The ability to see the world around you and instantly share that "vision" is something that makes Google Glass great for everyday use. No reason to pull out your phone to show off the amazing sushi plate you were just served—look at it, give a couple of quick taps and voice commands, and boom, your social network is salivating in jealousy.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Snapchat is great for sharing and receiving pictures that we don't want "living" for too long, but sometimes we'd like to hold onto those memories, whether the other party wants us to or not.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.
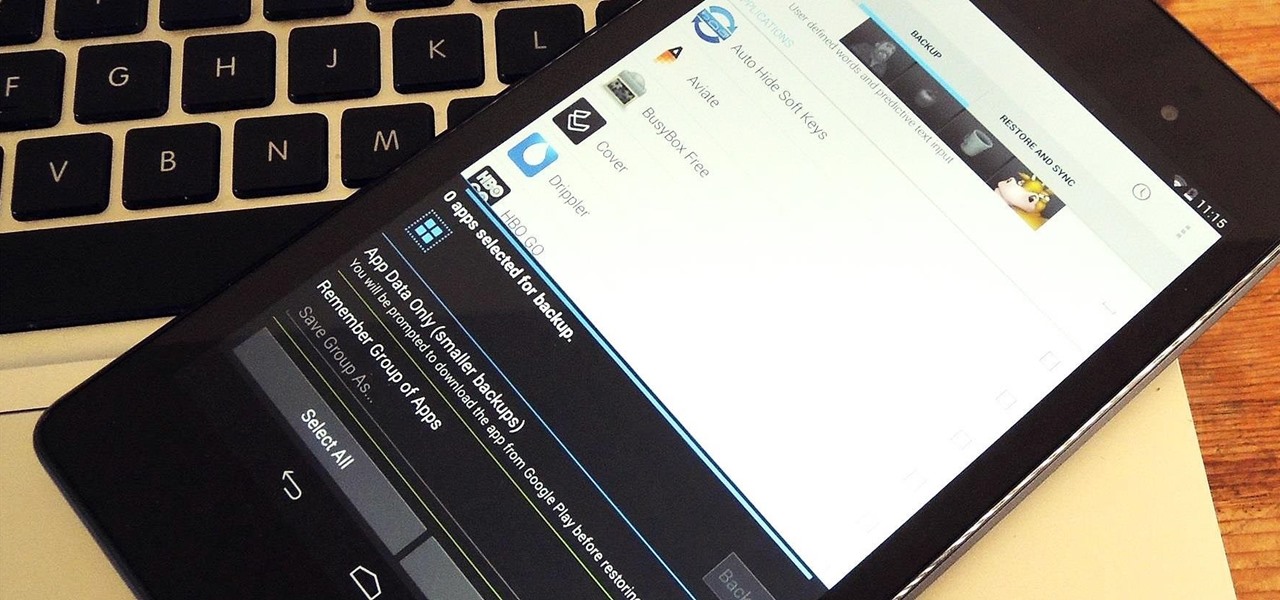
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

This last weekend, Apple released the second beta of iOS 7.1 for iPad, iPhone, and iPod touch, and I've got a firsthand look of what's to come in iOS 7.1—the first major update since iOS 7 was released.

Whether it's because you want to make a quick tutorial video or want to show off your gameplay skills, recording the screen your Nexus 7 tablet isn't an easy feat. At least, until now. Hidden inside Android 4.4 KitKat is a built-in screen capturing feature, but it takes a little effort to dig it out.

Instagram recently released their new Instagram Direct messaging feature in their Android and iOS apps, which lets users share private photos and videos directly with individuals or groups of up to 15 users. However, there are no restrictions on who you can send private photos or videos to.

Hey guy's, hope everything's going well! Here's a snippet of a few cool things and the latest news on Minecraft.

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

While there's still no set date, Jelly Bean 4.3 is rumored to be released on the Samsung Galaxy S4 and other TouchWiz devices within the next couple of weeks (or months), presumably sometime after the upcoming Samsung Unpacked event.

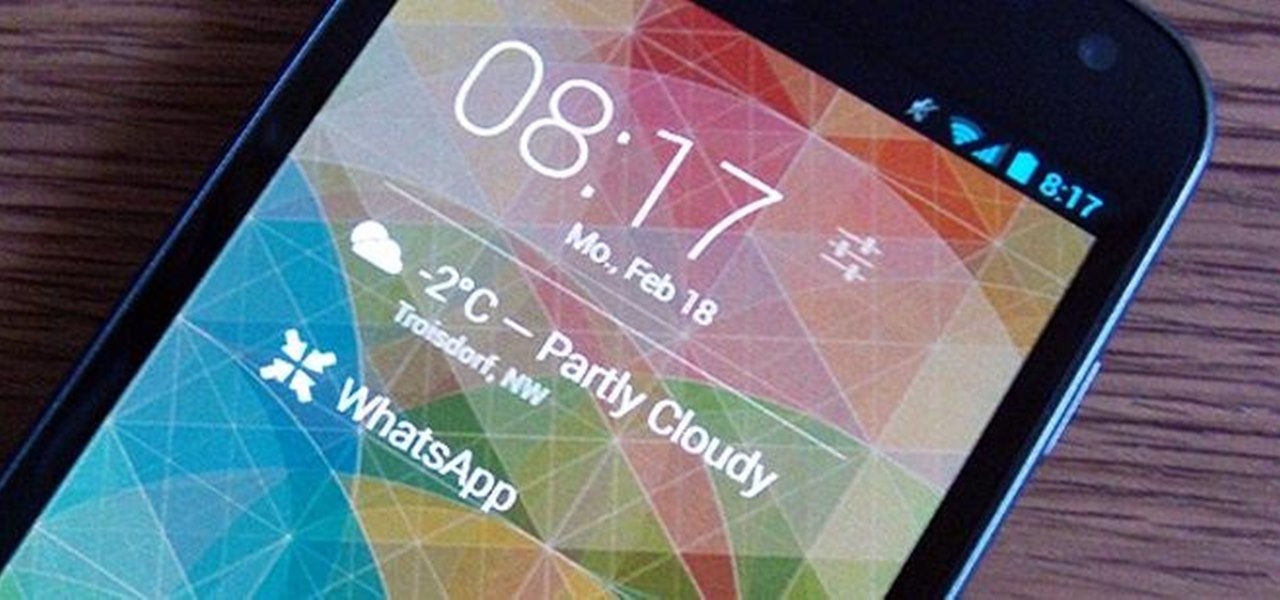
The new Android 4.3 Jelly Bean has been out for a while already, and most of you already have it installed on your Nexus 7 tablets. Many of you softModders have also probably rooted your tablet so you can take advantage of some of the more popular root-only softMods, like speeding up performance, installing WhatsApp, increasing internet speeds, getting Beats Audio, etc.

The new Jelly Bean is out in the wild, but if you've installed Android 4.3 from stock, you'll notice rooting is now not possible. If you miss the ad-blocking capabilities of AdBlock Plus, how Seeder made apps snappier, or the convenience of backing up with Titanium Backup, you'll need to get rooted.

To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you.

One thing that gets overlooked on Facebook is the amount of videos you can watch, and I'm not just talking about videos uploaded directly by Facebook users—I mean everything ever shared—YouTube, Vine, Instagram, Vimeo, etc.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

I've been a Sprint customer for a long time. Normally, Sprint (flagship) phones come with some useful apps, such as Sprint TV, Sprint Zone (for payments, updating PRLs, and account information), and NBA Game Time. In other words, relatively free of bloat.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

We've all had that moment when we enter into a classroom, meeting, or theater and completely forget to put our cell phones on silent.

It's all about widgets. Widgets are one of the most important features on an Android phone—they can provide valuable information at a glance and are easily customizable.

WhatsApp is a very popular messaging app on the Play Store, but unfortunately, tablet users have been left out of all the fun because WhatsApp only works on smartphones—until now.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

On the iPhone, the Reminder app is a great way to keep track of your to-do list. I use it for a bunch of crap I forget, like picking up a must-have item at the store or calling or emailing my friends back.

The PlayStation 3 is a sweet gaming system, and even though Blu-ray discs didn't really live up to all the hype and there is still no HBO GO app available, I love my PS3. One of the coolest things about it is that you can customize it to look however you want. One of the most common ways to do this is by changing the wallpaper, but most people use their computers to transfer wallpaper images over.

Inverting colors on your mobile device not only saves battery life, but also helps prevent straining your eyes, especially during the nighttime. Bright white screens interfere not only with your eyes, but with your sleeping patterns, as well. The bright lights greatly reduce your melatonin, a hormone secreted by the pineal gland in the brain that helps you go to sleep. Thus, the onset of sleep is delayed and the possibility of deep sleep is reduced greatly.

Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Lightning has struck, but not everyone is excited. Apple's new 8-pin Lightning connector for the iPhone 5 has replaced the aging 30-pin connector. Many users have concerns that their current third-party devices will no longer operate properly with the smaller all-digital design, not to mention the expensive price tag for each adapter. What Does This Mean for the User?

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

If you haven't heard of Steampunk, then you've obviously been living under a rock for the past couple of years. Steampunk style, which is an ironic style composed of designs that fuse anachronistic technology (proppellers, watch parts, etc.) with Victorian style.

While most of us have mailboxes from which we receive our deliveries, some of us still have small slits in our front doors known as letter box holes. This allows for the mailman to deliver mail straight into our homes, which is convenient for all intensive purposes.

If you're a vegetarian, you know that it's very difficult to find a good vegetarian dish at most restaurants. True, most restaurants offer vegetarian options, but it's hard to find a vegetarian dish that's actually delicious and a hit with your taste buds.