
How To: Improve your mental health
Stressed, sad, or just feeling blah? There are lots of ways to improve your mental health. Watch this video to learn how to get out of a slump, and improve your mental health.


Stressed, sad, or just feeling blah? There are lots of ways to improve your mental health. Watch this video to learn how to get out of a slump, and improve your mental health.

Studying to be a nurse? Then follow along with this how-to video to learn how to start an IV on a live person. IVs are an important part of a nurse's everyday routine. When inserting an IV needle, be sure to enter at a 30 degree angle. The nursing students in this video, Moe and Drew, insert the needle at 10 to 20 degrees.

In this three-part keyboard tutorial, you'll learn how to play John Legend's "Ordinary People" on the piano. While this tutorial is best suited for intermediate or advanced piano players, players of all skill levels can play along. Watch this lesson to get started playing "Ordinary People" on your own piano or keyboard!
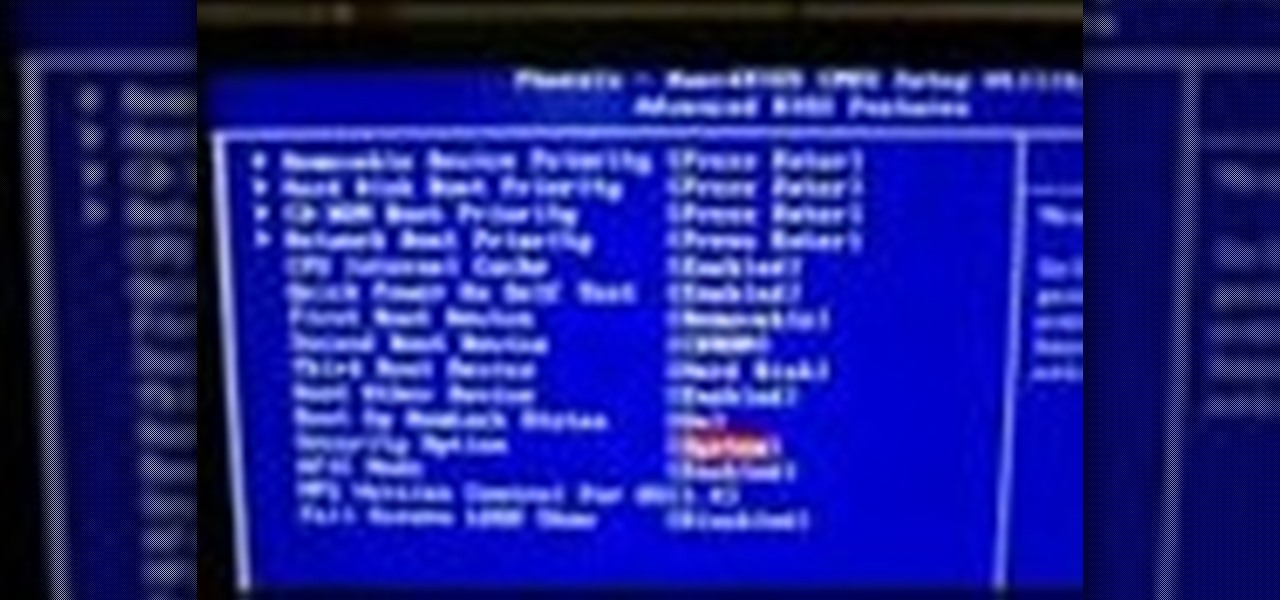
What you need to do is press a certain button when your computer boots (it should say something like press this key to enter setup). Press the specified key and inside the bios find the option that allows you to set a password. Once you create a password then you have to set it so the computer requires the password on boot. Please rate and comment this video.

Shogi is Japanese chess. It is a unique game of strategy. Captured pieces can be replayed and most pieces can be promoted when entering the opponent's territory.
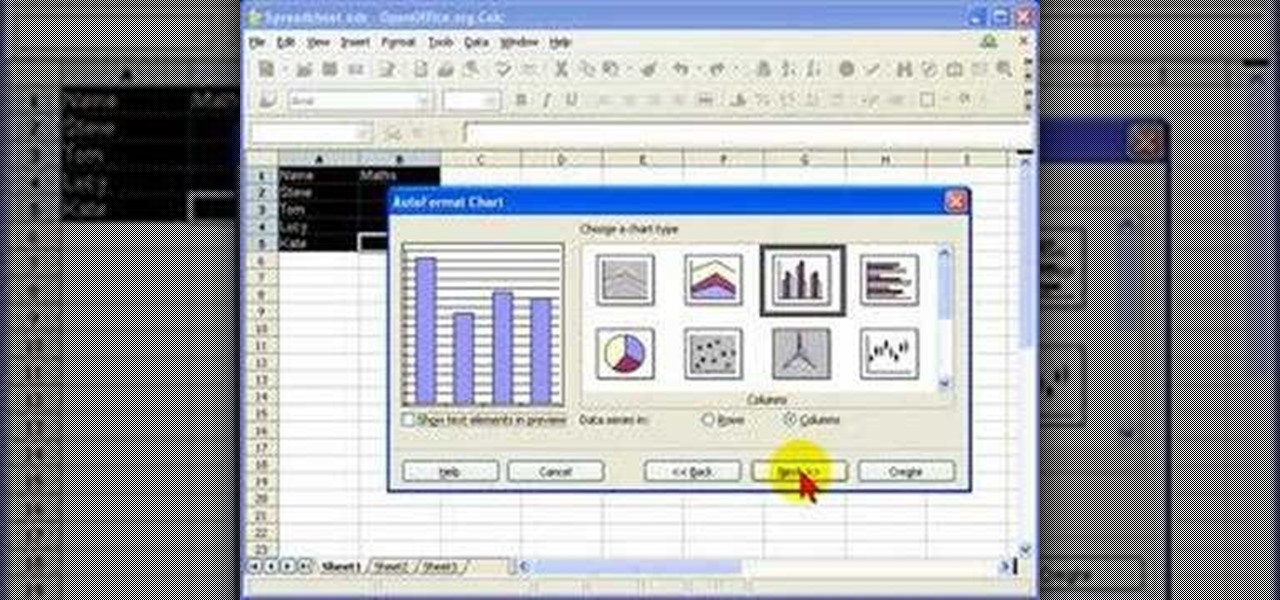
In this screencast tutorial, Steve shows you how to quickly and simply create a bar chart, from the data you have entered into your worksheet in Open Office Calc. If you're looking for a simple and clear way to represent your statistical data, then a simple bar chart is an option you should look at using. So check out this tutorial and start making OpenOffice Calc bar charts today.

Want to crack Ninja Gaiden Sigma for the PS3? Let a hot chick help you! In the regular version of this game, you can unlock the five additional missions that come on the collector's edition. After you've solved the game, go to the mission mode screen and enter: Up, Down, Left, Down, Right, Up, Square.

Get closer to God with a hot chick.

Try some gender bending in Elder Scrolls IV (4): Oblivion and flip the sex of your character. To do so, enter the code ~sexchange.
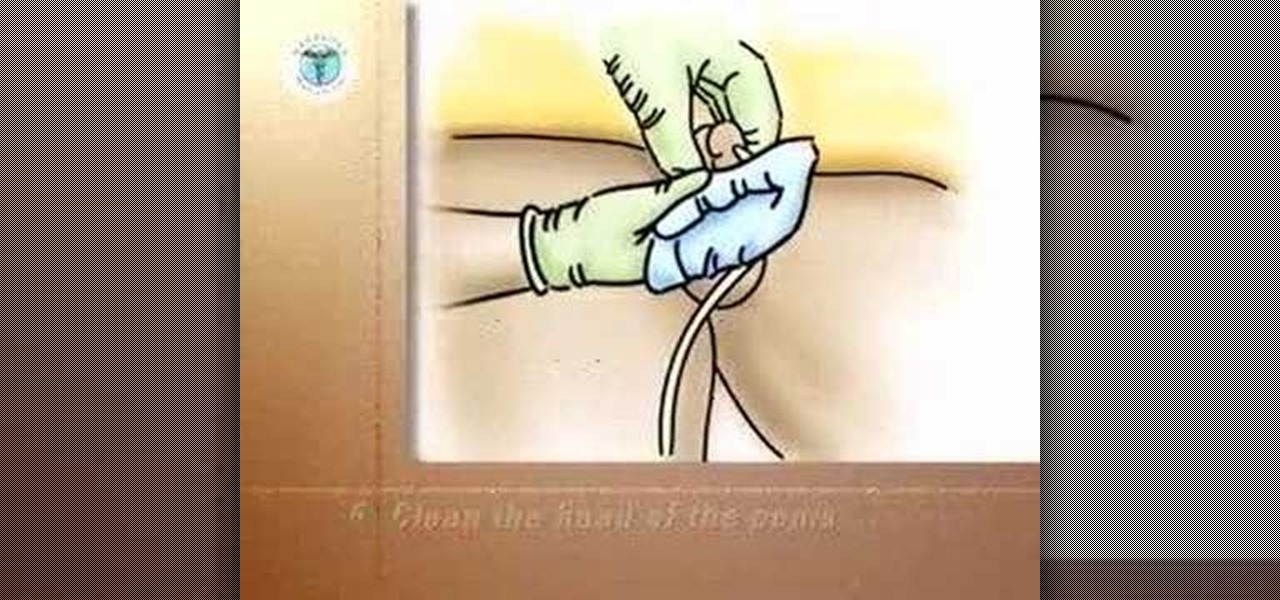
Once each day, or according to your doctor's instructions, you will need to clean the urethral meatus - the opening where the catheter enters the body. This video shows you how to give a proper male perineal wash.

This video shows you step by step how to choose the aperture to produce drastically different effects. The is the opening by which light enters your camera.

'Loose Change' is cool secondary quest in Dragon Age 2 that varies depending on whether you chose to be a smuggler or a mercenary when you enter Kirkwall. This video will walk you thorough the mercenary version of the quest, allowing you to, in fact, tie up your loose ends.
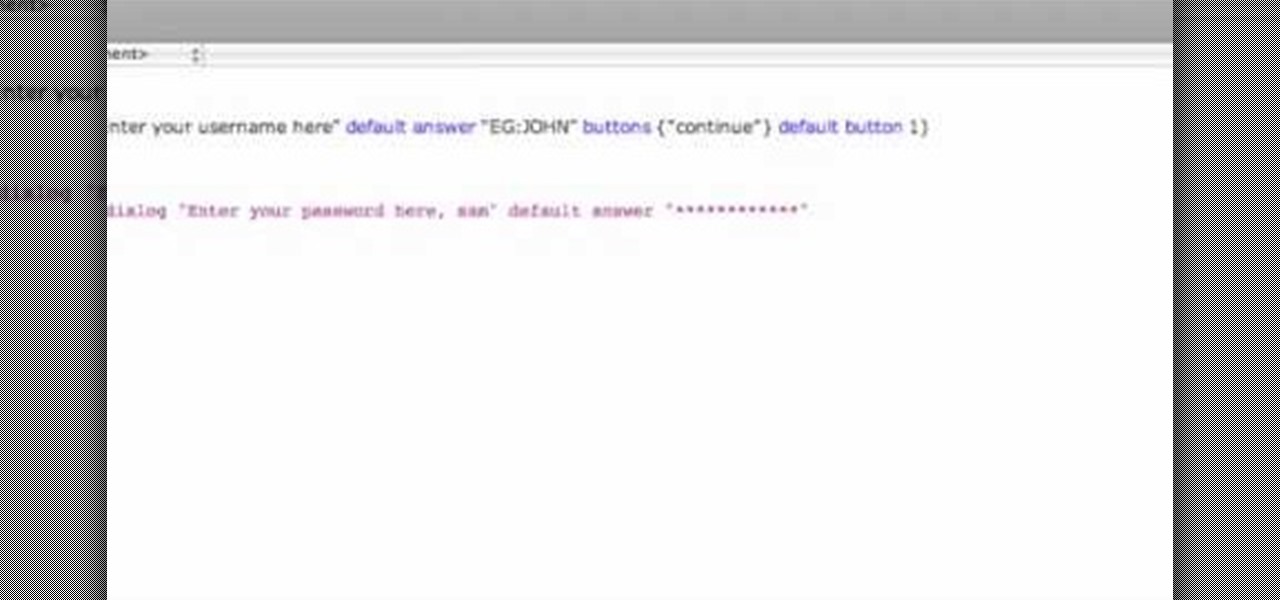
This video shows how to program a password and user protected application in AppleScript.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Halloween may be finished, but the augmented reality chills are not over yet for some people. Arachnophobes are bravely facing their fears by cozying up to augmented reality spiders for a university study.

Musical theater enthusiasts are about to enter a whole new world of melodic storytelling via augmented reality.

Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.
Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.
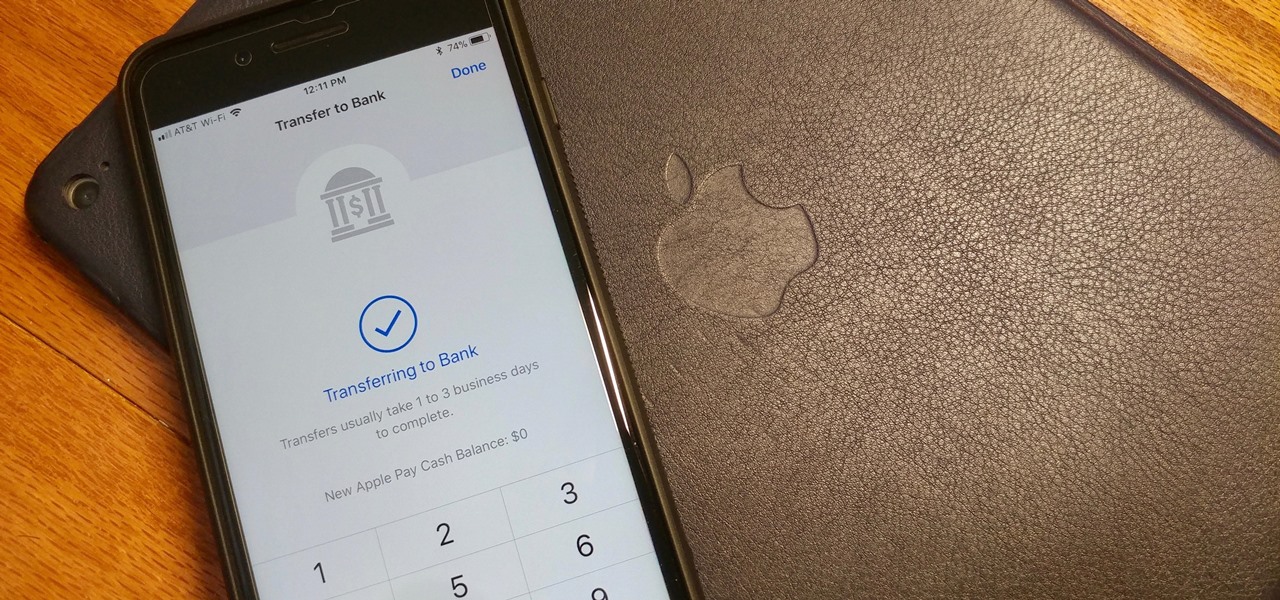
Let's say you receive $10 from a friend through Apple Pay Cash via an iMessage. You could spend that money in the App Store or at any retailer that supports Apple Pay using your Apple Pay Cash card. If you'd rather save it or use it for bills, it's easy to transfer that money to your bank account in iOS 11.2.
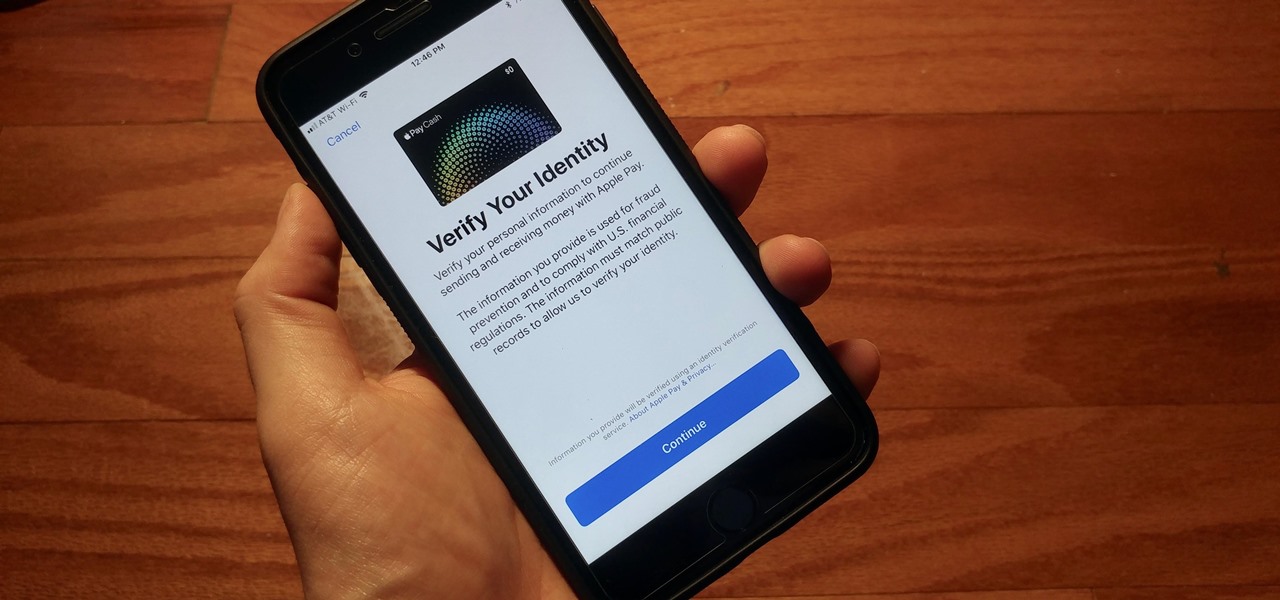
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

Considered by many (perhaps unfairly) to be a very public failure, Google Glass can add another plot point to its comeback story, this time as a tool to teach social skills to children and adults with autism.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!
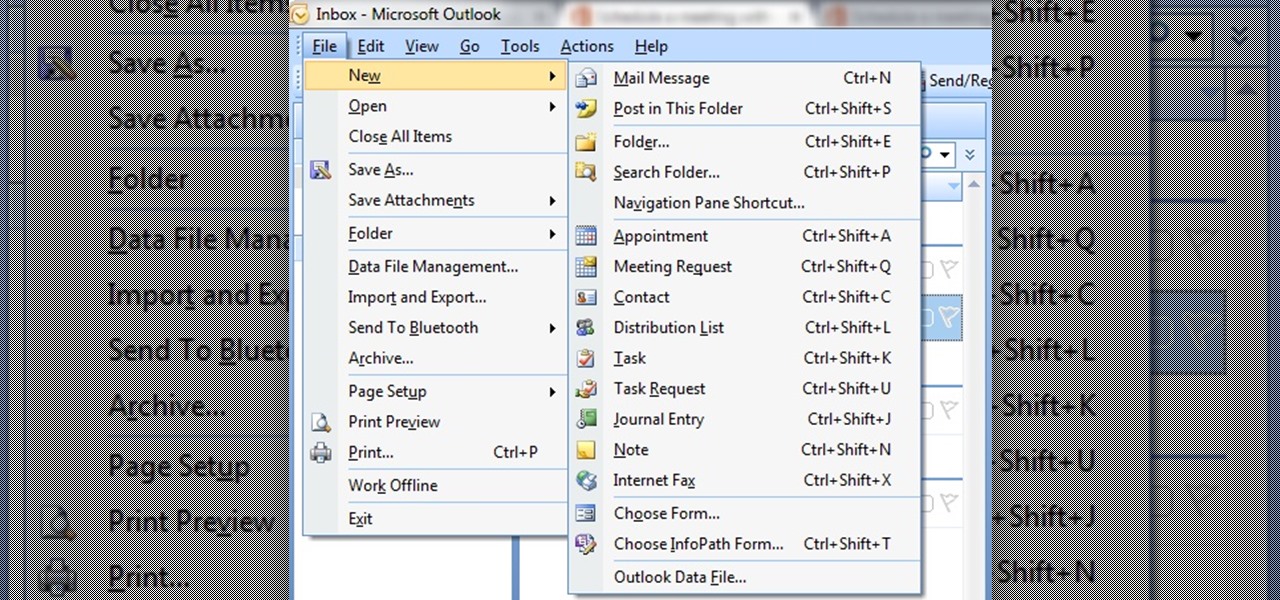
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.
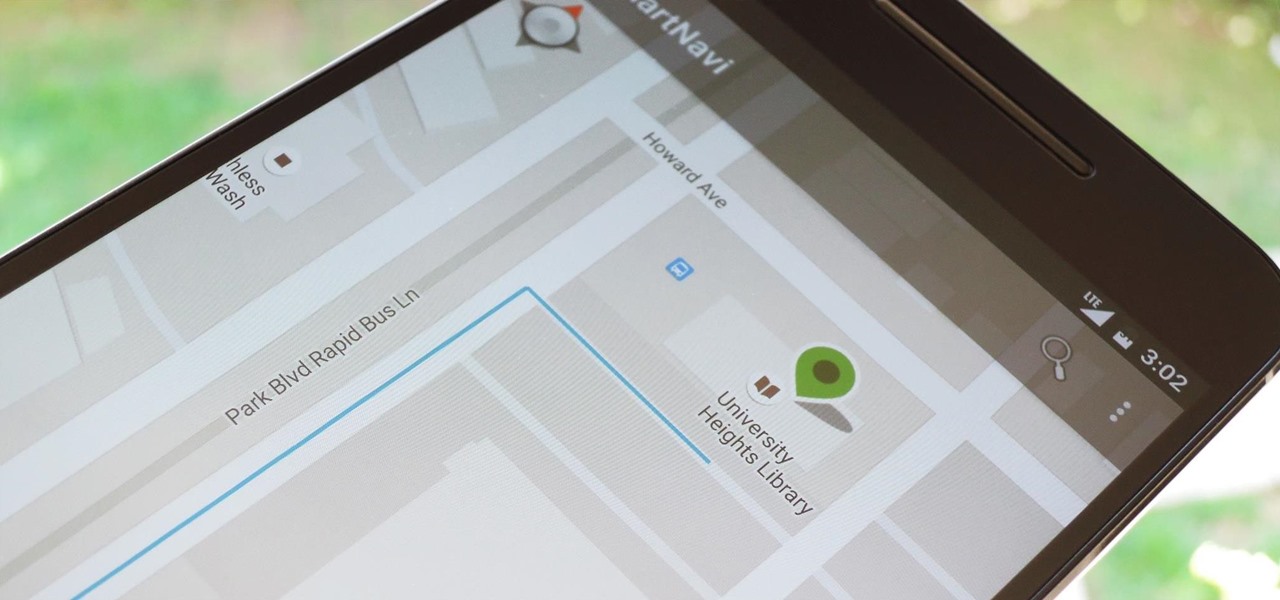
Modern smartphones are packed to the brim with low-power sensors like accelerometers and gyroscopes, which means they're capable of precisely measuring almost any type of movement. So why is it that when you just want to get walking directions somewhere, your device still uses its battery-sucking GPS connection to track your progress?

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

One of the most exciting things about a major iOS update is the discovery of new glitches, or even just finding ways to replicated the old ones that we've come to love so much. One of these is the glitch that lets you nest folders within folders on the home screen, which can save some major screen real estate. While this glitch was available in both iOS 7 and iOS 8, the process is slightly different in iOS 9, but you still have a couple options to choose from.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Google recently rolled out a new Smart Lock option labeled "On-body detection" for Android Lollipop via an update to Google Play Services. As I'm sure you can gather from the name, this new function keeps your phone or tablet unlocked using the built-in accelerometer to determine whether or not your device is being carried on your body, allowing you to set it down and walk away carefree knowing that's it's locked again.
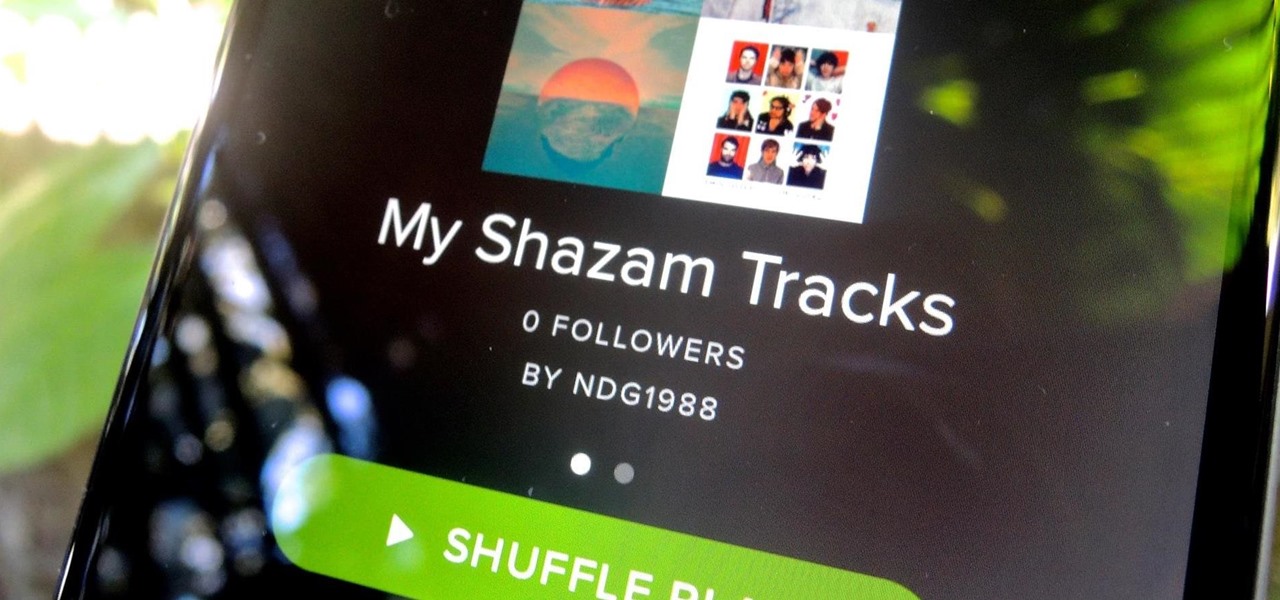
We recently showed you how to recover your Shazam history from Siri, which is a lot less intuitive than finding the songs you've tagged directly in the Shazam app. But with a subscription to Rdio or Spotify, there's no need to even locate your history. You can Shazam songs and have them automatically added to a newly created playlist titled "My Shazam Tracks."
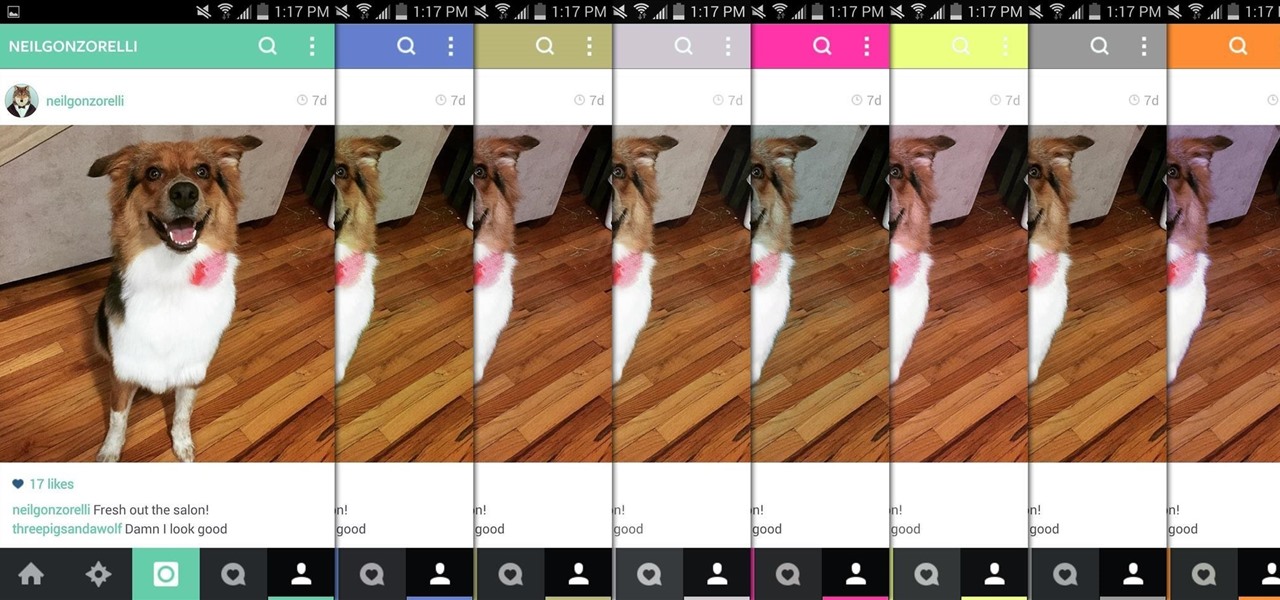
There aren't many complaints I can think of when it comes to the Instagram interface, and finding one would just be nitpicking. But like with most things in life, if given the opportunity, why not take advantage? "When in Rome," as they say.

Before phones became mobile-gaming, music-playing, app-downloading devices, they were used simply to make convenient, cordless phone calls. There's so much on phones these days that a passcode is needed to keep everything secure, and making calls is now more complicated.

Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.