Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

One of the major criticisms of virtual reality, and much modern technology in general, is the antisocial nature it creates. But vTime wants to overcome the isolating nature of VR headsets with a virtual hangout space for you and your friends.

Walking, talking, life-size holograms aren't just for staging Hatsune Miku concerts and reviving Tupac, Michael Jackson, and other fallen stars.

A motion-based lock screen app called GestureLock was among the winner's at 2106's Android Experiments I/O Challenge, and it lets you set a specific motion (gesture) that you use to gain access to your locked phone.

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

On September 1st, 2015, Google made headlines by introducing their new logo. It may not seem like huge news to some, but as I write this, there have been 2,167,914,729 searches on Google so far today. So there's a large amount of people who see their logo when browsing the Web.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Dating can sometimes be a cruel and embarrassing game. You could be having a great time with someone, only for the situation to turn awkward and uncomfortable when a little bit of information is released, especially when that information is your use of medicinal or recreational marijuana.

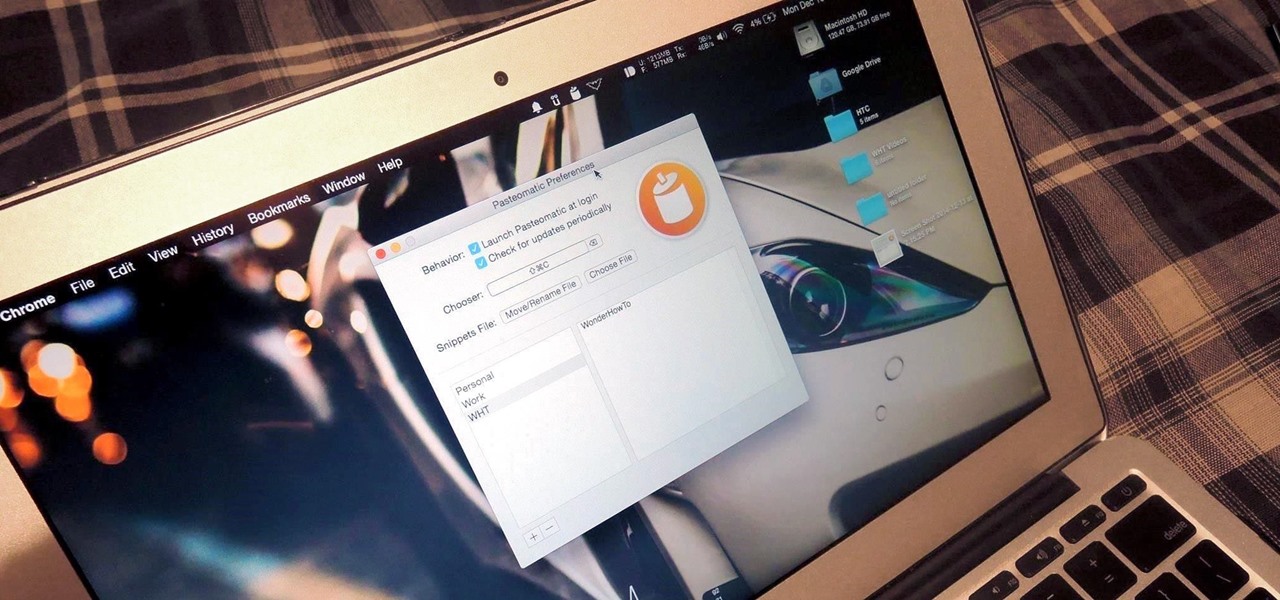
Your Mac's clipboard is great when you are just copying and pasting a phone number or address, but sometimes you end up having to re-copy the same thing over and over every day. To make those phrases a lot more easily accessible, the people over at Tiny Robot Software have released Pasteomatic. With this app, you will be able to use a hotkey to bring up a collection of your most commonly used text snippets and paste them into any text field or document.

At the end of an all-day affair with friends or family, I'll unwind and go through all the pictures I took that day as a sort of recap. All too often, though, I'll come across a few that are almost perfect, except I didn't quite position my phone well enough, leaving someone's face cutoff or too much space to one side of the image. It's a fail of a basic and crucial tenet of photography—framing.

With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"

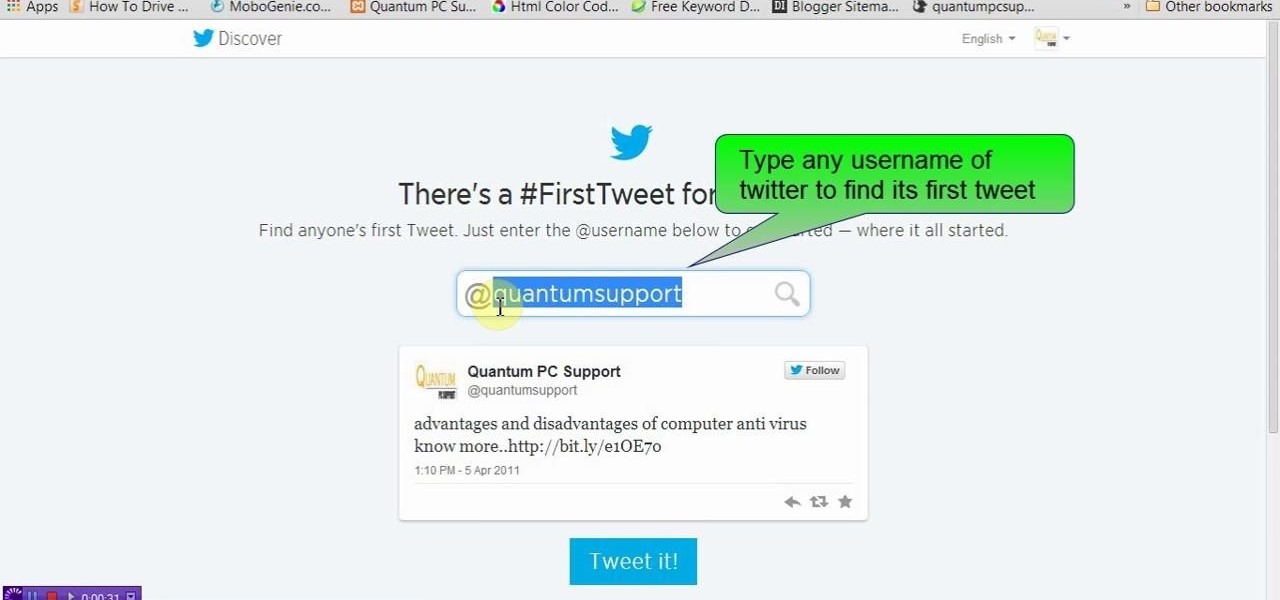
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

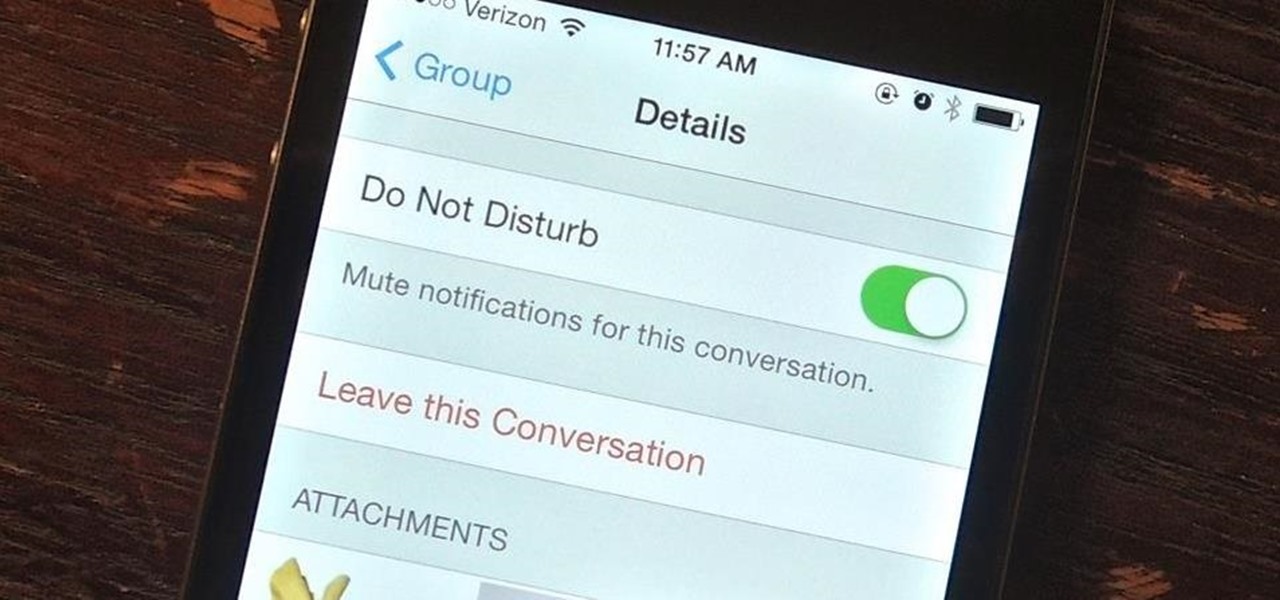
Group messages make for some hilarious conversations with your friends, and are also a great way to update multiple people without sending individual text messages. But as awesome as they can be, they can also be as equally annoying.

They say that behind every joke is a half-truth. If that adage itself contains a grain of verity, the Daily Show's satirical Glass piece should raise a few eyebrows amongst the Glass Explorer community.

April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television.

I'm sorry your mom hates you now, but it's pretty hard to forgive someone who forgets to say "Happy Mother's Day." Your poor ole ma could've spent anywhere from 10 to 20 hours popping you out, so the least you could do is set aside two minutes every year to say thanks. If you live to be 90 years old, that's only 3 hours over your entire lifetime!

Having your phone ring loudly in a quiet environment could be potentially embarrassing for you, but also quite annoying for everyone else that didn't forget to put their smartphone on silent. Whether it's in class, at work during a meeting, at the library, or a movie screening—you can bet that someone's phone is going to ring loudly, pissing some people off. You don't really want to be that douchebag that interrupts a movie or the middle of a lecture with their annoying ringtone just because ...

Antique car collecting and restoration is a very popular hobby practiced by many around the world. A quick drive through my town turns up with a handful of classic cars parked in their respective driveways, some in pristine condition, and others not-so-much. While some people end up eventually fixing up their classics, many also do not. Some cars end up rotting away, left to be either salvaged or sold off in pieces—mostly due to time consumption and excessive costs.

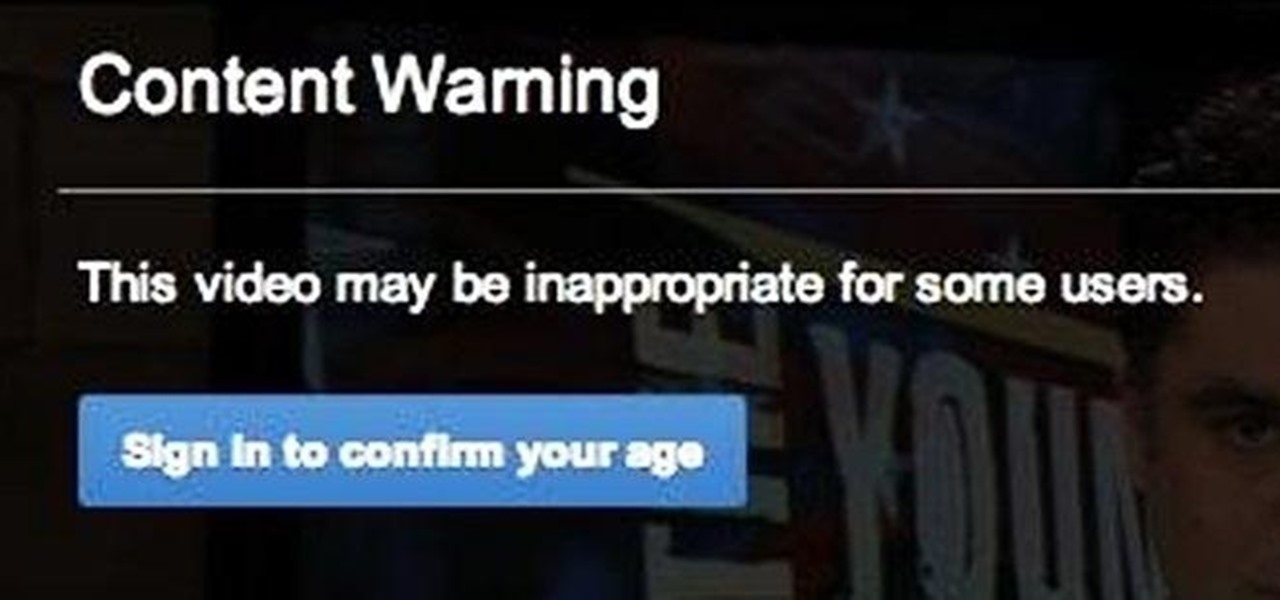
YouTube is the first place I go to watch funny videos online—me and about a billion other people. But one thing that always annoys me is having to sign in time after time to view age-restricted videos.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error reporter. On its own, the bug doesn't really pose a threat—just don't type it.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

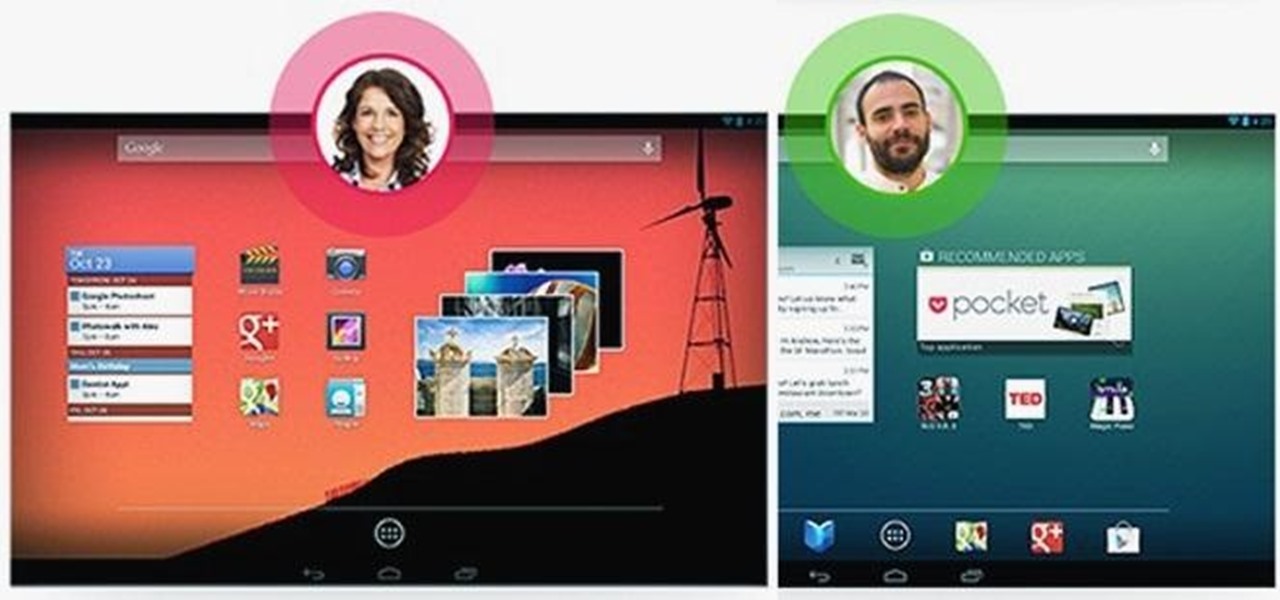
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

Summer is over and autumn is here. Serotonin levels are dropping and people don't have the motivation to be outside as much anymore. So we play Minecraft instead. But walking is cumbersome, so we want minecarts. Remembering to carry one in your inventory or placing one on the tracks might be a bit much to ask for, and don't even get me started on bothering to press a button to make it go.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Over 2 million people are anxiously awaiting the arrival of their new iPhone 5, which has caused a few shipping problems, to say the least. There has been a considerable amount of confusion about when, exactly, the iPhone is going to ship, depending on where it was bought and how it's being delivered.

One of the most played-up features of Windows 8 is that it's so much faster than previous versions. So fast, in fact, that Microsoft had to change the way that users access the BIOS because 200 milliseconds just isn't enough time to hit the right key. It may take some getting used to, but it's probably a welcome change for most people, considering that the "right" key is different depending on what type of computer you're running the OS on.

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

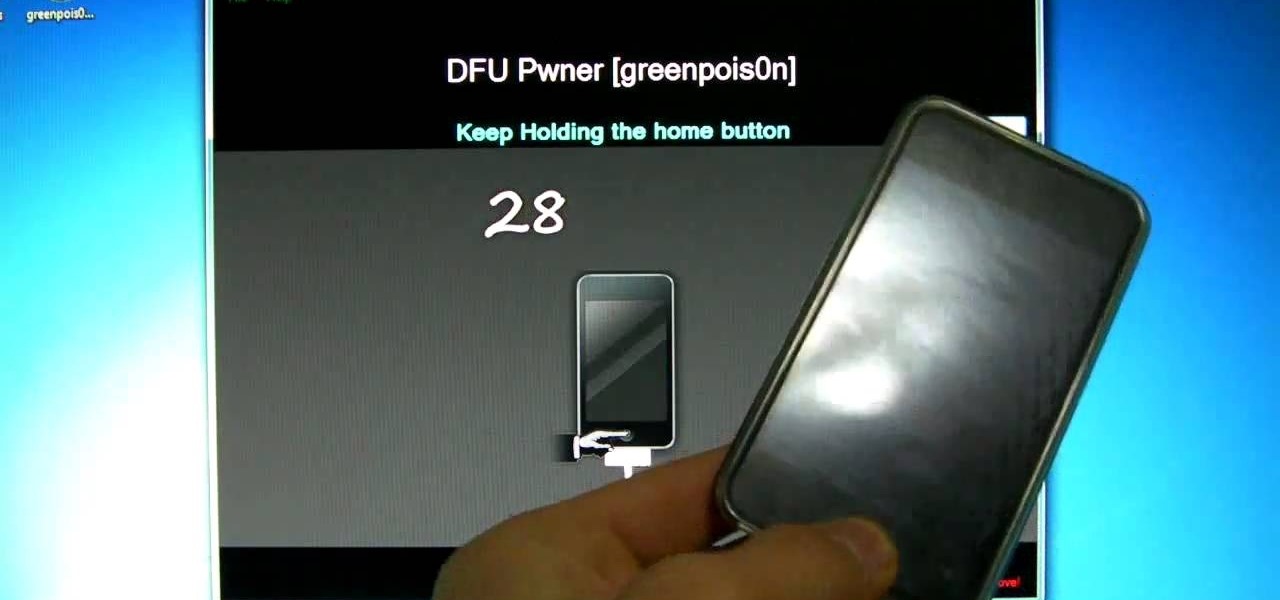
If you own an Apple iOS device (iPhone, iPod Touch, iPad) then you probably have the 4.3 firmware update by now. It's got some cool improvements, but as usual necessitates a new jailbreak. Enter Sn0wbreeze 2.3b1, the beta version of the jailbreak for the new iOS. It's in beta, so it's not perfectly stable, but this video will show you how to use it. You can see a written version of the guide and the necessary download links here.

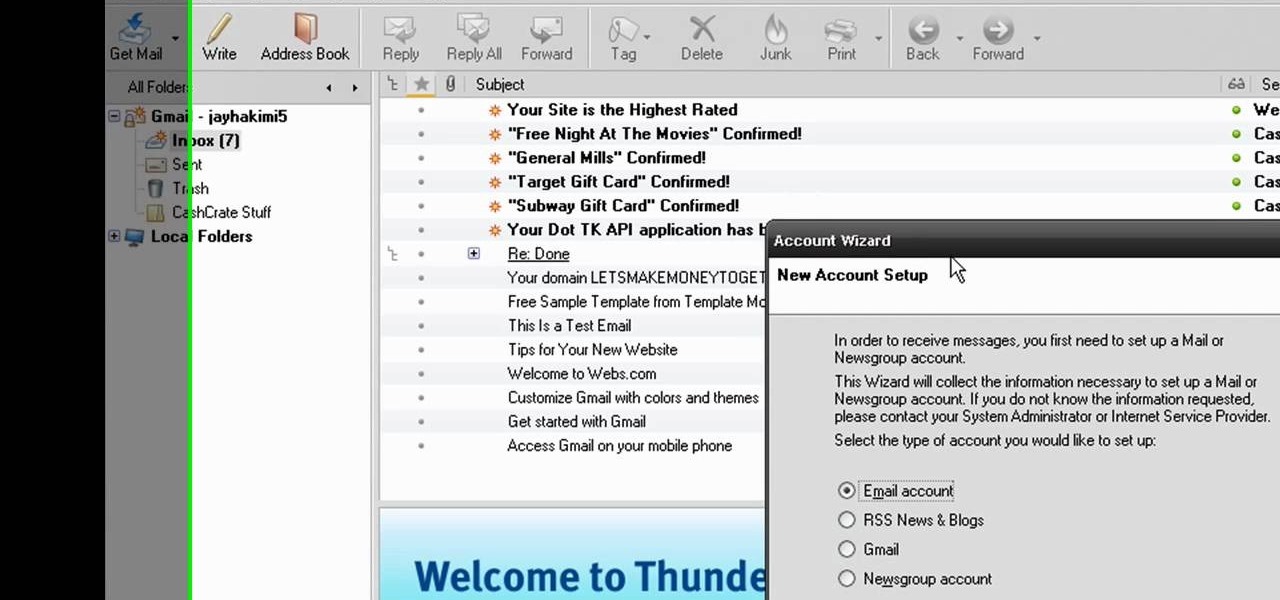
In this video from MegaByteTV we learn how to set up a Gmail account in Mozilla Thunderbird. First go to your browser and download Thunderbird from the Internet. Once downloaded, go to the Thunderbird application. Go to New and Account. Click on Gmail and enter your name and email address. Click Next and check off download messages now and click Finish. Your messages should now appear there. The first time you do this, all of your messages will look new but you can change that. If you'd like ...

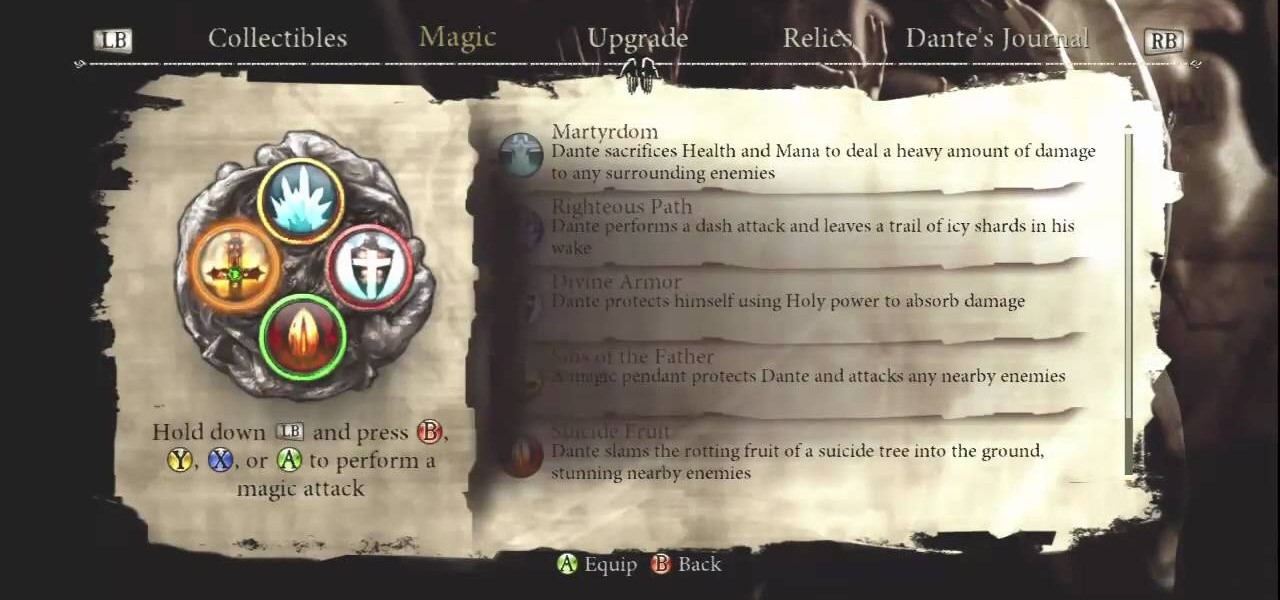
This video will show you how to get the "Poetry in motion" and "Masterpiece" achievements. When you enter the Fraud Circle towards the end of the game, you will be faced with ten challenges on ten levels. The fourth challenge (the save point is Malebolge 4) requires you to stay in the air for eight seconds. Instead of doing this, keep hitting the two demons until you get a 666 hit combo and the "Poetry in Motion" achievement. This can be done easier with the "Coin Of Plutus" and "Wings Of Fur...

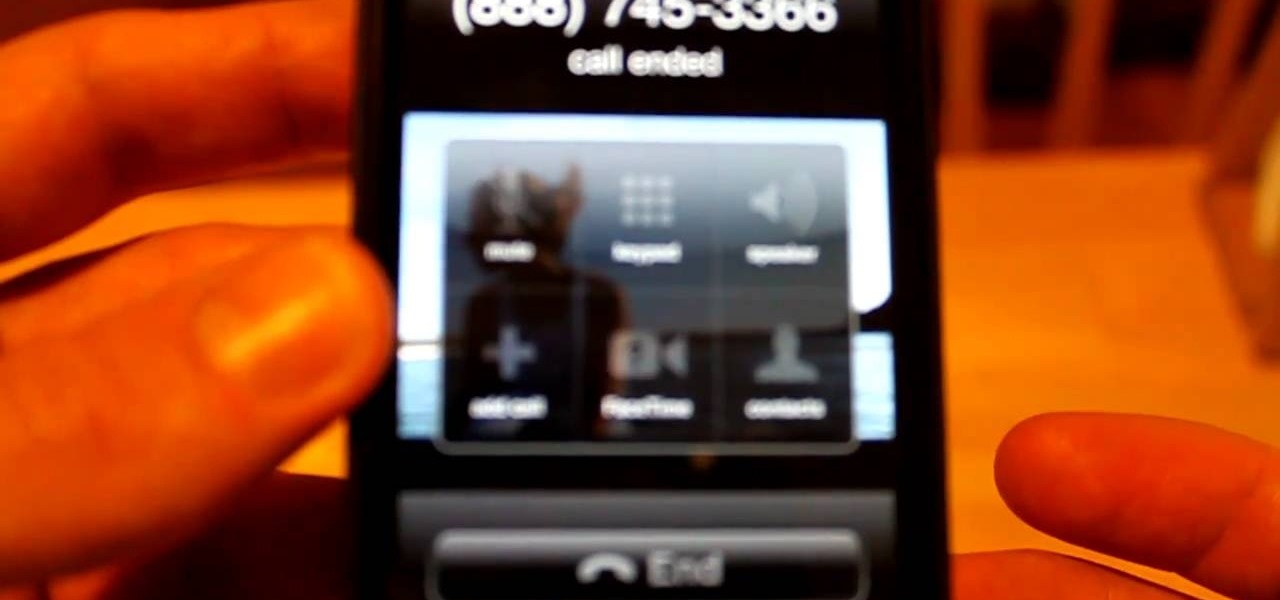
Want to make a phone call on an iPhone 4 running Apple's iOS 4.1, but don't know its passcode? Not a problem. In this clip, we learn a simple trick that will allow you to bypass the lock screen entirely and permit you to view the phone's contact list and place phone calls to any number you like. This glitch has been fixed with iOS 4.2, so treasure this hack while it still lasts! This will let you unlock someones password on an ipod or iphone touch.

It's a tired expression that men are dogs and women are cats, but there is definitely some truth to the saying. Women who are feline are a bit stealthy, sexy, and enter a room when THEY want to, not when you want them to. They're very independent and are in tune with their instincts.

Who is the hottest animated female character of all time? We're sure there are lots of differing opinions on that, but we think Jessica Rabbit must be at the top of the list of viable options. With curves so, well, curvy, that they enter the room before she does and eye-catching red hair, the seductress is one hot lady.

Need to protect a section of your overall flash content (say movie or slideshow) from unauthorized access, learn how to do so in this video.

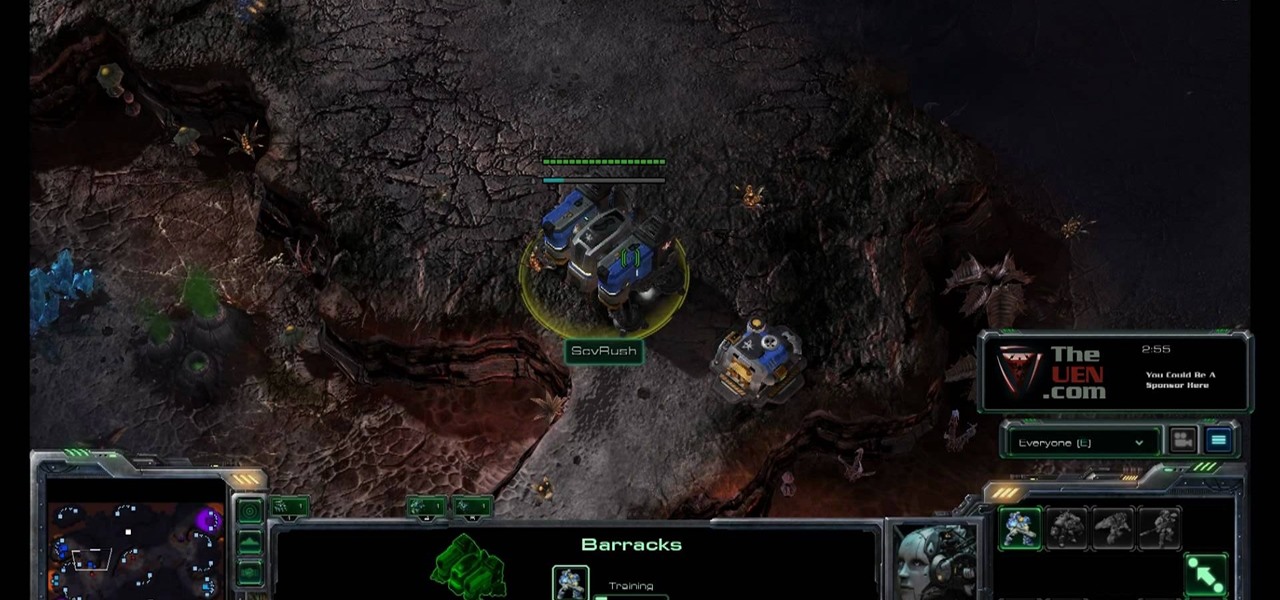
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to you can make a mobile wall of supply depots on your Terran base's...

In this video tutorial, viewers learn how to quickly troubleshoot memory problems in Windows. Begin by clicking on the Start menu. Type "mdsched" into the search bar and press Enter. The Windows Memory Diagnostic window will then appear. Click on "Restart now and check for problems". Your machine will then be rebooted and will run its memory diagnostics tool. It will look for any issues that may cause problems for your system. Advanced users can press F1 when it starts to specify certain opti...