
How To: Pronounce the word "fathomable" in English
Today's word is "fathomable". This is an adjective which means knowable or comprehensible.


Today's word is "fathomable". This is an adjective which means knowable or comprehensible.

JohnK (creator of Ren and Stimpy) explains cartoon contstruction and how to learn from other people's art.
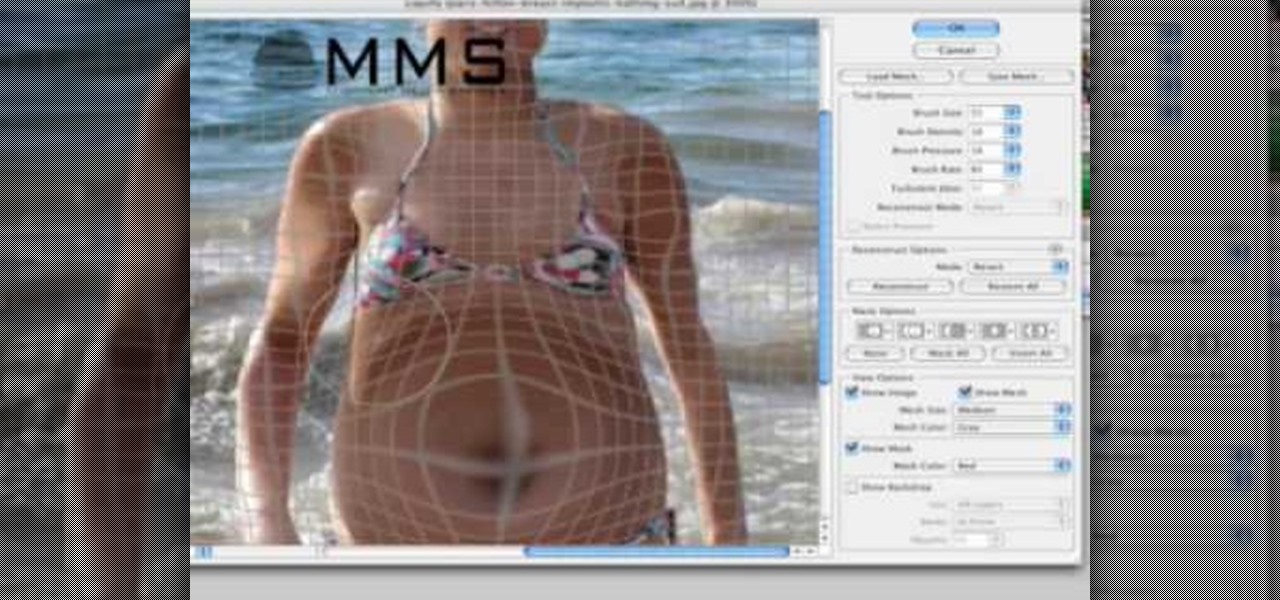
Well, usually people are looking to go from fat to thin, but sometimes it's fun to see what a person would look like if they were on a full Twinkie diet. Well, this tutorial shows how to use the liquify tool in Adobe Photoshop to add weight to someone to make them look pudgey, overyweight, fat or even downright obese. The tool is easy to use and the video shows clearly how to turn that beach babe into a Jenny Craig "before" photo! Check it out and YOU can make people look fat in photos.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...
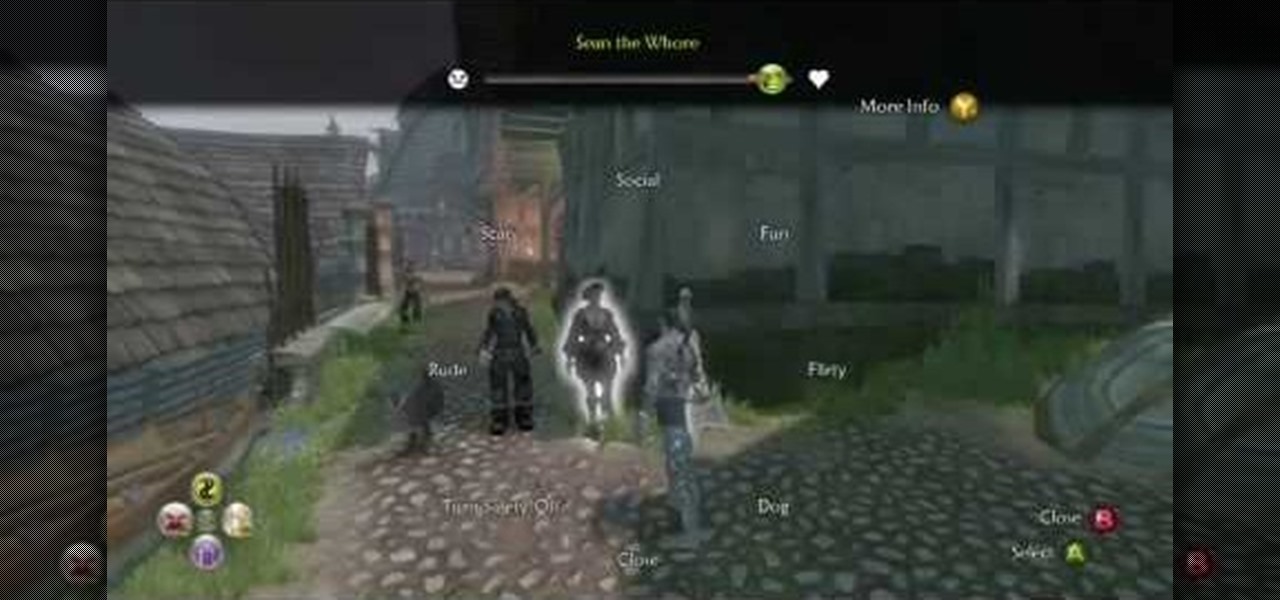
In this video, we learn how to get the Menace to Society achievement in Fable II. This requires you to commit an act of public indecency. So, start off the level completely naked and approach people in public places. Then, go purchase The Perv's Handbook from the worker and head out of the book store. Now, you will go down to items and read this to learn it. From here, you will continue to run around and find some whores that don't like being yelled at. Then, dance around showing people our n...

Combination locks are a major part of life for people High School, the Armed Services, and enough other places to make this video very useful to a lot of people. It will show you how to open any twisting combination lock (like a Masterlock) with using math or any other sophisticated skills or tools. All you need is a sharp knife and your fingers. Now you won't have to wonder whether Person X has your picture up in their locker or not anymore.

Breaking a finger is painful, and the sight of broken fingers pointing in unnatural directions from the hand is enough to make many people ill. This video will show you how to terrify such people by pretending to first shrink your finger, then kick it up a notch by snapping off the finger, tossing it in the air, and eating it with a crunch. All you need to do this trick are some nuts, manual dexterity, and a showman's charisma. It's magic!
Facebook is an internet phenomenon which is quickly gaining popularity. For those who do not yet have a Facebook, this video will show you the basics of how to meet people and to connect with people online as well as how to set up your profile on the site. After creating an account using your email address and setting up your password, log on to the website. Set up your profile by clicking on the tab labeled "info" and entering information which you would like to share about yourself. You can...

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

Chess is a serious game. People take chess so seriously that it is almost like a sport. All around the world people compete in matches and championships with this strategic game.
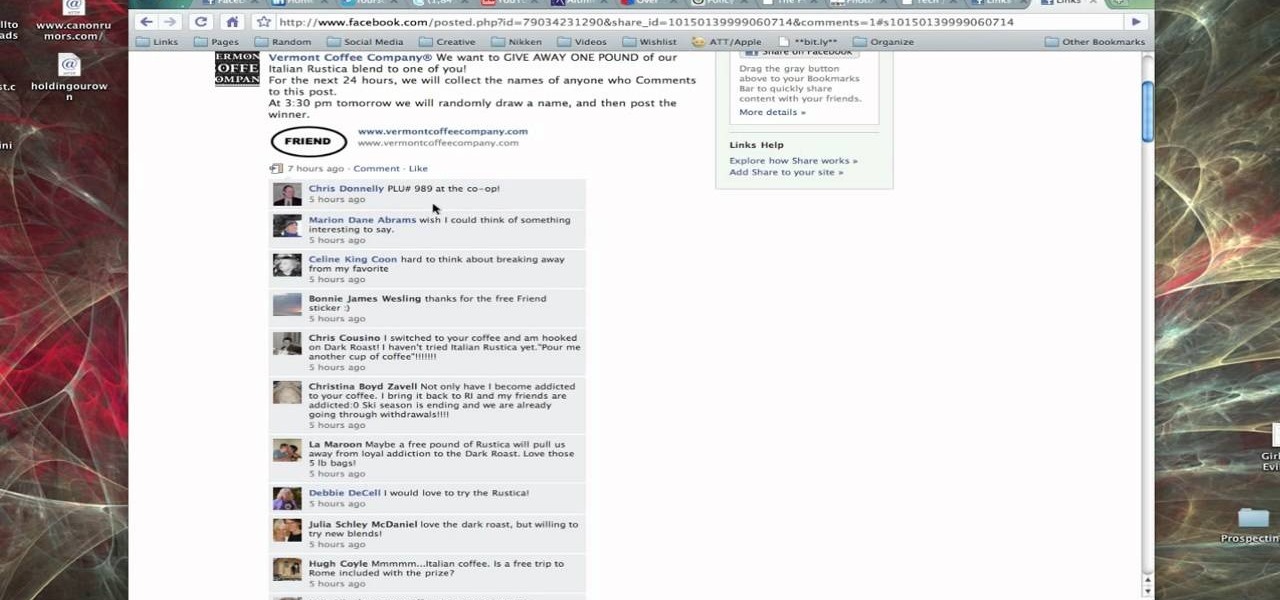
In this tutorial, Brian from TruTricks shows us an example of what Facebook can do to promote your business! One of the best ways to do this is to do micro giveaways on your Facebook. You don't have to give away something big, just something small that gives people incentive to post on your page and become a fan of your business! You will be able to see what people are posting on the page as well as everyone that is entered in your contest. This giveaway has given all the fans reason to parti...
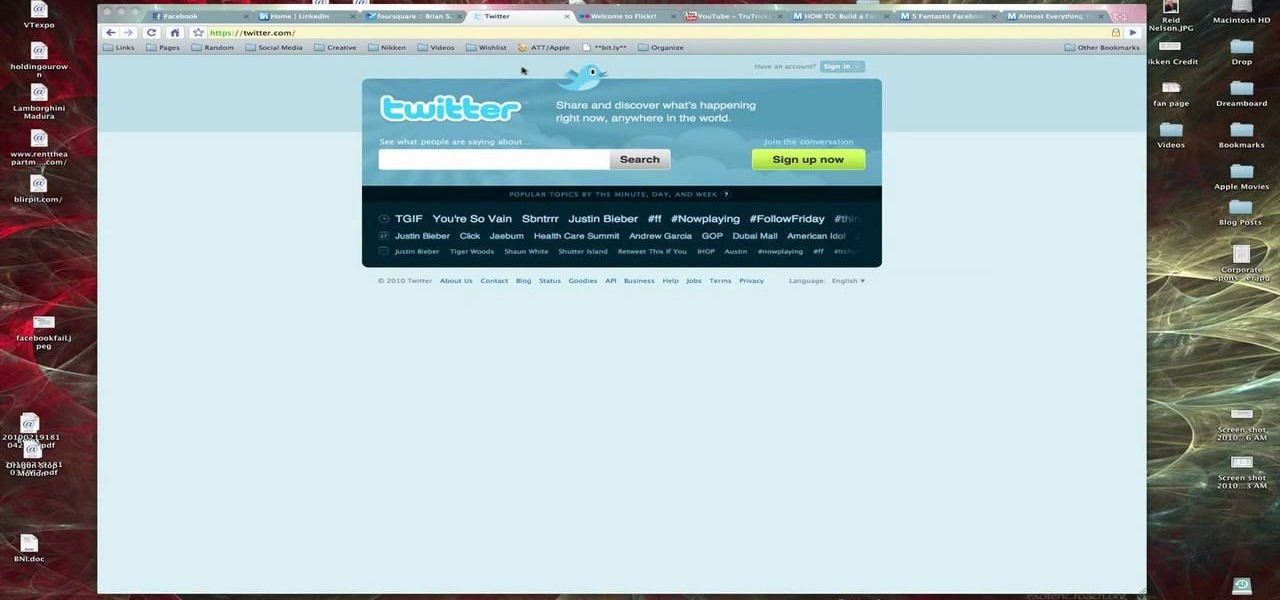
In this video, Brian from Trutricks shows us how to create a new Twitter account. First, go to Twitter and click on the "sign up now" button. You will now be brought to a new page where you can choose your user name and enter your email, password and full name into the information boxes. Once finished, click "create account". After this, you will be able to follow people you want as well as have other people follow you. Once you are ready to tweet you can type whatever is on your mind in 140 ...

Sick of living life on the sidelines? Ready to make more friends? This tutorial will give you a few key tips to help you achieve popularity.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

Delete Your Cookies and Browsing history.

Take a look at the first place winner's tutorial on making a dress out of old tees for the Generation-t tee recon contest! Follow along with the steps in this fashion design video and make your very own quick and easy dress.

People are very opinionated about what version of Microsoft they like. Some people love the easy-to-use nature of classic Windows 2000 and stick with that, whereas others love the upgraded, super sleek Windows Vista version which has its faults but at least looks amazing.

There's probably a reason that laser pointers are banned from most schools: They're just to fun to put down! Whether you're using them as a pointer, to distract your classmates, or to very wickedly point them in people's eyes, they are toys that are quite addicting.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Apple Music's name reveals a lot about itself — it's made by Apple, and it has a lot of music. 40 million songs, in fact, if the iPhone-maker is to be believed. With that many songs, you may find a gem before any of your friends or family do. How can you share that song with them?

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Augmented reality is quickly becoming a popular tool for marketing use cases, as demonstrated by new projects serving the automotive, entertainment, and tourism industries this past week.

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

There have been seven more people sickened from four states since the I.M. SoyNut Butter E. coli outbreak was announced earlier this month. The Centers for Disease Control and Prevention and Washington Department of Health have confirmed the I.M. Healthy SoyNut Butter was the cause of the outbreak in an update today.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.
What can be said about Spotify that most of us don't already know? It's the most popular digital music streaming service out there, giving you access to millions of songs on your computer. However, the mobile service was once an exclusive feature for paid subscribers. Not anymore, suckers.

Numerous studies have shown that people are over-confident in their own abilities. Most people, for example, think that they are better drivers than average.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Share happiness with thoughtful kindness and song from HappySlips.
You've managed to get your Motorola Droid X rooted, so now what? What's one of the first things you could install on your Droid X? What's the most valuable items you need on your cell phone? Everybody knows the answer… wireless tether, a way to suck the internet from your Droid X to your laptop or home computer. Well, this video tutorial will show you how to get the free Wi-Fi tether mobile hotspot app, called Wireless Tether, on your Droid X from Verizon Wireless. You don't have to pay tons ...

There are many tips and tricks on the best way to use your Gmail. In order to use the tips provided you will need to have the newest version of Firefox or Google Chrome for them to work. There are three tips that can help you maximize your Gmail funtionalities and help you save time.
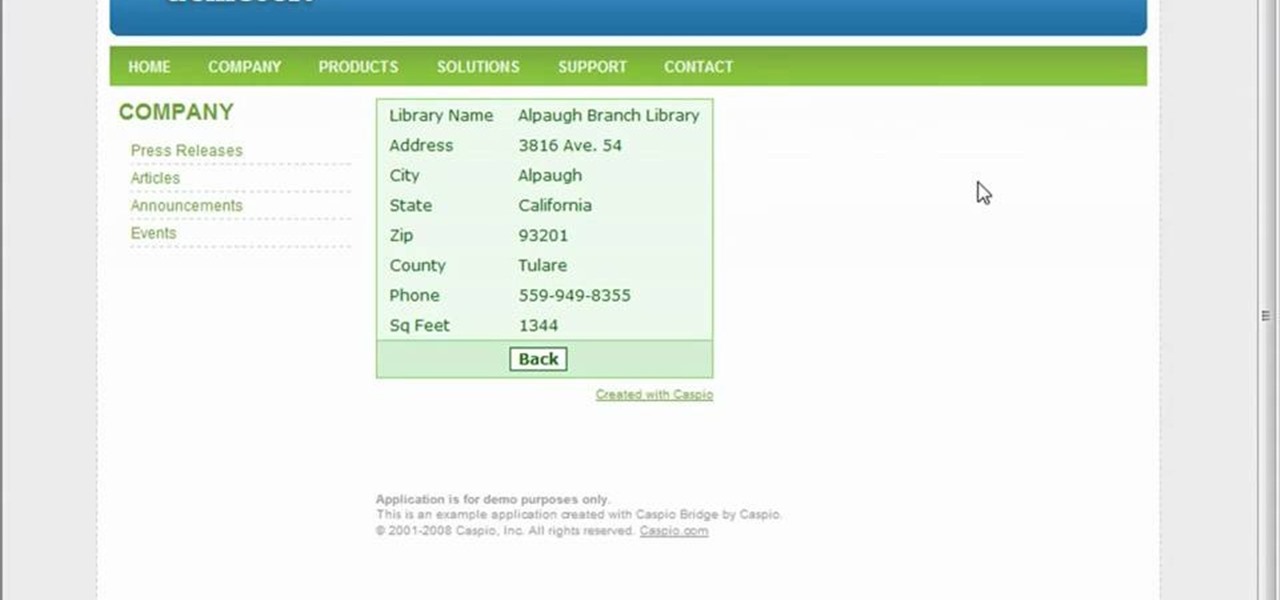
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...
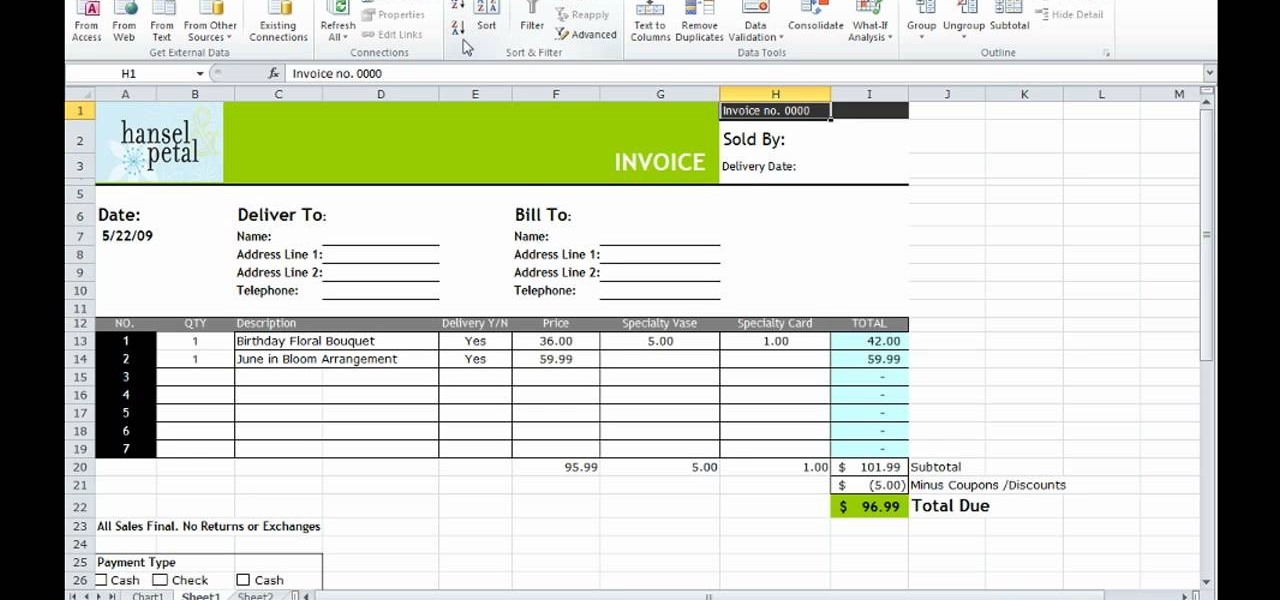
This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

You love your iPhone and you can't live without it, but it's lacked the basic ability to cut, copy, and paste across multiple apps. With Apple's OS 3.0 upgrade, you can do it all with just a few taps. Watch this Howcast guide to learn how to cut, copy, and paste on your iPhone.
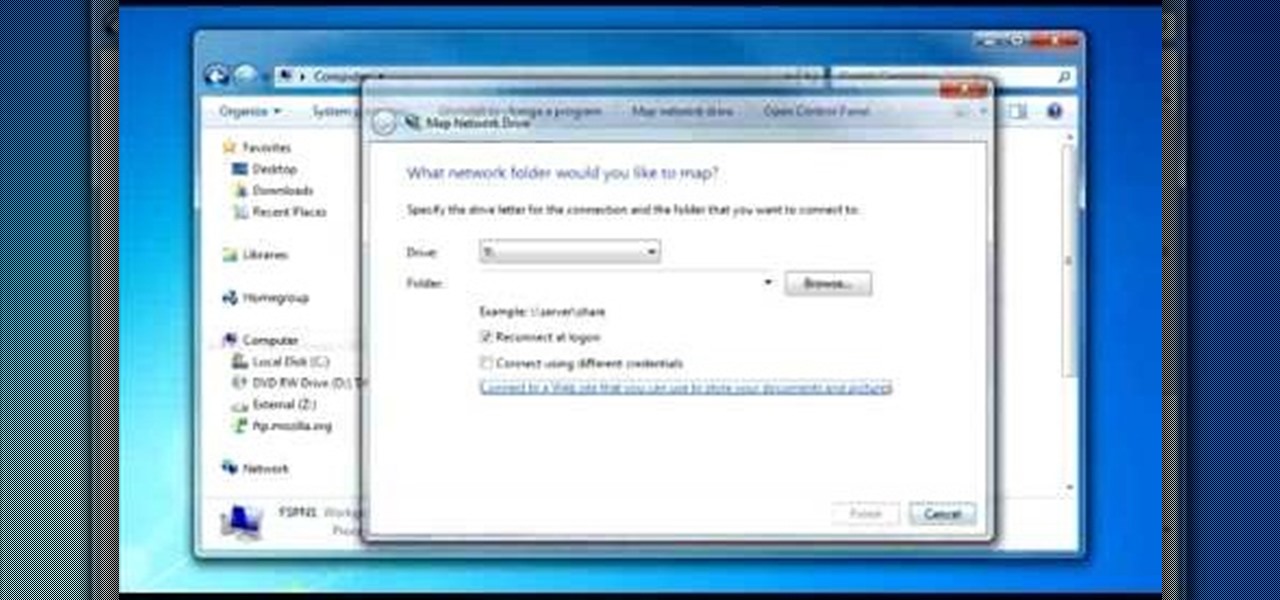
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

The iPod kids shows viewers how to covert movie files that are already on your computer into a format that will work with your iPhone or iPod Touch (2nd generation).