Now that you can invite anyone you want to Google+, the floodgates are open. If you've been bummed out about not being able to share the joys of Google+ with your friends and acquaintances, make use of that handy envelope icon the right side of your stream page. Just enter the email addresses of the people you want to invite, and hit the "Invite" button.

You've had a massive hard disk failure.. ...in your PC or laptop and like a large number of people who think it will never happen to them...you did not have a backup of those 2000+ family pictures, those hundred of important Word documents, those family videos that you downloaded from the camera then erased from the cameras disk...the inevitable "I'm Screwed!'

No two snowflakes are alike. The same goes for people. But a snowflake can easily compliment one's own individual charm, although finding your perfect soulmate snowflake is quite a challenge. Or... it was.

So many people have searched for bypassing the time limit on Google for sites like videobb and VideoZer, I figured it was time to tell people the easiest way to bypass those 72-minute time limits without downloading any software from third-party sites. This is a very easy guide on how to use a website to bypass time limits.

The email application on the iPad is similar to Apple's iPhone email application but revamped with some clean features. The interface in the app makes emailing a breeze, and there is even a bit of multitasking in the current OS for email. This video will show you how to use email on the iPad.

Mad Science has entered the automatic pet feeder project as an instructable in the Make It Real challenge. Nine of the winners will receive their own 3D printer! If you are now imagining all the cool stuff we could do for Mad Science with a 3D printer, please share your ideas and vote for the entry here.
Immigration Laws United States Citizenship

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

In this video tutorial, we will go through the basics of setting up and editing tasks in MS Project 2007. Project is a great application for time management, planning and scheduling. It's really a must for any business—small or large.

Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the latest updates on Google+ Photos.

One of my biggest frustrations with Google+ right now is the inability to search my stream, as well as the lack of any bookmarking features. To find posts I want to refer to, I either have to type in the name of the person who posted the status, or I have to keep hitting the "More" button to find what I need. Both ways are inefficient.

Meet DareDroid: sexy nurse, geek couture and mobile bartender, engineered into an all-in-one technologically advanced garment. Created by fashion designer Anouk Wipprecht, hacker Marius Kintel, and sculptor Jane Tingley, the team calls themselves the Modern Nomads (MoNo), and their series of garments fall into Wipprecht's invented family of "Pseudomorphs". Pseudomorphs are tech-couture pieces that transform into fluid displays—which is exactly what DareDroid does.

Enter to win an autographed copy of Sharon Beals' book, Nests: Fifty Nests and the Birds that Built Them. Enjoy her incredible photography of 50 birds and their nests.

As someone who’s entering a time of life that involves weddings, reunions, and generally running into people I haven’t seen in awhile, I find myself being shocked by how much people have changed over the years. A lot of times, people will have dropped a bunch of weight, or have turned into a kind and articulate human being, or have obviously stopped doing so many drugs. It’s important, when complimenting people on positive life changes, to let them know how well you think they’re doing withou...

New York based studio softlab's latest installation "(n)arcissus" is an eye-bending site specific installation currently on display at the Frankfurter Kunstverein art center in Frankfurt, Germany. The piece, made with over 1,000 mylar and vinyl laser cut panels, hangs in a stairwell, measuring 9 meters tall from the lobby ceiling.

Sorry, I posted way too late, but:Get a free Gobbler transformation with the promo code: gobblegobble. Enter it at the Wizard101 site, where you log in and then type it in in the "Redeem Card or Code" "Promotional Codes" section.WarningThis promo code ends at midnight TODAY, so enter it quick!

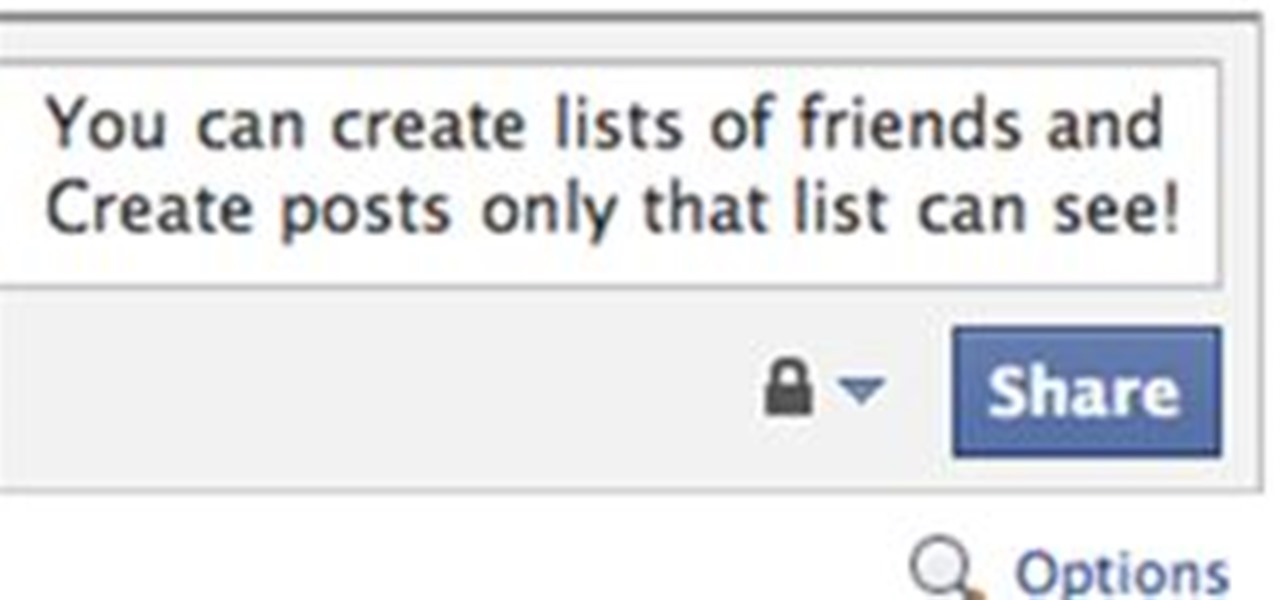
You may want to create a list of certain friends so that you can post certain status updates, photo albums, links, or application posts for just them to see. I'll show you how to set up lists

In this software video tutorial you will learn how to set a milestone in MS Project 2007. Milestone is an important task. Lot many times a milestone is like a goal or deadline to be completed by a particular date. It is defined as a task that doesn't have a duration. To make a milestone, enter a task and under duration, enter 0d. This will turn in to a milestone. To make task in to a milestone, double click on the task. On the next window that comes up, look for and click on the 'advanced' ta...

Dandruff -- the embarrassing white flakes that end up like snowfall on your shoulders and clothing. There are plenty of dandruff shampoos on the market to choose from, unfortunately, they are all very expensive. If you have ever wondered what ingredients make them so expensive, the simple answer is there are no expensive ingredients that make them so effective. So, the next question might be, why are they so expensive? And the answer to that is dandruff shampoo companies know they can charge ...

Not every tweak or theme is automatically available once you jailbreak your iOS device and install the Cydia application. For certain tweaks, you'll need to manually add its source, which is simply a web address linked to repository where the tweaks are hosted.

In this tutorial, we learn how to set up costs in MS Project 2007. First, go to your resource sheet and enter in the cost option in the type column. Write in how much you paid for this, because it's not a regular cost. Assign this cost to a task to specify the cost per task. At the end of the project, you will be able to see how much you spent on airfare. Enter in all the different costs you paid and then the amount for each one. When you are finished, you will be able to see how much you spe...

The iPhone 4 for Verizon is already old news, thanks to Sprint's unveiling of the Kyocera Echo smartphone last Monday.

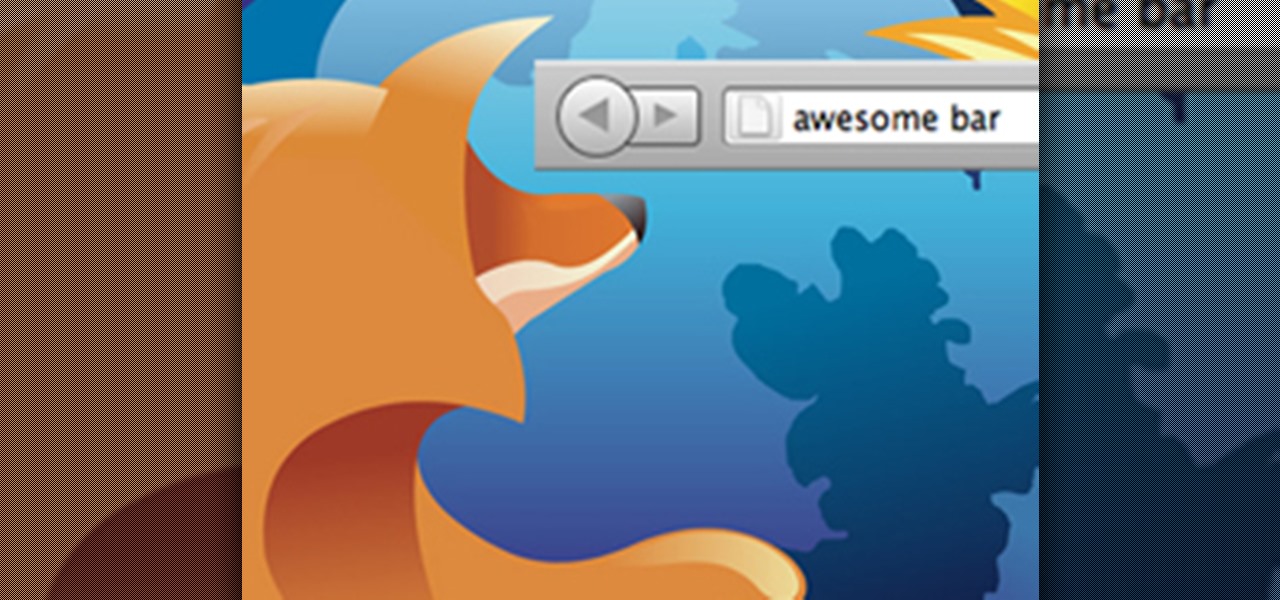
Getting used to your new Firefox 4 web browser? If so, you might have seen some improvements in the Location Bar. The updated features make browsing the web a cinch, so it's no wonder why more and more Internet junkies are calling it the Awesome Bar. It's faster and easier to use, and there's even some optional tweaks that you can employ to make your Internet experience smooth and effortless.

To prevent bed bugs from entering your suitcase, you will need to pre-treat it, with diatomaceous earth. Bed bugs often hitchhike home with you when you stay overnight in hotels or on long trips. They will normally stow away in your suitcase. To prevent that from happening, dust your suitcase with a diatomaceous earth (DE) compound. For this, you will need a paintbrush, diatomaceous earth, and a large plastic bag. Sprinkle a little onto your suitcase, and use a dry paintbrush to spread the di...

In this tutorial, we learn how to allow only your computer to access your Wi-Fi while using Apple Airport. First, select the Apple Airport Express item on the base station chooser. Double click this and press Configure, then enter your password in the new window that pops up. Now, a new window will open, and you will need to click to "Access Control" tab on the top of the window. Next, click "add" and then select "Mac address" and enter in your MAC address and description. Once finished, clic...

Okay folks, I've finally finished my underground ancient city. Actually it's more like, I need to move on to other things and really should stop obsessing over this thing already. You can find it at the warp location "woodcity" - which is funny because there is not a stick of wood in it! That's the idea: the city is so very, very old that nothing but stone (and some conveniently located, er, naturally burning torches and lava and ice deposits) remains to be seen today. All is enveloped in the...

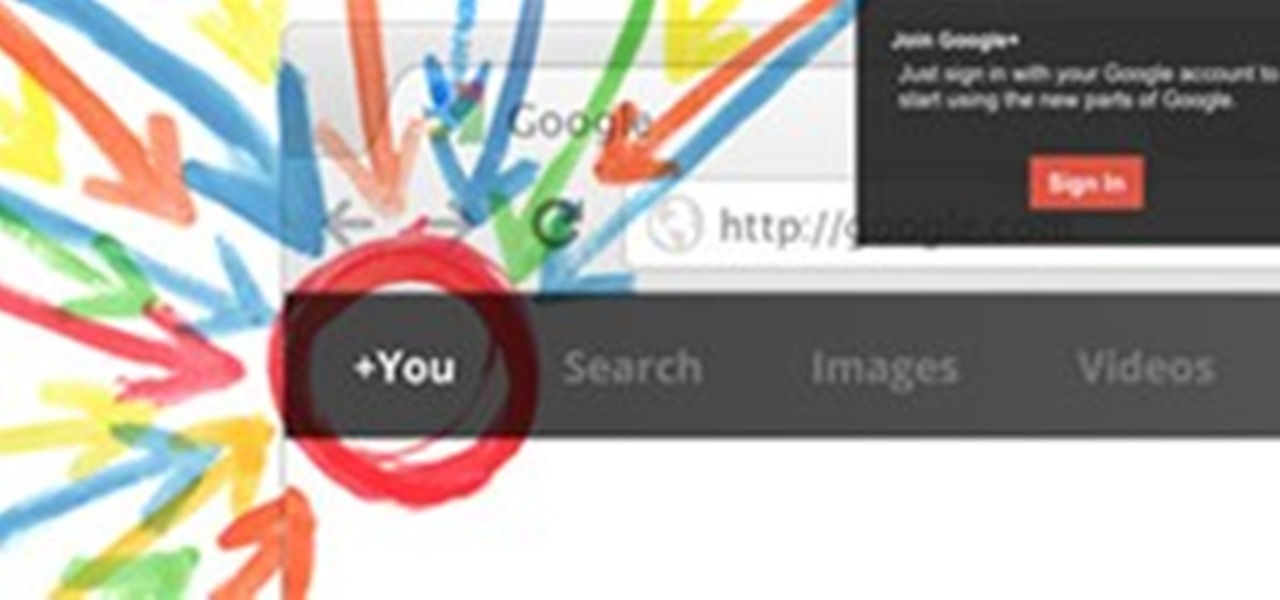
Google+ is nearly complete. We've got hangouts, pages, photos, games, and lots of ways to share what we love and build an audience. But it seems like Google isn't quite done yet. Since most of Google+ has been "shipped", it's now time to "ship the Google" as +Larry Page mentioned in the quarterly report.

Answer a few questions for the chance at $15,000.ENTER HERE

This prank will involve as many people as you can fit into one car, and you will need to have the majority of your buddies dressed in military outfits. The one exception is that you will need to have one person dress up as the military sergeant, which will be leading most of the prank. You need to rig the car that you are using to smart smoking from the hood, or if you want to make it more realistic you could actually have the wheels fall completely off the vehicle itself once it has entered ...

This is the GetNetWise video guide on how to set up Internet Explorer 6.0 for Windows to allow cookies from some sites. This is useful if you wish to block cookies by default, but allow for certain sites. The procedure is simple; firstly, select "Internet Options" from the "Tools" menu. Then select the Privacy Tab of the Internet Options menu, and under the Web Sites section click the Edit button. In the text box labeled "Address of Web site", type in the address of the site from which you wa...

In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like this are unlimited. For example, I modified the basic code so I would receive a text message letting me know every time someone rang my doorbell. The program could interface with Arduino through a serial port, and send d...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

You've finally got an invite into Google+. Now what? At first glance, things can be a bit overwhelming. We've got some great tips to help you get started.

Do you ever really know someone? I mean really really? Super really? Sometimes we can talk and be with people normally for years and then bam: five people dead, house on fire, dog missing. All the while people shake their heads and regret that if they had just put the little clues together all of this could have been averted.

So You're New to Counter Strike Source? So you're new to Counter Strike Source and you want to improve your gameplay? Great. You've come to the right place.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Minecraftian is a beautiful and lengthy machinima made using Minecraft; dubbed the 'first full feature Minecraft Film'. The movie has everything a great movie needs: strong editing, beautiful music, and Minecraft itself.

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

Make your mobsters2 avatar invisible here's how. Open Firefox,

If you have yet to check out the Secret Tips from the Universe DIY Contest, now's the time! The clock is ticking—you only have until Sunday, 11:59 p.m. to enter for a chance to win original artwork by Yumi.