Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

Sometimes you just want to kill a whole bunch of things at once, or to paraphrase Samuel L. Jackson in Jackie Brown, sometimes you absolutely, positively got to kill every mob in the room. Well, the automatic machine gun is the way to do it; accept no substitutes!

Summer is here, and temperatures are rising. Instead of shelling out for an expensive new air conditioning unit, why not build one yourself with a few bucks worth of old computer parts?

Hi! All the cake lovers, welcome to my first post in the World of Dessert Recipes. I would like to contribute a recipe for the chocolate cake, called Taraba. The original recipe was made in Bosnia. It is one of my favorite cakes, very sweet, but does not contain fruit.

One thing that's always important to have in your home office is a bulletin board, because they let you quickly display papers that you need to see every day, such as schedules, notes and memos.

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

Yarn is very useful! If you know how to knit or crochet, you can make everything from clothing to backpacks. But when making large items from yarn, such as a blanket, it can be a bit of a hassle to have to change yarn bundles every time you want a different color or thickness.

Everybody should have plants in their home. Not only do they give off oxygen, but they add a whole new level of decor and awesomeness to an otherwise drab room. So naturally, if you want to improve a room, just display a few plants.

Brushing your teeth is a necessity. You don't want to walk around with yellow teeth and stinky breath, and it's common courtesy to those around you to care about your personal hygiene at least that much.

Hello! I want to share a few thoughts about affection with you. This post is for all who wonder what is or could be the best way to communicate with the person you like. There are many ways of expressing. When Two Worlds, Mars and Venus Collide.

Home cooks know firsthand what it takes to make delicious and amazing food for friends and family. One of the most effective ingredients to making foods as delicious as possible is herbs.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

I was mesmerized by the decoration in Rosalind’s. It has pictures of the Ethiopian people from tribes, the walls are painted bright yellow and covered with black nyala’s an endanger species found in Ethiopia, amazing hut roofs on top of the tables, Hi-Definition television playing a basketball game and neon lights that attracts the eyes. I felt like I was in a different country.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

Jewelry takes patience to make. It's meticulous. It's dexterous. And there's a lot to know, like all the wire-wraps. This wire-wrap is the side-drilled double end wire-wrap. Though the name is long, it's process is the opposite, once you master it. This demonstration video will help walk you through the process of this wire-wrap side-drilled stone (double end) technique.

Jewelry making is meticulous and dependent on detailed movements and dexterity. This wire wrap for necklaces and such could take a little practice, but eventually you should be able to replicate this side-drill single-end wire wrap. This demonstration video will help walk you through the process of this wire wrap.

Tutus are not just for ballerinas anymore! Anyone who feels like twirling, dancing or just running around with a little extra poof can wear one! Follow this tutorial and make a tutu for yourself, your daughter or anyone else looking for a little fluff!

Dying leather is a great option to revamp or change the look of an existing leather piece. Choose a dye that provides the qualities you are looking for, be it flexibility or depth of color. The possibilities are endless.

Learn how to play "When You're Gone" by Avril Lavigne on the guitar. Chords:

We all love the relaxing quality and lovely smell a burning candle adds to a room but it is frustrating when candles burn through too quickly. By taking into consideration the placement and properly prepping the candle you’ll give it a longer life.

Depending on where you live, you will have to prepare for the hazards from different types of natural disasters. You can sleep easy if you have a secure location, stalked with food and supplied you might need if there is an emergency.

Buying a home is a big step so find out just what is involved when you are ready to bid for the house of your dreams. The whole process can be bit nerve-racking but as long as you stick with it you’ll be a home-owner in no time.

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

Everyone floats in the Dead Sea because the amount of salt in water effects the density. Do a hands-on experiment and practice checking density. Here’s a good science experiment to do in class or at home, if you have access to an electronic balance.

Gather your hoop and supplies. Wrap the suede evenly around the entire ring. Wrap it either eight or sixteen times, depending upon your preference. Glue the ends to the hoop. Secure them with a clothespin until the glue dries. Make the web. Tie the nylon string to the suede. Make eight knots evenly dispersed around the ring. Keep the thread taunt between knots. Make a second row. Place each knot "between" the knots of the previous row. Continue in this manner until a small hole remains in the...

Watch this how to video to learn how to make Malfouf, or what is also known as stuffed cabbage is. For this recipe you will need:

Blackjack or 21 as some call it is one of the most popular casino games in the world. It is played by all the players and the dealer being dealt two cards and then they choose to accept more cards or stay with what they have. The object is to get as close to 21 as possible without going over and have a higher number than the dealer after you choose not to accept any more cards. A lot of the popularity of the game is because of the unique combination of luck and skill. In this video series you...

Melody Mann earned & perfected methods of folding depending on where the clothes are going to be after folding.

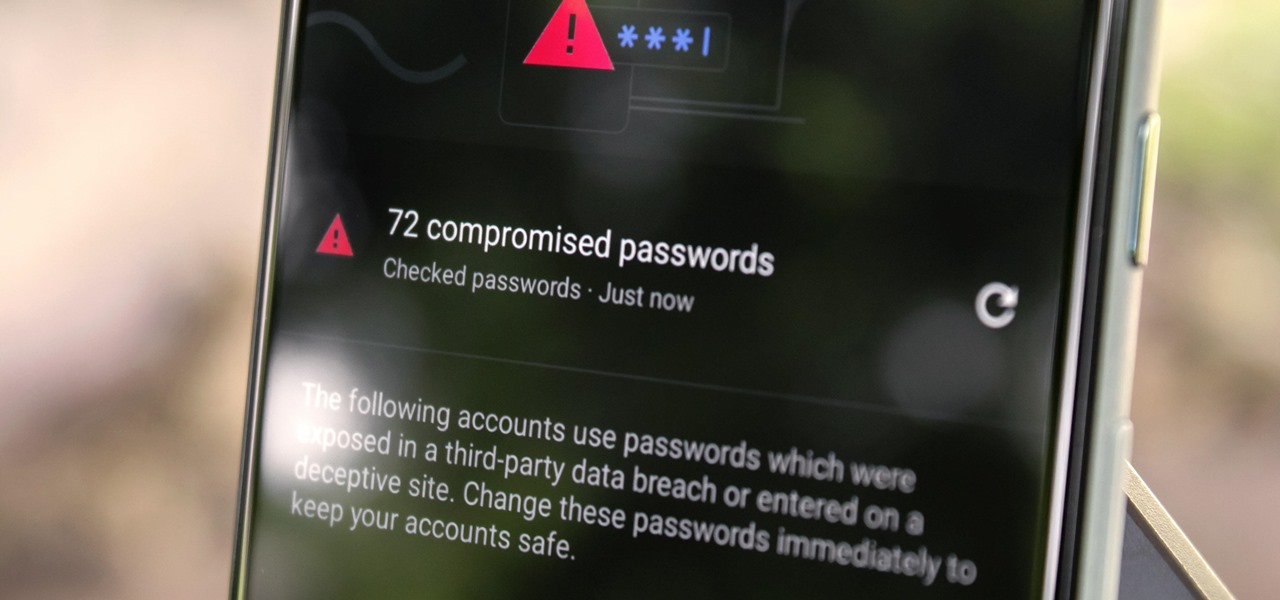
If you save your passwords in Chrome or even just use Android's default password manager, Google has some new security tools you'll be interested in.

The season for outdoor activities and indoor heavy cleaning has arrived, and with that comes all the aches and pains of enjoying it. If you find yourself with sore muscles and no easy way to fix it, then a portable massager you can use whenever you're in pain is something that could put the spring back in your step.

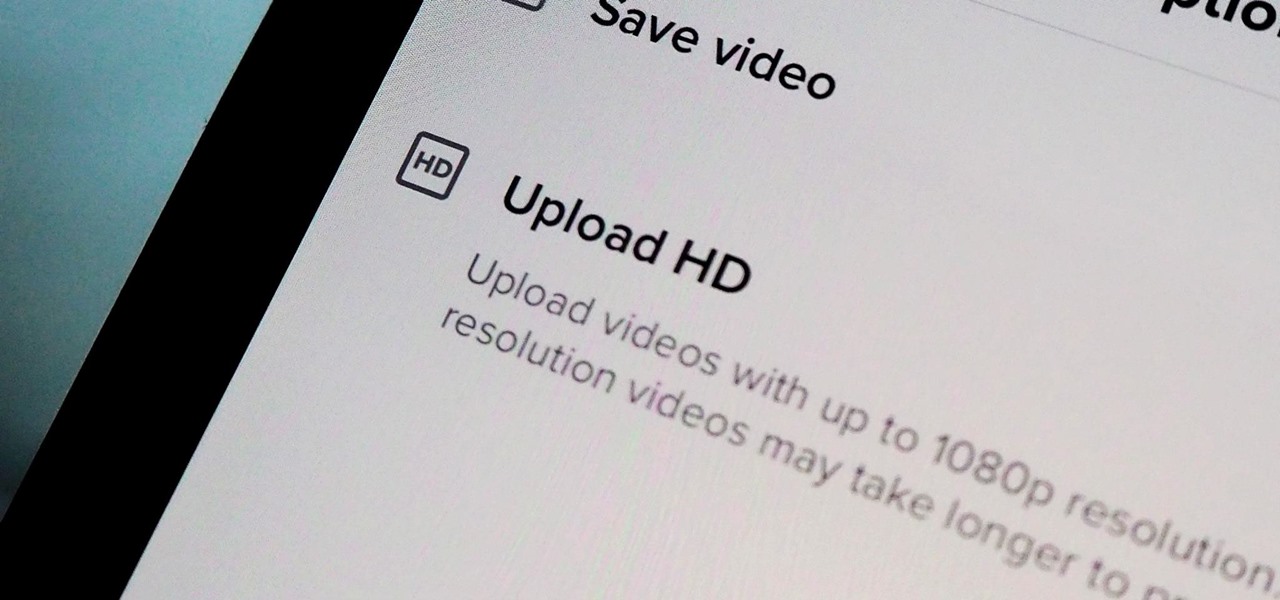
You might have noticed some of the videos you upload to TikTok don't always look great. If you think the answer is that you need a DSLR, you're wrong. The blurriness, pixelation, and overall bad quality that can happen in your uploaded videos is probably not your smartphone's fault — it might be because you aren't uploading your videos in HD.

Apple's "Reachability" feature made its debut with the iPhone 6 and 6 Plus, to compensate for larger screen sizes, allowing users to reach screen items at the top while using one hand. It has since become a staple feature of all iPhones (except the original iPhone SE), but how you activate it varies depending on if it's a model with Face ID or Touch ID.

If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

We all know Android updates have been iffy in the past. But Google has implemented several measures recently that have sped up the process substantially, and OnePlus is taking advantage of these. Still, a staged rollout update might keep you waiting for a few days or longer. So if you'd rather skip the wait, there's a better way to manually check for system updates.

Although Facebook has some questionable privacy and security practices, you'll find it still offers you ways to protect the information that's important to you. One of those ways is locking Messenger behind biometric authentication protocols such as Face ID and Touch ID, ensuring that no one else can access your private chats.