Pets America demonstrates how to perform CPR on a pet. First, lay the animal on the right side to bring the heart up. Bring the animal's left elbow back to the heart. Locate the pulse point. You can also feel the pulse on the pet's wrist or artery on the inside thigh. After locating the pulse, start CPR. Give the pet four quick breaths by having the head in line and tilting it back to open the airway. Close the lower jaw with your hands and hold the mouth shut. Bring your mouth down to the no...

Any patient with pain in the abdominal area will require you to perform an abdominal examination, and this video lesson outlines in great detail, how to perform a general abdomen exam. This is great for any medical student or up-and-coming doctor — even nursing students could benefit from this exam procedure. You'll learn about inspection of the abs, auscultation, percussion, palpation, the liver, the aorta, and the spleen. After watching the full procedure, you should be able to identify the...

In this tutorial, we learn how to properly perform the triangle pose. Start off on your hands and knees, then place your knees further back behind your hips. Next, bring your shoulders back and go into a downward facing dog position. From here, lift your arms away from the floor, then take a step forward with your right leg between your hands. Then, drop your left heel to the floor and place your right hand next to your right foot. Bring your right hip back and straighten the leg. The left hi...

As a doctor, sometimes it will be necessary to perform a neurological examination of your patient to rule out any neurological disorders. Your objective is to identify abnormalities in the nervous system, to differentiate peripheral from central nervous system lesions, and to establish internal consistency. This is a great video less that outlines the complete neurological exam procedure. It's great for medical students or doctors, and even nursing students can learn a thing or two.

Most won't know what the acronym HEENT stand for, but if you're a medical student, doctor or nurse, you know that it stand for head, ears, eyes, nose and throat. To perform a HEENT examination properly, you must know all the steps and techniques to diagnose your patient. This video lesson will outline the examination procedure, from start to finish, and shows you general palpation techniques and examining the temporomandibular joint, superficial lymph nodes, thyroid gland, eyes, ears, nose, m...

The key to being a good doctor is great patient care and thoroughness, and those are exactly the skills you will learn in this video lesson, as you learn to perform a cardiovascular examination on your patient. This is a great, step-by-step resource for the proper examination procedure. Every medical student should know these techniques, and nursing students could benefit from this knowledge, too. Every cardiovascular exam should include inspection of the pulse, blood pressure, carotid pulsat...

There's no better way to learn then by visual media, and that's what makes this video lesson on performing a chest exam so great. It's perfect for any future doctor, and great for nursing students to understand the proper procedure for examining a patient's chest. Medical students can easily learn how to perform a general chest exam, because ever step and technique is outlined and shown. A chest examination is very important to determining what's wrong with your patient, and you will be able ...

Whether your training to be a doctor or a nurse, there is no doubt that this video lesson will help you better understand the procedure for musculoskeletal examinations. Musculoskeletal exams rely exclusively on inspection and palpation and tests using a combination of those techniques. The main purpose of this exam is to identify in your patient any signs of musculoskeletal disease, by way of pain, redness, swelling, warmth, deformity, and loss of function. Watch this video to see the entire...

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...

This video explains how to perform the Color Monte card trick! Not an easy trick to perform, but with enough practice you'll get there :)

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

This video will show you how to perform the turn in the road driving test manoeuvre. Commonly know as the three point turn, it is used to turn the car around in the road to face the other way. You will need to keep the car slow and move the steering wheel quickly when you do this.

Your iPhone only has a few physical buttons, buttons with a set number of default actions assigned to them, like sleeping your display, controlling volume levels, and even taking pictures. But as much as these buttons can do for you, they can do more. You're not stuck with the out-of-the-box defaults. Every push button on your iPhone can be customized in one way or another.

As a side scrolling game, performing various jumps in Super Mario Run on your iPhone or Android is as vital as eggs in a breakfast buffet.

With as much creativity and freedom that we have on Android, it feels a little underwhelming that the only gesture we can perform on the status bar is a downward swipe to expose the notification tray or quick settings. Maybe this is a field for Android to expand on in the future, but until that day, third-party developers are exploring this now.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

In this video we will show you how to change the front brakes in your 1999-2004 Honda Odyssey.

Pull through the Legs is a beginner move that is quite easy to pick up. Definately a great move to begin with!

Here is a manoeuvre that you won't see every day. It is intended for drivers in commercial vehicles who cannot see to the rear. By reversing with the flow of traffic it is possible to see approaching vehicles through the front windscreen and the right hand kerb by looking down over your shoulder. This manoeuvre sometimes occurs on the ADI, Part 2 Test of driving ability.

Want to know how to possible save someone's life? Then watch this video to learn the proper way to execute the Heimlich maneuver. The Heimlich maneuver could help someone who is choking before the paramedics arrive.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

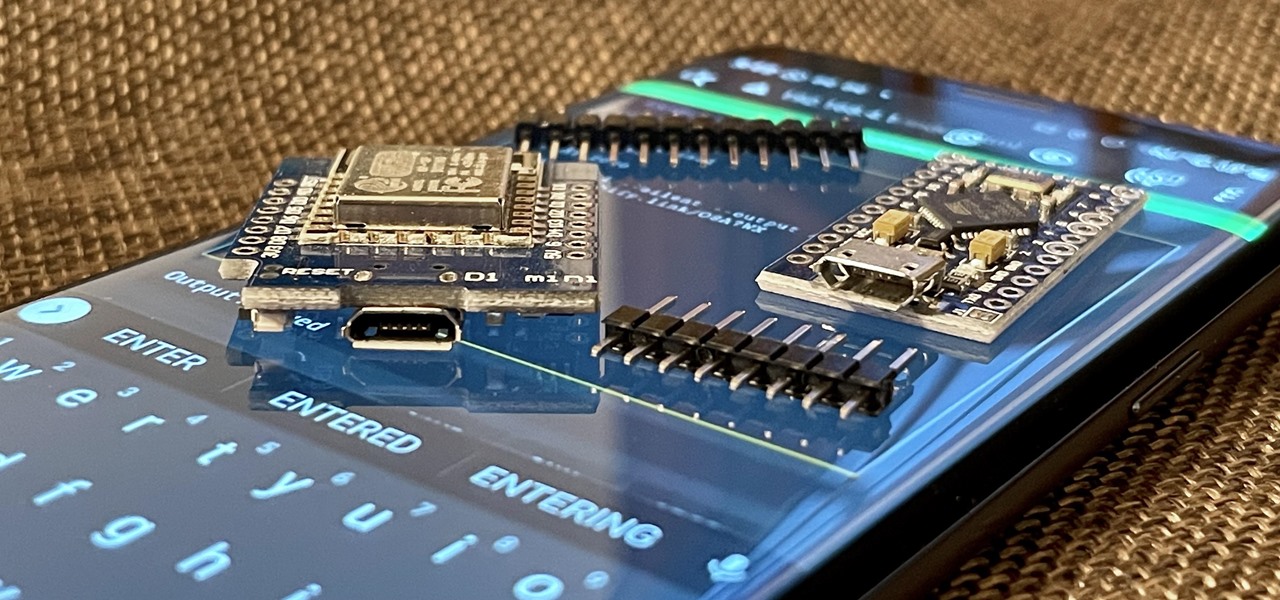
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

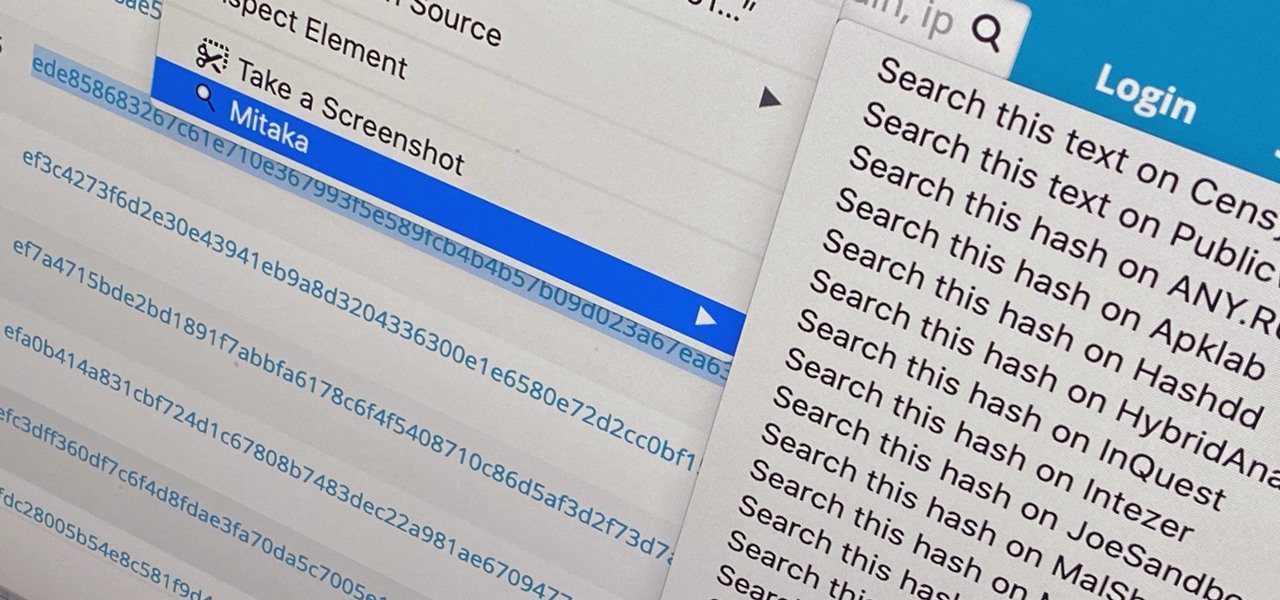
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Microsoft's HoloLens has two gestures: bloom and air tap. While the two might not seem like much to learn, some people struggle with the air tap because the headset can be a bit particular. The easiest way to learn the proper form is to look through someone else's eyes while they do it, so we've captured that for you.

Numbers are everywhere in life, and some are better at doing the math than others. Unless you're Gert Mittring, it's safe to say you use the calculator app on your tablet just as much as I do, and it's often disrupting your other tasks.

There are a lot of ways you can use pumpkins to decorate for Halloween. Of course, there's always the traditional jack-o'-lantern, but if you want to step it up a bit, you can make them glow in the dark, or put them to work for you by turning them into surveillance pumpkins to catch pranksters who prefer the 'trick' in 'trick-or-treat.'

Navigating and editing text is an essential part of any operating system, and with iOS 13, Apple has made some significant changes. Some things remain the same when working with text, but there are many updates to moving the cursor, scrolling, and selecting, cutting, copying, pasting, undoing, and redoing text.

With a price that undercuts flagship devices like the iPhone 6s and Galaxy S7 by hundreds of dollars and a smaller size, new tests show that the iPhone SE incredibly packs just as much power as its bigger brother.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

The HoloLens has become a frequent sight in medical facilities around the world, but a new demonstration shows just how seamlessly it can be integrated into traditional medical procedures to improve the experience for physicians and patients alike.