Learning Chinese is hard, but it can be a lot easier with the help of a few great apps. As a native English speaker who's currently living in China, this is a process I've recently gone through. After playing the field, here are the three apps I personally think will help you the most with your Chinese learning adventure.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.
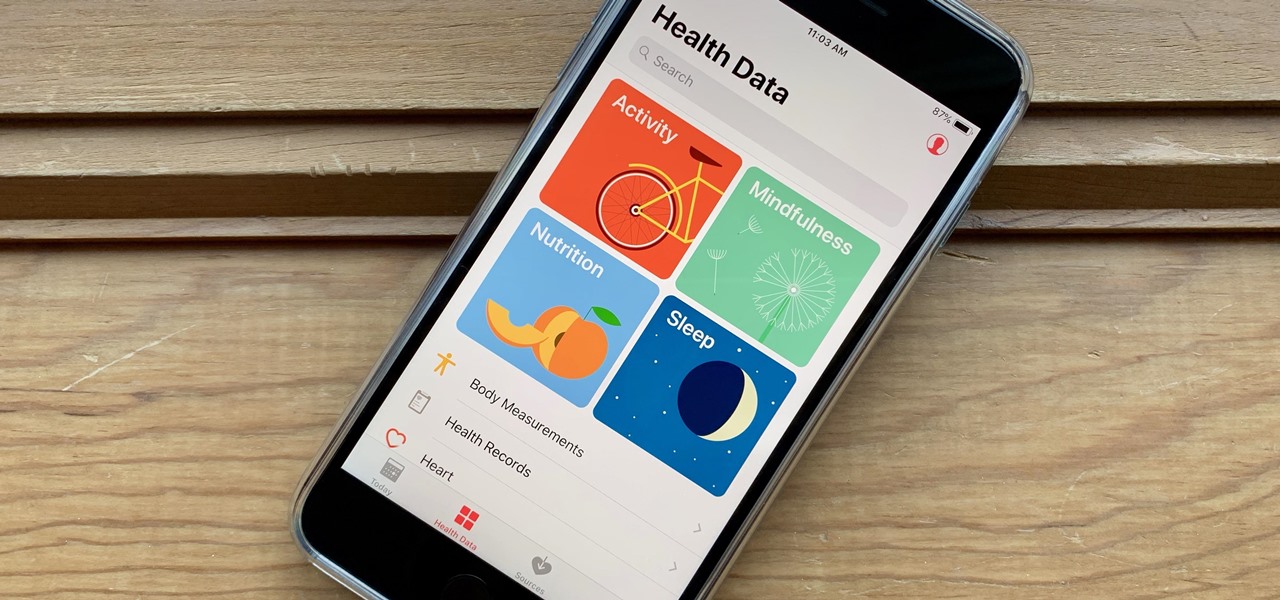
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.
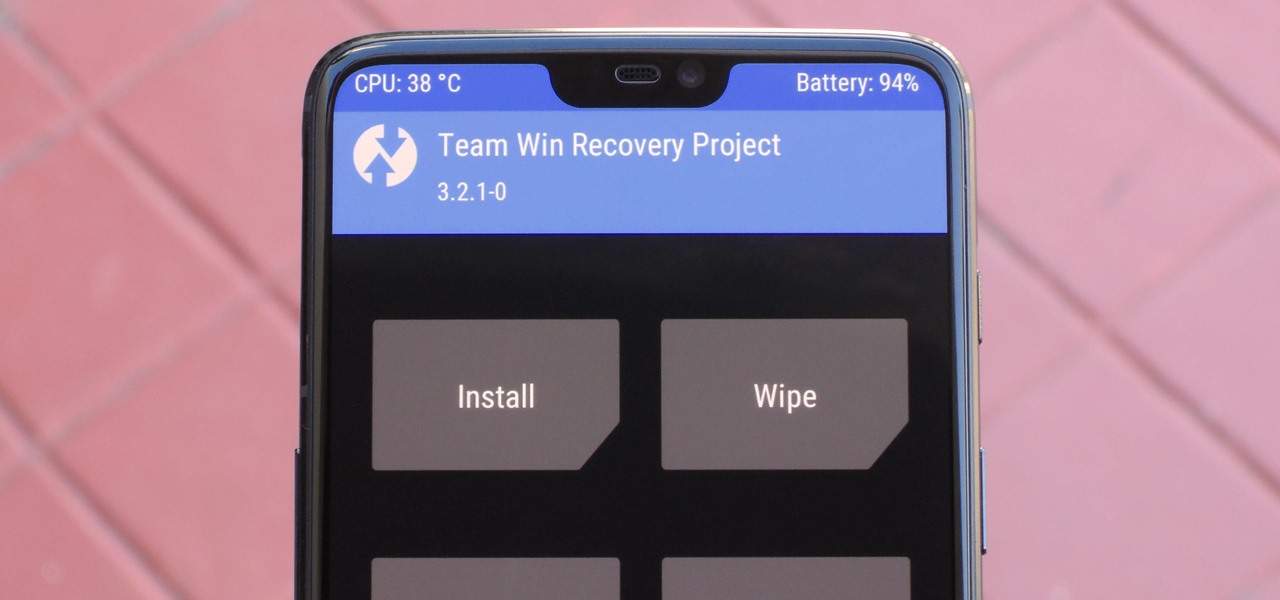
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

As the first Animal Crossing game on mobile devices, it's clear that Nintendo had a more social experience in mind for Pocket Camp, and I'm not talking about all the animal friends you can make. You can add other players to your list of human friends, and they're incredibly useful for a wide array of tasks.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

Having a Clostridium difficile infection means stomach pains, diarrhea, fever, and loss of appetite, and if the symptoms weren't bad enough, the disease often reoccurs. Now, new research has found an increased risk of recurrence in people who take medication to treat their stomach acid, gastroesophageal reflux disease, peptic ulcer disease, or stomach discomfort.

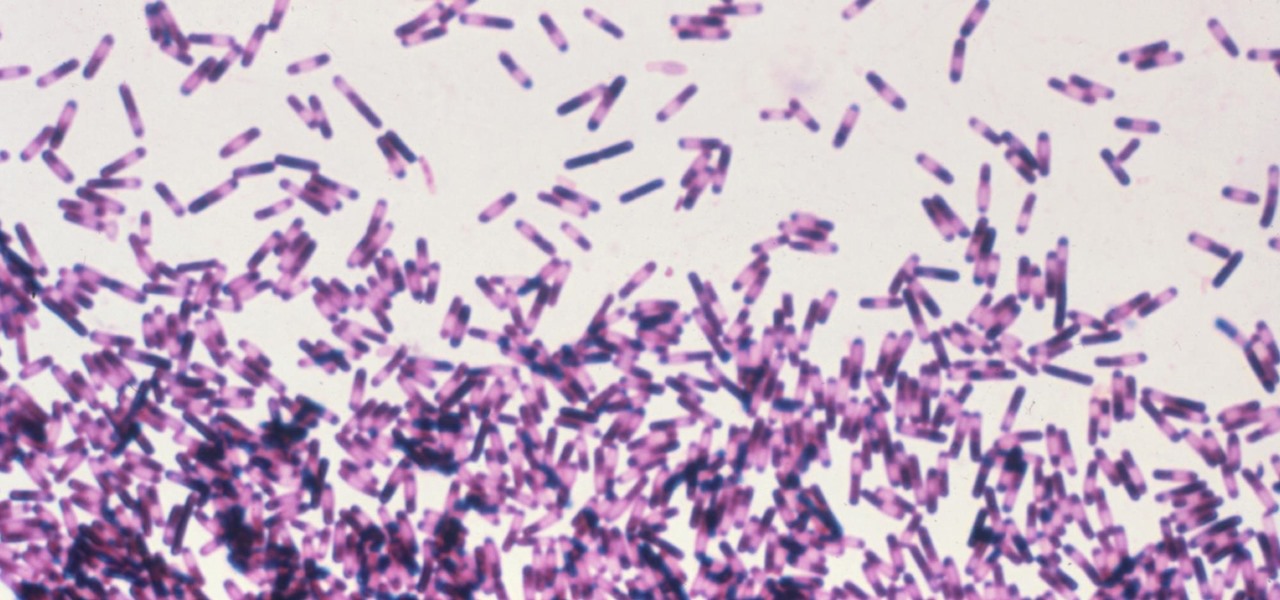
Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

Immigration and immigration policy are some of the biggest discussions happening in international and domestic politics right now. From building walls to opening borders, a definitive plan has not been made about how to deal with the large number of people who are fleeing their home countries in hopes of a different life.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

The next time you plan on going on an adventurous road trip, get paid for it! With the the new mobile app called Roadie, from developer Marc Gorlin, you can get paid to go where you're already going.

Technology allows us to communicate with others like never before, providing us with the ability to stay connected with past and current coworkers, classmates from high school, and even relatives in far-away countries.

Learning how to draw cartoon people can be a bit tricky if you're new to art, but in this video, I show you a really easy way to draw a cute cartoon clown.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

An open bottle of wine can be dangerous. You intend to enjoy—nay, savor—a single glass, but then two episodes of Top Chef later, that sucker is empty. Now you have to go to work the next day with a wine hangover. What happened? Turns out there are some unconscious reasons you might be chugging more wine than you wanted. Never fear. Along with clenching your fists to make better food choices, there are some tricks you can use to moderate your wine intake. Researchers at Cornell University disc...

I've often marvelled at the complex worlds people come up with on Minecraft. I particularly enjoy looking at maps with skyscrapers and modern structures in modern cities. If you're one of those people too, check out this sneak peek for a tour of a world-class city containing replicas of buildings including the Trump Tower, BMO and one of my favourites: The Bellagio Hotel! The world has been made on the XBOX 360 by a very creative user with the gamertag: TH3 3ND 0F TiM3.

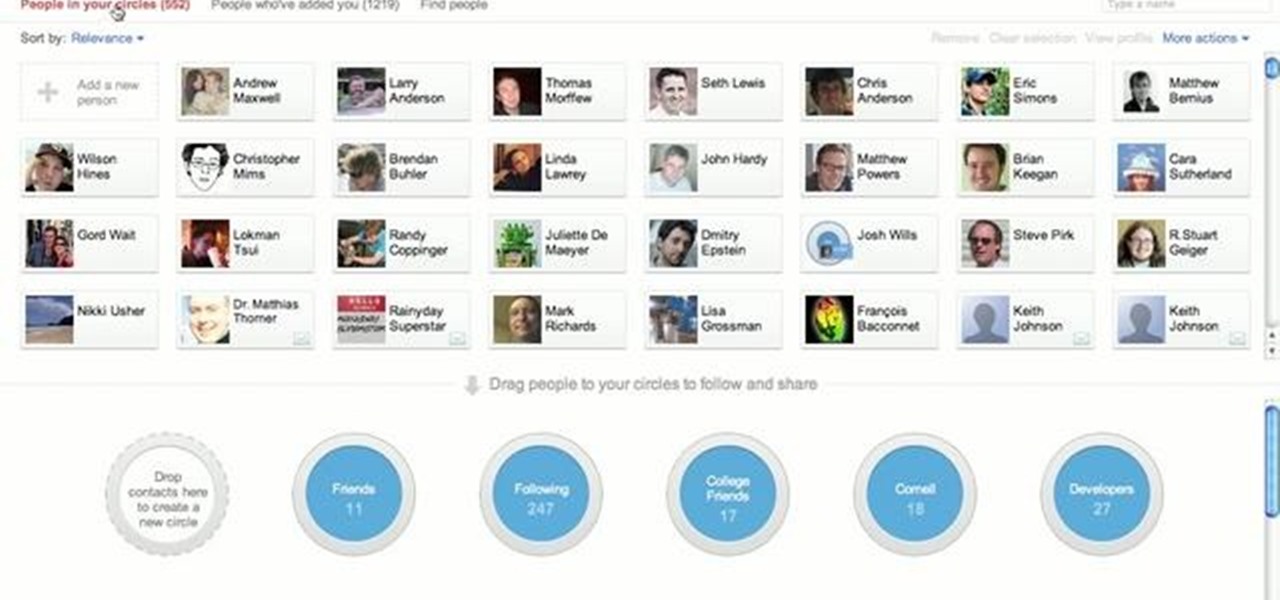
In addition to being a great way to share content and information that are also using Google+, additional sharing features in Google+ allow you to send content and information to other individuals who do not use the service. You can even import your address book to make sharing even easier.

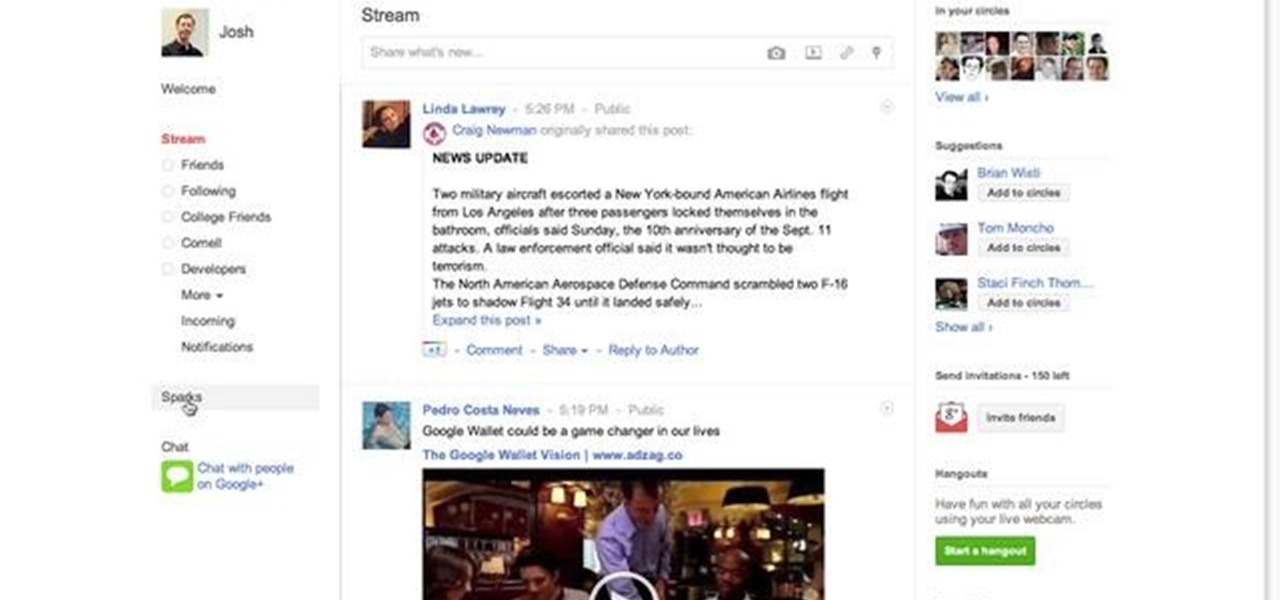
The Google+ Sparks feature is a kind of social search that allows you to find and read different articles and websites that have been selected by the people you follow and other Google+ users. It can help you find interesting posts and information on a specific topic.

Hack a pair of sunglasses to secretly record audio and video and spend less than $40 in the process with this how-to video. To replicate this hack for yourself, you will need a spy camera and black solar shield sunglasses. For detailed, step-by-step instructions on building your own spy recorder sunglasses, watch this hacking how-to from Kip Kay of Make Magazine.

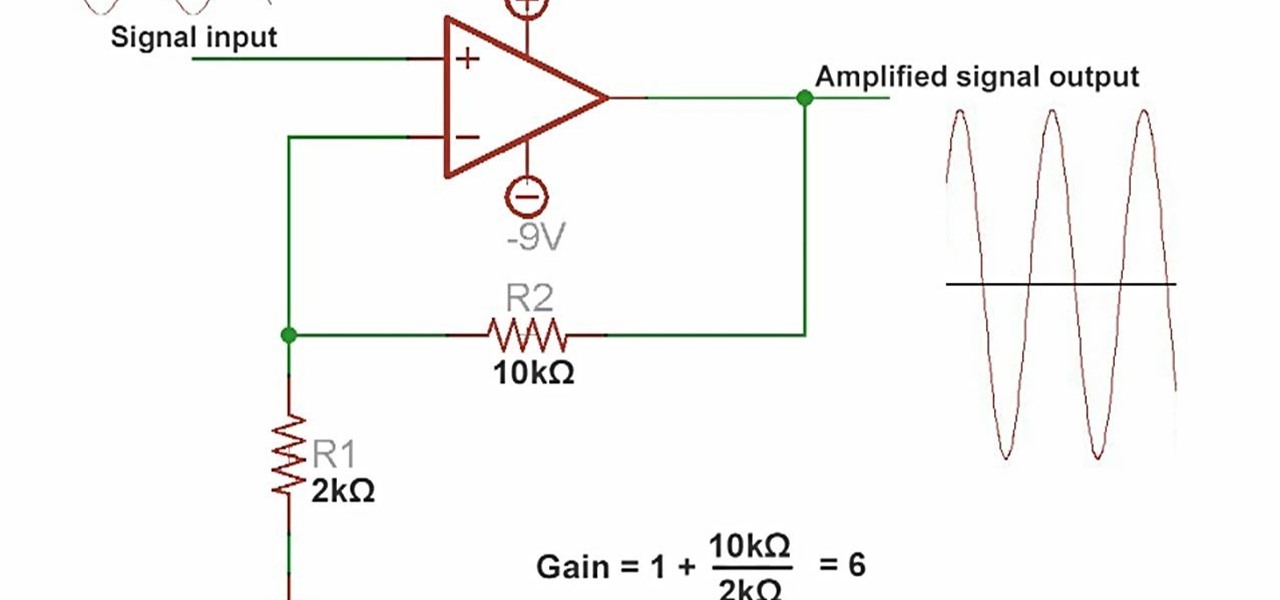
An amplifier is something that amplified the voltage on a circuit. The most basic kind is an operational amplifier, and this video will show you how these work and how to use them in your electronics. As an example you'll learn how to make a microphone circuit for spying on people or listening to your heartbeat.

The Bruno Mars single "Grenade" is taking him to a whole 'nother level of stardom, especially in light of his amazing performance at the Grammy's. This video will show you how to play a cover of the song on acoustic guitar and woo yourself some people.

Lots of people have problems with XBox Live matchmaking due to the NAT for their network not being Open. It's not readily apparent how to make your NAT open, but this video will show you how to do it.

The Assault class in Battlefield Bad Company 2: Vietnam is a nice simple class that can kill people quickly and support your team by providing them with extra ammo packs. This video will teach you some strategies for dominating as the Assault and also analyze the different weapons you can choose for the class.

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.

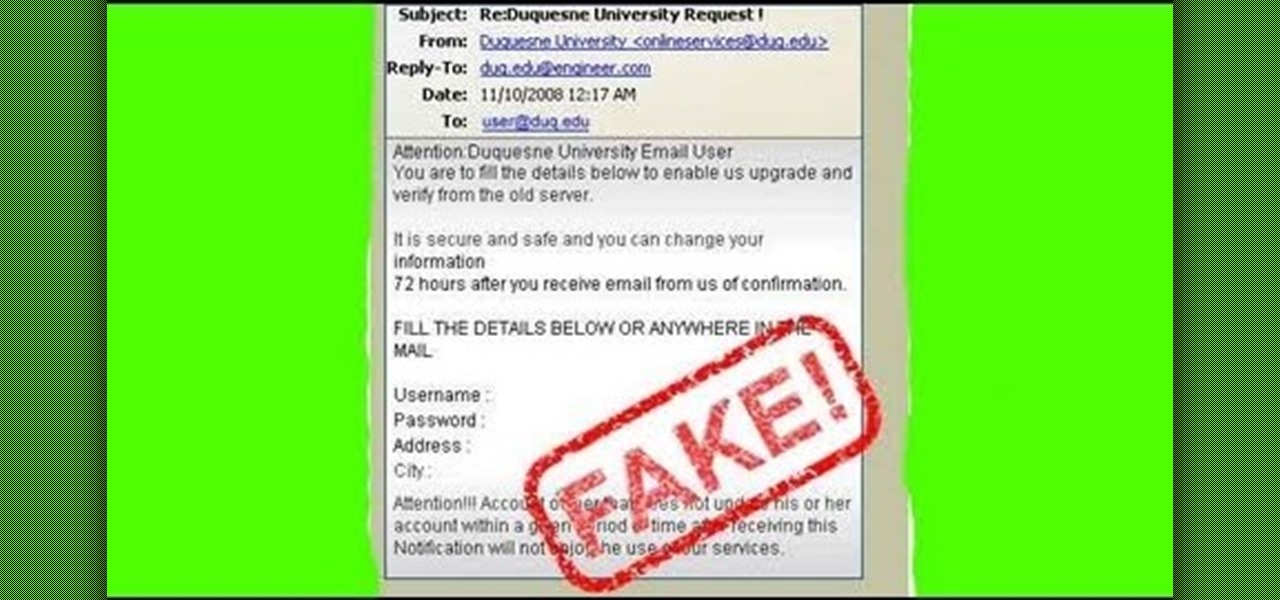
One of the greatest tools of email scam artists is spoofing, the process by which you can send emails that appear to come from a different account than the one from which they were sent. This video will explain spoofing to you, how to do it, and how to tell if a message you've received has been spoofed and avoid it.