One of the downsides of living in an unprecedented age of connectivity is the near-constant bombardment of information. WhatsApp, the go-to messaging app for people the world over, is just as susceptible to buildup of useless media files, thanks to awesome features that allow us to communicate in multiple ways, such as broadcasting to friends and family. Luckily, the app makes it easy to remove old and unwanted data from your iPhone or Android.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.
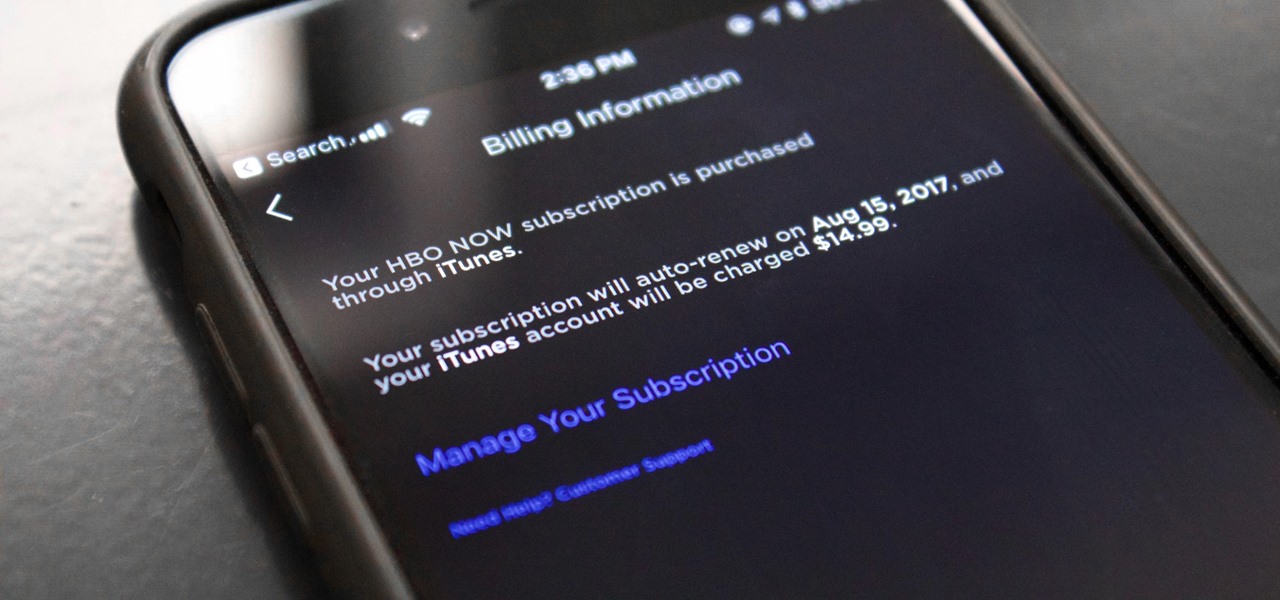
I'm a little biased — I love HBO. I wouldn't want to cancel my subscription, because there are constantly shows I want to watch. But I understand not everyone is like me. Some people might only subscribe to watch, say, Game of Thrones, then cancel their subscription when the show ends. In that case, if you're reading this before July 30th, you'll want to use this information five episodes from now.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.
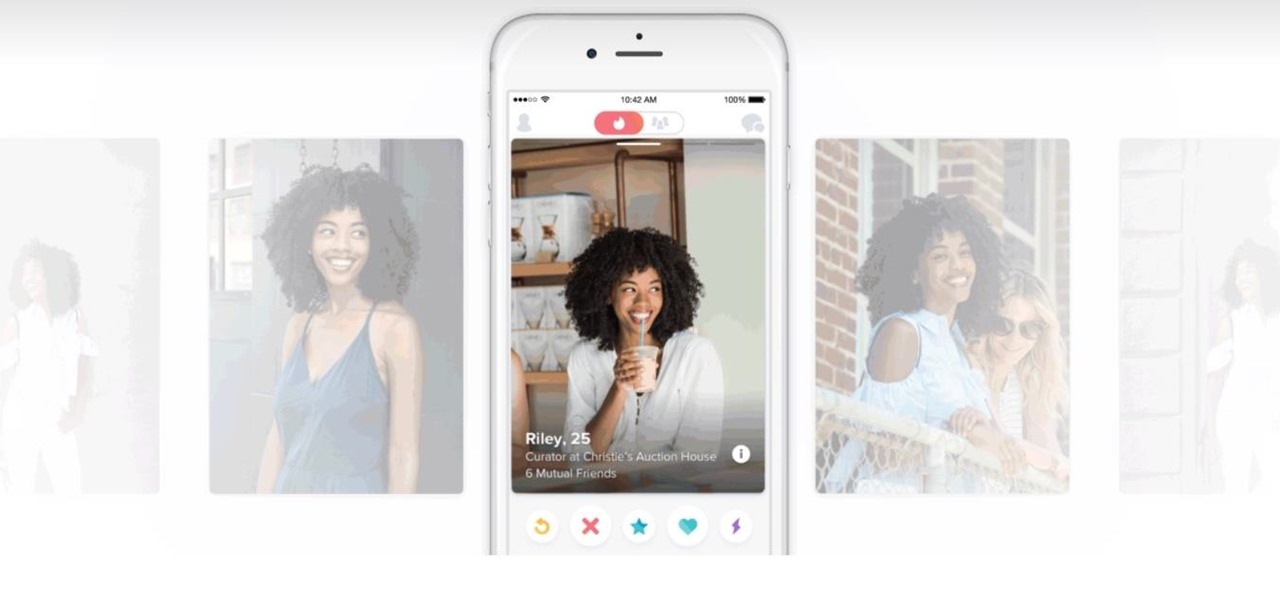
If we're being honest, very few people go on Tinder to fall in love with someone's personality. Oftentimes, the only reason they'll look at your bio is to make sure there are no red flags.

According to a new study from the Reuters Institute and the University of Oxford, people are getting their news from ... unexpected sources. Put away your CNN app and stop checking the New York Times because a familiar app is now keeping you up to date on current events: WhatsApp.

A new dating app has arrived, and it'll finally land you a date with your celebrity crush ... kind of. The app — Dating AI — uses face search technology to help you search for potential love interests that resemble a celebrity you're attracted to.

The Asphalt series has been a staple in the racing genre since its first incarnation all the way back in 2004 — I still remember buying it for my newly-obtained Nintendo DS. It warms my heart to see that, after all this time, Gameloft continues to produce mobile Asphalt games, releasing the latest for Android today. Unfortunately, that's about all Gameloft has taken from its previous efforts. To be frank, this game ain't good.

Update 6/16: This number is now way higher. In just the first two days of this sale, over 350,000 people have pre-registered for the phone.

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

The common thread between this week's Brief Reality stories is that augmented reality is beginning to prove its worth as a technology that improves workflows and processes. From customer service to healthcare to manufacturing, augmented reality is helping companies improve productivity.

Online lives could be made easier now that Facebook, Instagram, and Messenger are testing merged app notifications. 'Could' being the operative word!

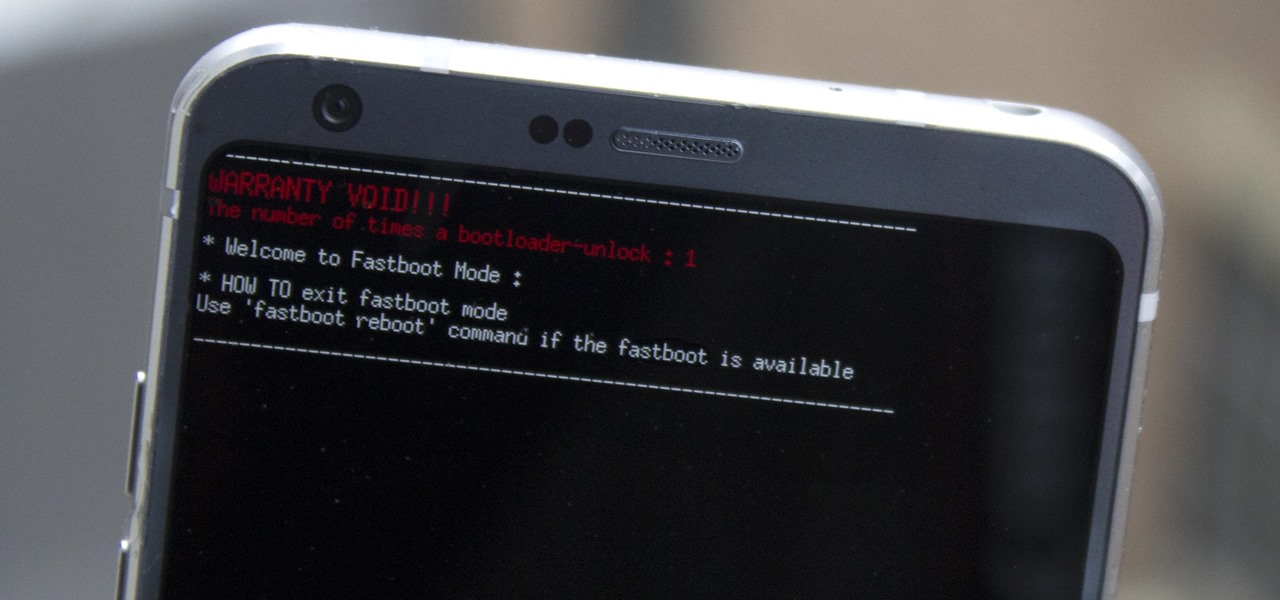
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Usually, we think of vaccines as preventative, a shot we get to prevent the flu or some childhood disease like measles or mumps. But there are vaccines for other purposes, such as the ones studied by researchers from the Netherlands.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

Princess Cruises' Coral Princess voyage disembarked in Fort Lauderdale on Saturday, March 18, after a 10-day cruise in which 182 people were sickened with symptoms of vomiting and diarrhea. According to federal health officials, a norovirus is suspected for the outbreak.

A bacterium which triggers respiratory disease has been detected in the water systems of two Pennsylvania nursing facilities.

A new contender has entered the mixed reality ring. San Fransisco-based Occipital has just released an "Explorer Edition" of Bridge—an iPhone-based mixed and virtual reality headset that uses their popular Structure Sensor. At a fraction of the cost of a HoloLens developers kit, this could be a place many curious people use to find their NextReality.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

If you're looking to mix up your home décor with something a little bit outside the traditional cabinet box set, check out the amazing Wave cabinet from NYC-based, Chilean designer Sebastian Errazuriz. This revolutionary design will change the way you think about interior decoration and furniture functionality.

Deaf people primarily communicate through sign language, so understanding spoken languages can prove challenging. To bridge that gap in communication, the HoloHear team built a mixed reality app at a Microsoft HoloLens Hackathon in San Fransisco that translates the spoken word into sign language.

The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swipe to the left from right side to quickly snap a picture.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

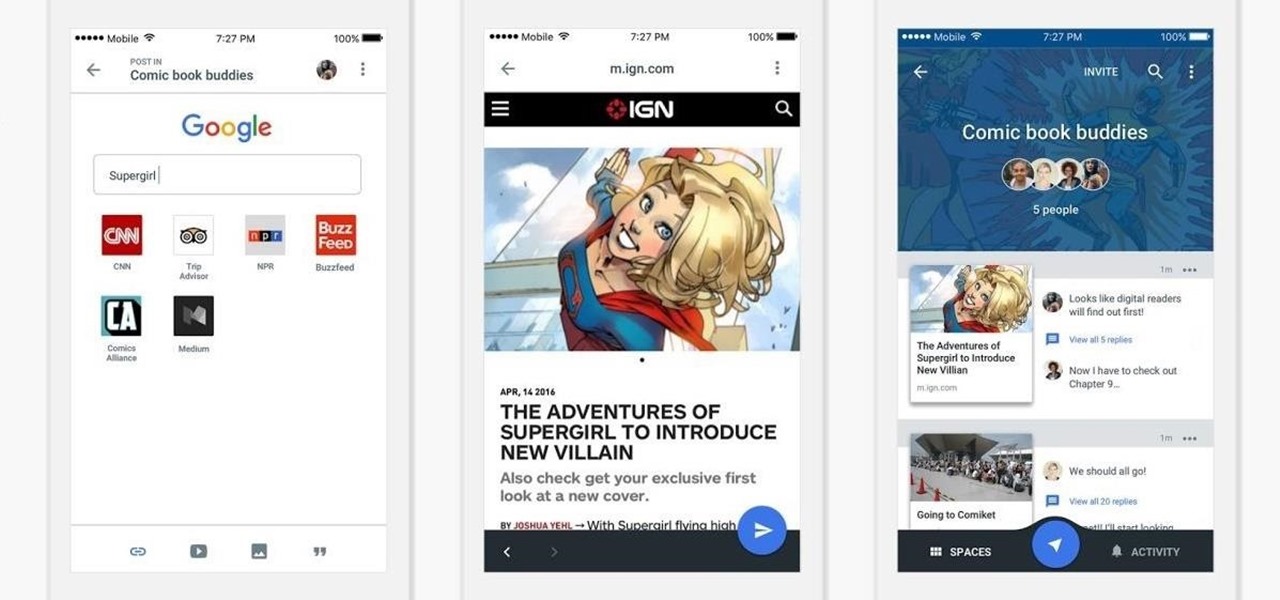
Google is launching a new app called Spaces that lets you share things from the web with small groups of people. The aim of Spaces appears to be granting you a forum with like-minded people to help cut down on off-topic comments that can steer a conversation off the rails. Spaces comes with Google Search, Chrome, and YouTube built in, so you won't need to switch apps to go hunting for interesting content to share. You can invite people to your groups—or "spaces" as they're called in the app—b...

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best due to Google's excellent cloud service, feature-rich web-client, and their easy-to-use Android and iOS applications.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.