Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

There are myriad wrong ways to cut an onion, a few right ways to cut an onion (including this one)... but only one ultimate way to dice onions, and that's what I'll be sharing with you today.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Hello friends. This is actually my first how to.

Chicken breasts have gotten a bad rap. Dry, flavorless, boring... poor white meat gets no love, and dark meat gets all of the credit for being sinfully flavorful and delicious. But the truth is, even though chicken breasts are lower in fat and calories, they can also be incredibly versatile and full of flavor... if they're prepared correctly. You're probably familiar with poaching, which is a technique that gently cooks more delicate meats such as chicken or fish fully submerged in a liquid b...

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

The morning started out like most of them do: I was hungry, and it was time to chow down on some breakfast. However, this particular morning had me craving something besides the usual milk and cereal.

Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Hearthstone is a collectible card game by world-class developer Blizzard Entertainment. It has taken an entire generation of casual and professional gamers alike by storm. So many people play it, chances are you've already sunk some money into it. So, if you're going to pay a little anyway, you may as well get a discount.

When it comes to your baby and your time, nothing but the best and most efficient will do. These high standards carry through every aspect of your life as a new parent, from diapers to strollers and especially to food.

Everyone starts their mornings differently, but one common thread amongst the masses tends to be the consumption of coffee, albeit in many different forms—instant, pre-ground, K-Cups, Nespresso, and so on. And I'm sure that we all have our own preferred methods, as well.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

There are few things more satisfying than fulfilling a craving with instant gratification. Companies like Pillsbury and have made this possible with the introduction of their famous Ready to Bake Cookies line: just rip open the package, break off the cookies along the creased lines, place on a cookie sheet, and bake.

There's only one day that can top the aftermath of Easter and its copious amounts of leftover candy, and that is November — the day after Halloween. As you come down from your sugar rush and realize you now own more chocolate than your stomach can physically hold in one sitting ... fear not! Here are several ways to turn your Halloween chocolate into delicious snacks and desserts that you can enjoy at your leisure.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

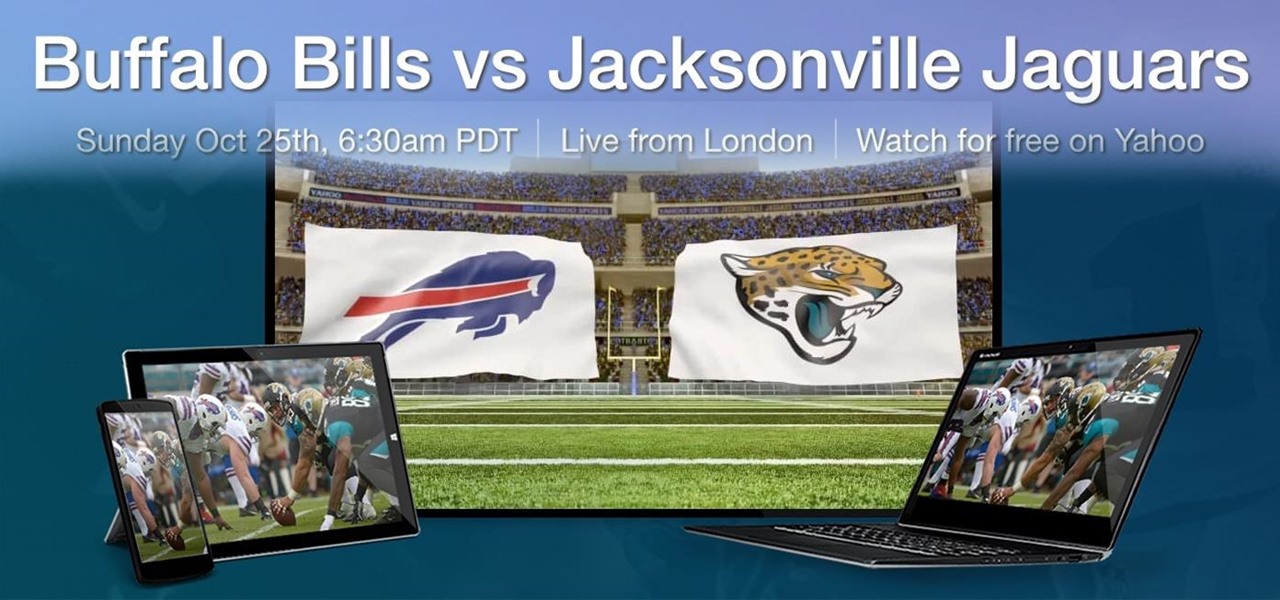
For a lot of would-be cord cutters, the lack of streaming local sports is the only hurdle that needs to be cleared before they can sever all ties with big cable. This is why it was a huge victory for us anti-cable folks when Yahoo announced that they would be hosting the first ever live-streaming NFL game this Sunday at 9:30 AM Eastern.

Samsung's Galaxy series of devices have one common design theme that ties them all together—the physical home button at the bottom of the phone. This button can wake the phone, take you to your home screen, and even scan your fingerprint to securely unlock your device.

Living on a budget often means compromising what you want for what you need—or at least, for what's affordable. But that doesn't necessarily mean you have to compromise on flavor, especially if you know the right tips and tricks to make something spectacular out of the ordinary.

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

Black lights come in all shapes and sizes, and they're useful in a variety of ways. They can help you spot fake currency, urine stains, interesting rocks, and deadly scorpions, and they can even help you view cool fluorescent artwork.

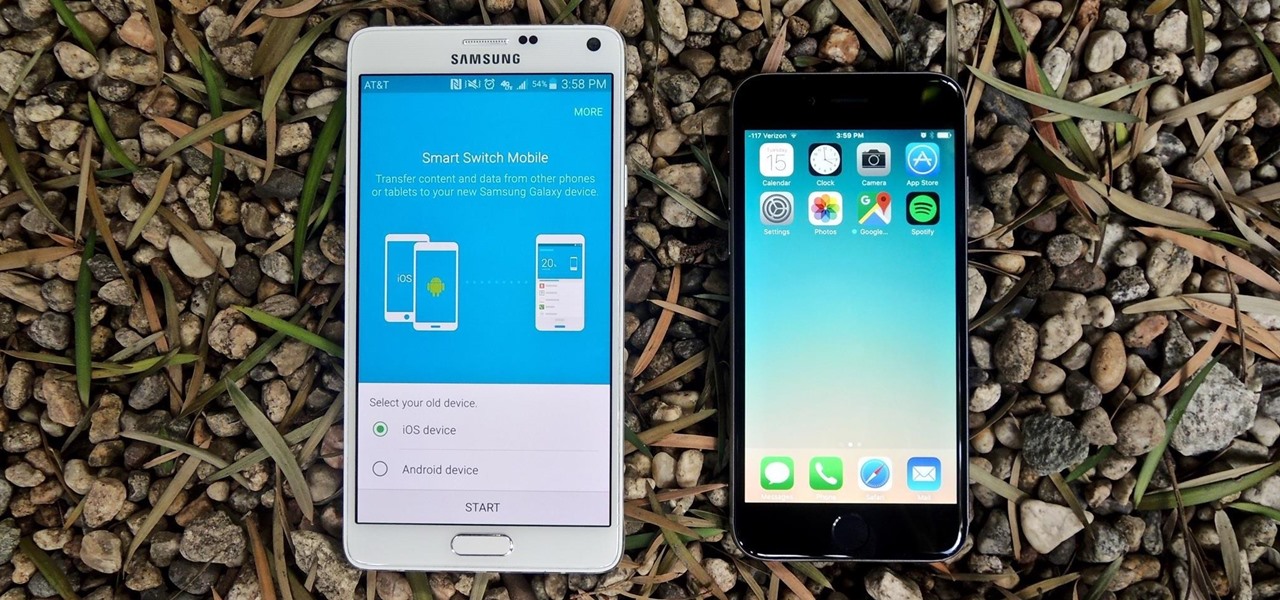
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5.

At night, no matter how dim my Android's screen gets, it never seems to be enough—especially when I'm in bed. In fact, in pure darkness, the lowest brightness setting on my Android devices end up giving me a headache that keeps me up for hours.

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

Initially reluctant to port Firefox over to iOS, Mozilla has finally released the first public preview of their famed web browser. While this is great news for all Firefox users, the bad news is that the browser is currently available for download only in New Zealand.

ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

I've been involved in the Android scene for a very long time and have grown to develop a love/hate relationship with CyanogenMod. While I do like the stability they offer in their custom ROMs, they don't always include the flashy features on top of their vanilla Android base.

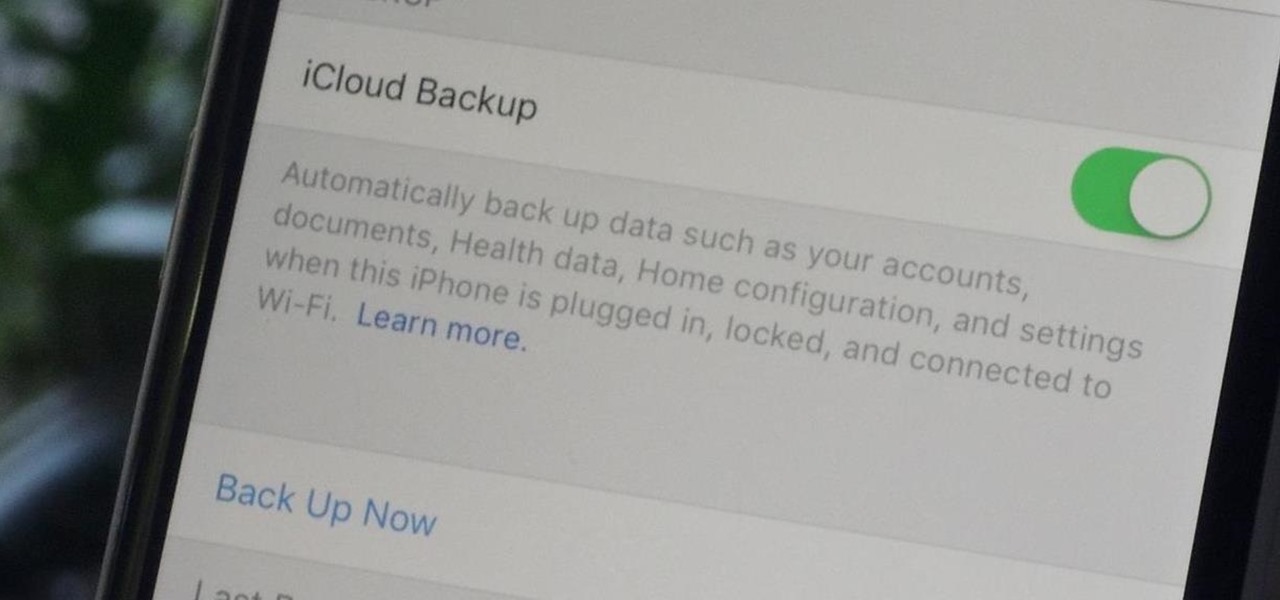
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking process of installing and configuring all of my favorite programs, and I may not ever get things back exactly the way they were.

When summer rolls around, I think of two things: grilling and ice-cold beverages. To me, nothing beats loading up the grill with charcoal, letting the smell of smoke get stuck to your clothing, and imbibing the most refreshing drink you can find.

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Flowers may be beautiful, but they're not usually appetizing. Sure, nasturtiums are hip in fancy restaurants, but they're primarily used as a garnish. Granted, fried squash blossoms are incredible, but the point remains: flowers are usually reserved for looking at, not masticating.