For people who would like to find an easy way to communicate with their loved ones via video or voice chat on their computer, this video will show you how to create and use a Skype account. After going onto Skype.com, you should download Skype, since you will not be able to use this without having the program on your computer. After downloading the file, you should then create an account on the program that appears, creating a username and password. By following these simple steps, anyone wil...

In this tutorial the author shows how to find, download and install Firefox 3. He points out to the Mozilla Firefox website which is [www.mozilla.org/firefox]. Now you reach the Firefox web page where there is a link to download the browser. After clicking the link you will be prompted to save the file and now you can download the software. Now after the software gets installed the author guides you through the various steps to get Firefox 3 installed. He also shows how to transfer settings a...
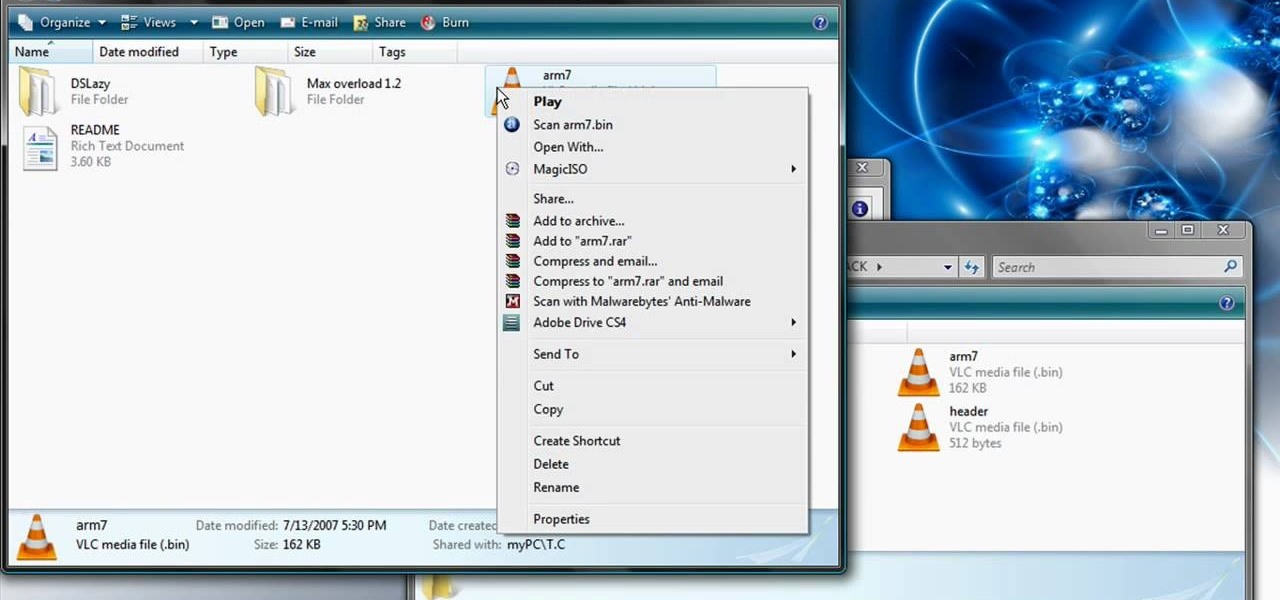
Do you have video games that you long to play on your computer but have errors when you try to play them? Watch this video and your technical problems will be solved in only 6 minutes. Just sit down, relax, and watch the video that guides you with easy steps on how to fix corrupt rom files for games on your Nintendo DS! Be sure to follow the link in order to download the software required to fix your problems! You'll be playing your favorite DS games with ease in no time!
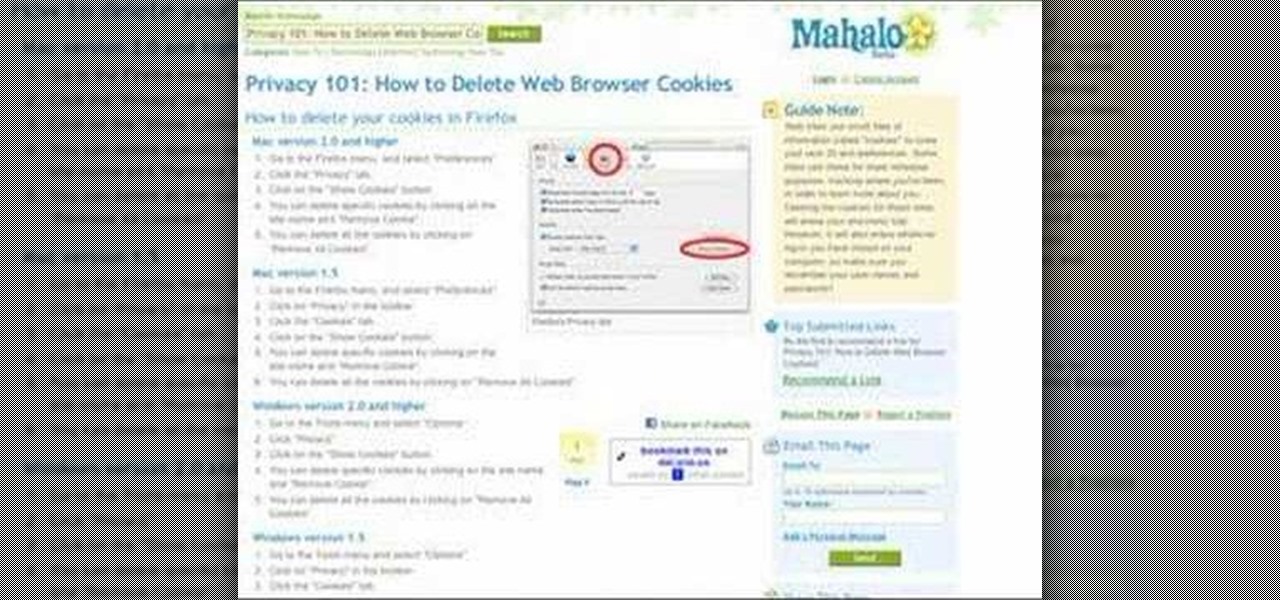
Veronica Belmont shows how to get rid of browser cookies. She starts with explaining what a cookies is, that it is a small file downloaded to the computer from the internet so that the website can remember more information about the users, which she says is quite helpful if you visit a website regularly. She also explains about some malicious cookies which track user actions and report to websites. She now explains how to open options in Firefox browser or settings in Internet Explorer and wh...
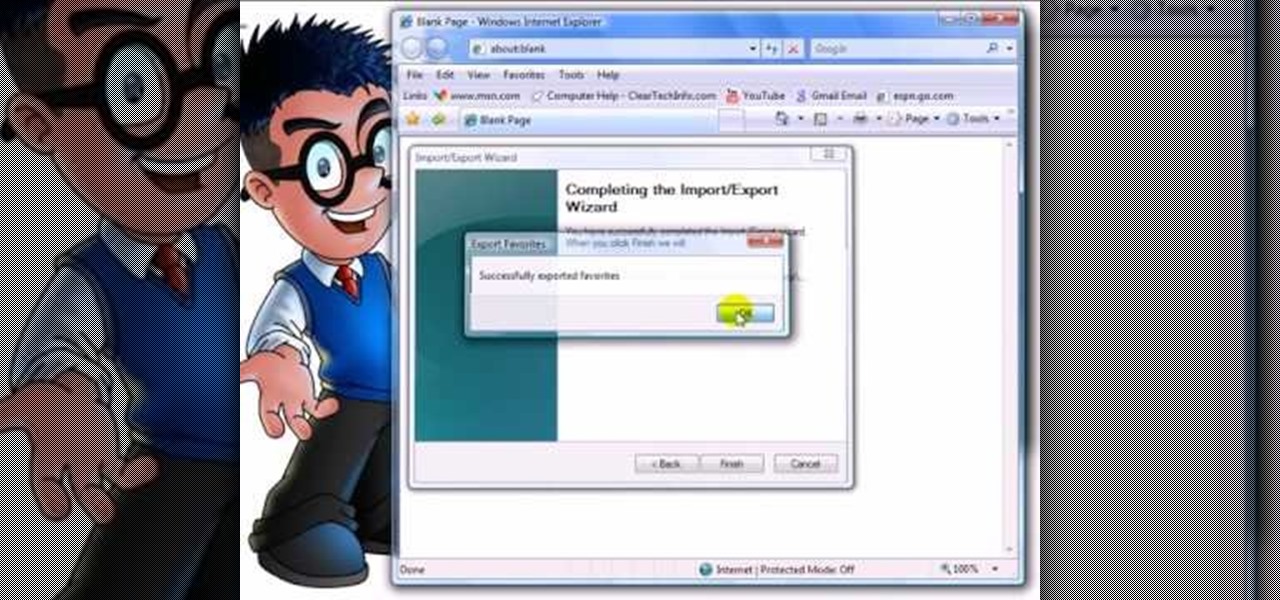
how-to Backup and Restore Your Bookmarks in Internet Explorer ClearTechInfo shows you how to backup and restore all your precious bookmarks in Internet explorer. These bookmarks can be used on another computer or can be restored onto the same computer if and when the bookmarks get erased or corrupt.
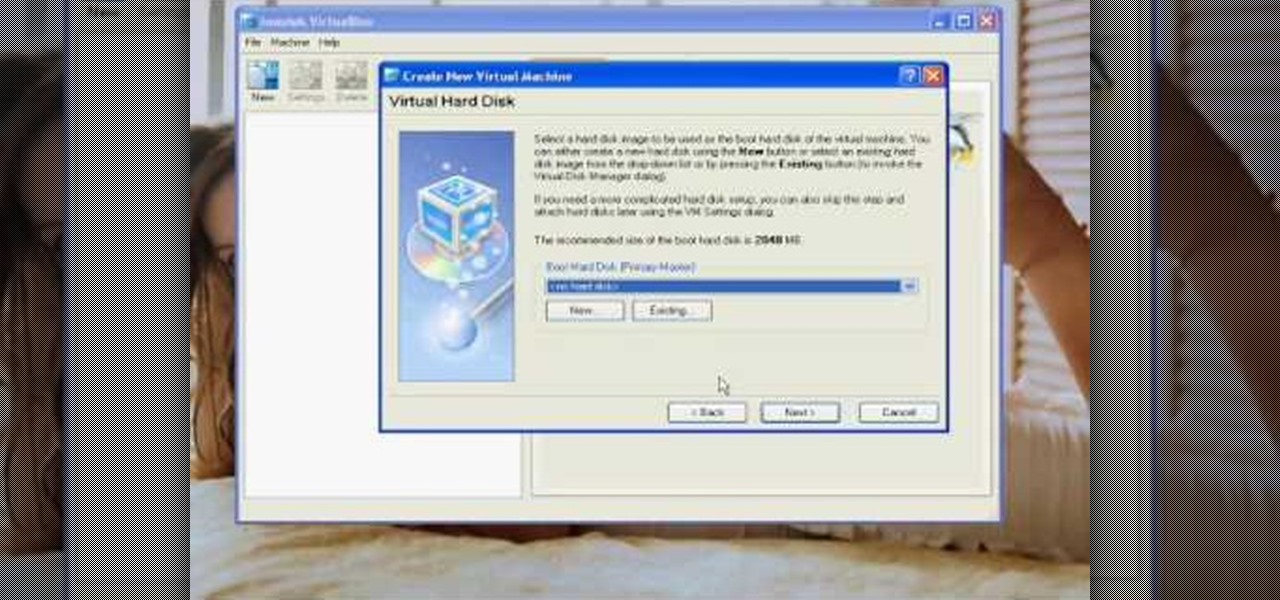
The author shows how to install Puppu Linux 4.3.1 in Innotek VirtualBox 1.5.2. He shows steps to create a new virtual machine in Innotek VirtualBox, by showing the various configuration settings like the RAM size, hard disk space etc. He shows how to boot the virtual machine with the Puppy Linux installation ISO file. Next, during boot up, he shows how to set the language and regional settings, resolution settings etc. In the next screen he shows how to access the local drive and partition it...

This is Cartoonsmart's introductory lesson on how to draw using vector illustration Flash CS4, CS3 or Flash 8.

Have you ever heard of tradigital art? Tradigital art incorporates traditional materials with digital media. This is a combination of such techniques as illustration with Decocolor Markers, Prismacolor Markers, pencils, and Photoshop. Watch this tutorial to learn how to enhance traditional art methods with digital media. It illustrates the tradigital process step-by-step. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

This video shows us how to make quick and cheap ematches from Christmas Lights. • First we need to break the top of the Christmas bulb tubes without damaging the filament inside.

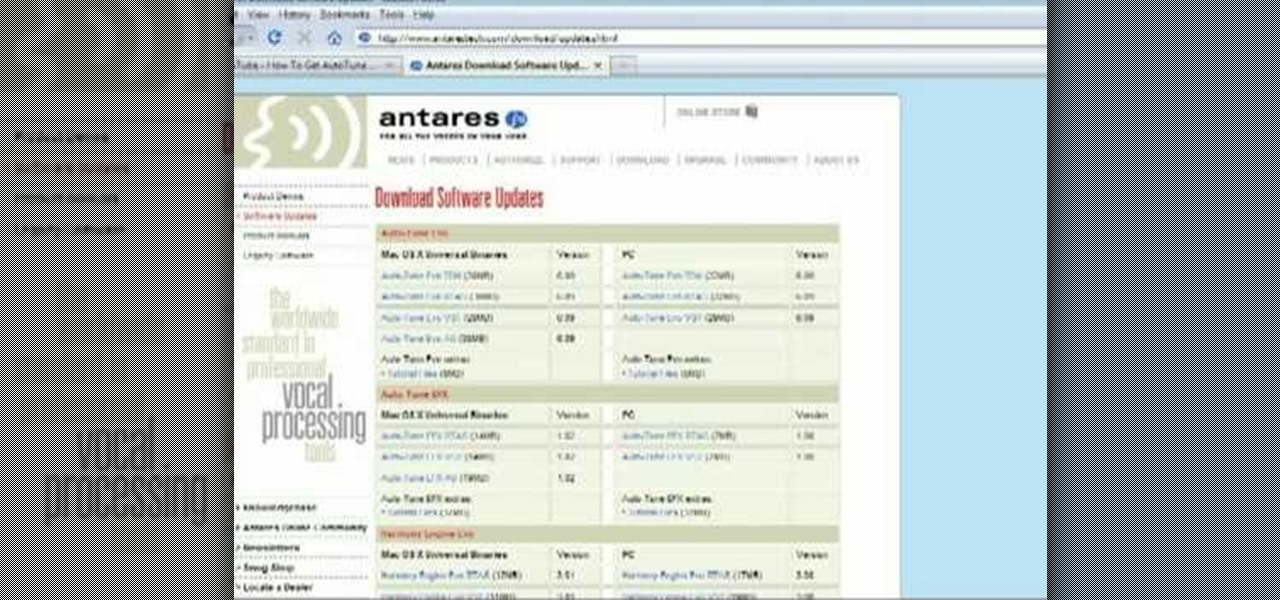
Access auto tune for your Audacity recording software with help from this video tutorial. Step-by-step instructions are gone over, and the following links will be needed:

Check out this masterclass on Houdini 9.5 and how to rebuild the fire simulator. Houdini's Fluid Tools offer a powerful simulation environment for visual effects artists. Senior Mathematician Jeff Lait introduces you to the basic building blocks for generating fluids and low level tools that make it easier to control the simulations.

It's so convenient to take a screengrab of one of your most favorite moments from your favorite movie or show, but sometimes you just can't. But you can actually take a snapshot of it. Check out this video tutorial on how to create screenshots from videos on Ubuntu Linux.

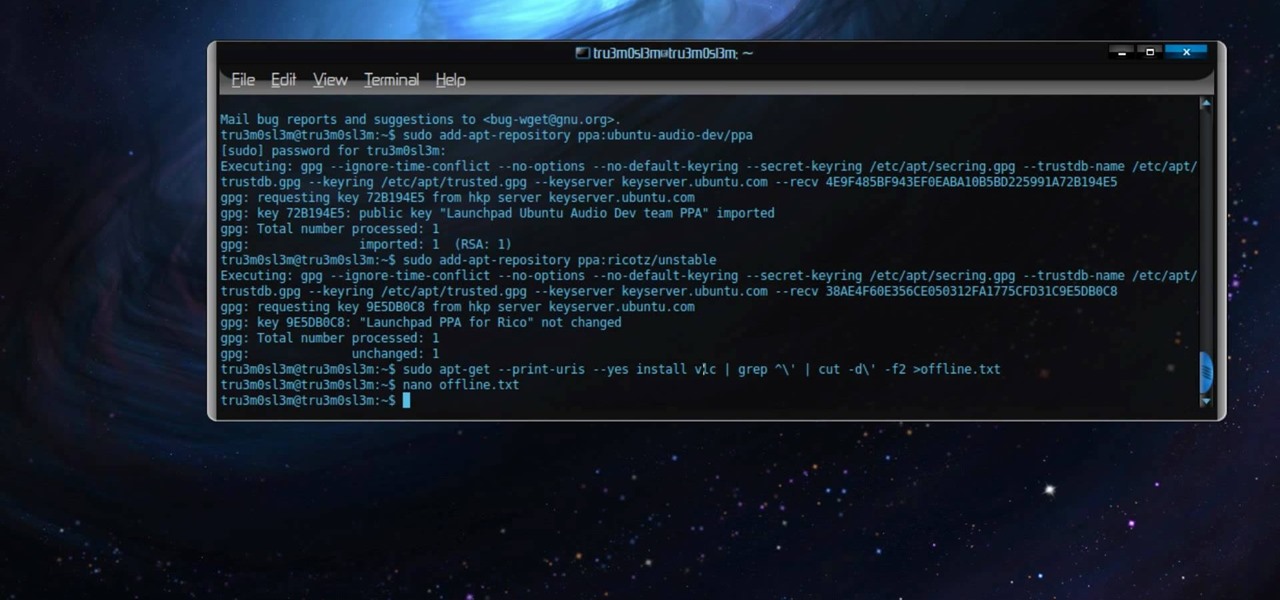
Permanent access to the internet might not always be possible for you and your Linux system, and this computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to offline package install and update on Ubuntu Linux.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Ingrown toenails happen when the nails on your toes grow in the wrong direction and dig into the surrounding skin. Follow a few easy steps to treat this painful condition, and prevent it from happening again.

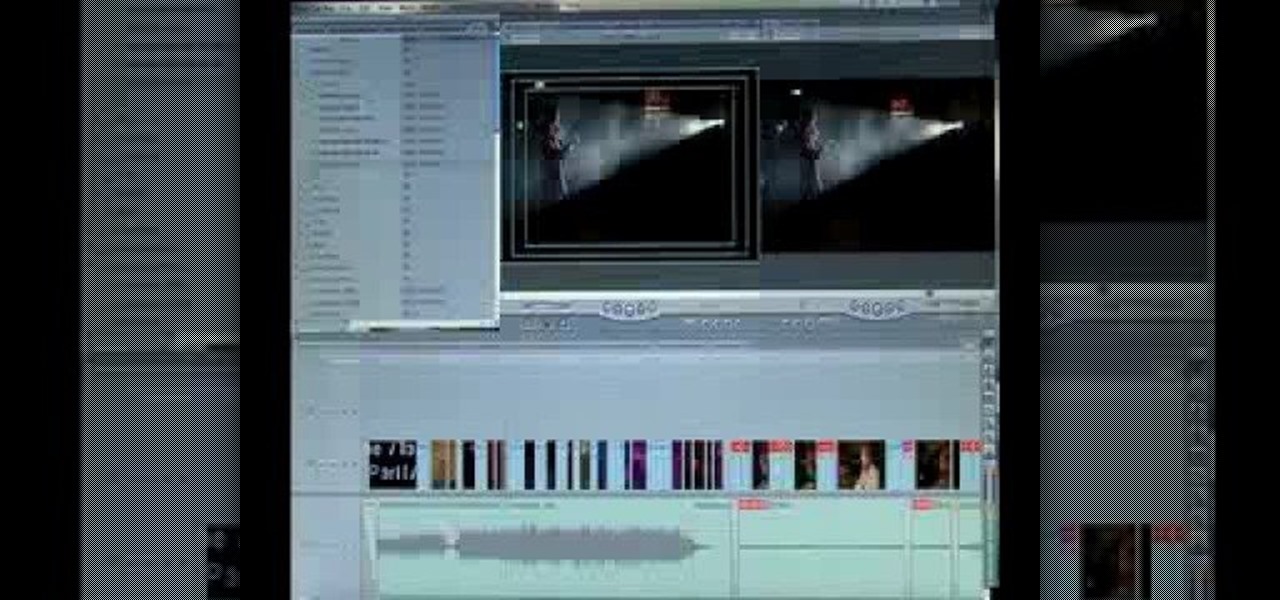
Forgot to take a few production stills on set? No problem, work with what you have... the actual video footage. See how to get photos from video with iMovie or Final Cut Pro 6.

This video helps people make hills and elevation on their farm! Here is my spreadsheet, which might come in handy:

This easy-to-follow video tutorial walks you through steps of converting old VHS tapes to DVD. Roxio Easy VHS to DVD is a combination of software and hardware that allows you to easily and quickly digitize old analog recordings. You simply attach the included hardware to a free USB 2.0 port on your computer, then capture from virtually any analog video or audio source.

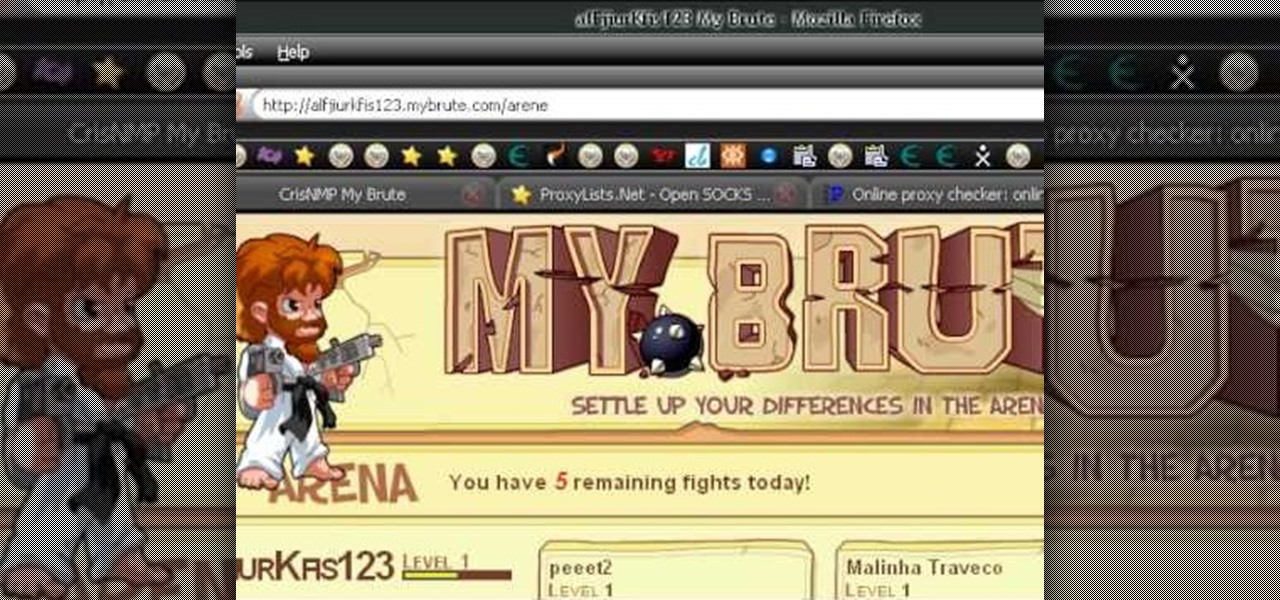
Watch to learn how to get infinite EXP with proxies in MyBrute (04/23/09). It shows how to get exp from pupils you make by passing the current two checks (Flash SOL files and IP check).

See how to make some cool gift / party favor bags for any occasion. They are made with envelopes. You can make them from nearly any size and type. The ones in the video are made with some surplus greeting card envelopes. Sometimes you can purchase "leftovers" from an office supply or drug store (any store that sells greeting cards). "Left-overs" mean that the cards get damaged or lost but the envelope is left. Just ask the manager if you can purchase them.

Wouldn't your TI calculator be way cooler with some sweet programs like Nintendo or Tetris? This is a short tutorial on extracting the files from a ZIP archive, and transferring them to your calculator.

He's not exactly demanding sexual favors, but his flirting is getting really gross. What's a girl who likes her job to do? You will need diplomacy and documentation. Assess his behavior. Now, don’t be offended, but we have to ask: Is he really coming on to you, or is he just a sociable, flirtatious kind of guy? If it’s the latter, just ignore it. Do your part to keep the relationship professional. Don't chat about how your last two boyfriends cheated on you and then expect him to know that di...

Adam from Chemical Reaction wants to show you a little movie magic. This video tutorial will show you how to make an Assassin's Creed hidden blade prop for your homemade film. If you're a fan of the Assassin's Creed video game, then you can't not make this hidden blade. This is a great prop for anybody wanting to recreate it for a fan film. It's cheap and quite easy and works pretty well.

Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...

Need to shoot a film for class and realized you don't have a Fisher Dolly and your cinematographer's hands are a little to shaky for what you would consider good filmmaking? Well, this video tutorial will show you how to make your very own steadycam. Check out how a nautilus design transforms into a more suitable steadycam; the gimbal is the key, and gimbals are very hard to find, especially the right one.

TorrentFlux is an web-based system for managing bit torrent file transfers. It is an open source package (GPL) and developed for Linux, Unix & BSD platforms on the ubiquitous LAMP stack. In video tutorial, you'll learn how to set up TorrentFlux and how to share your downloaded content via a Samba share to an Xbox running XBMC. For detailed, step-by-step instructions, or to get started watching your own torrented media from the comfort of your couch, take a look.

Boris Title Toolkit gives Adobe After Effects users advanced titling capabilities for maximum quality, speed, and creativity. Using Title Toolkit, graphic artists can import ASCII or RTF files for fast, easy credit rolls, take advantage of rich text style options such as bevel borders, gradient fills, simulated extrusion, and embossing, and save or apply custom or preset text styles, gradients, and colors, all of which can be applied on a per character basis.

This tutorial is on GIMP Basics. GIMP is a free Photoshop substitute available for all platforms and pre-loaded in Linux operating systems. The tutorial covers the scale, crop, cut with transparency, flip, and rotate commands of GIMP. Part 2 covers saving and file size reduction in GIMP.

This software tutorial shows how to make an animated gif file that changes the color of your eyes or of anything you want in Photoshop. Animated gifs are perfect for profile pictures on sites like Myspace and forum sites. So check out this Photoshop tutorial and learn how to make your own cool animated gifs.

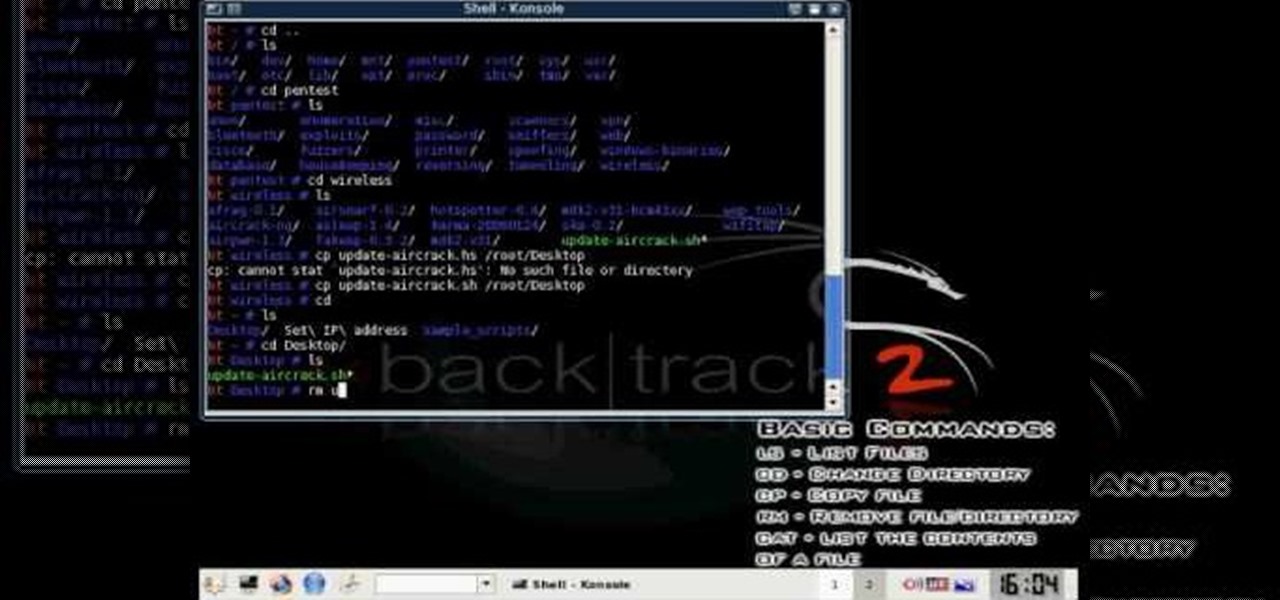
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

When you need a file on your Mac as soon as possible, you usually have to get your MacBook or hop on your iMac, Mac mini, Mac Pro, or Mac Studio. But that's too much work if you're in bed, lying on the couch, or outside in the fresh air. Why even bother when you can access that file directly on your iPhone or iPad — without moving an inch?

Not all websites are created equal, and that's why Safari doesn't apply Dark Mode to each webpage you visit during your iPhone's system-wide dark appearance. But in Safari's latest update, Apple gives its web browser more power to automatically apply Dark Mode to specific website content without having to use extensions like Noir.

Apple's Reminders app has come a long way. In the past, if you really wanted to keep track of your important daily, weekly, and monthly tasks, you needed to install a specialty third-party app to make it work. While those apps still offer valuable features, Reminders can get the job done for many iPhone users now. With iOS 14.5, Apple only sweetens the deal.

If you use iCloud Photos, Apple's iCloud link feature is meant to make sharing multiple photos and videos faster and easier, but it's not as great as you might think. Luckily, there's a way to stop your iPhone from creating them automatically, as long as you're running iOS 13 or later.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.