So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.

Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

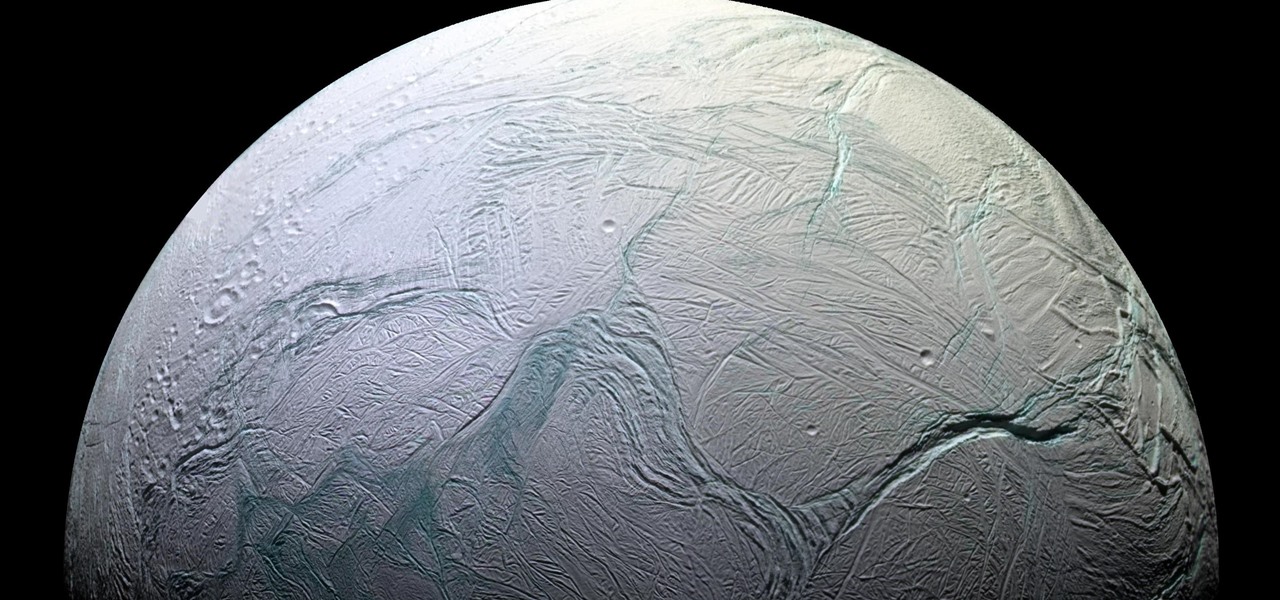
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

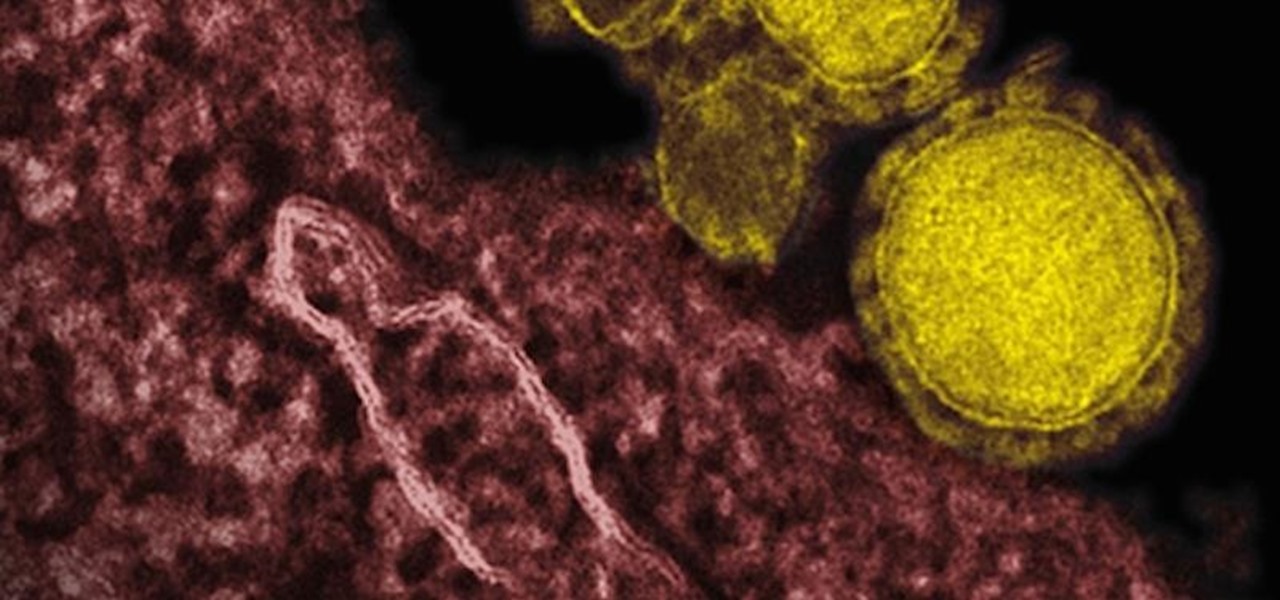
Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

Cholera may be rare in the US, but cases of the disease have increased worldwide since 2005, particularly in Africa, southeast Asia, and Haiti. An estimated 3 to 5 million people are infected, and more than 100,000 die from the disease globally each year, mostly from dehydration.

If you spend a lot of time reading about food, chances are you've heard about bone broth. It's all the rage these days, from high profile chefs like Marco Canora building menus around it, to celebrities like Salma Hayek using it as self-prescribed beauty regimens.

Video: . This video will show you how to secure your kayak to a J bar roof rack carrier.

Many people who use braided line complain that it gets wind knots which may have to be cut off and expensive line discarded. Almost all "wind knots" have nothing to do with the wind and are caused by user error. This video explains how to avoid those knots and start taking advantage of braided fishing line.

Beautiful Macrame Bracelet. This video tutorial is intended for people who know a little bit about macrame :)

Hi again! :) Many people have been asking me to do a lesson about what to say when you visit the doctor in Lebanon, so here's that lesson. So if you're sick, I hope you get well, and I hope you enjoy this lesson and find it useful.

How to make a Macrame Lagoon Earrings. A good accessory to wear everyday and for any occasion. (This video tutorial is intended for people who know a little bit about macrame)..

If you're still looking for that perfect prank to pull off on people on April 1st, here are 5 simple yet funny practical jokes you can get your friends and family with. Most require household items which you should already have, so you won't need to go out and purchase any additional stuff. Check out the video tutorial to start pranking right away!

This is just a heads up that thieves are now using GPS fitness apps to target people. Thieves are using popular GPS fitness apps such as Strava to find out where you live where they will then come and steal your bikes.

How to Make a Easy Macrame Criss-Cross Bracelet with Beads. It's simple to make and looks really cool and fun :) Even people who just found out about macrame can make this bracelet!

How to make a wavy macrame snake necklace with beads. This necklace looks very interesting and not hard to make, perfect to wear everyday and for any occasion :) This video tutorial is intended for people who know a little bit about macrame.

Looking for an April Fools idea for a prank, Well here's one you can easily pull off. Works best in the mornings which is when most people usually eat cereal. Check out the instructional video for further details.

Sun in the Sea waves - Macrame bracelet tutorial. This bracelet has some macrame design elements - waves, chevron etc, and this is my design. This video tutorial is intended for people who know a little bit about macrame :)

Maybe it is inspiration for some people around here. I have done this in AE and want to share it. Feel Free to download and use or customize it however you want. Download the template here (music not included).

How to make a Macrame Bracelet with a big bead (eye) in the middle. This video tutorial is intended for people who already know how to macrame..

This video will show you an easy way to draw one of the most popular people on YouTube at the moment - Zoella! From drawing out a rough first sketch, all the way through to creating a complete, coloured-in illustration, this video will show you how it's all done. Hope you like it!

For Halloween, most people want to go all out when it comes to decorating their homes with spooky, scary decorations. I myself decided that for this year I would go ahead and try something more realistic, which is why I went to my local thrift store and purchased a stuffed dog. I made sure it looked as realistic as possible for this project.

This method can be used on any kind of scroll saw pattern. Animals, people, inanimate objects, etc. Done on paper and scanned onto my computer only to clean them up and color them in to display. Three part series.

For this prank, you'll be messing with people while they eat. You'll need a fake zombie finger and a bag of their favorite snack. Preferably chips. This one is perfect as a Halloween prank.

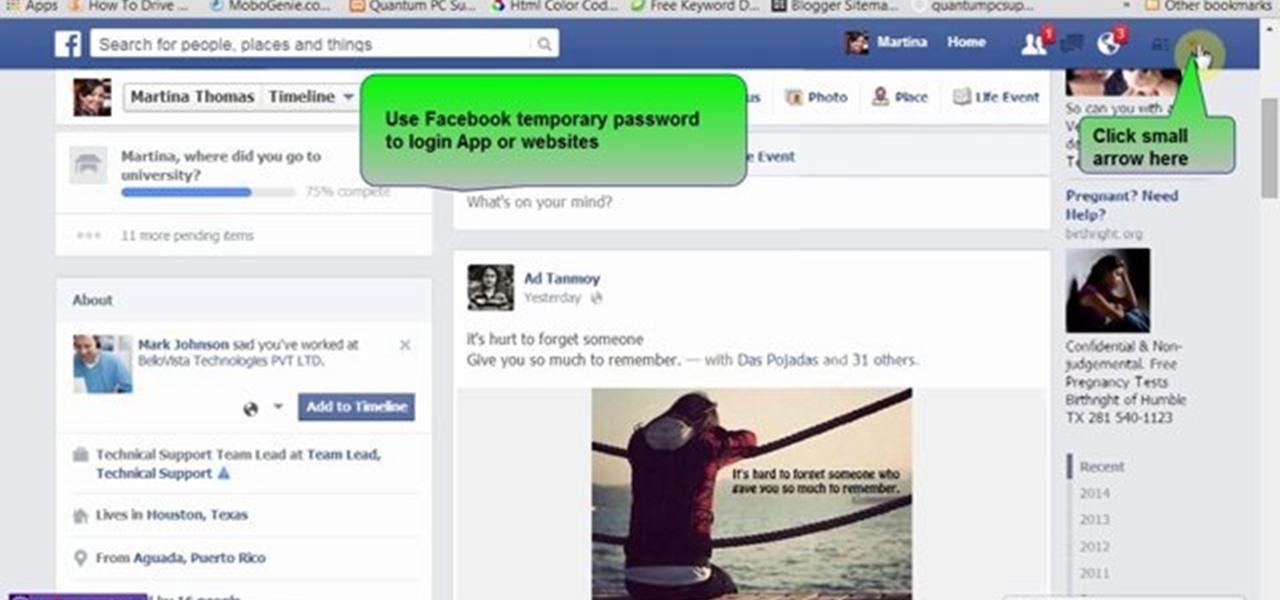
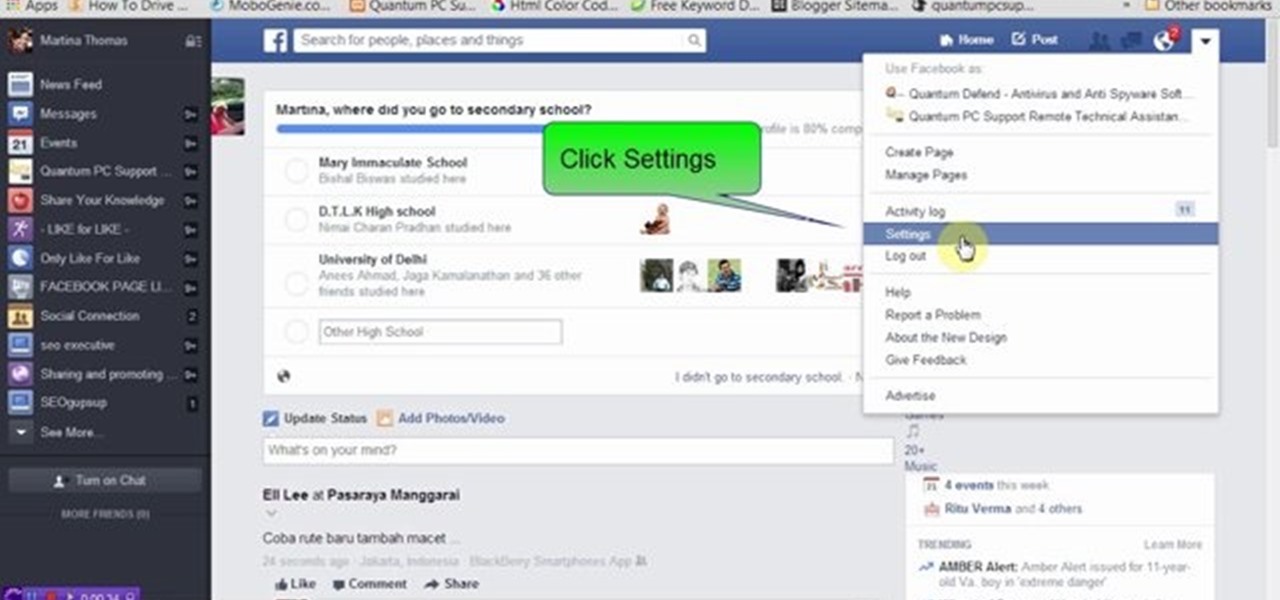
Many people use Facebook login detail to enter different apps or websites. This is somehow dangerous because unethical websites or apps may use your Facebook detail. So to avoid this warning Facebook is generating a temporary password for you. Now you could use this detail to login app or websites. You don't have to use your Facebook original login detail.

This video will show you how to stop spammy notification from apps on Facebook. It is often seen that people unintentionally install many unnecessary apps. Not only from those apps but from few useful app also they get spammy notification. This is irritating and frustrating. So if you want to stop notification from those apps then you must watch this video.

This is a tutorial I made in order to help people have a little more control over their pc and a little more options to change settings.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

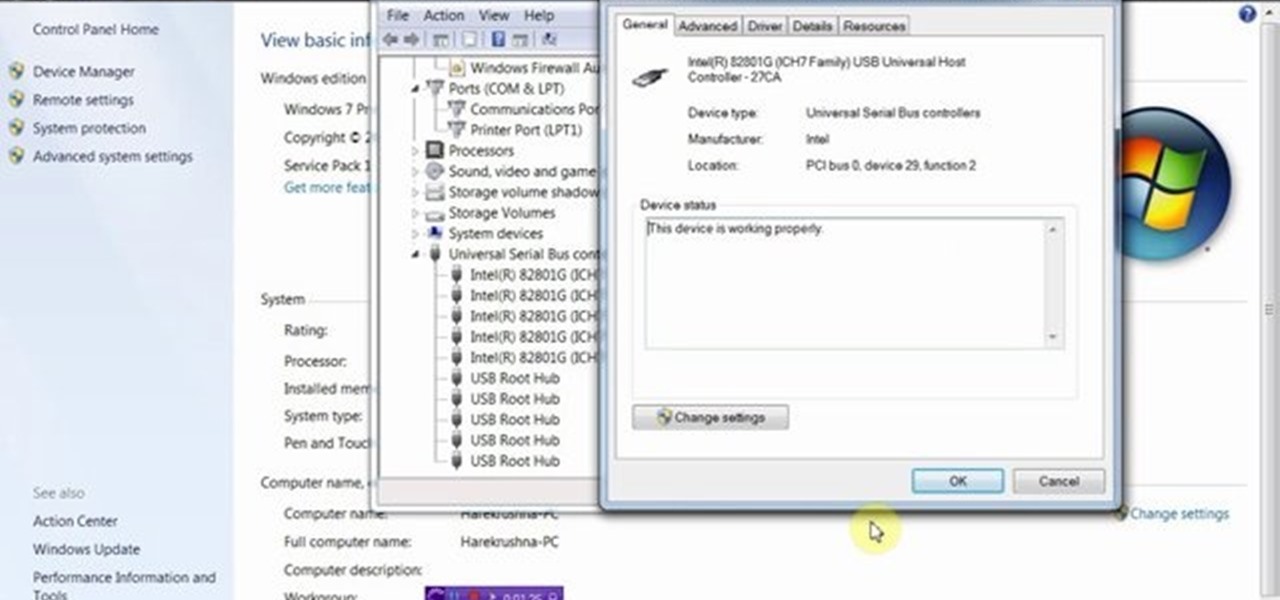
This video will provide an idea how to disable or enable the USB port on your PC. By disabling USB port will restrict people from copying your files into USB devices. This is a very effective trick to save your data. Watch the video and follow all the steps.