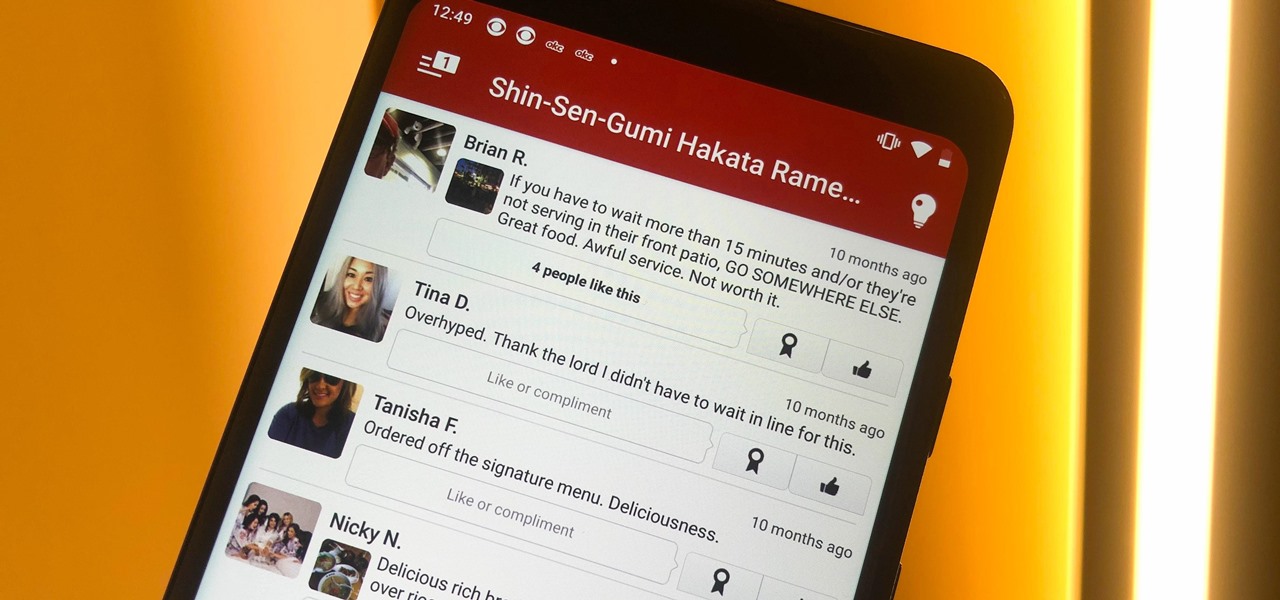
Yelp reviews are great for getting a feel for how a business operates, but they can't always be trusted, and they don't always get to the point fast enough. That's where "Tips" come in, and you can view and make them whether you're on an iPhone or Android phone.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

If you're familiar with jailbreaking, you're well aware of the fragmented nature of downloading tweaks. Unlike the iOS App Store, which contains about two million apps of varying categories, installing jailbroken packages often requires you to first install a separate repo into either Cydia or its replacement Sileo, as many of these tweaks aren't available outright.

After entering the UK's version of bankruptcy last month, Blippar's assets are up for sale, and bidding ended today.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

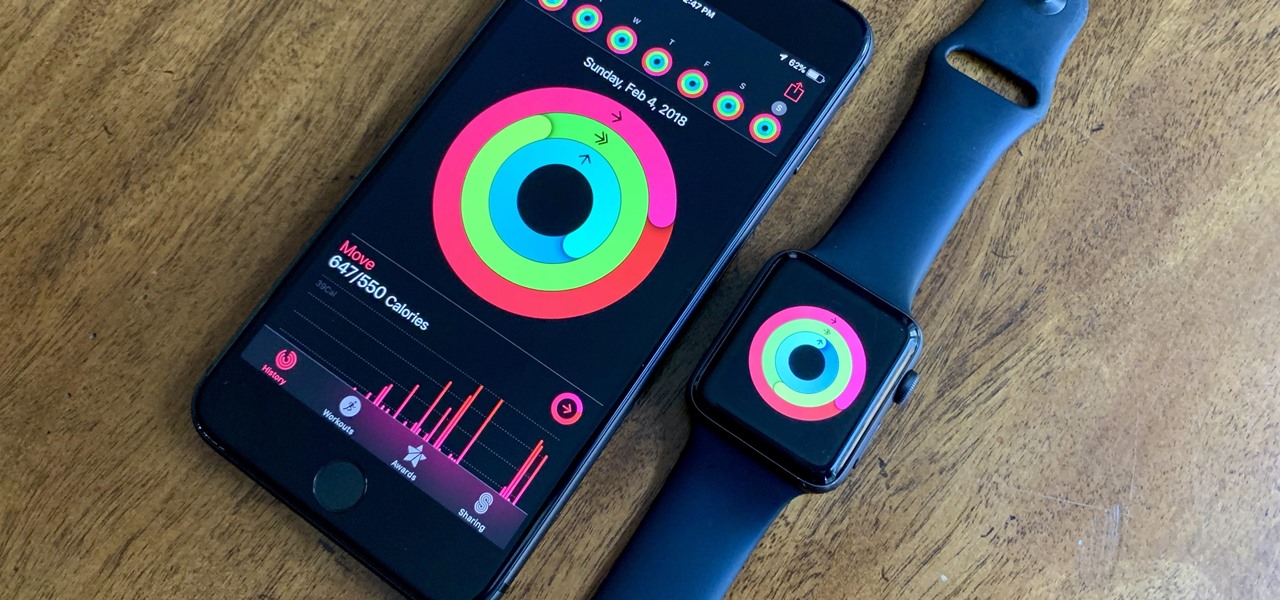
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

Magic Leap and AT&T have lifted the lid on multiple parts of their mysterious relationship today. According to AT&T Communications CEO John Donovan, the company is planning to launch a beta version of DirectTV Now for the Magic Leap One in 2019.

FaceTime has been around since iOS 4, and year after year, things stayed pretty much the same aside from a few small changes. In iOS 6, calls over cellular networks were finally possible, and audio-only calls were officially supported starting in iOS 7. But the one feature most everyone has wanted since FaceTime was a thing — group video calls — didn't show up until iOS 12.1 for iPhone.

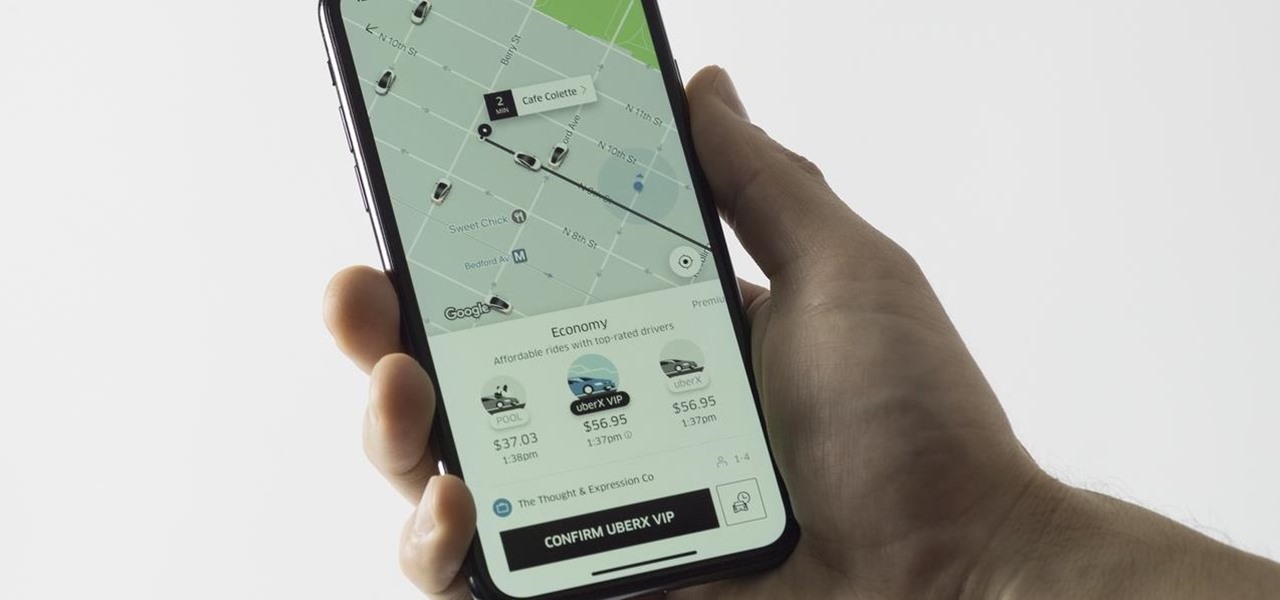
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

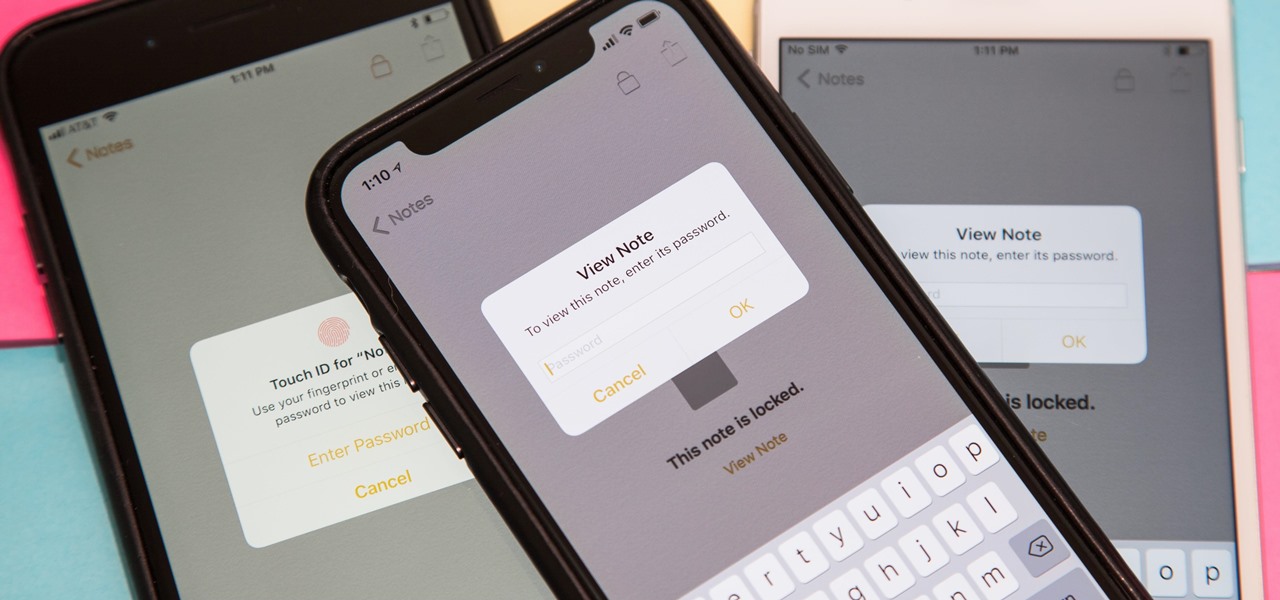
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

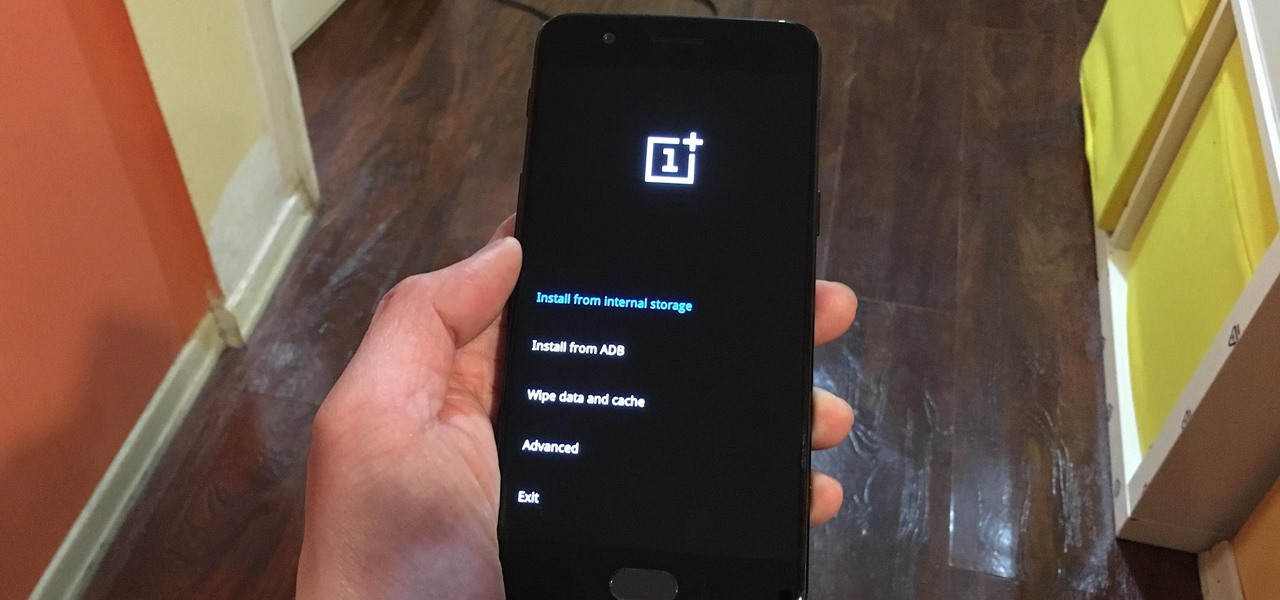
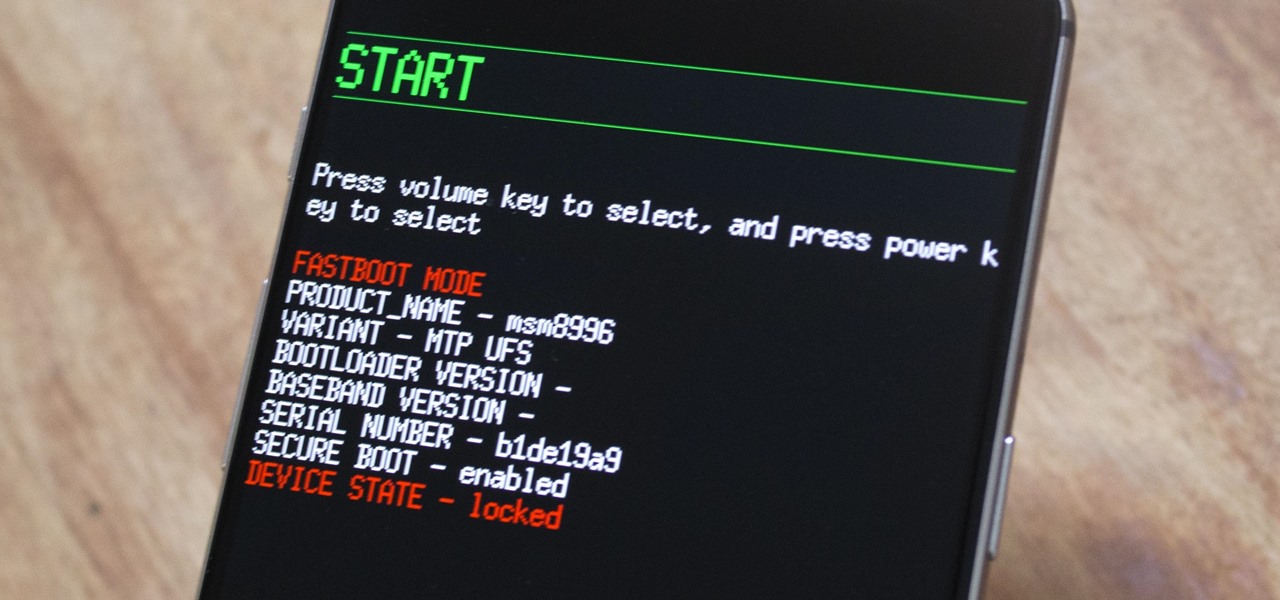
Both the OnePlus 5 and 5T have two pre-boot menus that every owner should know about: Recovery mode and bootloader mode. The recovery screen lets you wipe cache, perform a factory reset, or install firmware, which can help save the phone from a soft-brick. Bootloader mode, on the other hand, lets you send Fastboot commands via PC or Mac to lock or unlock your bootloader or flash images.

After installing the new iOS 11 update on one of our iPads, we noticed something peculiar — AirDrop simply stopped working. The button was still there in the revamped Control Center, but it was almost imperceptibly grayed out. Tapping it did nothing, nor did long-pressing or 3D Touching. Even more perplexing, AirDrop was just working flawlessly before the update.

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

If you live in New York City and are itching to sell your Yeezys, you're at risk of falling victim to thieves. A devious duo is searching Facebook to find people selling the popular sneakers and then robbing them at gunpoint when they meet up in person.

With significant advancements in the treatment and prevention of HIV, you'd think the stigma surrounding the deadly virus and AIDS, the syndrome the infection causes in the body, would have lessened. Unfortunately, a new project looking at conversations on Grindr — a social networking app for gay, bi, curious, and queer men — has shown that this stigma is very much present.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

A new medical development is going to change the way many of us look at getting the flu vaccine. A painless flu vaccine skin patch is making needles and vials a thing of the past. Researchers from the Georgia Institute of Technology and Emory University have shown that a flu vaccine can be administered safely and comfortably with this new patch, which delivers the vaccine through a matrix of tiny dissolving microneedles.

Maine reported their first measles case in 20 years yesterday, June 27, in a press release from the Maine CDC. Many other people may have been exposed and could show signs of infection soon, with the potential for outbreak brewing. The last measles case in Maine was in 1997.

Millions of dollars continue to pour into the Chinese driverless market. Now, according to research firm CB Insights, $929 million have been invested in the first quarter of this year.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

Viral infections have been the focus of attention in the development of autoimmune diseases—diseases where the body's immune system reacts to the body's own cells—because they trigger the immune system into action.

The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

A terrifying antibiotic-resistant superbug, one thought to only infect hospital patients, has made its debut in the real world. For the first time ever, the superbug carbapenem-resistant Enterobacteriaceae (CRE) infected six people who hadn't been in or around a hospital in at least a year, and researchers aren't sure how they got infected.

This week, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that not only does Samsung have a new virtual reality headset coming, but that Samsung intends to enter the field of augmented reality, too. In fact, Hong talked very little about virtual reality and instead spoke at length about Samsung's move into augmented reality.

The rumor train for Samsung's upcoming flagship phone is now running on full steam, and some of its cargo (or lack thereof) might not be warmly welcomed by many when it finally pulls into the station.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)