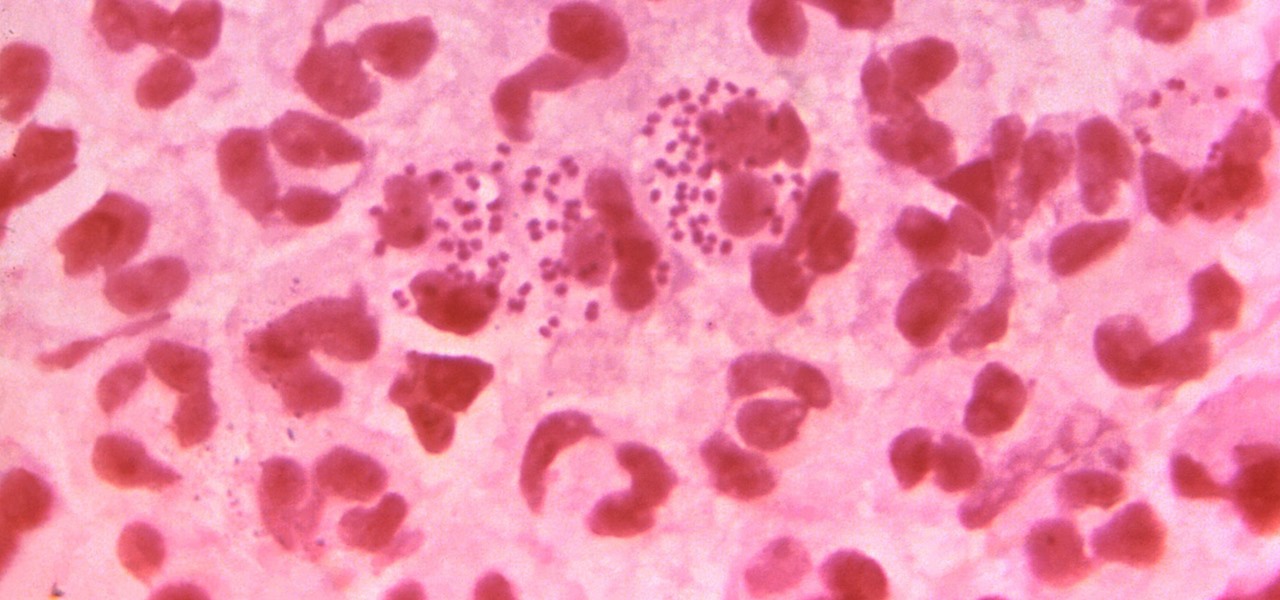
In the race to outsmart "untreatable" antibiotic-resistant gonorrhea, one of the three new treatments on the track is about to enter Phase 3 clinical trials. Hopefully, it'll be widely accessible sooner rather than later, for the 78 million people who are diagnosed with gonorrhea each year.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

New research reveals how E. coli bacteria construct elaborate and effective tunnels to pump unwanted molecules like antibiotics and other toxins out of cells. The discovery could help us better understand how antibiotic resistance occurs and give us a leg-up to beat them at their own game.

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.

In this Tuesday's Brief Reality report, there's a trio of stories from the healthcare world where augmented reality is helping out with surgical microscopes, asthma treatment, and other diagnostic and treatment tools. There's also something for all of you AR/VR storytellers out there.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

Move over rainbow food trends, there's a new, darker kid in town: jet black ice cream. And no, it doesn't have squid ink in it.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.